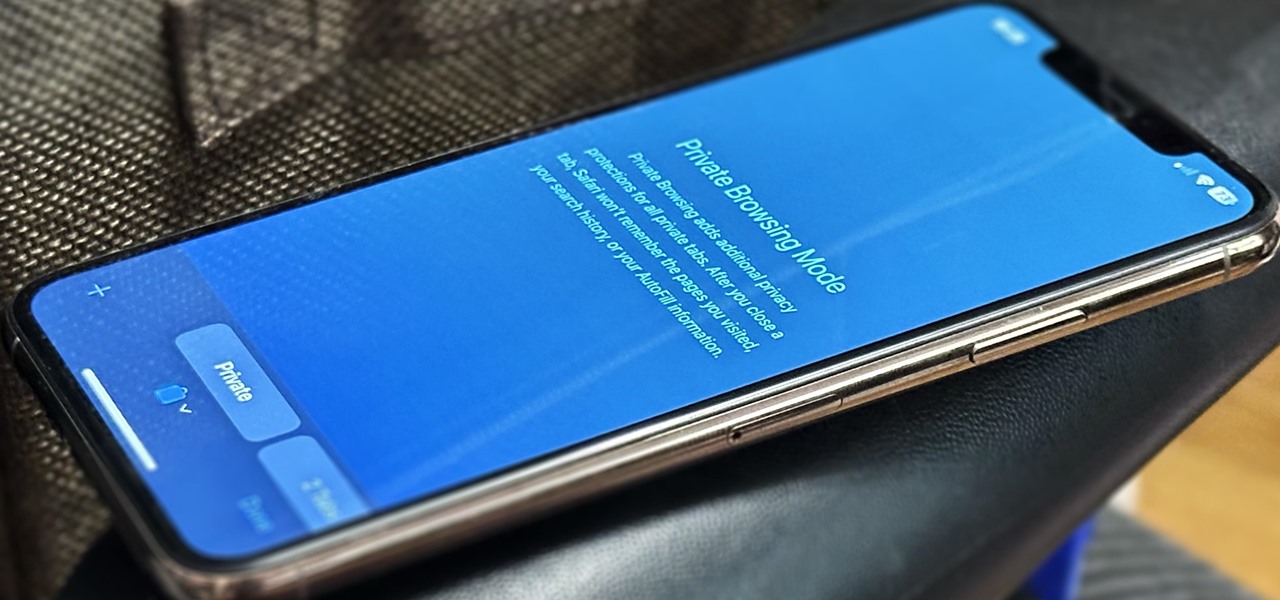
Private Browsing mode finally lives up to its name in Apple's huge Safari 17 update for iPhone, iPad, and Mac. So whether you search for things you don't want anybody to know about or want to ensure websites and trackers aren't eavesdropping on your activity, you'll want to update your devices pronto.

Augmented reality and computer vision company Blippar has a new lease on life, as previous investor Candy Ventures has completed a successful bid to acquire the assets of the beleaguered company.

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...

We may or may not see Apple's long-awaited take on AR smartglasses this year, but the company is more than getting its practice swings in with its current wearables business, which hit record revenue in 2019 according to financial results released this week.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

Increasingly, cutting-edge platforms like blockchain technology and augmented reality are overlapping, forging new digital frontiers that promise to change the way we interact with the virtual and the real world.

Developers and enterprise customers chomping at the bit to get their hands on HoloLens 2 may not have to wait much longer, as Microsoft passed one of the remaining hurdles needed to release their new tech into the wild.

Many apps, including Facebook, Twitter, and Facebook, do not let you download videos, even if they are living on your own account. Saving these videos usually requires a third-party app or screen recorder, which is inconvenient and can result in loss of quality. However, TikTok, the newish popular short-form video platform, makes it easy to download videos — even if they're not yours.

While these days it is better known for the cross-platform gaming sensation Fortnite, Epic Games also makes Unreal Engine, one of the top development environments for 3D content and, in turn, augmented reality and virtual reality experiences.

A sizzle reel just released by augmented reality cloud company 6D.ai shows off what kind of hyper-realistic AR experiences developers can build with its SDK.

Location-based gaming pioneer Niantic has offered a preview of its augmented reality cloud platform that could change the immersive content game yet again.

