If you want to use your iPhone with another carrier, all you have to do is contact the original carrier to request an unlock, which is usually granted in a few days. Unfortunately, you need to meet specific criteria to officially carrier-unlock your iPhone, like paying off the device in full and completing any contracts. But that doesn't mean there isn't a workaround you can use beforehand.

Using a passcode on your Apple Watch is a good way to keep other people out of your data, but what happens when you see that "Wrong Passcode" screen yourself? You can, of course, try again in a minute, but if you've forgotten it for good, there's still a way to get back into your Apple Watch.

Apple's own Photos app received some pretty amazing updates in iOS 11, but does iOS 12 have what it takes to one-up last year's Photos improvements? We think so.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

Setting up Face ID is simple, but getting it to work correctly every time is a different story. While there are numerous tips for getting Face ID to work every time you need it on your iPhone X, XS, XS Max, or XR, Apple has added a better option in iOS 12 that lets you add an "alternative appearance."

The Augmented World Expo is winding down in Santa Clara, where Qualcomm, Vuzix, and Meta Company were among the companies making big announcements.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

Apple's next big developer event happened on June 4, and it was the first glimpse of iOS 12 that anyone's seen. While there were lots of rumored features to be unveiled at WWDC 2018, Apple concentrated mostly on squashing bugs and making iOS work as seamless as it did years ago. Still, we had hoped that Apple would have added these features in iOS 12, but only a few made the cut.

With the change to a glass back, many of us are concerned about the durability of OnePlus 6. While glass does offer some benefits such as lighter weight, without proper reinforcement, it can easily shatter in one drop. Now we have our our first look at its durability thanks to JerryRigEverything.

When traveling or sightseeing, you may come across a landmark you can't quite identify and want to know what exactly it is and the history behind it. It could be a building, waterfall ... anything. If there are no signs around or they're in a different language, you'll have no idea what you're looking at. Fortunately, Google Photos can be your personal tour guide with the power of Google Lens.

Augmented reality is expected to eventually change everything, and the prevailing view is that those changes will be for the better. The converse view, however, is that the technology will further erode privacy.

You really can't beat Google Photos. Not only does it give you free unlimited cloud storage and let you search for almost any object in one of your pictures, but it also packs a few powerful editing tools. Among these is a dead-simple way to create your own animated GIFs out of any set of pictures.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

A funny thing happened on the way to the release of the virtual reality epic Ready Player One — augmented reality grabbed a major piece of the spotlight. Specifically, Microsoft's HoloLens.

Unless you own an Exynos model, there won't be much development on the custom ROM front for the Galaxy S9. But that doesn't mean you have to put up with all of the UI quirks from Samsung Experience (née TouchWiz). With a little work, you can give your S9 a stock Android makeover, even without root.

In one of the worst-kept secrets of the upcoming Mobile World Congress, Google has officially released ARCore on the Play Store for owners of the latest flagship Android smartphones.

