Do you have something important that you want to hide from your parents or friends? Well, then check out this tutorial. In this video, you will learn how to take an ordinary Pepsi bottle and turn it into a secret stash box. Because the bottle is see-through, no one will ever suspect there is something inside of it.

In this Computers & Programming video tutorial you will learn how to hide and lock folders in Windows. When you want a private folder that you don’t want any one else to open and see. You will need this feature. For this open a new folder. Open the folder, right click on it and go to ‘customize’. Then select ‘change icon, click on a blank icon, click OK and ‘apply. Now you will see that your folder icon on the desk top will disappear; only the name will be visible. Now rename it with a small ...
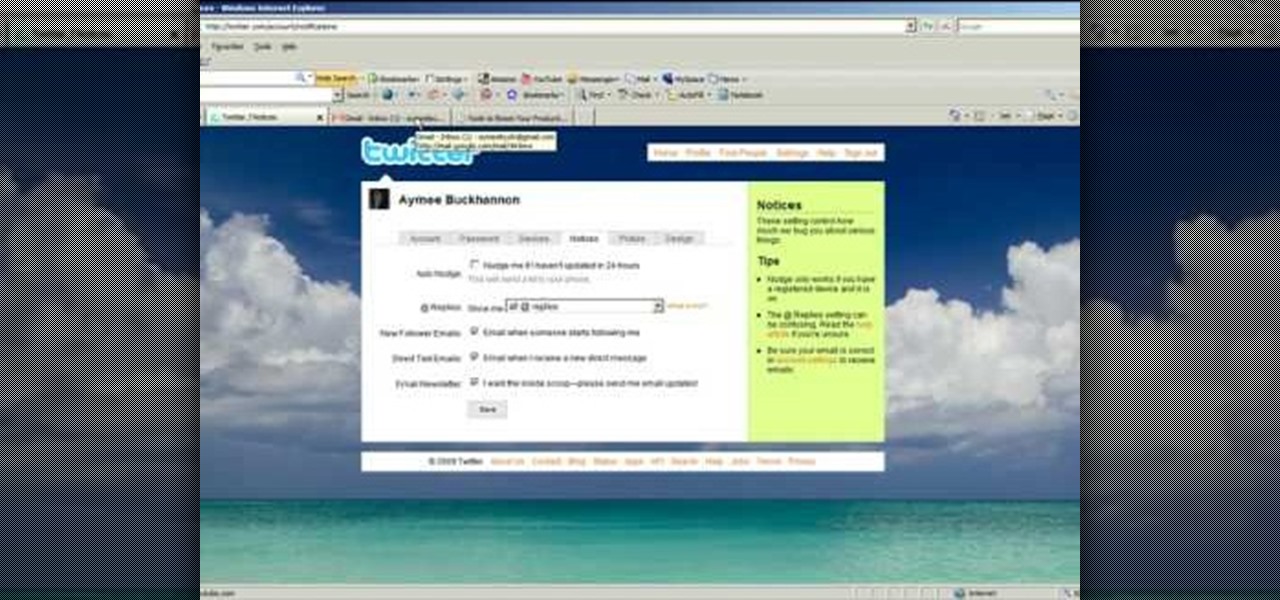
Twitter is the latest popular social networking forum. Twitter is used to keep your friends updated with what you are doing using 140 character messages called tweets. In twitter you can follow your friends and you will be notified when ever your friends posts a new message. Similarly other people can follow you on twitter to know what you are doing. In twitter you can customize to send an automatic private response to your new followers. To do this open your twitter account. Go to the notice...
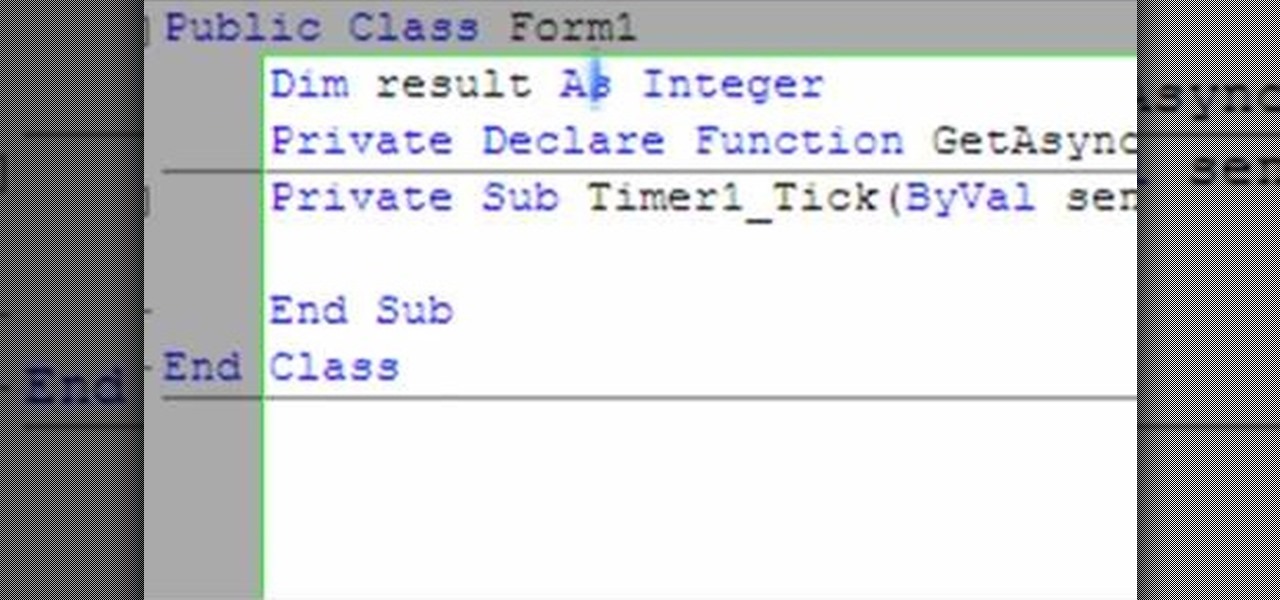
The following video shows how you can make a keylogger in Visual Basic 2008. Follow the steps below to create your own keylogger. First you will want to open a new application and name it according to your preferences. Then you want to click on the toolbar button and click textbox. In the textbox values, you will want to select the value of true for 'Multiline' option and the value of True for 'Read only'. On the toolbar, select the 'Behavior' tab and mark it as 'Window'. Go back on to the ma...

