Now that more people are working from home on unsecured networks and personal devices, hackers are having a field day accessing everything from private browsing histories to personal banking information. A virtual private network (VPN) is the first and most important line of defense when it comes to protecting all of your devices from digital intrusions, but not all VPNs are created equal.
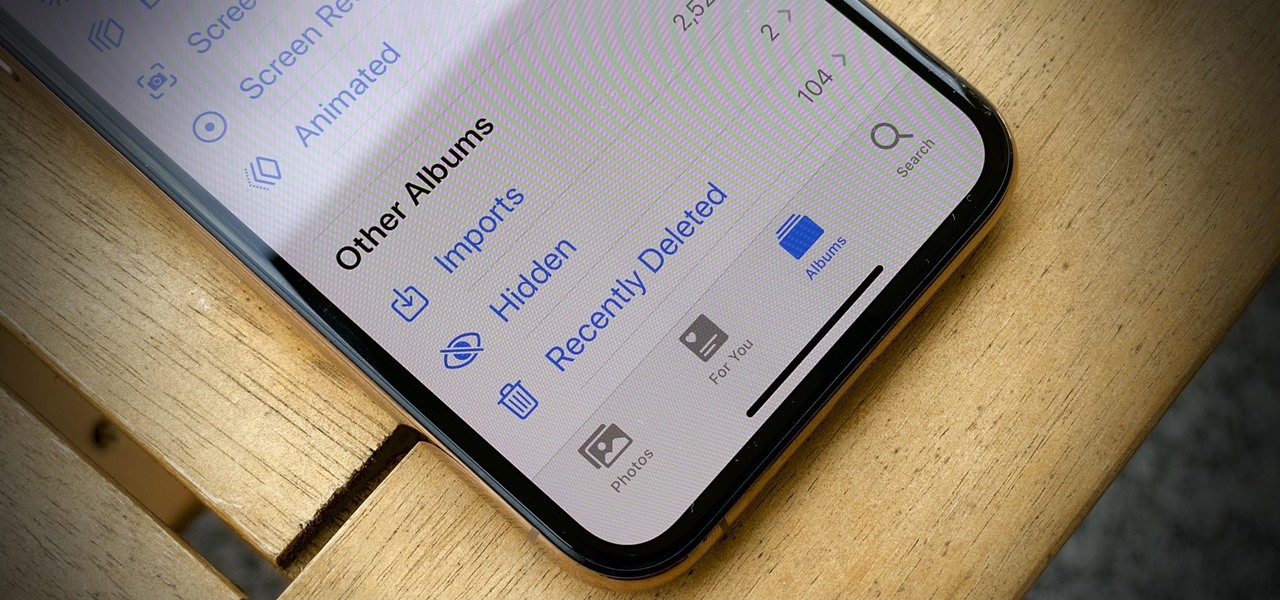
The "Hidden" album on your iPhone has always had one problem — it was never truly hidden. Since iOS 10, when the feature was introduced in the Photos app, any image or video that you conceal in the private folder could be seen by anyone with access to your unlocked device. Finally, that has changed.

Mobile privacy is one of the most pressing security issues in existence. Since we carry our phones with us everywhere we go, we need to ensure that we're safe from prying eyes.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

Spam calls are one of the most annoying things to happen in the world of smartphones for more than one reason. Not only are they bothersome, but they can also be dangerous to people who don't know any better. Google has come up with a crafty solution known as "Call Screen" to let the Google Assistant handle the call for you while you listen in on the caller like a stealth ninja.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

There once was a time in the Android rooting scene where we couldn't rely on using a custom recovery for all of our modding needs. Manual file flashing was very popular in the early days of Android before custom recoveries started taking over. With the rise of TWRP, it seemed like there was almost no need for manual file flashers; however, they appear to be making a welcomed return in a big way.

