You're only as smart as your communication skills allow you to be, as other people will simply never know your inner genius if you can't effectively express yourself. Regardless of the medium—be it a Facebook post or even a simple text message—this fact remains true.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

If you're ever lost or hurt out in the middle of nowhere with a dead cell phone, you might be able to "flag" down help as long as you're near some railroad tracks.

Whether you're ready to admit it or not, we've all got our alter egos—especially when it comes to the internet. Perhaps you have one Facebook account that you use publicly, while maintaining a second account for more private interactions.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

If you purchased something from iTunes, the iOS App Store, iBooks Store, Apple TV App Store, or the Mac App Store and it doesn't work, didn't download, is buggy, or wasn't what you thought it was, you can get a full refund from Apple—you just have to know how to ask.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.

Yes, there's already a way to jailbreak iOS 9 on your iPad, iPhone, or iPod touch, but given the fact that it's only been out for about a week means that not all developers have had a chance to make their tweaks fully compatible yet. That doesn't mean they won't work, but that they might not be as smooth as they should be.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

I have a personal rule when it comes to an app's interface: If it doesn't follow Android's design guidelines, it was probably written with Apple's iOS in mind first and foremost.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

If you have some photos, videos, and documents that you want to keep completely hidden and encrypted on your Android device, Andrognito is the app you need. We showcased this app in the past, but since then, CODEX has rebuilt it from the ground up with new and improved features.

When setting up a new Mac, there can be a bunch of settings that need to be changed in order to get the system running the way you like it. That usually involves going through tons of System Preferences panes and app settings—but it doesn't have to.
Hello and Welcome back to another How-To on the Xbox Community Ambassadors World! In this How-To, I am going to tell you and kinda show you how to deal with or avoid angry Xbox Customers.

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

With over a billion monthly active users, it seems that Facebook is nowhere close to being dethroned as the most popular social media service in the world (sorry, Ello). While their stats may be impressive, it doesn't mean that Facebook is as good as it can be.

We all carry a bit of anxiety around with us. Is our boss still annoyed because we could barely stay awake in yesterday's pre-dawn meeting? Will our friend hate us forever because we forgot to call them back two weeks ago? Whatever worries pop up in your mind, whether they're monumental or insignificant, it can be hard to quiet those nagging voices, but you can shut down your nonstop mind with a bit of relaxation, distraction, and action.

Admit it: you've been caught muttering to yourself under your breath in very public places. Maybe you've gotten stares while wandering the grocery store talking to yourself out loud. If you're like me, you might even talk yourself through various tasks, giving the atmosphere a little background noise.

While we now know that iCloud was not exploited by hackers to steal private celebrity photos, Apple did admit that guessed (aka brute-forced) passwords and/or iCloud security questions were to blame for the breach.

If you've read any health news in the past year or so, you've probably been bombarded with headlines announcing that frequent sitters face certain death, even when you're just relaxing and watching TV at home.

Certain files contain sensitive data that you don't want being shared with just anybody. Even still, it would be nice to be able to send such a file to a certain confidante without fear of it falling into the wrong hands.

The biggest hurdle faced when text messaging (besides more convincing lies) is accurately communicating our emotion and tone. Anything we say can be interpreted in various subjective ways by the recipient, and that's why we have emoji—to illustrate what we actually want to say.

Hi! Let me get started on this subject as it is a very "touchy" subject. We all want to "hack" these days, and that's logical. Te be real honest here, i was inspired once by the words someone from the Null byte community said. In the (near) future, wars will be ended by computers and not a nuclear missile. That's something i really do believe in. But let us take a defensive measure instead of the offensive one. Sure, Full frontal bryte forcing is an option, but when it'll come that far we'll ...

The newest version of iOS 8 beta is now out. Almost three weeks ago, in the iOS 8 beta 2 release, we saw podcast integration, full-screen caller ID, new assistive touch toggles, and a "disable all" button for app notifications, among other things.

