Build a web page to collect information from the user with the Wizard control, validate that information, and use the System.Net.Mail classes to send a confirmation email message. Check out this video tutorial to see all about making a 'contact us' page on a ASP.Net website.

No need to sift through your contact list to change a friend's name. Tekzilla will show you how with one easy step.

Check out this video to get a lesson in contact paper screen printing.

While many image sites allow you to hide image and video catalogs behind passwords, you can often gain access to these images by "guessing" the URL of the image. This process is called fuskering. Photobucket is one of the popular websites that can be fuskered and this tutorial will teach you how to use Nav.Net 4.2 to fusker private images

When conducting covert mobile surveillance with video it is vital to have a good bag that will contain and allow you to get footage in an inconspicuous manner. Always take into consideration the lighting and distance you’ll be at.
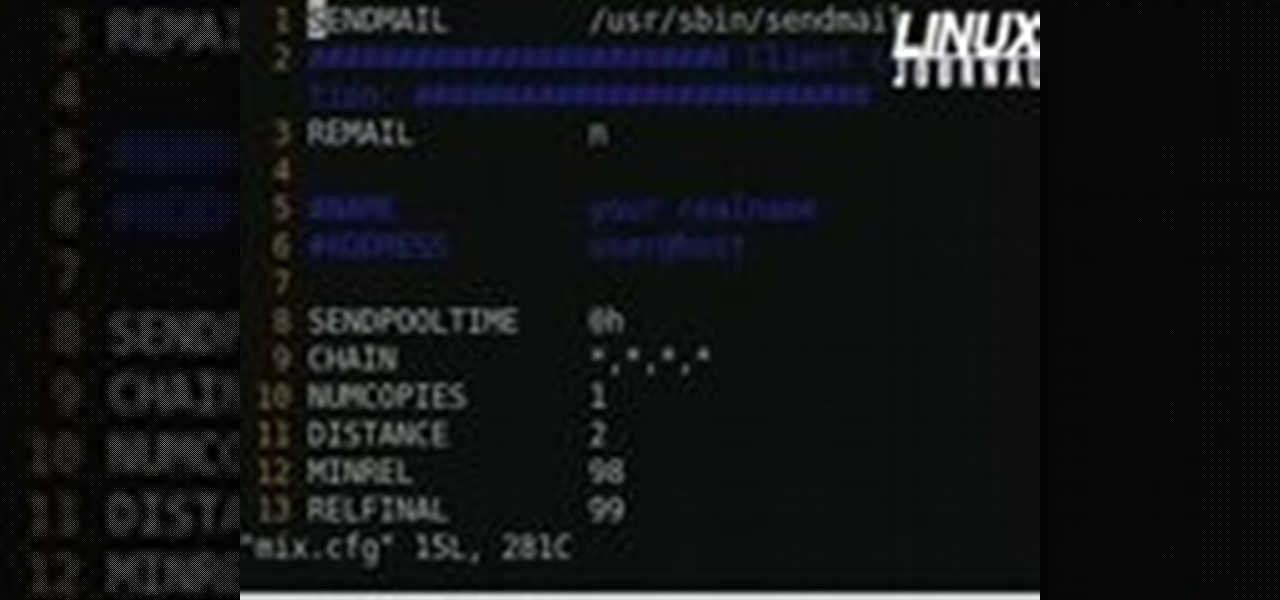
Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.

Learn how to manage contacts and business cards more effectively with this tips and tricks video on Microsoft Outlook 2007. This MS Office tutorial will show you how to create a contact from scratch, and give it a business card look in Outlook 2007.

Social contact is important in establishing yourself as the "alpha" in your dog's eyes. Don't forget to learn this important dog training step. Watch this video pet training tutorial and learn how to use social contact to establish leadership over a pet dog.

When dancing with a partner, eye contact is incredibly important. This how to video goes over proper eye contact with your Latin dance partner.

Apple may pride itself on its commitment to user privacy and security, but it isn't invulnerable. We now know there is a bug in the latest version of iOS 12 and iOS 12.1 beta that allows those in the know to bypass your passcode and access contacts and photos. This applies to both Face ID and Touch ID-enabled iPhones. Not only do we know about the bug itself, we know exactly how to exploit it.

