Maybe your kids are using iPhone/iPad too much, as a parent, you want to know what they are having to deal with to help guide them through of that. Here is the tutorial on how you can parental control your kids on iPhone/iPad. You are able to monitor as well as take control of their devices. Kids’ activities on iPhone/iPad like SMS, chats, web browsing will be recorded and you can check them remotely with e-mail without getting access to the devices. OK, here comes the steps: Step 1:

When you really think about it, registering for any website is a little scary. Not only do they now have your name, email address, and a username/password combination you might've used elsewhere, but certain sites and services ask for quite a bit more private information. From phone numbers to addresses to birth dates and more, that company now has all of your information stored.

Use the following Gourmandia napkin folding secrets to impress and surprise your guests at private parties, restaurants, weddings and date dining. Learn how to fold a napkin like a peacock. Fold a napkin like a peacock (Pliage paon).

You never know when you may lose your BlackBerry and expose all your personal information to whoever finds it. That's okay, protect private data on your mobile PDA by setting a password. Now you don't have to worry about strangers stealing your secrets anymore. Set a password for your BlackBerry Bold.

What happened to please and thank you? When did asking someone to come look at your build degenerate into COME NOW or FOLLOW or sending out teleport requests to any and all currently on the server without asking?

Cell phone jammers, a DIY endeavor for the darker crowd. I'm pretty sure we've all considered having one at some point: whether the obnoxiously loud woman next to you is announcing private bedroom stories to a crowd on the subway, or your kids are grounded from using the phone (and consequently snagged a hidden prepaid phone), sometimes having a cell phone jammer comes in handy.

There is a near-infinite amount of ways a computer can be broken into. But that does not mean that there isn't a reason to secure our computers as best as we possibly can. It's like the principles of a secure house. Which are the most secure houses? The ones with locks and advanced alarms, obviously, but not for the reasons people normally think.

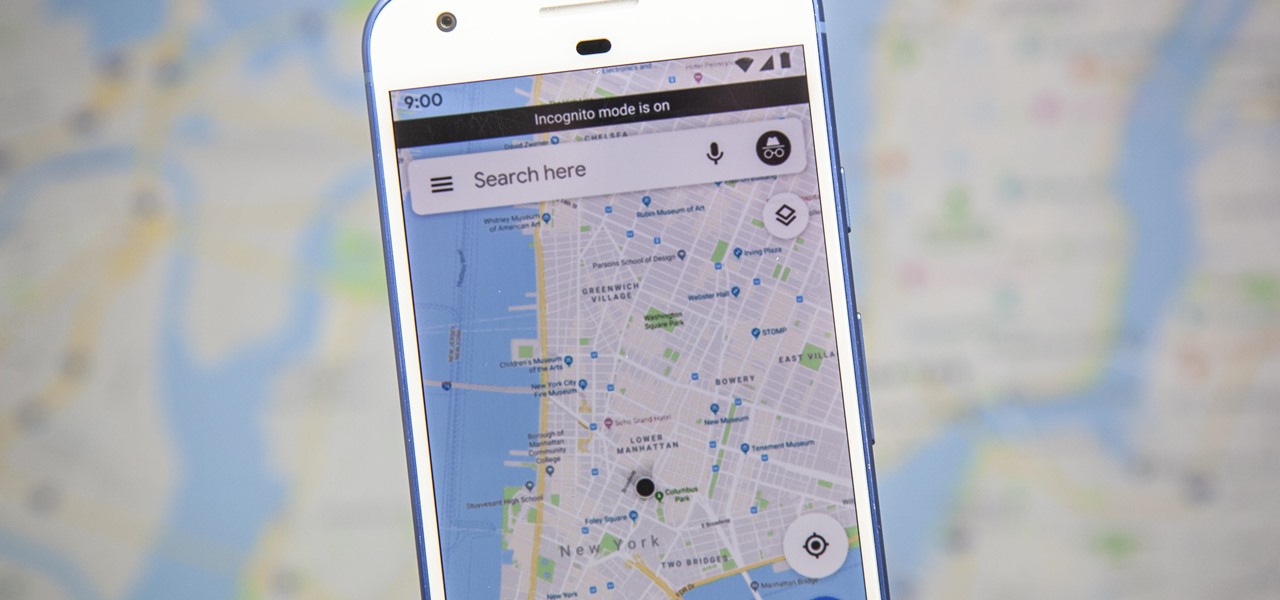
Google just recently added an incognito mode feature to Google Maps for iPhone and Android. With that, you can now use Maps in private at any time, which means you can browse and search with peace of mind.

