You might feel the bite, you might not, but an infected mosquito has injected you with a parasite named Plasmodium falciparum, a single-cell protozoa that quickly takes up residence in your body.

Alphabet's moonshot factory, X (formerly "Google X"), is a secretive place, but it seems that when they are close to graduating a project, then they need to staff it up quickly. Watching for these job ads is one easy way to know they're close to budding off a baby.

When you do an internet search, you'll see ads that are relevant to your query mixed in with the rest of your results. Nothing surprising there—it's how the internet is funded. But then, when you click one of the search results, you'll also see ads that are related to your initial search. Now that's a bit creepy, because it demonstrates that one webpage knows what you typed into a different webpage.
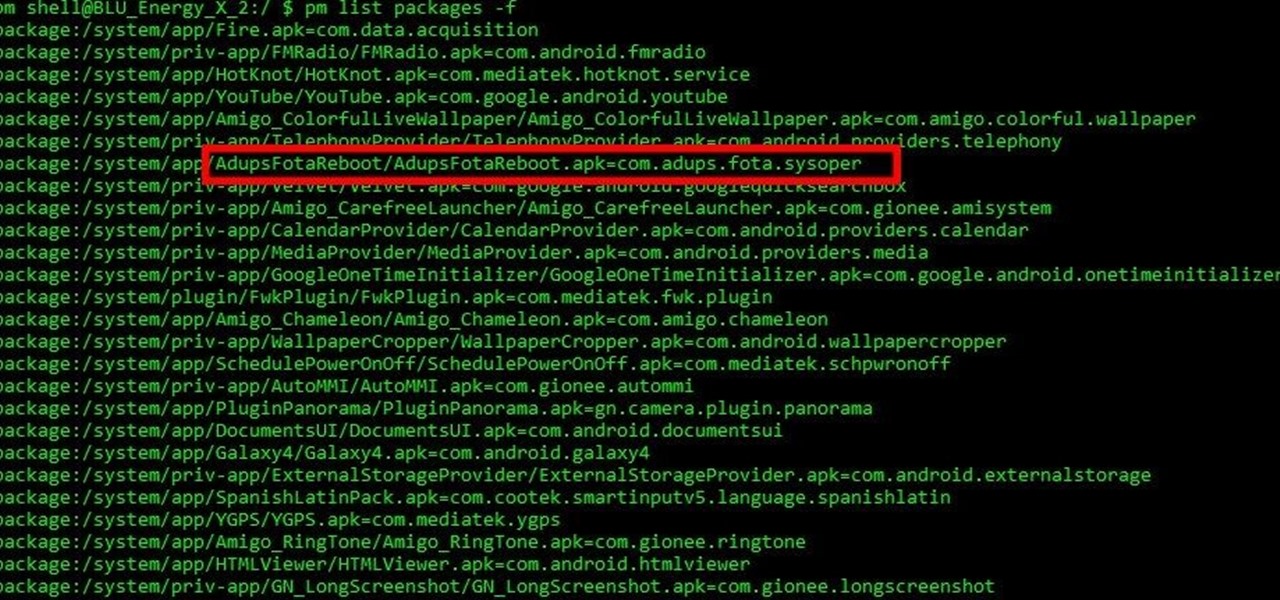
Mobile security researchers at Kryptowire recently uncovered spyware preinstalled on hundreds of thousands of Android smartphones by FOTA provider Adups which was gathering personally identifiable information (PII) such as call logs, app usage data, and even the full contents of text messages and sending these to a third-party server—all without the users' knowledge.

In this first part of my series on getting started with Windows Holographic, we are going to cover everything you need to get set up for developing HoloLens apps. There are many pieces coming together to make one single application, but once you get used to them all, you won't even notice. Now there are different approaches you can take to make applications for HoloLens, but this way is simply the fastest.

We haven't had a working jailbreak method since October of last year, and that only worked for about a month until iOS 9.2 came out and shut down the loophole it was using. So all of those cool Cydia tweaks have been out of the question for quite a while now, unless you downgraded your firmware to keep jailbreak compatibility.

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.