Pilates is fantastic exercise. If you are a beginner, though, it can be confusing to choose the right type of class. Check out this tutorial before you head to the studio and ensure you get the most out of your exercise routine.
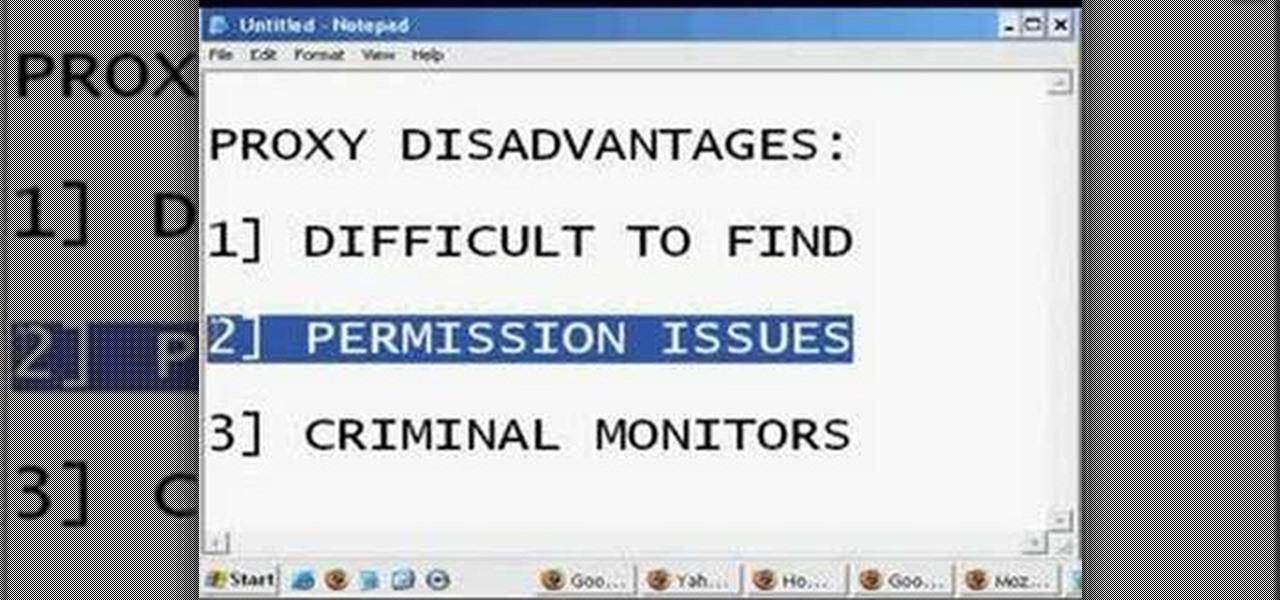
In this tutorial, we learn how to change your IP address in five different ways. First, go to your security settings and clear all cookies, then start to browse the internet with private browsing from your internet browser. You can change your IP address by going onto your internet browser and changing the LAN settings. Type in your address and port, then bypass the proxy server. Next, go to options and then advanced on your browser. Type in the proxy and port, then click where it says no pro...