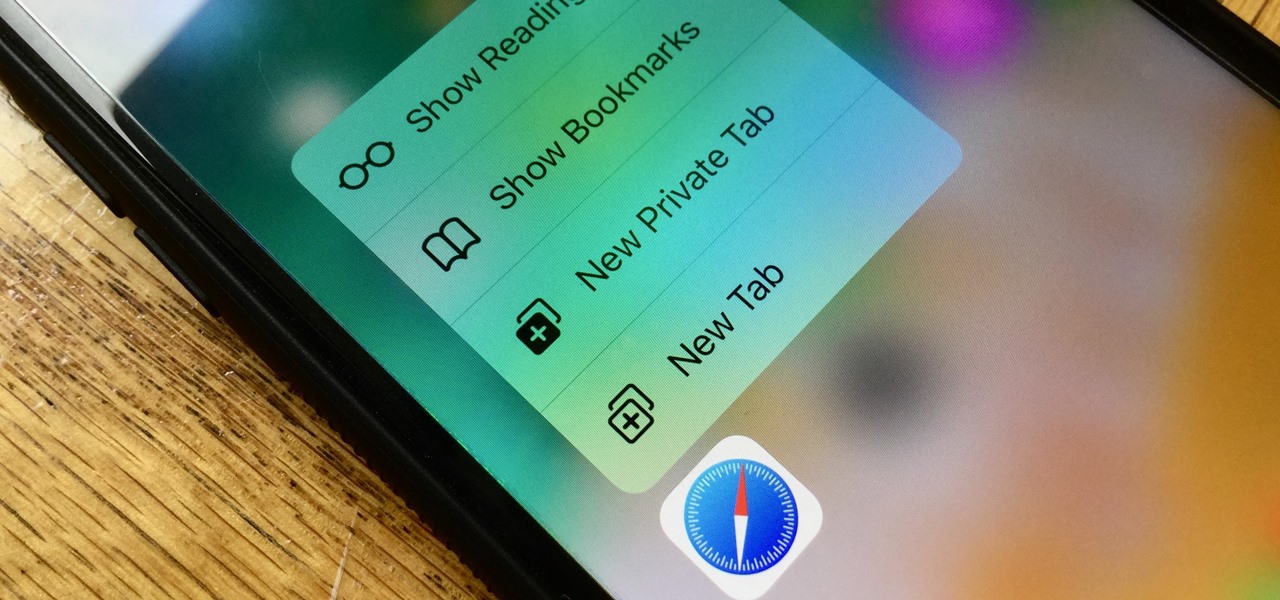
Introduced on the iPhone 6s, 3D Touch is just about the closest thing to a "right-click" that we have on iOS. Apple and app developers utilize this feature to give us helpful options that might otherwise clutter the overall app experience, as well as opportunities to "peek" into an action without committing to it. Safari on iPhone is no exception.

No matter your reasons, you might need a second phone number that's a little more disposable than your primary number — a "burner" number, so to speak. If you create this burner number using Google Voice, you'll get new functionality like call forwarding and voicemail transcripts, and best of all, it's completely free.

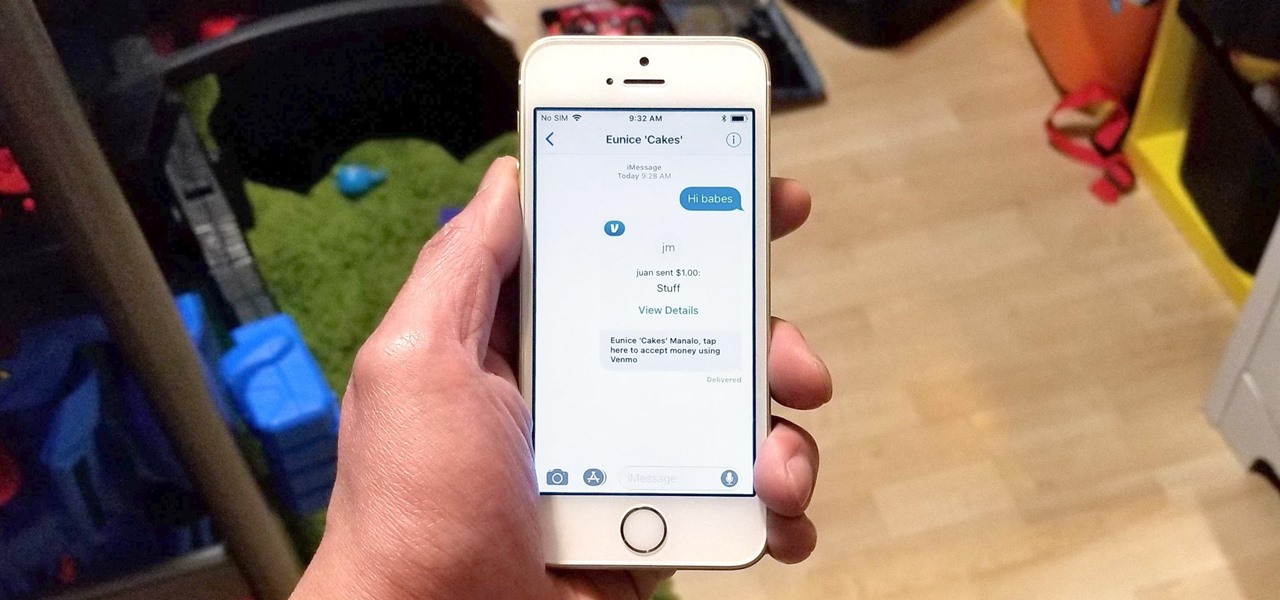
Venmo makes it incredibly convenient to send money to friends and family, and it all happens instantly from the comfort of your smartphone. Even better, if you have an iPhone, Venmo lets you conduct transactions straight from the default Messages app, giving you more flexibility and convenience over Android users.

