Can you trust every user you come across on TikTok? The answer to that may depend on how use the service, but the real question is — can you trust every user that sees your content? Not everyone on TikTok is someone you want viewing or interacting with your content, and there's a way to prevent them from doing so.

Since starting as a simple messenger with self-destructing pictures, Snapchat has grown into a full-fledged social media platform. As features were added, new permissions were requested, and we're all probably guilty of just tapping "OK" to try out the latest and greatest. But at some point, it's a good idea to review your settings to see what personal data you're putting out there for all to see.

Having your home and work addresses set in Apple Maps makes them incredibly easy to navigate to no matter where you're located. If you move to a new house, stay in a hotel or resort while vacationing, report to a different office, or have multiple job sites to visit regularly, updating these addresses isn't only straightforward — there's more than one way to do it.

It seems like there's a cyber security scare every day. Consumers are growing increasingly concerned about the safety of their accounts, and they have reason to be. Hackers will maliciously attack you anywhere — and we mean anywhere — they can to get your private information.

It appears a privacy lawsuit that began five years ago is about to come to an end, and you might get some money out of it.

TrueCaller is sharing your phone activity by revealing the last time your phone was used to contacts. The application used to identify unknown callers launched in 2009 and has faced a wealth of privacy concerns before.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

Samsung included an "SOS" feature for its phones since the Galaxy S6 that could literally be a lifesaver should you ever find yourself in an emergency situation. It's one of those things that we hope to never have to use but will be very thankful for if a need ever arises.

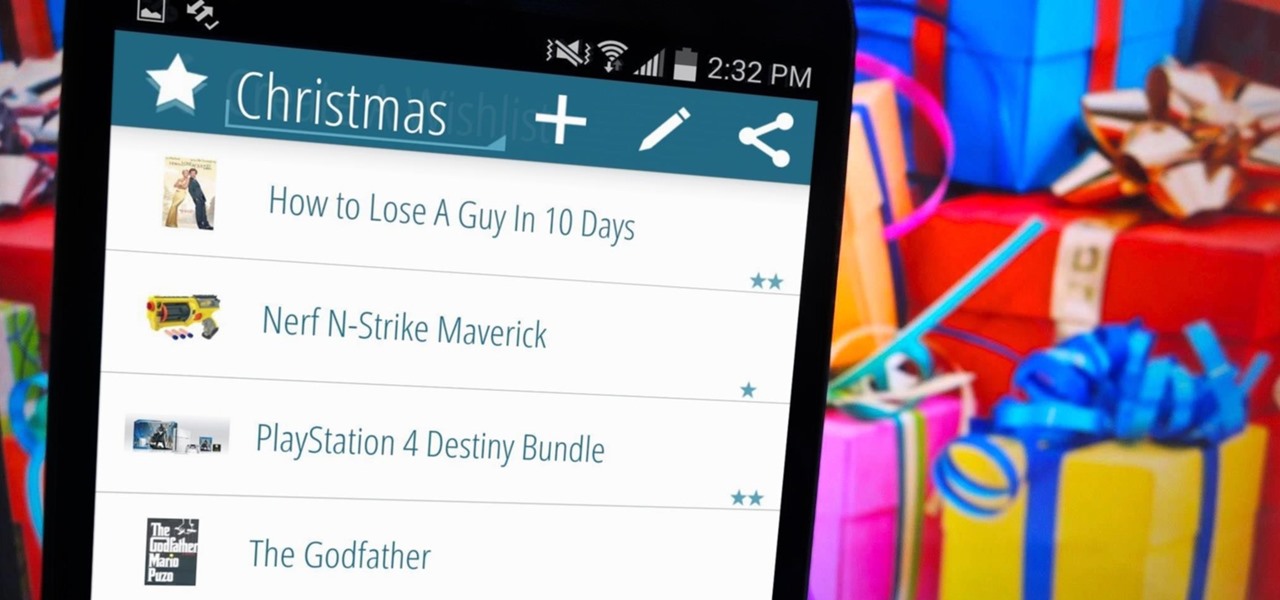
I love the holidays, but man am I sick of receiving oversized sweaters as Christmas presents. As well as people think they know us, their gifts often say otherwise. Instead of stocking up on useless items and articles of clothing you'll never wear, it's high time to create a wish list that's easily sharable amongst family and friends, and it's incredibly easy to do on Android.