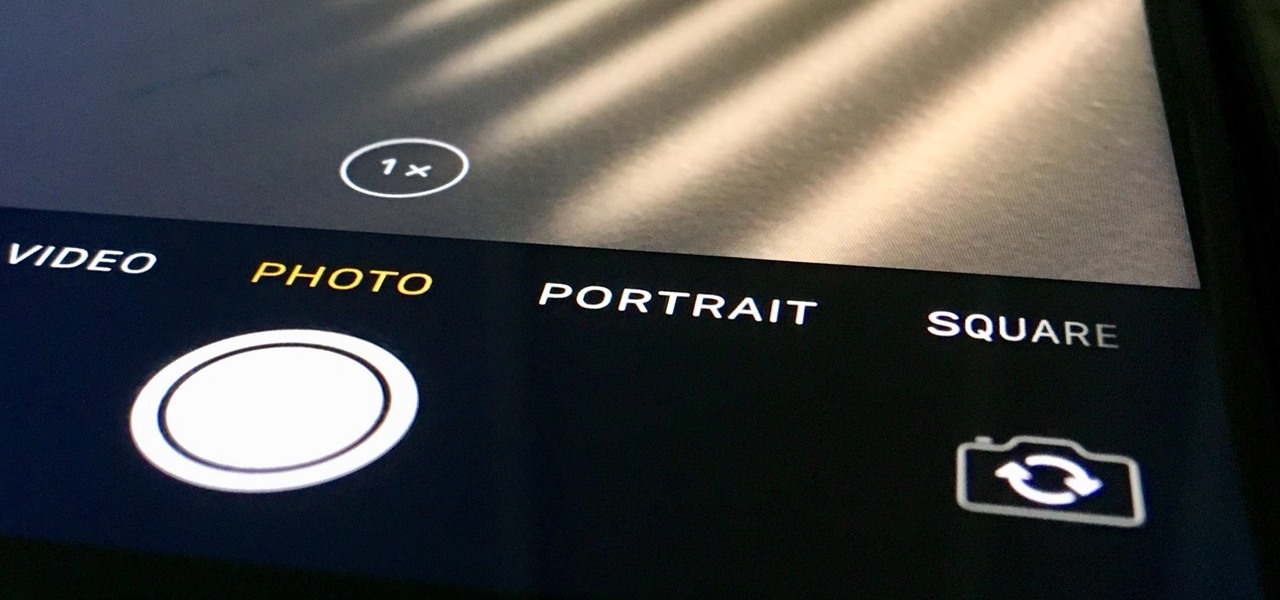
Even though your iPhone's Camera app is fast and easy to use, its default settings prevent you from immediately accessing any other shooting mode aside from "Photo" with "Live Photo" on and no filter applied. But there is a way to make the Camera app remember what you prefer the next time you open it up.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