Nova Launcher is one of the most popular apps on the Play Store thanks to its rich features and fluid navigation. But one downside that comes with this abundance of features is that much of Nova's functionality is lost on the masses. Fortunately, I've used Nova for several years and learned a few tricks along the way.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

Scanning important paperwork on smartphones is a tedious process, often relying on either external scanners or third-party apps that had to be either purchased or were loaded with annoying ads just to get the job done. Thankfully, iOS 11 now lets you easily scan documents using your iPhone, and finally does away with the need for third-party apps or machines.

In the US, law enforcement officials can make you unlock your smartphone with a fingerprint, but they can't force you to input a password or PIN, which would violate your Fifth Amendment rights. To help you from ever being in a scenario where you're forced to put your finger on the Touch ID sensor, Apple has a built-in way for you to disable biometrics on your locked or unlocked iPhone in mere seconds.

For the first time, the US Food and Drug Administration (FDA) has approved medication to treat children with a serious infection called Chagas disease, which stealthily infects and damages the hearts of millions of victims a year.

Whether or not a microbe is successful at establishing an infection depends both on the microbe and the host. Scientists from Duke found that a single DNA change can allow Salmonella typhi, the bacteria that causes typhoid fever, to invade cells. That single genetic variation increased the amount of cholesterol on cell membranes that Salmonella and other bacteria use as a docking station to attach to a cell to invade it. They also found that common cholesterol-lowering drugs protected zebrafi...

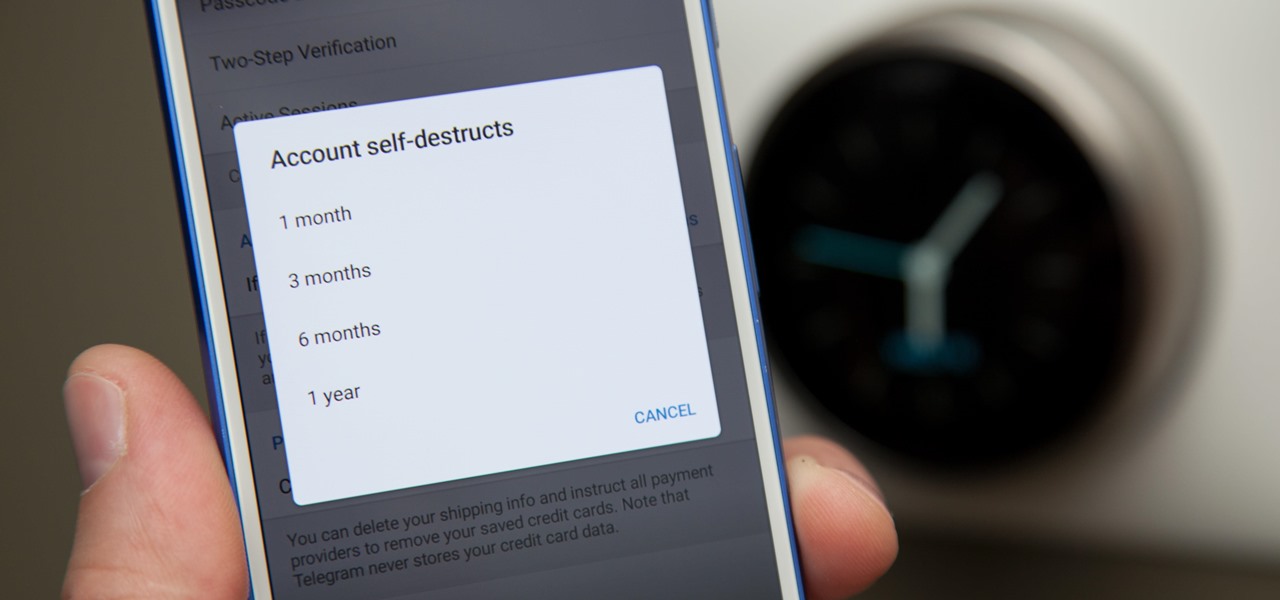
You can send self-destructing messages in Secret Chats, but that's not the only thing that can destroy itself in Telegram after a specified amount of time. Your whole account can disappear after a certain amount of inactivity, so it's important to adjust these settings to give you more time or to kill your account even quicker.