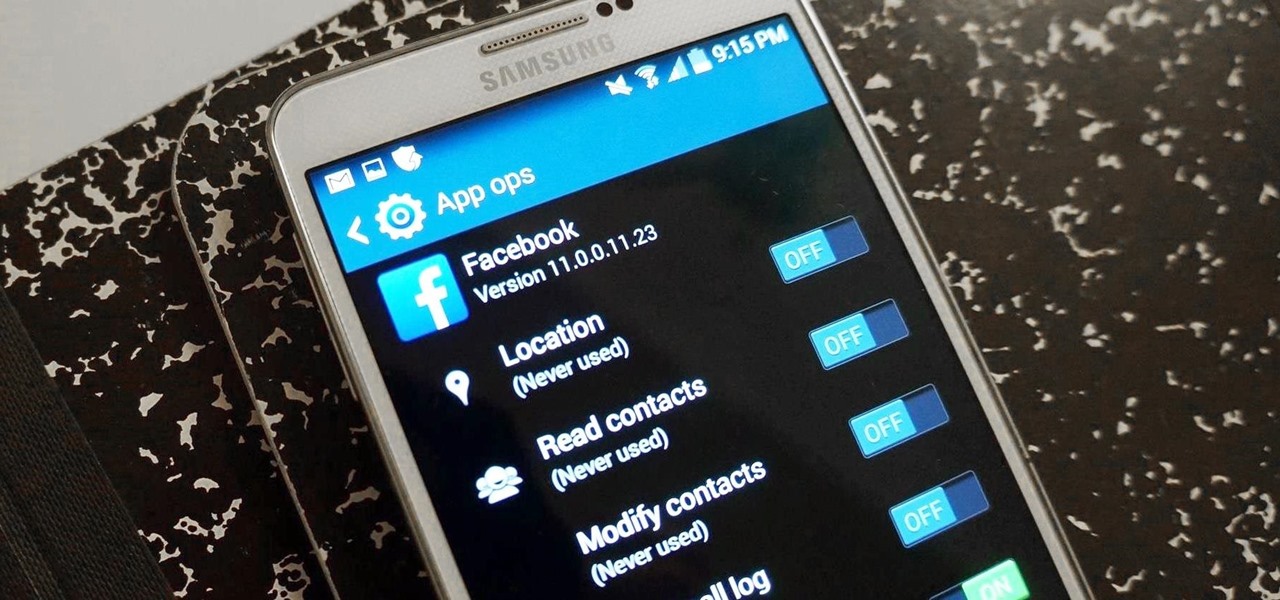
It's a modern day nightmare to accidentally reveal too much information on Facebook. I've inadvertently told the world my location more times than I can laugh off, and my friends haven't fared too well either. Just take a look at the requested app permissions next time you're about to click install and you'll quickly realize how much that app can reveal about you.

While their merger with Microsoft has lead to a seemingly complete halt of new device development, some Nokia employees are still hard at work to bring new software to the table.

When OS X Yosemite was first announced, there were a number of features that struck my attention, but one in particular that stood out above them all was the ability to make and receive texts and phone calls from your Mac, which Apple calls Continuity.

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.

Dropbox, the cloud backup tool that is a mainstay on many of our devices, has added two companion apps to its service. Earlier today, we showed you a glimpse into a new testing version of the Gmail app, with features like pinning and snoozing to keep your inbox in check. Now, Dropbox has released Mailbox for Android, about a year after they purchased the company and its iOS app, with a simple goal: taming your inbox.

What do Hulu Plus, Pandora, and YouTube all have in common? Ads—and lots of them. Sometimes, an advertisement or two isn't a big deal, but when you're bombarded with them daily on your iPhone, they can get old really quick, and might even lead you to delete the apps entirely.

Most people keep their ungodly sexual desires deep inside, only to be indulged in private on their computers. It makes you wonder... what secrets do your neighbors have? What kind of porn are they watching? And how much and for how long? Thanks to some public (and anonymous) data, you can now find out.

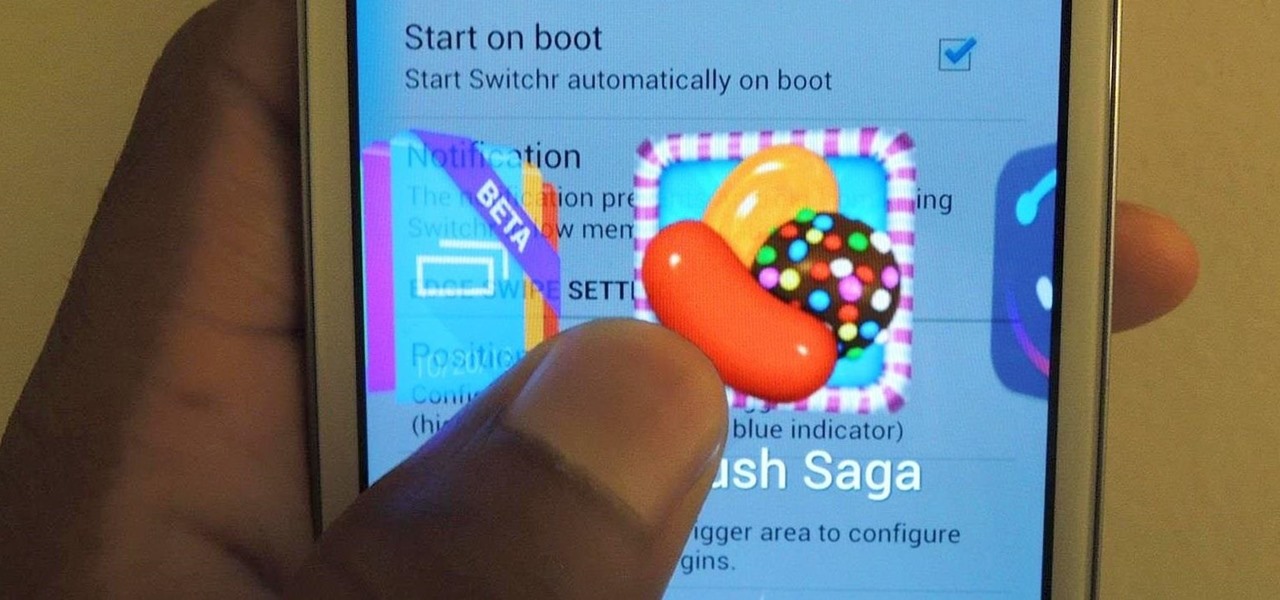
I've covered a few multitasking app switchers before, but none of them are as sleek and smooth as the aptly titled Switchr, a new app developed by Mohammad Adib that lets you move from one app to another quickly and smoothly—just like how I switch between my women. Well, not really, but I would.