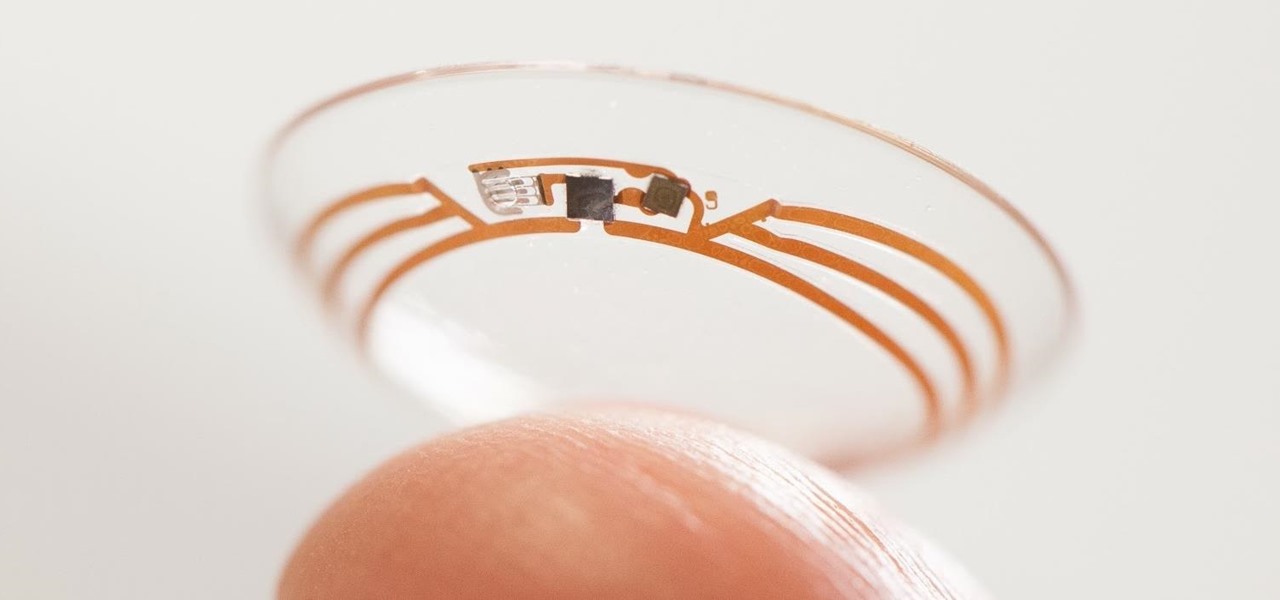
Warning: Google wants to take control of your sight. While this statement isn't (or is) true, it doesn't change the fact that Google is partnering up with Novartis to create contact lenses.

While their merger with Microsoft has lead to a seemingly complete halt of new device development, some Nokia employees are still hard at work to bring new software to the table.