Magic Leap's recent flurry of patent applications prompted us to look around for any trademark movements from the company, and it turns out that the Florida-based company has been quite busy.

With Instagram's archive feature, we have the pleasure of hiding all our stupid photos of #gettingcrunk from back in the day. This wonderful new IG feature will still allow us all to cherish those embarrassing moments in our life, yet hide them from those people we hope would never scroll so far down.

If you have personal information stored on a Kindle Fire tablet, be warned that Amazon has removed encryption support for Fire OS 5. So if you have stuff on these devices...maybe a risque book, or private notes, or pictures you'd rather not let out to the world, now would be the time to remove them. And unless Amazon changes its mind and re-enables encryption, don't use your device for anything personal, as anyone who gets a hold of it will be able to gain access to everything on it.

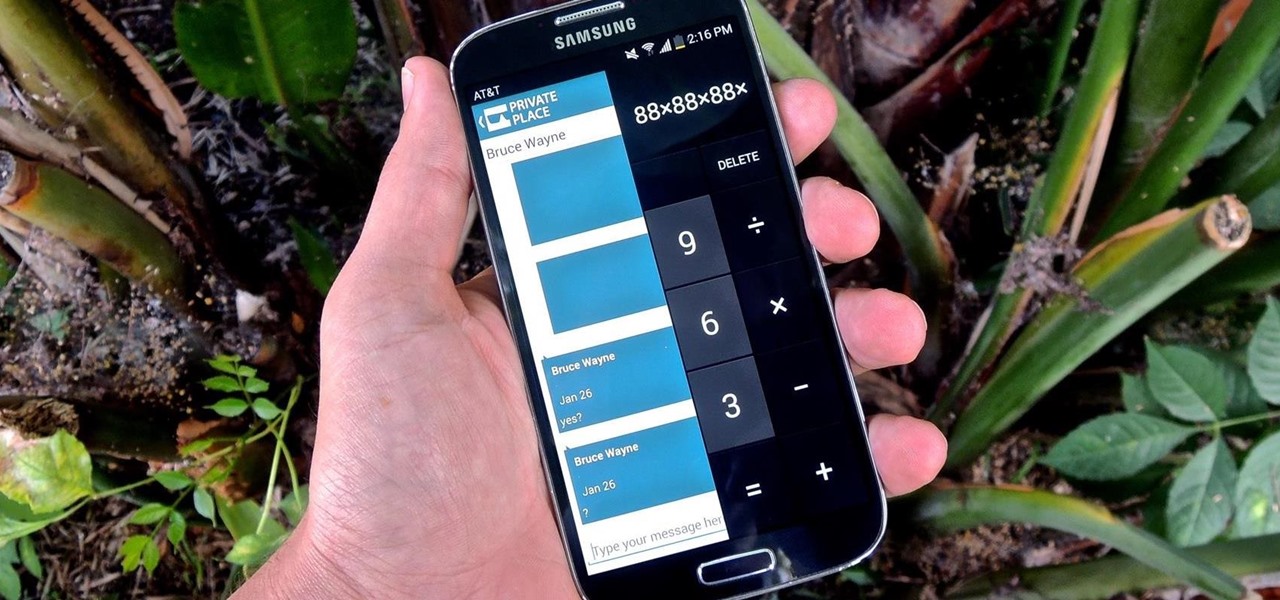
Whether you're a secret spy or just a regular person with a few secrets, you may want to keep certain information on your smartphone private, and it's totally possible on Android to do so.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

1. Describes how to setup a VPN connection on Windows XP. 2. Goto Start-> Control Panel-> Network connections.

In this video, you'll use Scope and create a simple calculator while learning a little about private, public and protected properties in OOP programming. If you're looking to bone up your PHP coding skills you'll want to check this video out.

If you're Apple computer needs a little cleaning, not the hardware, but the software, then MacKeeper is the way to go. This application will help protect your hard drive from junk and other useless data, freeing up much needed space on your Mac. Also, you can recover files, hide private files, clean up your login items, apps and plugins, and more! Watch this video to see how to use MacKeeper.