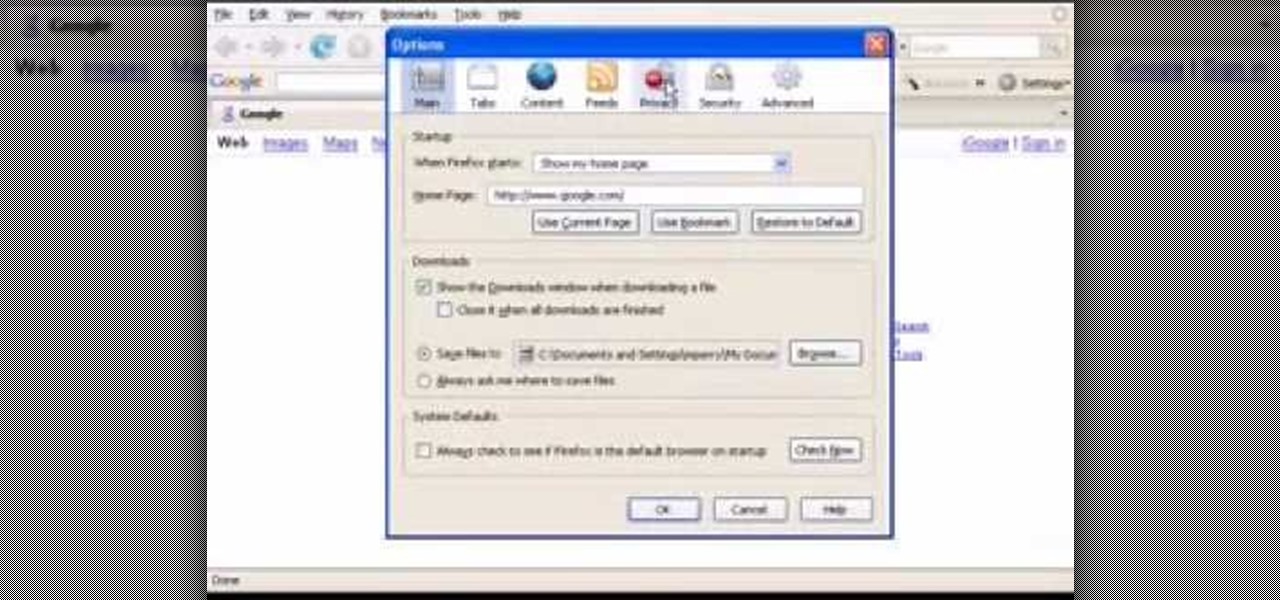
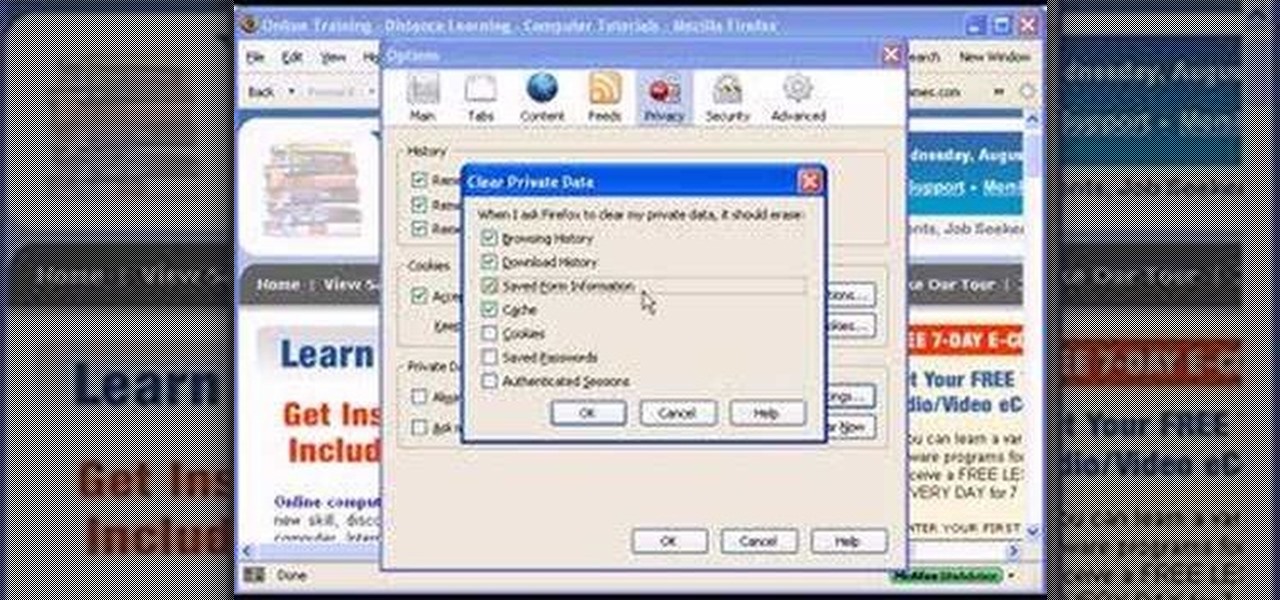
In this video, we learn how to reset your browser history in Mozilla Firefox. First, open up Firefox, then go to the options menu. When you're on here, go to the privacy tab and then click on the options that will dump out the history that has been saved. You can also change your settings if you want to remove your search history and clear your cookies. At the bottom, check if you want it to clear private data. After this, press on the "ok" button and everything will be saved. When you are do...