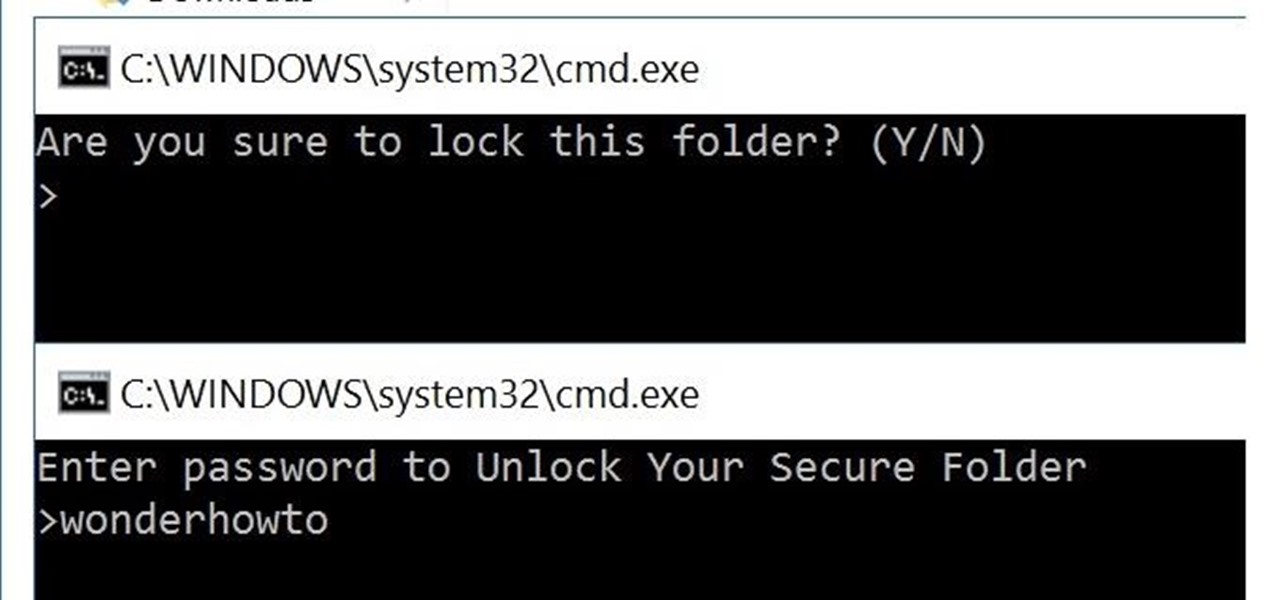
You can easily lock any folder on your Windows computer with a simple Notepad hack. By creating a batch file, you can hide a folder and require a password be entered before it becomes visible and accessible. This is a great tool for locking sensitive information, like pictures, financial statements, and a lot more.

For my money, one of the greatest improvements brought about from the smartphone revolution is the advent of visual voicemail. No longer do we have to slog through dial menus or trudge through every single message to get to the next. We can just look at our messages, right there on our screens, organized neatly like emails or text messages.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

In this tutorial, Brian teaches us how to make your wireless network secure. First, go to the start menu, then go to run and type in "cmd", then type in "iconfig /all". Now a new window will pop up and you will look for the default gateway. Find the IP address to log onto the routers you have. Now, type in your IP address into your address bar on your internet browser. You will be asked to log into your account with your password and user name, which you can find at the manufacturers website....

Babysitting is the prime teenage job for young women to start learning responsibility and earning a wage, but it isn't all fun and games… you are dealing with an infant, which is far from fun, but it's money in your pocket. Earning a little extra money babysitting infants can be more fun — and a lot easier — than schlepping food at your local diner.

Lady Gaga is one of the most secretive women in show business, hiding behind her stage performer mask and outrageous costumes so often that we can hardly believe there's a real person underneath all that fluff.

So, you're browsing the web on your iPhone using Safari, and you come across a picture you really want to keep forever and ever… what do you do? You can save it directly to your phone! But how do you download that web image? Best Buy has answers. The Best Buy Mobile team explains how simple it is to save web images from Safari on your Apple iPhone.

If you're worried about having your private information taken away from you by hackers and other malicious people, this tutorial may help you. This tutorial will help show you how to easily use and understand the phishing filter in Internet Explorer 8. It only takes a couple of clicks to activate and can be the difference between making sure your private information is secure or out in the open for others to use. Good luck and enjoy!