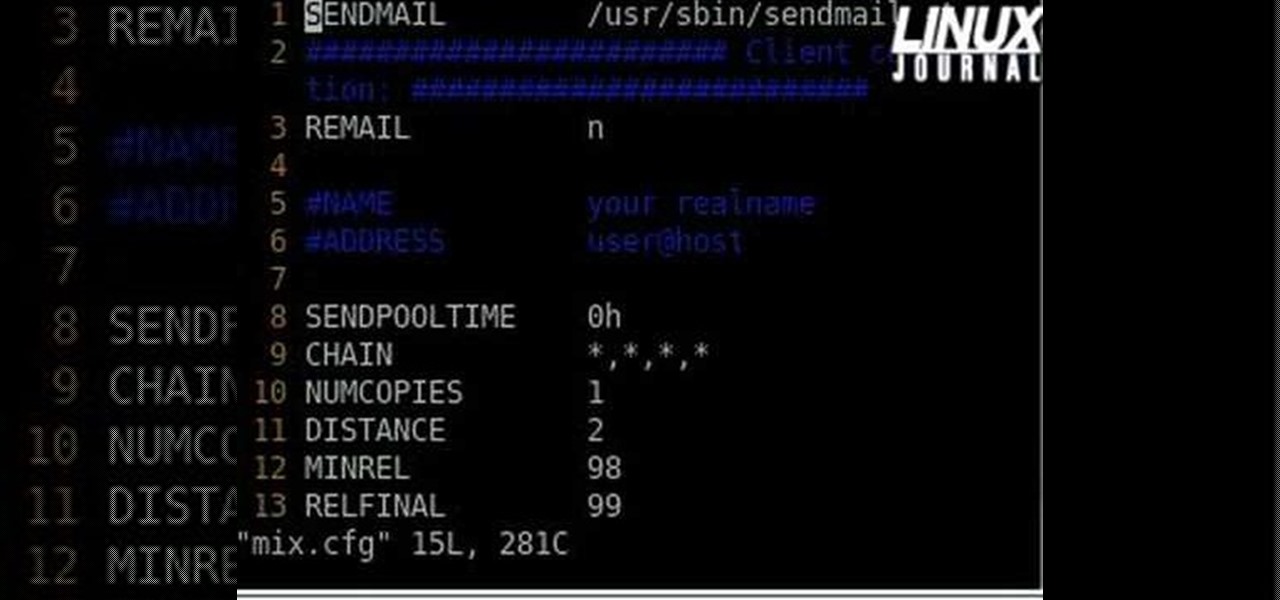
Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.

If you're using the Private Browsing feature in Safari, you'll still need to do more to keep your surfing history secret. This helpful software video tutorial shows you how to cover your tracks in the Apple application Safari.

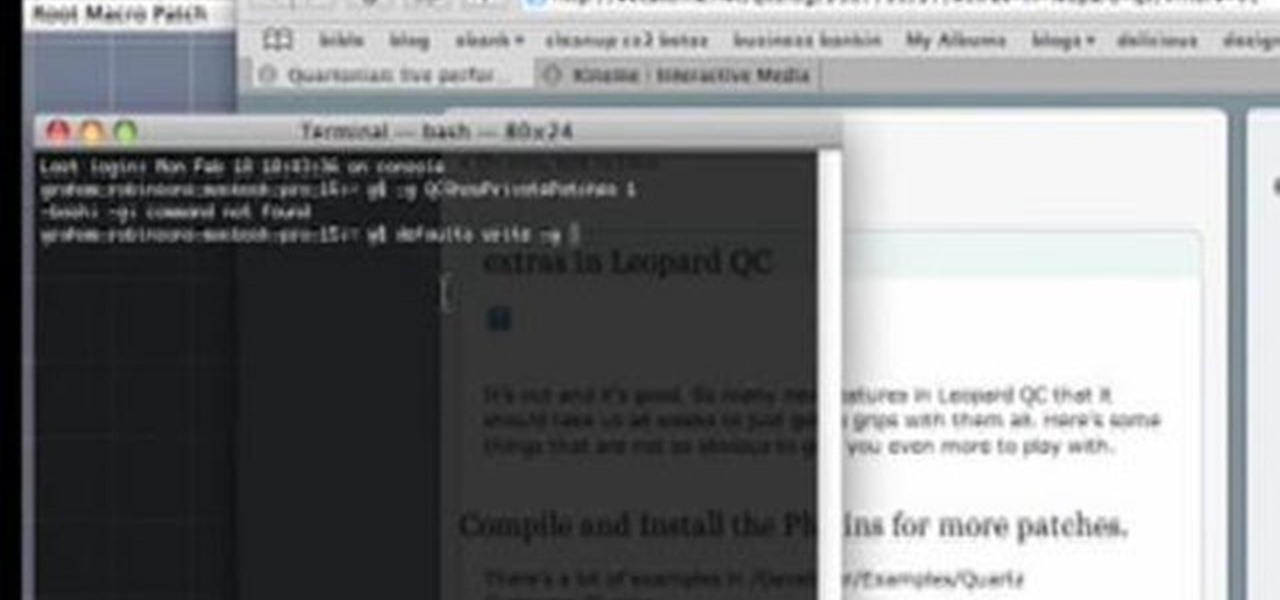
This is a very basic introductory video that teaches you how to successfully install Quartz Composer on your MAC OSX 10.5 Leopard. Quartz Composer is a node-based graphical data software that uses visual programming language. Built exclusively for use on the MAC OSX, it's a handy software for graphic designers.