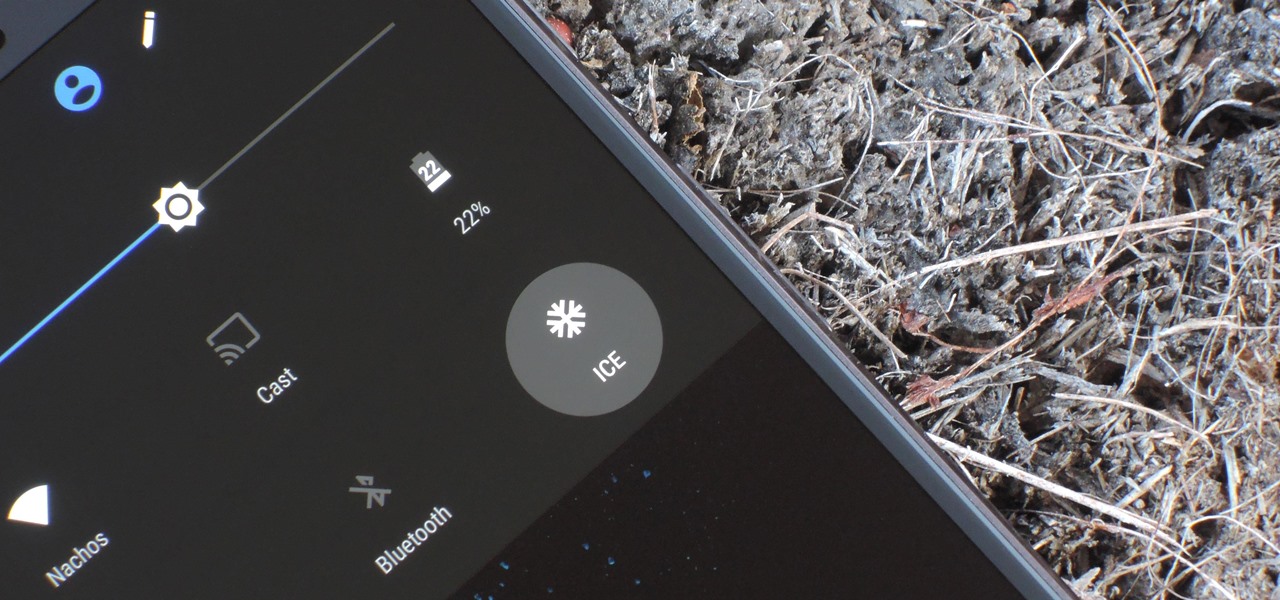
If you're ever in a major accident or have a bout with acute onset health problems, first responders will need to know as much information about you in order to provide proper care. For this reason, paramedics and firemen have been trained to search a subject's cell phone to find ICE (in case of emergency) contacts that know your allergies, blood type, and other vital details.

Accessing and getting in touch with your favorite contacts has never been easier thanks to the "Friends" feature on the Apple Watch. However, this only applies to users who are running watchOS 2.2.2 and lower. When Apple issued watchOS 3, the "Friends" option was completely removed. So if you're running watchOS 3 or higher, you won't be able to follow these instructions.

When I stumble upon a new song that I'm really into, I don't just listen to it repeatedly—I share it with family and friends that I think might enjoy it just as much as I do. Now, thanks to a new iOS app called Craaave, sharing those tunes are a cinch, no matter if I'm using Spotify, SoundCloud, or any other music streaming app on my iPhone.

This video will provide an idea how to merge duplicate contacts on Samsung android device. This tutorial would help you in merging duplicate contacts for a Samsung Android device. Watch the video and employ it yourself.