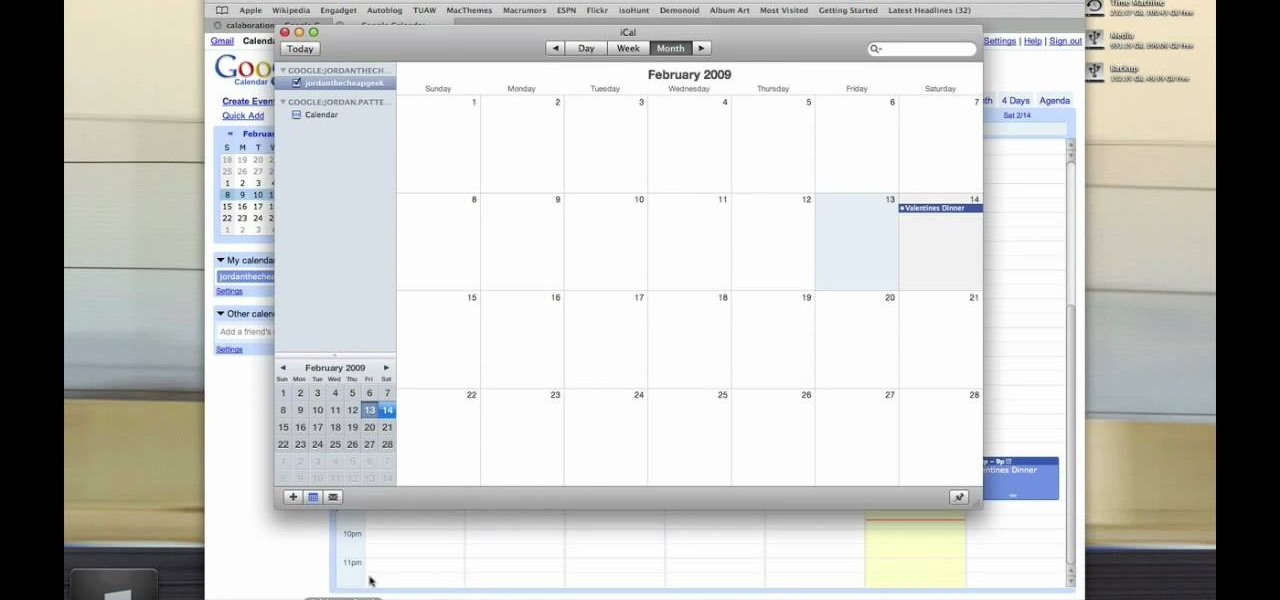
Jordan Patterson the Cheap Geek has made a video showing you the steps to sync your contacts and calendars on three mobile devices together, the iPhone, a laptop running Windows, and a Mac running OS X utilizing a few downloaded programs and Google Calendar. First he shows you how to sync calendars on the Apple computer, by downloading a program from Google code called collaboration code, and then running it. After putting in his g-mail account information, he tells the program which calendar...

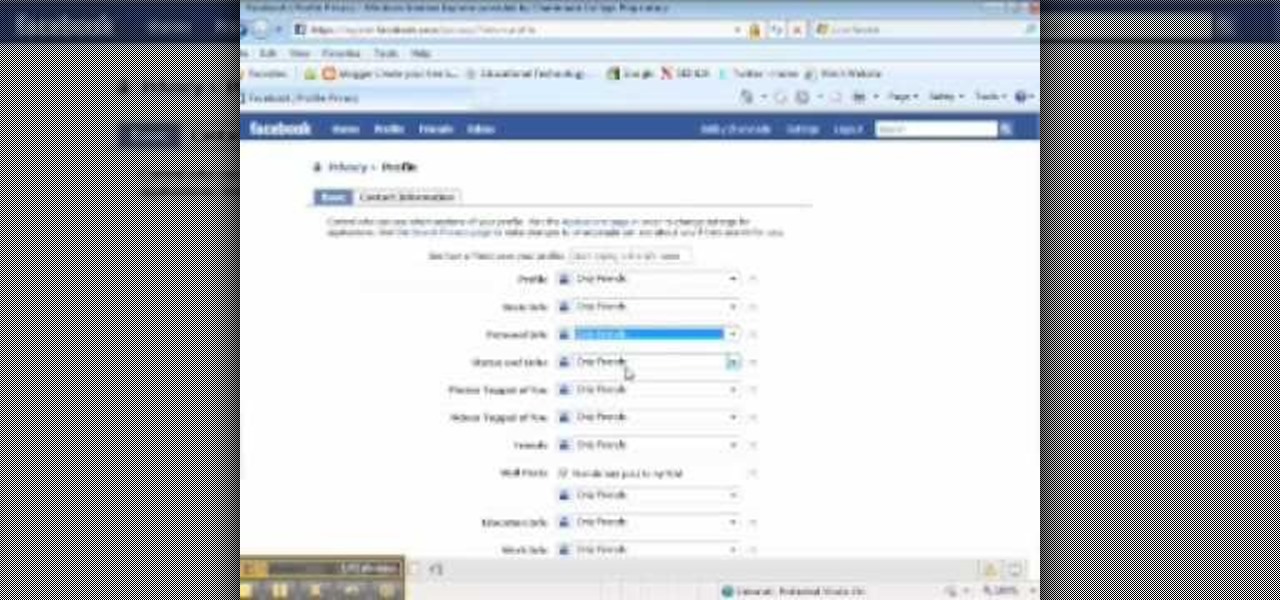
This video tutorial from ChaminadeENN shows how to set your Facebook account to private mode. First what you need to do is to sign in to your Facebook account.