In this tutorial, we learn how to create a Facebook event for a group or member page. To do this, log into your Facebook account, then click on the "create an event" link. Now you will be able to add a name, tagline, description, date, type of event, start time, location, and more details about the event. Once you do this, you can invite your friends into the event and also make it a private event or a public one. After this, you will also be able to upload a photo and then once friend's RSVP...

In this video tutorial, viewers learn how to clear cache and cookies in Mozilla Firefox. This task is very simple, easy and fast to do. Begin by opening the Mozilla Firefox web browser. Then click on Tools menu on the top of the window and select Options. Now click on the Advanced tab. Under the Network tab in Cache, click on Clear Now. To clear cookies, click on Tools and select Options. Then click on the Privacy tab and click on Clear Now under the Private Data heading. This video will bene...

Deleting your Internet history once in a while is important. Not only will doing so protect your privacy, but it will also clear up much needed space on your harddrive and help your PC run quicker.

This video tutorial tells you how to create a free VPN with the website itshidden.com. The first step in creating your VPN on itshidden.com is to make an account on itshidden.com. Register with your own username and password. Then when you've made an account log in to it so that you can use the rest of the website. Next you go to control panel, and then network setup. Then you will have to click through the instructions in order to create a new network. Next you will have to create a new conn...

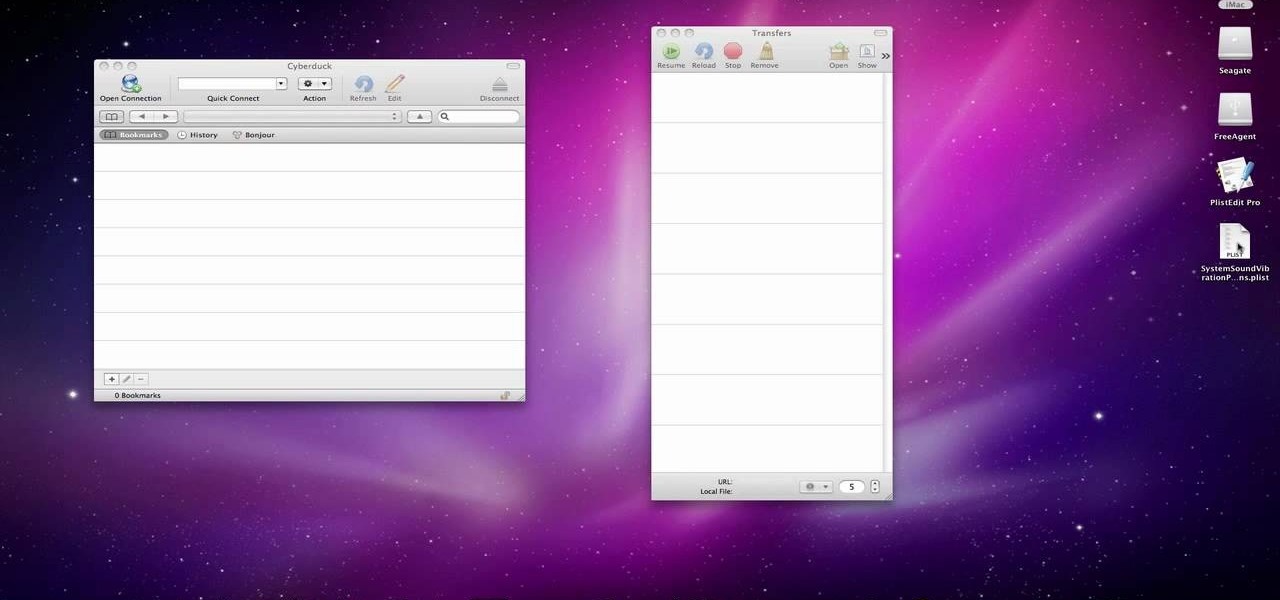
In this video we learn how to make your iPhone vibrate your notifications longer. For this you need an SSH program like cyberduck. You also need plist edit pro. Once you have SSH in your phone, go to system, library, private frameworks, celestial framework, then find vibration patterns. Double click that. Download it to the desktop. Open it. Open up the plist file. Go to default, look at total duration, click into that to change the time of the vibrate duration. Change the On Duration too. No...

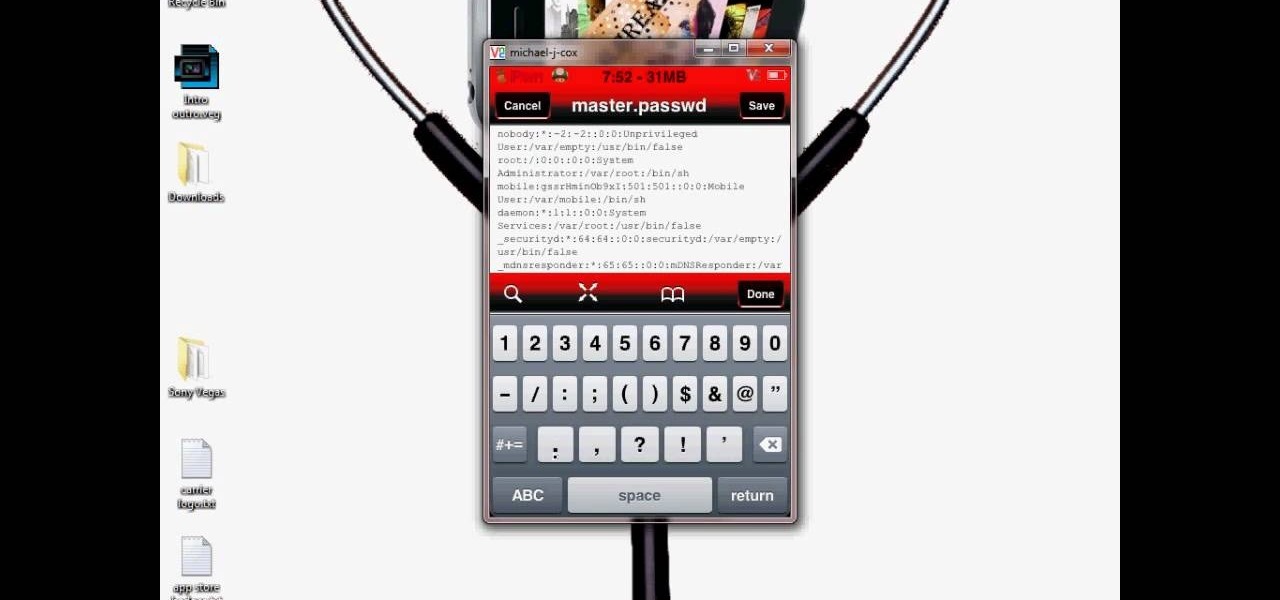
This video tutorial from DrJailbreak shows how to reset your SSH password on iPhone or iPod.If you changed your password through Rock with your Mobile Terminal and forgot it, this is what you are going to do to set your root and mobile password back to alpine.First you will need iFile application. Open Cydia and browse to http://repo.beyouriPhone.com. Navigate to Be Your iPhone Repo and scroll down to iFile. Download and install.Open iFile and navigate to /Private/etc.Scroll down and open mas...