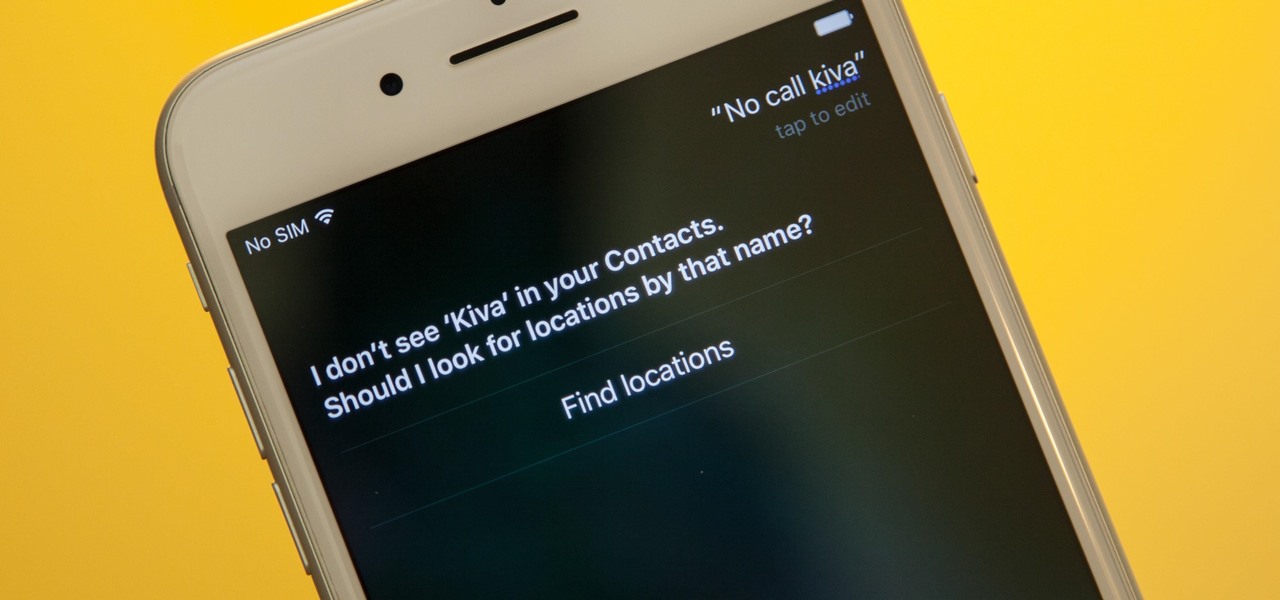
Siri makes it easy to call almost any contact on your iPhone with just a quick verbal command. I say almost because counterintuitive name pronunciations such as Caoimhe, which is actually pronounced "Keeva," will confuse the hell out of Siri. Luckily, there's a way to get Siri to understand pronunciations for the tricky names in your contact list ... it just takes a little grunt work on your part.

A hidden feature residing in Mac OS X Mountain Lion is the ability to view and also reply to your friend's tweets through the Contacts application, previously known as Address Book. The only way to do this, though, is to provide your Twitter account login data to the Contacts app. To integrate your Twitter, just go to System Preferences, then click on Mail, Contacts & Calendars and choose Twitter. Put in your Twitter login information and then click on Update Contacts. Twitter will use your e...

Google calls it "Incognito," Microsoft says "InPrivate," the other browsers call it "Private Mode," and colloquially it's known as "porn mode." Whatever you call the tracks-free way to browse, here's a trick to force your favorite browser to always start with its privacy protocols activated.

Tinkernut demonstrates how to hook up your exercise bike to Google Maps. Using a stationary bike can be good for your health but it can also be boring. You can spice up your exercise regiment by using Google Maps. You will need a USB keypad with arrow keys, a magnetic contact alarm with wires, soldering equipment, an exercise bike and a laptop computer. Connect the contact alarm to the up arrow key on the keypad by opening up the keypad and connecting the wires to the up arrow key by solderin...

In this video tutorial, viewers learn how to play the game, Borderlands online with Hamachi private network. Users will need to first download the Hamachi private network. Then open Control Panel, and select Network and Sharing Center. Under Tasks, click on Manage Network Connections. Click on the Advanced menu and click on Advanced Settings. Move the Hamachi network up and click OK. Now open the Hamachi and create a new network or create on. Type in the network ID and password. This video wi...

In this video, we learn how to create a favorites list on an iPhone. Doing this will make it easier and quicker to speed dial! First, just tap on the "favorites" button. Then, click on the "+" button to add a new favorite from your contacts. You can then click "edit" to rearrange or remove favorites from your list. Click on the blue arrow next to a name to see the full contact details for that person. As soon as you add or remove someone from your favorites it's saved. That's all you need to ...

Apple's web browser, Safari, stores information like web history, Google's search history and cookies from websites. There may be certain instances where you want to keep this information private–for example, if you're on a public computer or have borrowed a computer from a friend, you may want to keep that information to yourself. For a step-by-step guide to using the private browsing feature in Safari, watch this OS X video tutorial.

Looking to go electric on the cheap? In this video tutorial, you'll learn how to make a contact microphone out of a Piezo Transducer, available for $2 from Radioshack (part #273073A). You'll also need some sort of audio connector, which can either be salvaged from old electronics or bought from Radioshack as well. This video also covers how to make shock mount for the mic out of scrap styrofoam. Amplify most anything with this how-to.