Look, we all like getting things for free. That's why we can stomach things like advertisements and optional purchases in freemium apps and games — we're willing to pay for our mobile experiences in every way but currency. Although freemium seems to be the model for the future of iPhone entertainment, it looks like a different scheme might win out in the end.

Uber's year is going from bad to worse, and they may be subject to a potential criminal probe in the ongoing Waymo legal battle.

A federal judge wants answers after an Uber engineer accused of data theft pleaded the Fifth in the ongoing Waymo versus Uber battle. This privilege would protect the accused, Anthony Levandowski, of self-incrimination and handing over specific documents demanded in a previous subpoena and forthcoming deposition.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

Make sure your private documents are completely secure. This episode by Tinkernut deals with not only encrypting your files, but also hiding them in a hidden volume.

The people of Iceland forced their corrupt government to resign. A public assembly was created to rewrite the constitution.

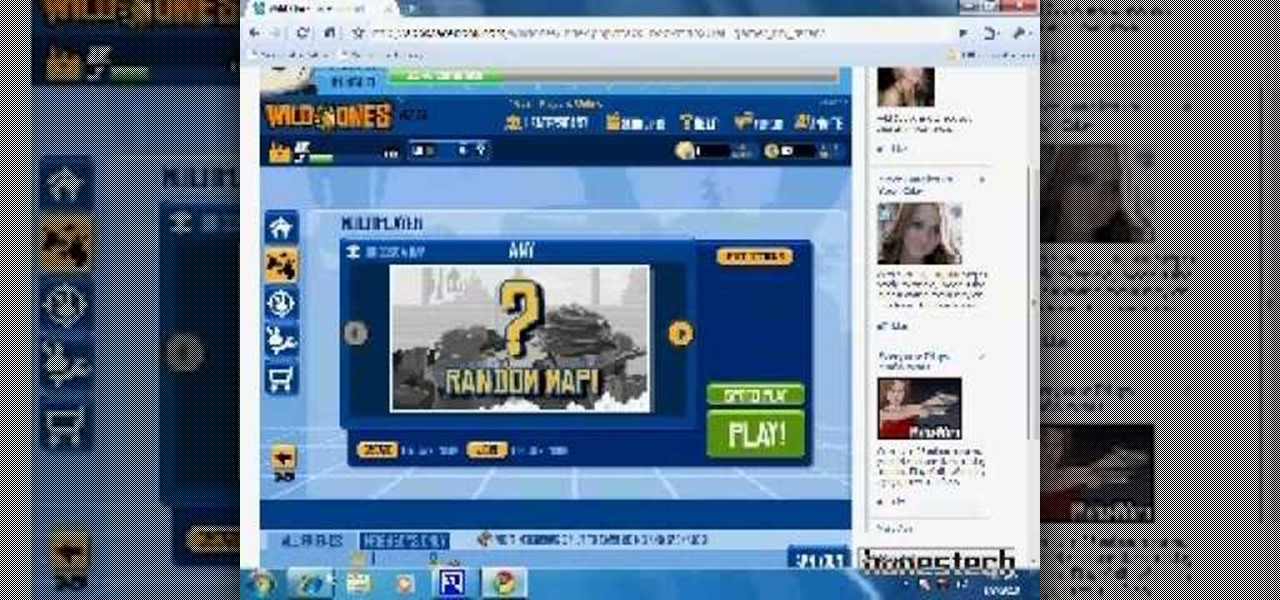
Do you find yourself getting rocked by your friends and relatives whenever you play Wild Ones on Facebook? A little more money would help right? This video will teach you how to use an easy cheat to acquire a theoretically infinite amount of money and coins. All you need are two Facebook accounts and two different web browsers and you can do this easily. Now get in there and buy yourself a better pet!