Some of you may stick with your iPads, but for those looking for a similar Android version, you finally have a winner.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program.

Welcome to the 10th Community Byte session for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Null Byte is looking for forum moderators! Welcome to the ninth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the eighth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the seventh Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the sixth Community Byte for coding in Python and beating the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and essentially grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the fifth Community Byte for coding in Python and beating the challenges given to us from HackThisSite. These sessions are created to bring our community together, to learn from each other, and essentially grow together. Everyone is welcome, from novice programmers to aspiring hackers—even people that are nearly computer illiterate.

I'm most thankful for the simplest things in life...and how they can be so beautiful. Take this margarita I was sipping on a patio with my friends. Just a few friends, chatting...watching the people pass by on a busy street...the summer air so calm and relaxing....and the sip I'm about to take from this beautifully salted margarita. A relaxing moment in time. So simple, yet so precious to me.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Long ago some smart folks figured out how to make water, lava, and some blocks do the mob killing for them. More recently, with the addition of redstone, these mechanisms for resource collection have gotten rather complex.

It's great to see proof that Google+ is listening to feedback from their users. As a result of the discussion surrounding gender and privacy, Google+ Profiles Product Manager +Frances Haugen announced that Google+ will allow users to hide their genders on their profile.

Instead of watching one of the most cliché-ridden war movies of our generation (modelled after Spielberg's Saving Private Ryan), why not watch a really, really well-made documentary about the Oka crisis of 1990? Huh?

Want to keep an eye on your home while on vacation? Terrorize your family pet while at work? A homespun telepresence robot might be just the ticket! Luckily, thanks to shrinking hardware costs and the efforts of renowned hardware hacker Johnny Chung Lee, building a physical avatar has never been easier! Lee's robot has two important parts: an iRobot Create and a lightweight netbook running Skype. Notable extras include a wide-angle lens and a plastic stand to raise the computer to tabletop he...

Some really good tips in here, like using "private sale" sites or booking your flights on Tuesday.

THIS IS IN THE PALTALK PC TECH ROOM..

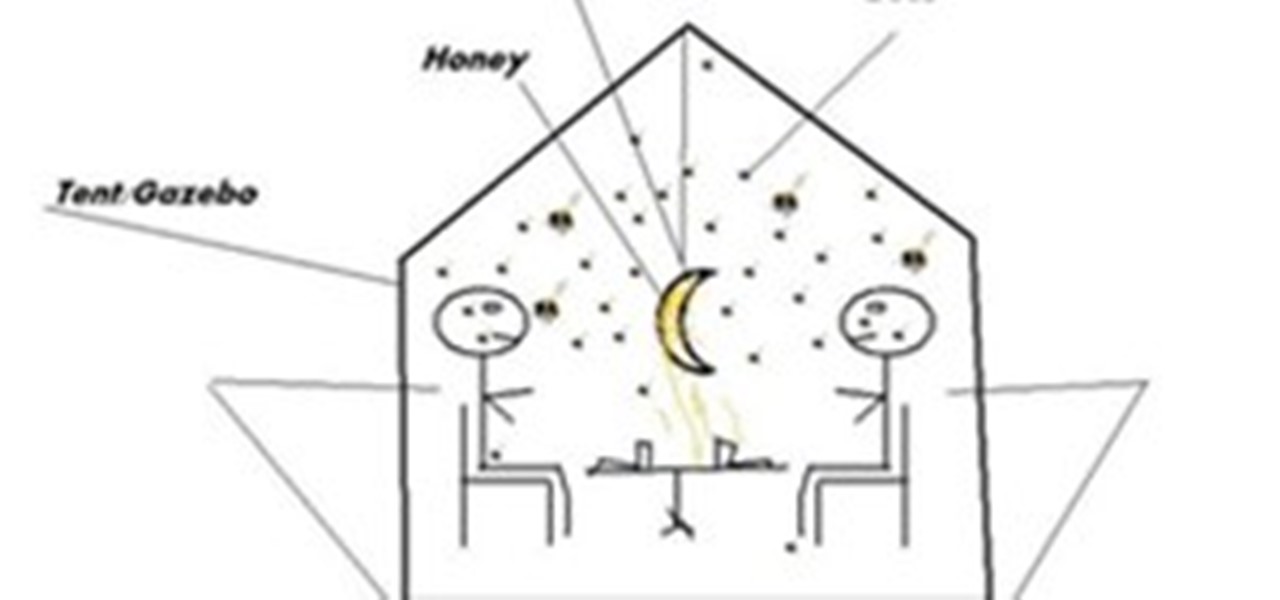
Spend all day together, laugh together, go on bike rides, go to the zoo, orgo on a romantic Honey Moon, all expenses paid.Set up your private location in a tent, gazebo, or a giant glass cube, anywhere completelysecluded, set up your table, two chairs, maybe some romantic musicpossibly a candle, whichever you desire, hang a fake moon in the middlelather it with sweet sweet honey, then add the last ingredient, see how long your lover can lastwhen the bees are added, this tests true commitment....