Check out this video tutorial to see how to keep your private files private, even if you have to email them to yourself at your office? TrueCrypt, an open source piece of software, lets you encrypt your files so they remain accessible only to you. This works on any platform; Windows, Linux, or Mac. So, watch this video to see the TrueCrypt download process, how to install it, and how to create an encrypted volume on your hard drive.

One method you can use to protect yourself, is to ensure you clear your private data, such as your search history, and in this screencast tutorial, we show you how to do just that in Mozilla Firefox.

Getting your pilots certificate may be on the expensive side, but after only a few weeks of training you can be flying all over the country! We show you some tips on the path to getting a private flying certificate in this video, and if you're afraid of heights, just do what Veronica did -- pretend it's a video game!

Check out this DIY video tutorial from Curbly, the best place to share pictures of your home, find design ideas, and get expert home-improvement advice.

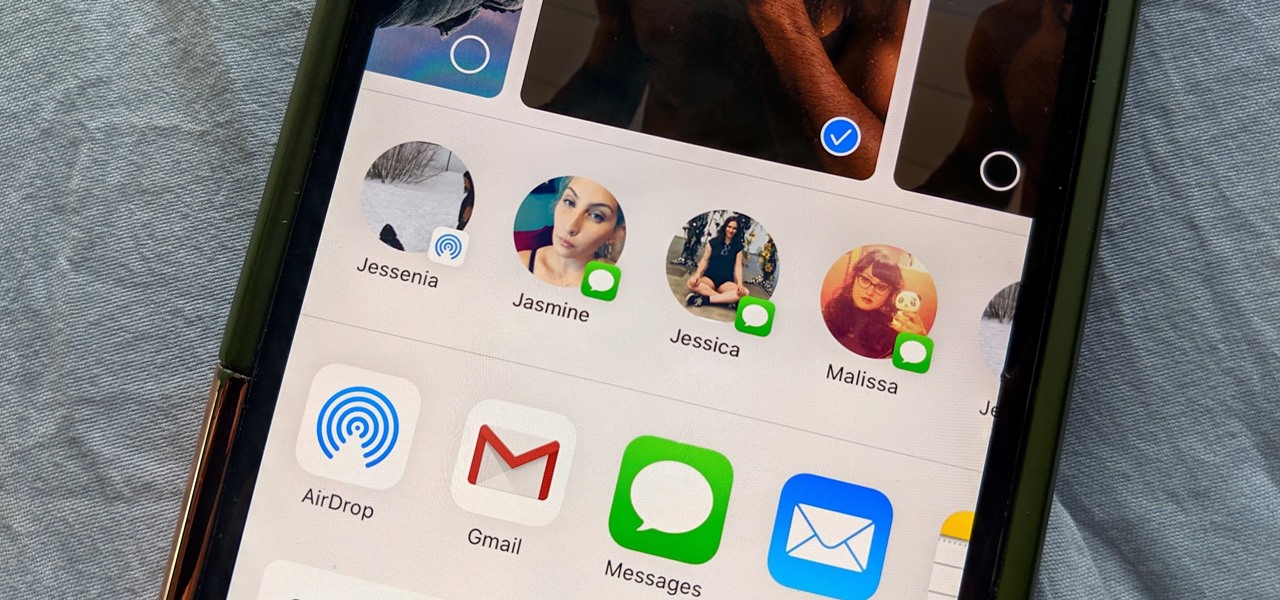
The share system on your iPhone serves as a hub for actions and share extensions, streamlining the process of saving files, sharing photos and videos, and other important tasks. On iOS 13 the Share Sheet has received a considerable upgrade, including the ability to more easily share content with your favorite contacts.

Apple's Mail app has always been a stylish yet simple way to check and send emails. Third-party apps up the ante with powerful tools and features to help keep junk and spam mail out of your eyesight. But with iOS 13, you don't need them since Apple gave the Mail app some much-needed superpowers. One of those being the ability to block senders from emailing you.