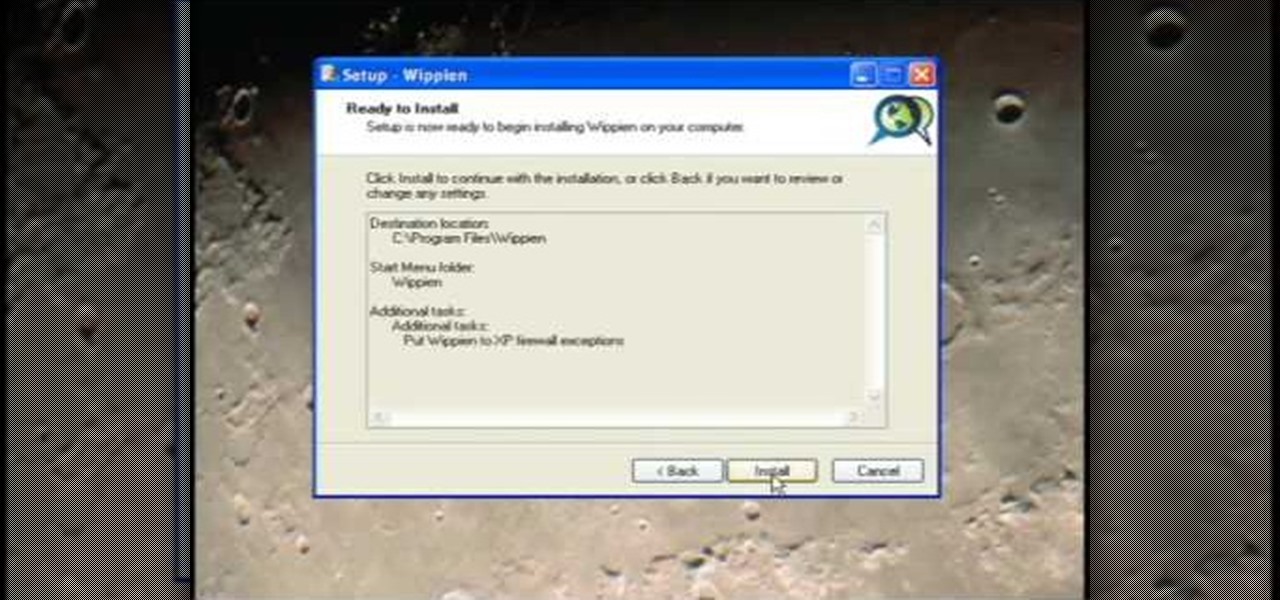
This video tutorial from ruralgeek shows how to set up and use Wippien VPN on Windows XP. First, download Wippien client from here: www.wippien.com.

You can use surveillance skills to pursue a career as an investigator or to spy on whoever you like. You will need to have a mobile means of making observation and this might include things like pen and paper, camcorder or camera.