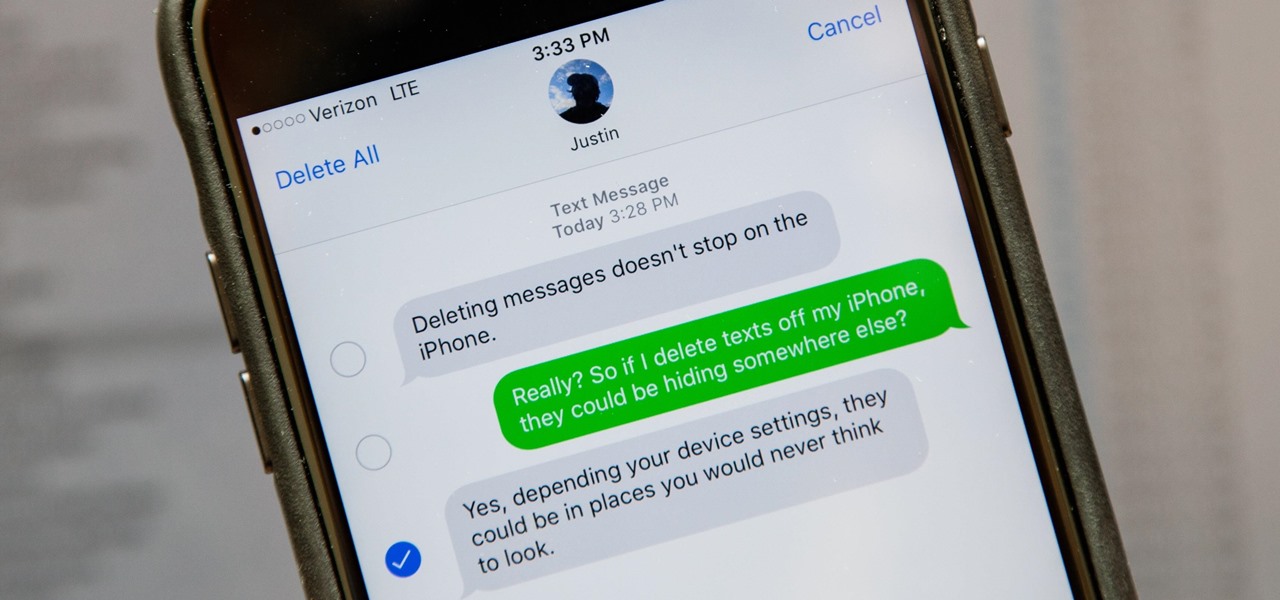
Deleting text messages on your iPhone may seem like a pretty simple task, but it's those really simple tasks that usually end up causing headaches later on. Data can stick around, even if you asked it not to, so there's always a slight chance that embarrassing and incriminating texts you supposedly deleted may end up in the wrong hands one day.

A wave of shock and anger swept across the country after Edward Snowden released private documents recounting the U.S. government's secretive mass surveillance programs. Although some of the fear was unwarranted (they don't read your emails or listen to your calls), many scrambled to find privacy of new heights for protection from the all-watchful eye. While the government may not be tracking you down, there are a myriad of other candidates that fill that Big Brother role—and I'm not talking ...

Whether or not you believe that the government is snooping around in our private emails, texts, and phone calls, it wouldn't hurt to protect ourselves a little better in the digital realm.

It starts innocently enough, with a nosy friend hovering over your shoulder to see what you're texting. Somehow, that doesn't satiate their inexplicable thirst for curiosity, so the first chance they get, they're rummaging through all of your super private photos—even though you told them not to.