Chau-Minh, a private tutor, discusses cramming and how to do it effectively. This video does not intend to endorse cramming, but if you are probably screwed then you might as well see it. When you cram, don't expect to get a high grade because you lack time. To pull out a high grade, we need to do deletion. Deletion is just like chopping a branch to make the tree smaller. The tree would signify the lectures of your professor. Crossing out the topics that are discussed rarely by the professor ...

Jim from the "My Temp Number Helpline" teaches us to block outbound caller ID on your phone. The first way to do this is to open up the dial pad and enter *67 before the number you want to dial. This will show up on the receiving line as "Private Number" or "Unknown". To permanently block the number you go into your phone's settings. Then click on the word phone. Then click where it says "Show my caller id". If this setting is off, then your number is blocked on all outbound calls. This is us...

In this video tutorial, viewers learn how to save money on beauty products. In-store cards and frequent buyer programs can save a lot of money. When you scan the CVS Extra Care card at checkout or in-store kiosk, coupons based on your purchase will be printed automatically. It will give good discounts. Web only offers are becoming popular. Private sale sites have also become popular. You simply sign up on the site and take offers that the site has. This video will benefit those viewers who ar...

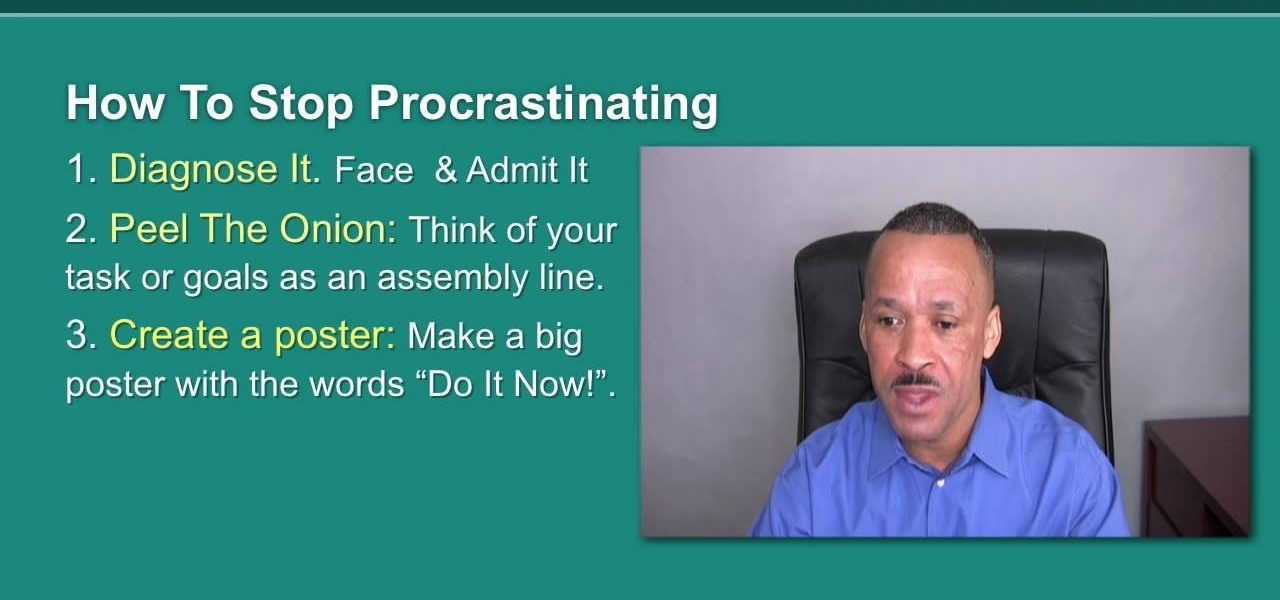
glemo teaches you how to stop procrastination. This is like termites eating at the foundation of a house. It eats you up inside and you need to learn self control and discipline. You have to discipline yourself to do the things you do now, or you will feel regret later. First off, you need to diagnose your problem and admit it. Think of your life or your activity as an onion. There are different layers and different components. You need to break your task into smaller ones. You have to trick ...