Tim and Kevin meet up/hang out & talk their talk. They discuss buying domain names, choosing business names, starting companies, and selling books by their color. These two entrepreneurs have lots to teach us about selling ideas and making profitable businesses.

In this tutorial, we learn how to sound like a biological woman while speaking. There are many different techniques to help you speak like a woman, including going into falsetto. This isn't about getting the sound, it's about learning how to not speak with resonance. You want to focus your voice up in your throat instead of deep down. You probably haven't used the muscles for this voice, so using falsetto is a great way to practice. You may be able to speak a few minutes and feel yourself fal...

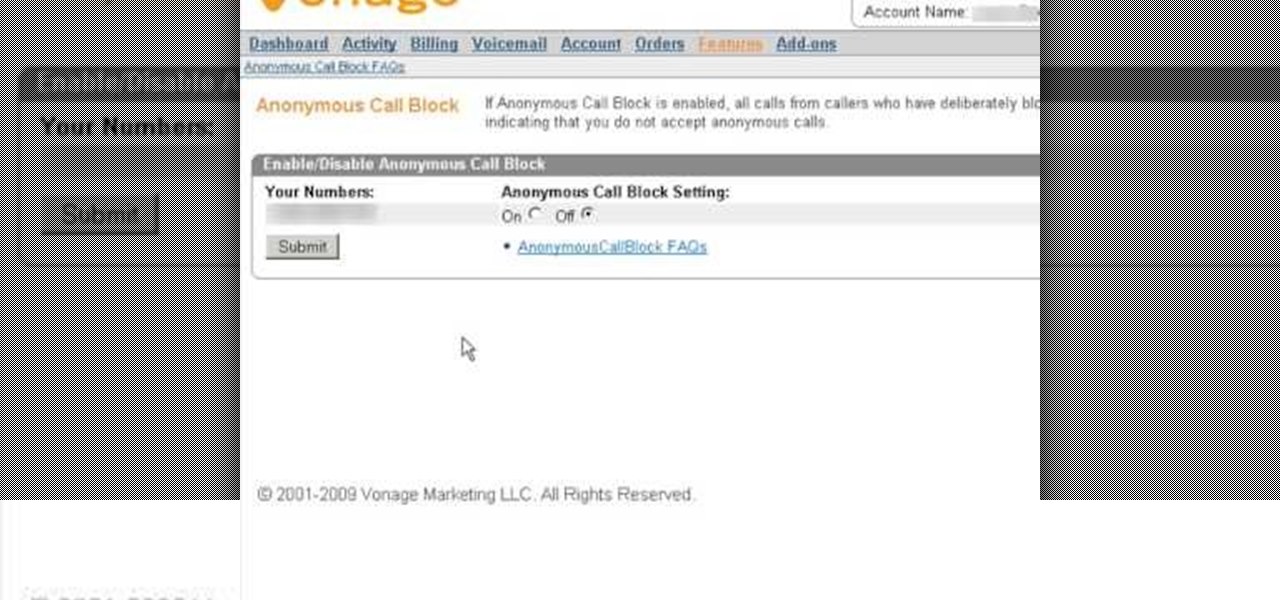
If you are looking for a way to prevent telemarketers and nothing else is working, consider signing up for Vonage's call blocking feature. In this tutorial, brought to you straight from the professionals at Vonage, learn how to set your phone to block any incoming call without a number attached to it.