Counter-Strike is one of the most popular first-person shooters of all time, and deservedly so. What originally started out as a third-party Half-Life mod garnered such a cult following that Valve had to hire the developers and purchase the intellectual property to make it an official standalone release.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

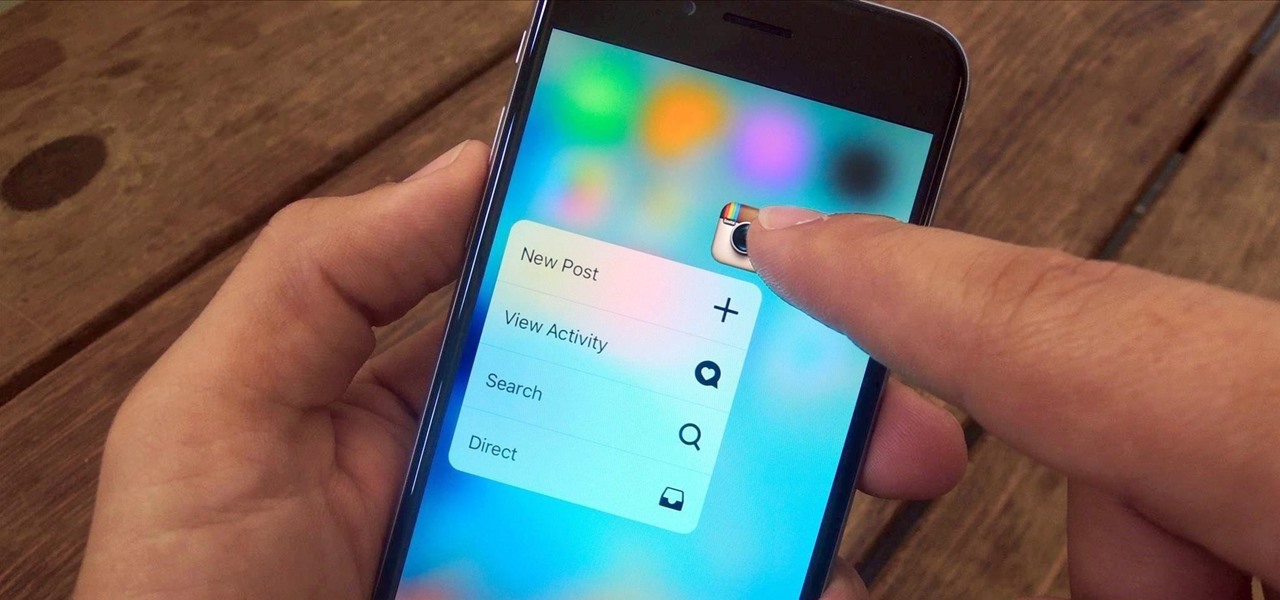
3D Touch is a new feature on the iPhone 6S and 6S Plus that's reinventing the way we interact with our smartphones. With just a little bit of added pressure when tapping on the display, you can perform Quick Actions from an app's home screen icon, "Peek" at emails, stories, and photos in-app, as well as perform other app-specific gestures. Since 3D Touch is such a new concept, here are some of the apps that currently support it, along with the shortcuts you can use.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Humans in general are great at keeping things about themselves private, from feelings to personality traits. While smartphones and social networks are making these secrets more open, narcissists have and always will love being out in the open with everyone's attention on them.

Have you ever fallen victim to a clever Jedi mind trick? Don't worry. It happens. There are evolutionary reasons as to why our brains sometimes give into the oldest tricks in the book. Fortunately, the more you understand the tricks of a salesman, the easier it is to avoid their gripping psychological influence. Clue #1: Too Much Specificity

Let's be honest, most of us buy the bottom-shelf vodka either because we're broke or because we're going to disguise the gag-inducing taste of it with juice or something fizzy. If you're cooking or baking with vodka (ice-cold vodka works wonders in pie crust), what's the point of buying Belvedere?

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

Let's take a minute and talk about something you're doing wrong — using the restroom. Many view the subject as improper or even taboo, but why? Thanks to your upbringing, you've assumed you know the basics... But you don't. Avoiding discussion on the subject has led many of us to unwittingly interact incorrectly during our private time with our old friend, Jon.

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.

In the UK, 20 percent of divorce filings include the word "Facebook." You may think you're being slick by using the site to chat with your ex, but the problem is that Facebook saves everything, and I mean everything. All someone needs is your login information and they have access to everything you've ever said on Facebook, public or private.

I was kinda disappointed with last year's James Bond movie, Skyfall. Don't get me wrong, it was a solid flick, but only made me jealous with all its super spy hacker stuff.