Steps to clear the cache on Firefox and delete unnecessary temporary files from your computer. In your Firefox browser go to TOOLS. Click on OPTIONS. Then go to PRIVACY tab. Click on PRIVATE DATA section and click on SETTINGS. Now you can clear the following items: browsing history, download history, saved form information, cache, cookies, saved passwords, authenticated sessions. Check what you'd like to remove, specially the cache option. Mow click on OK button. click on CLEAR NOW and click ...

In this video the instructor gives tips on how to erase a PC hard drive. An MIT study shows that 74 percent of the discarded hard drives contain private data on them that can be read and recovered by others. So you should learn how to completely erase all the data so that no one can recover or read from it later. Now formatting the drive or deleting a few files wont do it. For this you will need to have a proper software that meets or exceeds that US Department of Defense standards for data r...

Syncing Twitter with Facebook is what we learn to do today. Go to your left hand corner and click applications. Go to browse more application and type in Twitter sync. It will pull up the application. Click on that. Go to tweet sync on Facebook and then become a fan. Then you will go to application. There are some nice options so you're not swamped with tweets. Now click on if you have a private Twitter account and enter your Twitter id. Now whatever you tweet or Twitter will automatically be...

To upload pictures to your Facebook account, this video instructs, you'll want to start by knowing where the exact picture or pictures you're wanting to upload are located on your computer. Then, from your main Facebook account page, click on "photos". From here, you decide how private to make the photo. Then, remembering the location of the photo you wish to upload, you must go there and click on it. That done, you can choose a caption for the photo, and click confirm. The biggest social sit...