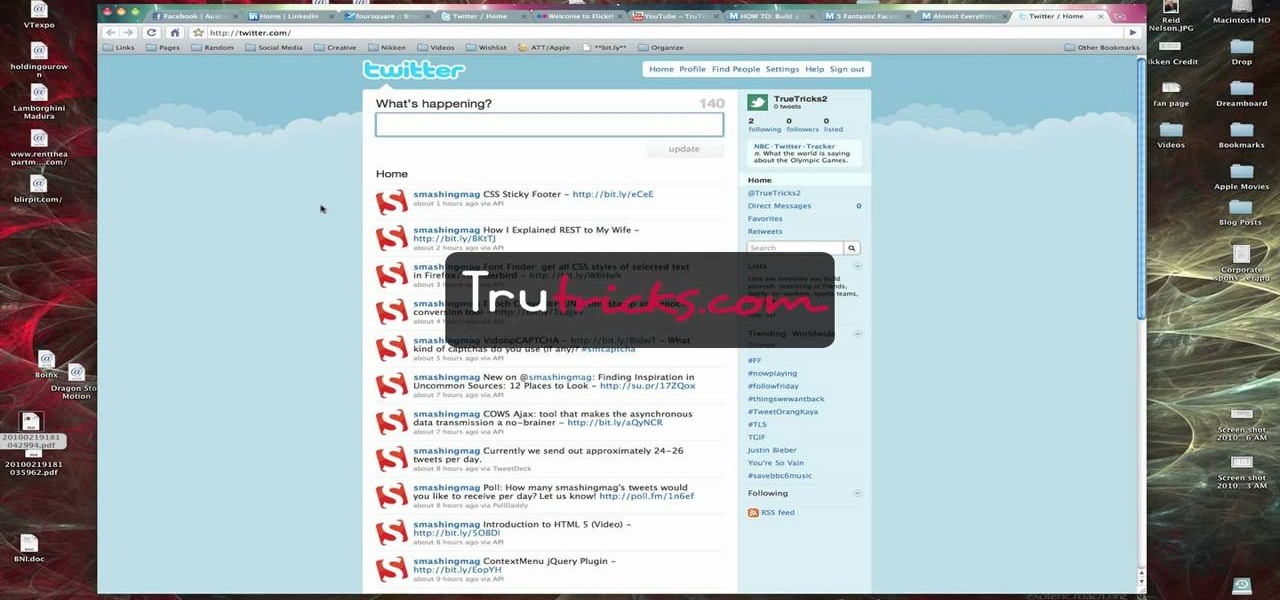
Brian explains us how to use Twitter, one of the best social media networks out there. One thing to notice is that Twitter allows you to send text messages up to 140 characters. In the right corner you can see you account name and your avatar which can be changed from the settings menu. Twitter allows you to follow people and be followed by people. Basically when you follow people you will be able to see messages they post and when people follow you, they will see what you post. Twitter is a ...

Need help with Satellite Uplinks in Battlefield: Bad Company 2 on the Xbox 360? Jack and Geoff from Achievement Hunter give you this two-part video guide on finding all 24 M-Com Stations. In the first video, see the locations of the first 12 M-COM Stations that you must explode for great glory! Part two of this tutorial reveals the last 12 locations, along with the location of the Holy Grail. They also finally break that barrier and hug each other. And they also pick up the Complete Blackout ...

Check out this guide to Battlefield Bad Company 2, the mission entitled Zero Dark Thirty. Find the M-Com Stations and destroy them, but stay alert for all enemies. Watch this video walkthrough to learn how to complete the Zero Dark Thirty mission in Bad Company 2 on the PS3.

Things are really heating up now with that the Russians are putting on the pressure in Battlefield Bad Company 2. This time your helicopter gets hit by an RPG and you need to put it down and make your way through the clearing in the jungle. Destroy all the M-Com Stations, and nobody can die. Watch this video walkthrough to learn how to complete the No One Gets Left Behind mission in Bad Company 2 on the PS3.

The first thing you need to do in this mission on Battlefield Bad Company 2 is to hop out of the copter and get in the sand buggy and head to your marked location. You'll need to locate and head to each station on the map: Bravo Base Station, Charlie Base Station, and Alpha Base Station. After that, complete the Triangulation Point. Watch this video walkthrough to learn how to complete the Sangre Del Toro mission in Bad Company 2 on the PS3.

Some of the new features in iOS 15 take some getting used to, and the biggest one of those is Safari's relocated search bar, aka address bar. There are more than a few reasons why it's a jarring change, but the good news is that you can return Safari's search bar to its pre-iOS 15 position at the top of the screen.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.