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

When browsing the web, I enjoy my privacy. It's reassuring that I can peruse the internet without the worry of having my activity tracked back to me, allowing me to leave fun, anonymous comments when I get the urge to troll.

For some reason, there's only ever one person in a group of friends that has a cooler. Every time there is a hangout or BBQ, that friend is called and has to lug his expensive, huge plastic cooler around for everyone. Not really fair, is it?

It's that time a year when winter storms begin causing havoc across the United States, and when "rotating outages" are common to help sustain the electrical grid during intense cold periods. That means pretty much anybody with snow and ice in their backyard can succumb to power outages. And no electricity means no electric heat.

Ultimately a doctor’s note is the only necessary proof needed to show your boss that you really did go to the doctor’s but if you feel like making an airtight case you can always take a few extra steps to make sure there’s not a shadow of a doubt.

In this series of videos, learn more about playing the flute from our expert. An experienced player, she first teaches you about buying and assembling your flute. You will also learn about the accessories needed for playing and caring for your flute. Learn scales easily by watching videos on the C scale and F scale. Tuning your flute is often necessary to get the right sound. Other common problems with flutes are addressed in this series as well. Get tips on private lessons and instructional ...

You no longer have to worry about repair technicians accessing the personal information on your iPhone when you send it in for repairs. With Apple's new security feature, you'll no longer have to erase your iPhone to ensure your photos, messages, accounts, and other private data remain for your eyes only.

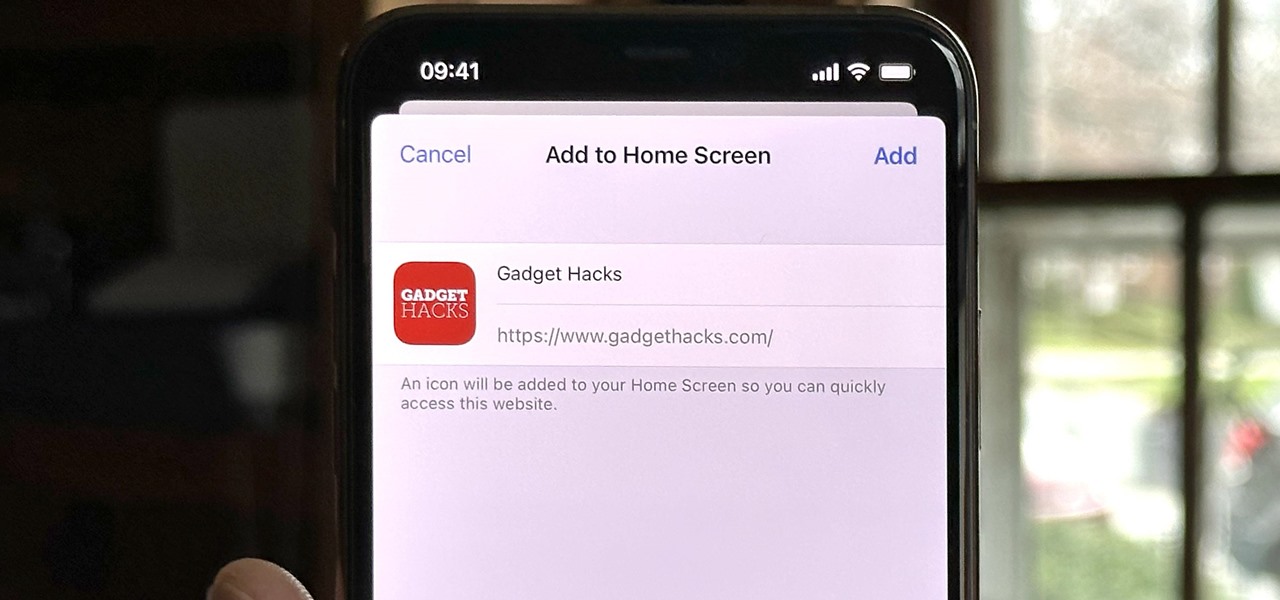
Safari isn't the only web browser on your iPhone or iPad that will let you add icons to your Home Screen for progressive web apps and website bookmarks. Apple gave developers the key to its "Add to Home Screen" feature, and your favorite iOS or iPadOS web browser may already support it.

Your iPhone has a powerful feature that can keep your secrets hidden from other people, and you'll never have to worry about sharing or showing someone something embarrassing or incriminating ever again.

Safari keeps getting better and better on the iPhone, and that's exactly what happened with the latest Safari 16 update for iOS.