Unless you're a WhatsApp pro user, you may be surprised to know that there are text formatting options that you can apply to your messages. Markdown characters can help you emphasize certain words or phrases by making them italicized or bold, and it'll even let you cross out words and change the font. It's one of those nice touches that isn't available in most other messaging apps.

So cute, so furry, and so chock full of parasites. While raccoons are fun to watch, they are neither friendly nor clean — and they can make you sick in more ways than one.

Regarding foodborne pathogens, eating fish is not as hazardous as it was a few years ago — but if fins are on the menu, it's good to have a heads-up about what's good and what's bad these days.

Elon Musk's SpaceX is launching the world's most powerful rocket. The Tesla founder and CEO says the company is about to go through "manufacturing hell" to make delivery schedules for its new Tesla 3. Somehow, Musk says Tesla will offer Level 5 driving (so you can take a nap while your car drives you to and from work) within two years.

Gonorrhea infections reached a peak in 1975, then decreased until 2009, when infection rate started rising and has increased each year since. With the rise of antibiotic resistance, those numbers are only going to get worse — unless we find new treatments against the bacteria.

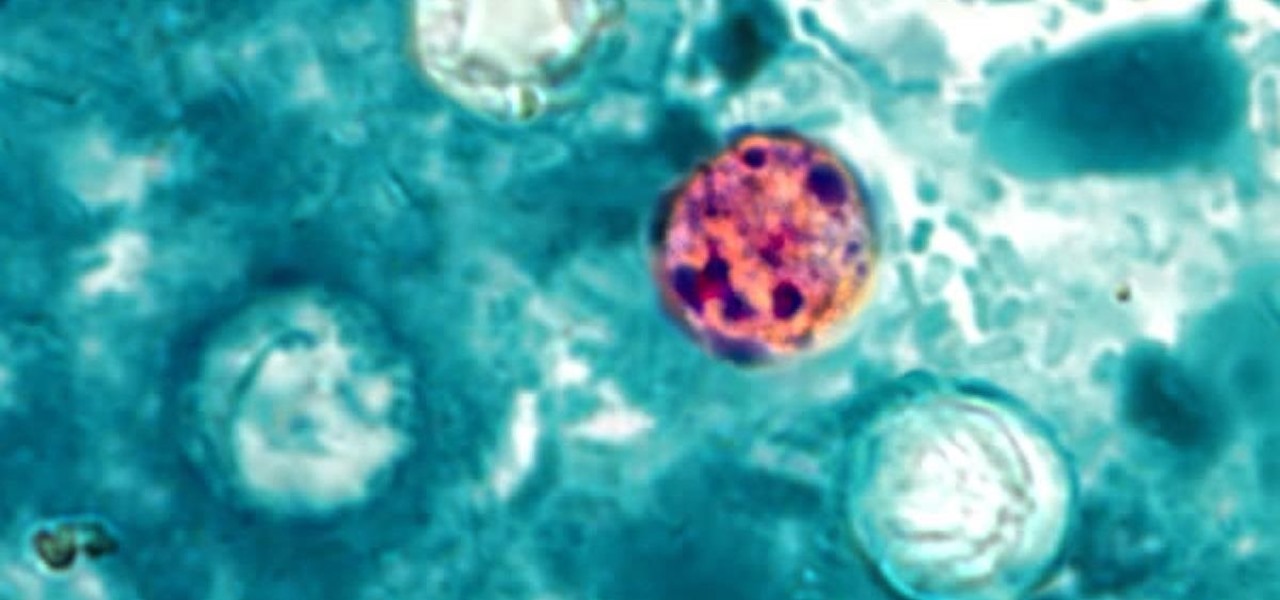
The intestinal parasite Cyclospora cayetanensis has a dramatically increased infection rate this summer, and the source is still unknown, the CDC advised today. 2017 is a good year for Cyclospora looking for homes to start their families and a bad year for those of us who don't like food-stealing tenants living in our bodies.