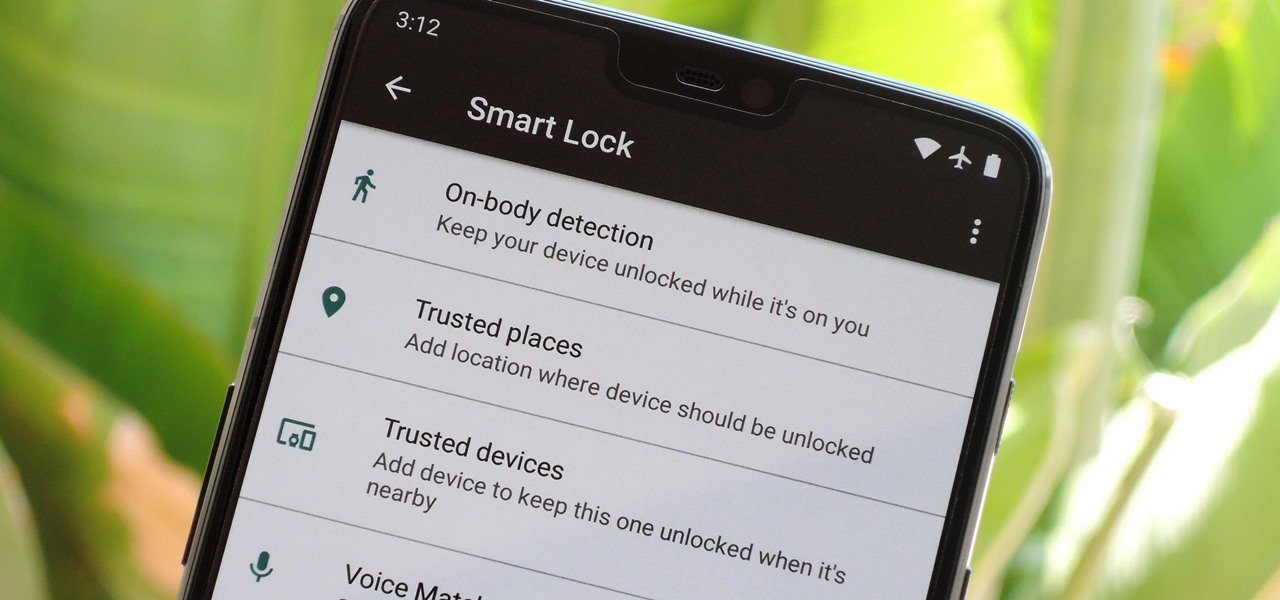
When it works, Android's Smart Lock feature is incredible. There's no need to enter your PIN when your phone "knows" it's in your hands — just unlock and go. But Smart Lock, particularly its Trusted Places feature, can be finicky sometimes.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

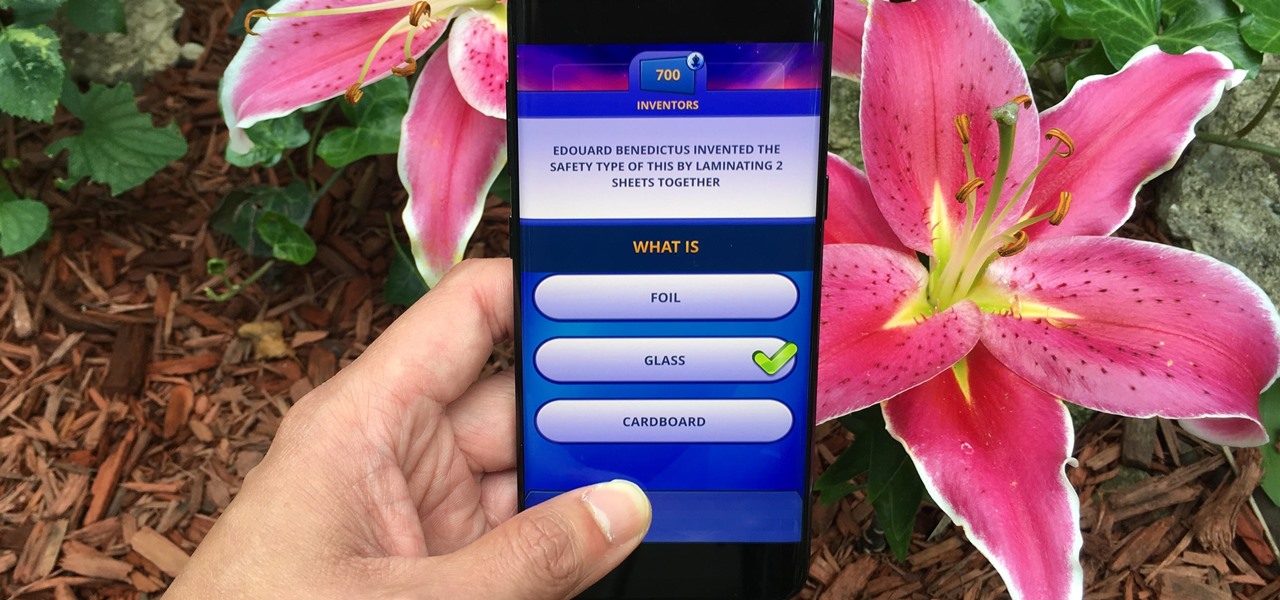
Trivia games are a great way to test your knowledge and learn about people and things you never knew of before. They're ideal in a group setting because they can serve as the perfect conversation starter when you're enjoying time with friends, family, or even complete strangers.