When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

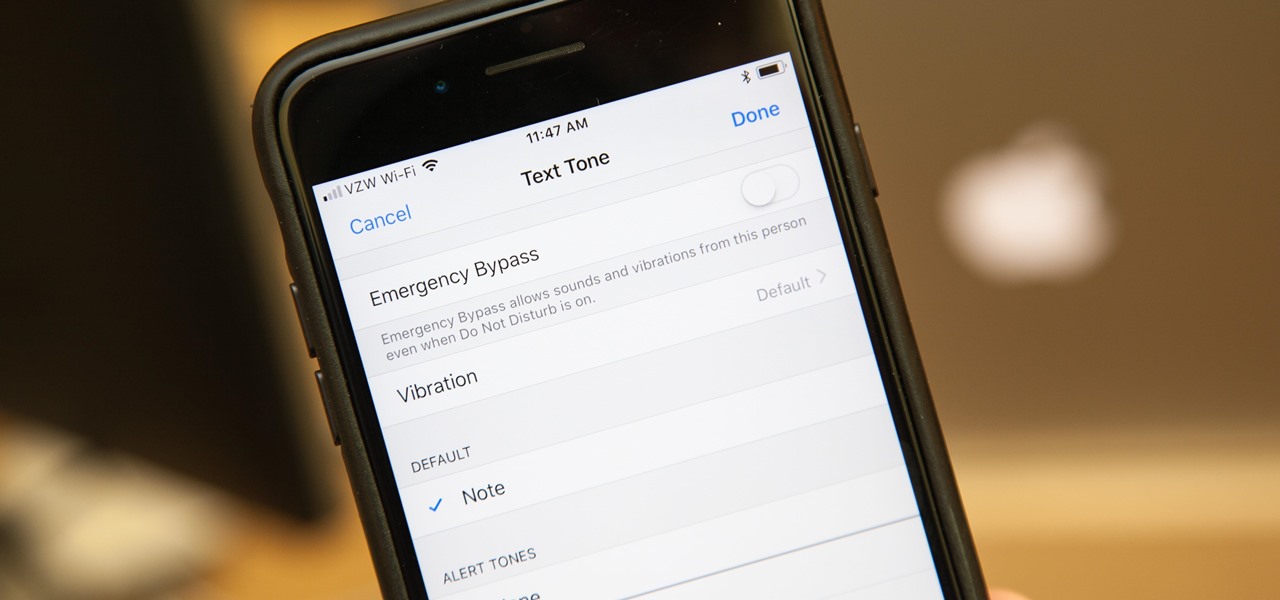
In the "Do Not Disturb" menu in your iPhone's settings, you can choose to allow phone calls from everyone, your favorites, or specific groups. However, this does not apply to text messages, only phone calls, so there's no way to get vibration or sound alert for messages from select contacts — but that doesn't mean there isn't a way.

For every contact photo you add, Android keeps two copies. The first is stored at a 720p resolution, and this is used for high-definition imagery when you're looking at a full-sized contact card. But the second image is only 96 pixels by 96 pixels, and this is used for all thumbnails throughout the operating system.

Extremely important calls have a way of coming at the most inopportune moments: when you're in class during an important lecture, at a big business meeting for work, or even when you're just enjoying a day at the movies.

Whether it's embarrassing pictures and videos on your smartphone, or files you just don't want anyone reading, there are plenty of ways to hide them. For most devices, that means installing third-party apps like Gallery Plus - Hide Pictures, Sectos - Photo & Video Vault, TimeLock, or Hi App Lock.

Folders are a neat way to keep your home screen apps organized in your own specific categories, but what about your personal contacts? You can actually populate a folder with all of your favorite contacts for one-tap instant access.

With so much of our personal data floating around the web, it's nearly impossible to get away from spam calls, texts, and emails. Unfortunately, this isn't just limited to the online world — filling in your contact information in a raffle ticket with the hope of winning that shiny new car in the mall, for instance, can often result in getting swamped with spam texts containing sketchy loan offers.

Taking a cue form Snapchat, WhatsApp Status lets you share updates that come in the form of GIFs, photos, videos and good old text. This awesome feature is available for both iPhone and Android users, and it even lets you choose which contacts to share with while disappearing after 24 hours.

A new iPhone exploit has recently been discovered by YouTube user videosdebarraquito, who has found many other exploits and bugs in iOS over the years. This new exploit allows someone to bypass the lock screen and gain access to contacts and photos via Siri, Apple's digital voice assistant—but it only affects the iPhone 6s and the iPhone 6s Plus because it requires 3D Touch functionality.

I misplaced my iPhone 6 just a few weeks ago, so I know firsthand that losing an iPhone sucks. Luckily, my tale didn't have a bad ending.

If you've haven't had your fill of Apple's security issues in recent weeks, Siri is now the latest to join the slew of problems with the most recent version of iOS (7.1.1).