Augmented reality sells, but who's buying? Over the past week, two companies made executive hires to capitalize on the growth of augmented reality as a service to sell to other businesses. Meanwhile, two companies joined forces to offer augmented reality tools to headset makers and content providers.

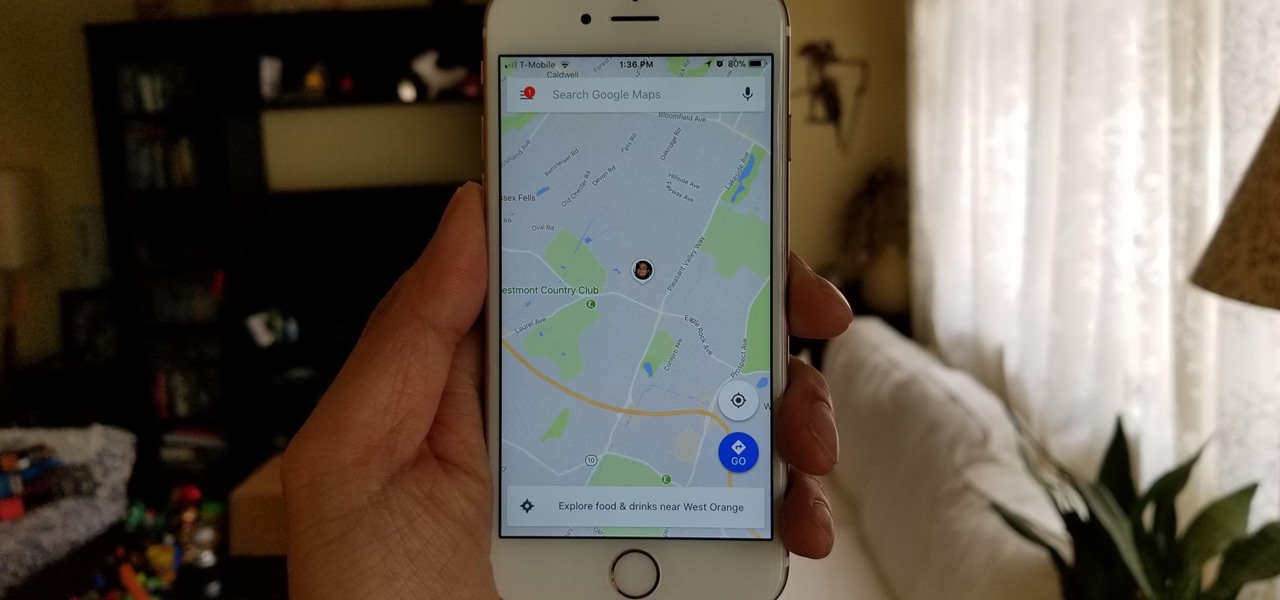
Life is all about spending time together with loved ones, experiencing new places together to enjoy and create memorable moments. Luckily, Google has made it easier for us to rendezvous with friends and family at specific places by letting us broadcast our locations using Google Maps.

In late June, the biggest measles outbreak to strike Minnesota since 1990 seemed to be winding down. Today, public health officials announced a new confirmed measles case in the area.

A recent case of Powassan virus has been reported in Saratoga County and may have been the cause of the infected patient's death. It's the 24th case in New York State since 2000, and will be reported to the CDC tomorrow, the NY Department of Health told Invisiverse. The tick-borne illness has no vaccine or specific treatments and can damage the nervous system.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

The primary method of activating Siri is done by pressing and holding either the Home or Side button, depending on the iPhone model, but there's a much better way to ask a question to Siri or command it to do something — and you don't need to touch your iPhone at all to do it.