Would you glue fly legs to your eyelids? More or less stomach churning than gluing your eyelids to your...eyelids? (Shudder.)

Check out K 59 if you get a chance. North of El Zonte and Sunzal, it's a wave you want to check out.

BBC captured jaw-dropping HD super slow motion footage of surfer Dylan Longbottom in a 12 foot monster barrel.

The menstrual cycle can be very stressful and painful for women at times. This video will show you how to relieve menstrual pains using massage techniques. You will need to find a quiet, private area to do this. Massage away menstrual pain.

Skype has recently made some really great changes to their Android app that were once exclusive to softModders with rooted devices. Previously when Skyping, using your device for other tasks was impossible. Your entire screen was devoted to your Skype conversation.
Step 1: New User for Android System in Galaxy Note 2..Need Advice for How to Protect My Privacy

Prank Calls, Masked NumbersWho is calling your phone or your child's? Pranksters use a lot of tricks to make sure they can get on your nerves. Being able to trace prank calls is important because you're not going to learn much from your Caller ID, since most prank callers use an unlisted number - such as, a cell phone number. Many also use special code *67 to mask the number so your Caller ID will show "Blocked Number" or "Private Number". There are a lot of mild cases of so-called phone bull...

The art of creating Snapchat Lenses is really only the beginning of the augmented reality experience on the social media platform.

Is there a certain someone whose pictures and status updates you would rather not see? Like, ever? Wish you could hide a person on Facebook without publicly defriending him or her? Your new best friend is a Michel Gondry-inspired Google Chrome extension named Eternal Sunshine.

Many communities obtain their drinking water from underground sources called aquifers. If a surface water source, such as a river, is not available, water companies will drill wells into the soil and rock to a water source below. Some homes have their own private wells and must tap into the same ground water sources. In this video tutorial, you'll what aquifers are, how they work, why they are important and, of course, how to build your own model! Build your own aquifer.

Last week's social engineering phone calls were a blast. We made some friends, and even some enemies. We scored cheap food for some buddies, made some phone bills disappear, and even got a few people some free pizzas. So overall, it was a very successful night. In light of its success, I figured we'd all do another one!

This is the first official announcement for a new weekly activity on Null Byte for the community to participate in. Starting next week, depending on how much traffic we get doing it, we are going to start doing live social engineering calls via Skype. I've made a list below so that you can get a feel for some of things we'll try to accomplish in these calls.

Hardware hacks are something I feel we don't get enough of at Null Byte, so today I figured I would introduce a fun one. I've always been a curious hardware hacker. Taking things apart and learning how their internals work has always been a part of my nature. Quite some years ago, my father showed me a really cool trick on how to hack normal radios to scan frequencies that are normally non-listenable. This little hack allowed us to scan frequencies belonging to law enforcement, and even frequ...

Most people have had the unfortunate experience of not having a washer and dryer at some point. Apartments in my area tend to charge at least one hundred dollars extra for the units with washer and dryer hookups, and even more if you want a unit with an actual washer and dryer installed already. If you are young and just starting out, this may be hard for you to manage with your current salary. If you have no washer and dryer, the only alternative is the laundromat.

We love tearing apart security here at Null Byte. Several years back, upon returning items to Wal-Mart due to a malfunction, I noticed something very peculiar about the way their overall procedure goes. I brought the item up to the desk, and the woman asked if it didn't work, which I responded affirmatively. Without a moment's notice, she takes it right off to the defective items area and asks if I would like cash or store credit.