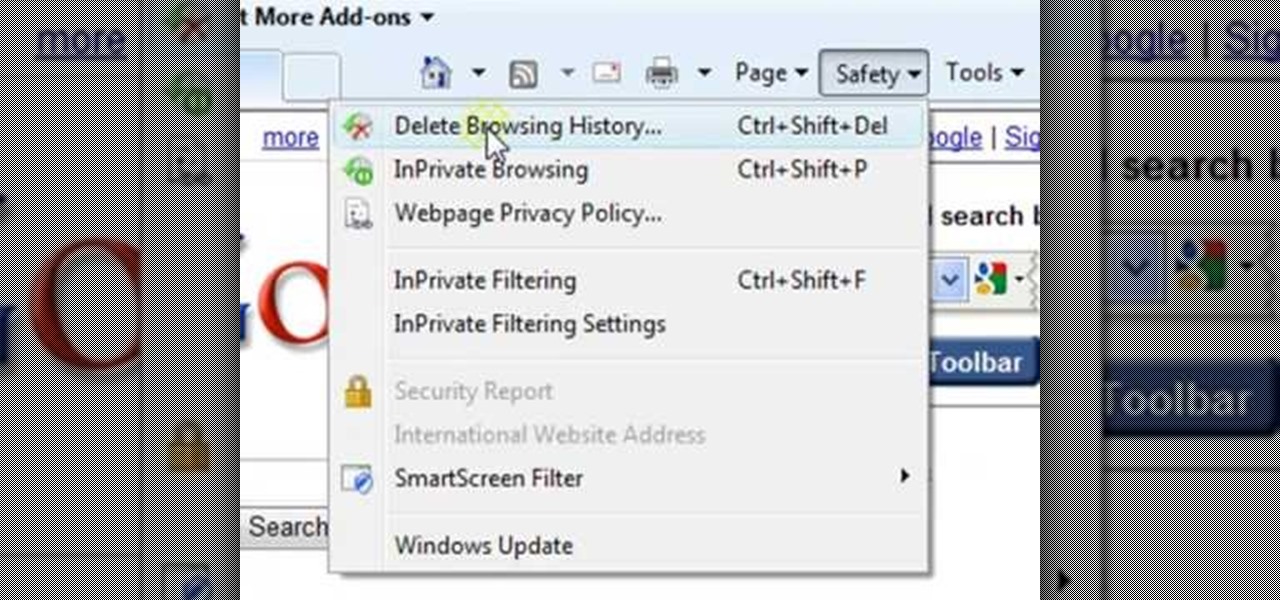
ClearTechInfo presents a how-to video on clearing Internet Explorer 8's browser history. Computer users are reminded that the only silly question is the question not asked. In the video, the viewer is shown that by clicking the button marked "Safety" in Internet Explorer 8 the "delete browser history" option is revealed. As long as each option is clicked, the history for the computer user is deleted. The browser history, cookies, cache, and passwords can all be deleted with the click of the b...

In this video the instructor shows how to remove vocals in a audio using the Adobe Audition 3 software. He says that one cannot remove vocals 100 percent but just reduce them to a minimum compared to the rest of the sound. He shows you a sample track first which contains vocals.

In this video, Dr.Travis Fox explains how you can tell if your partner is cheating through eye cues. Many people will search and hire even private investigators to find out the truth. Dr. Fox in this video says to "save your money." He tells you about certain indicators that are used to read if they are lying. For example, looking to the left or looking down might indicate that they are lying to you. He does say that it is not 100% always correct but works well in a lot of cases.

In this tutorial by Shooting Eggs, you'll learn how to create your own "ocean in a bottle". The supplies are very simple and cheap, probably stuff you've already got around the house. But the finished effect is pretty impressive.

In this AeroCast episode, Anthony Bottini discusses the Power Off Stall maneuver as performed in the Piper Warrior (PA-28-161), referencing the procedures and standards outlined in the UND Aerospace Warrior Standardization Manual. All performance tolerances are based on the performance standards set forth by the FAA Private Pilot Practical Test Standards. Power Off Stall practice is vital in increasing a pilot’s proficiency in regards to stall recognition and stall recovery techniques during ...

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

Smartphones have so much sensitive information attached to them. If you share your home with others, then you know the pains of trying to keep anything private. Photos are surely among the things you'd prefer to keep to yourself, so OnePlus has you covered.

After drawing attention from nostalgic Gen Xers for its Motorola Razr reboot with a foldable screen, Lenovo has a new augmented reality smartglasses concept that the company hopes will also turn some heads.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

Two characters from the popular sci-fi animated comedy Rick and Morty have already made their way into augmented reality courtesy of ARKit experiments. Now, it's possible to become one of them on the iPhone X.

If you've received a spam message in Signal Private Messenger, you know that anyone can contact you as long as they have your linked phone number. But when it comes to the people you're actually trying to have a private conversation with, how do you know it's really them?

One of the most popular things to do on Snapchat is to earn a Snapstreak. This occurs when you and one other friend have sent snaps (not chatted) to each other within 24 hours for at least three consecutive days. One you've passed the three-day mark, then you and your friend will receive a fire emoji next to your names.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

Fring is a free app available from the Apple store which will allow you to use video chat, Skype or AIM on your iPhone 4 over a 3G network. This tutorial demonstrates how to use the app with your iPhone to make video calls.

Learn insider tips for managing a private health club and the best way to manage your health club, gym, spa, or fitness center with expert health club management advice in this free online management video series.

This tutorial shows you how easy it is to start a one way video chat in iChat and goes over some of the benefits of using it.