Last June, Meta began shipping their Meta 2 mixed reality headset, to the delight of many. In September, it was announced that shipping had been delayed until the end of the year. Then it appeared that Christmas would bring something magical when Meta sent out an email four days before the big holiday saying that the Meta 2 developers kits were finally shipping. Unfortunately, having a few on order here at Next Realit,y we are still patiently waiting for ours to arrive.

Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basically, whatever you can afford.

I've been an iPhone user in the iOS ecosystem for years now after a brief stint in the Android realm. But, I'm also enthusiastic about varying forms of technology in general; I realize that iOS is far from perfect and that healthy market competition is beneficial for all. So, naturally being curious about other platforms, I decided to take Windows Phone for an extended trial run.

Your slow cooker isn't just for making lunch and dinner—it's also perfect for making a complete and super delicious breakfast with little work.

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.

When it comes to security, there are usually only a handful of things that you want protected from prying eyes on your iPhone—private photos, scandalous videos, and important text, such as credit card and social security numbers.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Old habits die hard. It may be a cliché, but it's undeniably true, especially when it comes to the bad ones. Nail-biting, fidgeting, and overspending can label you as someone who is obsessive-compulsive, overly nervous, and routinely stressed out, but you can make the break less painful with a few simple tweaks to your routine and by understanding how your habits work.

Unwanted advertising is everywhere. Annoying pop-up ads, overly loud late night commercials, spam...it never ends. And before spam, there was junk mail. Junk mail is even worse because unlike TV commercials and internet ads, it's physical. You can't just delete or ignore it—and it's an awful waste of paper. So what can you do about it?

Firstly, let me say a few quick things: Once built, this is a lazy (one button) way to harvest melons, but this is going to be a complex and lengthy build.

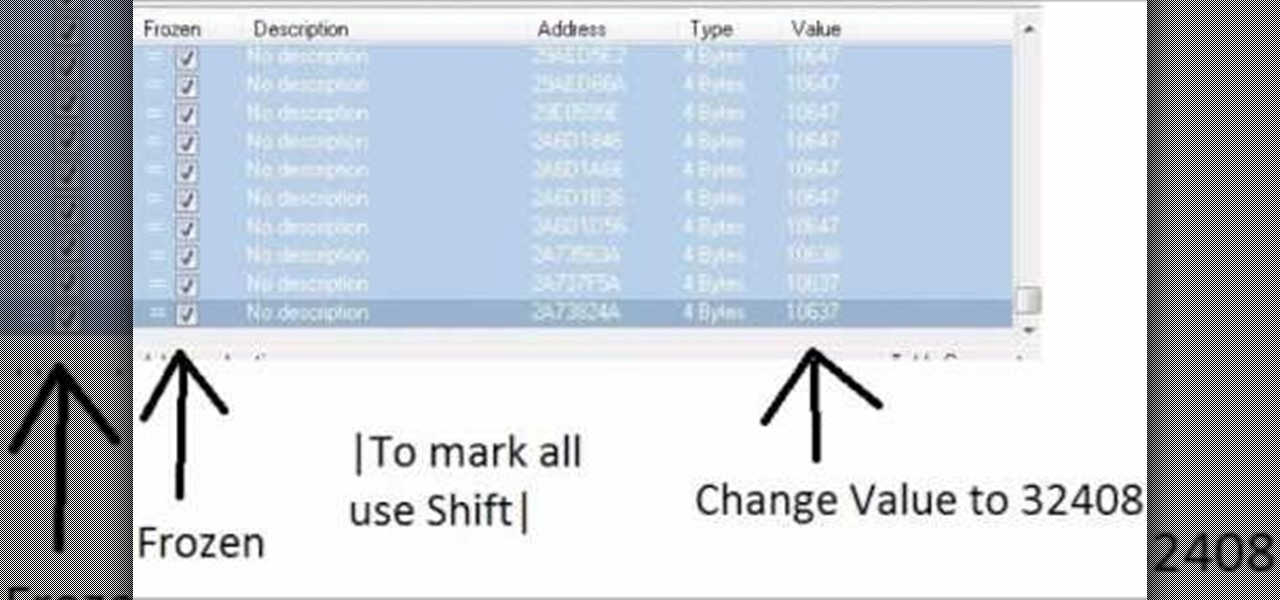
Increase your damage output in World of Warcraft! This tutorial won't work on all servers, and is better on private servers than public. All you need is Cheat Engine - buy some mundane items, and then use the program to turn them into rarer, better items.

How far would you go to save your life? For James Franco, who plays real-life hiker Aron Ralston in Danny Boyle's "127 Hours", staying alive means cutting off your own arm with a dull pocketknife. If you've seen the movie (or even heard about all the people who fainted and threw up after watching it), you know that it presents one of the most grueling self-amputation and bone breaking scenes in movie history.

First of all you need some basic tools like sewing machine, scissors, pins, ruler, measuring tape and thread. You also need a printed knit of size 1.5 yard or 1.4 meters ad a separating zipper of size 18 inches or 46 cm. First you have to start by making the straps and bodice. Cut off two rectangles those measures from the top of your bust to the bottom of your bust. The length should be enough to go all the way around your upper half. Place these two rectangle pieces together. Now separate y...

You don’t have to eat meat to get all the iron you need. There are many very iron rich vegetables that can be eaten on their own or juiced and drank to make sure you have appropriate amount of minerals in your blood.

Want to play your video collection on any media extender, console or AppleTV? Step one is to get your movies off of the DVDs and onto your hard drive! If you're like most people you probably have a huge library of DVDs that you've bought and collected over the years. Unfortunately, it's an inconvenient format if you want to playback all that content anywhere around the house. So, learn how to rip and encode that stack of DVDs into a format that you can play on your Windows Media Extender, set...

How to summon Illidan in World of Warcraft. This only works on a private server.

This article is a guide for making Chainmail Armor from start (simple wire) to finish (a finished chainmail shirt). We will be using the European 4 in 1 weave, as this is the most common weave. This is the weave that you usually see in movies. There are several sections to this guide: Materials, Making the Rings, Weaving the Rings, and Making the shirt.

This how to video will give you ideas on how to make a sandwich that looks like a sailboat. Preparing this sailboat sandwich is a fun activity to do with kids. Watch and learn how it done.

Florist Jodi Shalgosky takes us through the choices you have when choosing your wedding flowers and shows us some beautiful, but different, bouquets and table arrangements. Watch this wedding how-to video and let Brides Magazine give your more tips and inspiration for your wedding flowers.

James Bond's alcoholic drink of choice might have been a shaken, not stirred martini, but the 007 (double O seven) is a sweet vodka, 7-Up, and orange juice cocktail. Learn how to make a 007 cocktail by watching this video beverage-making tutorial. Here's a hint, fast forward through the first minute of bloopers and start making this cocktail right away.

Stains on your shoes and bags can diminishes your wardrobe choices. So watch this how to video to learn how to remove nasty stains from your shoes and bags with a once simple ingredient. Our host will teach you how to use nail polish remover to clean the inside or your shoes. Try not to use tissue as they tend to absorb too much of the solvent too quickly and not leave any for the stains.

Have you ever heard of cricket? No, we're not talking Jiminy Cricket or the wireless cell phone service provider. We're talking about CRICKET. The team sport, nicknamed "the gentleman's game," is the popular sport of choice in places like India, Australia, South Africa, Sri Lanka, England, Pakistan and Zimbabwe, though not America. But guess what? It's very similar to the American pastime we all love so much— baseball.