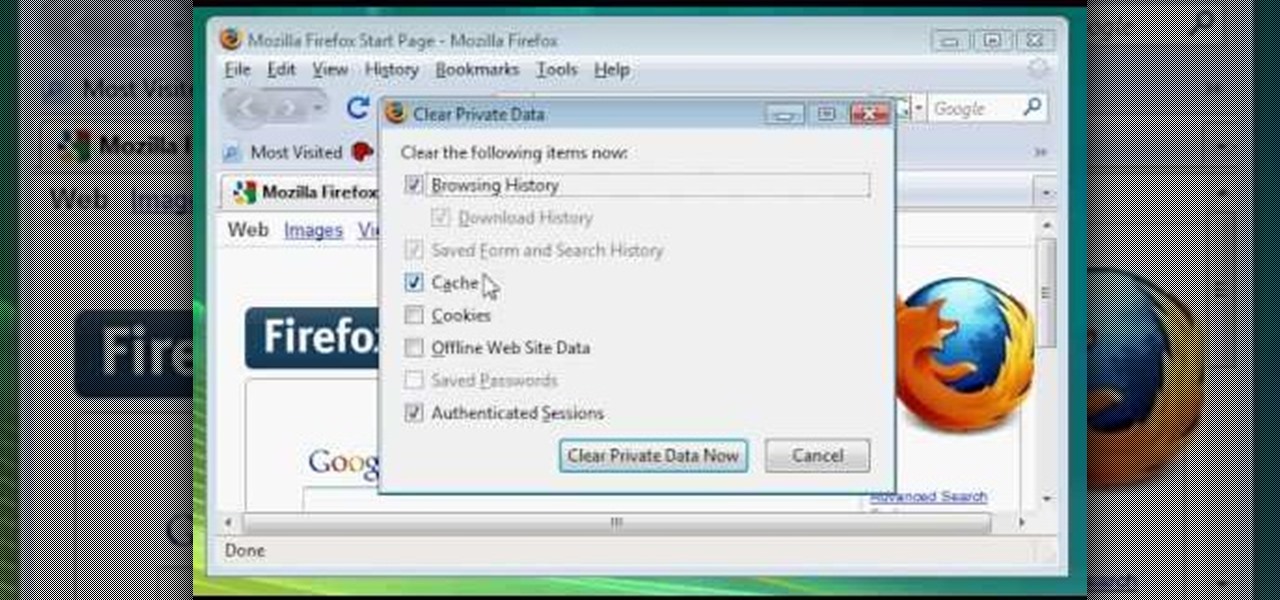
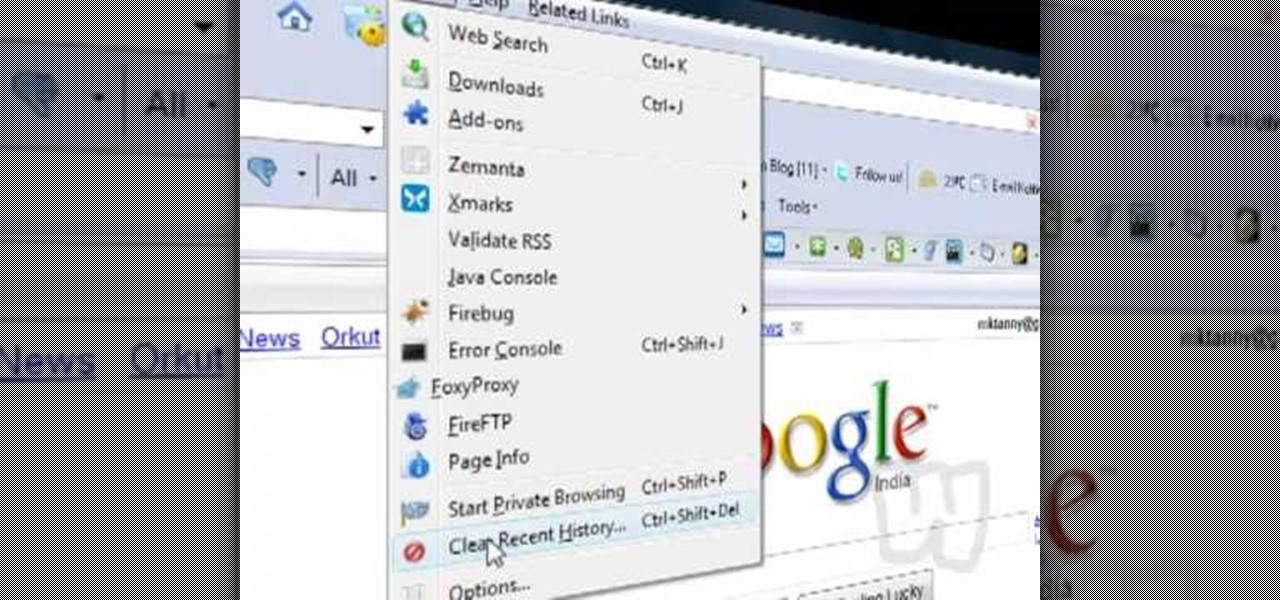
Here Danny Beales shows you how to quickly clear your Firefox cache and cookies. To clear your Firefox cache, do the following: Go to Tools Clear Private Data Select which data you would like to have cleared, and click on Clear Private Data. Your cookies and/or cache has been cleared. Remember to do this from time to time, because it will help speed up your browser's performance as well as keep harmful cookies from tracking your browsing.

This video shows you how to easily delete cookies from your browser. First thing you have to do is open the web browser you usually use (the video shows how to delete cookies from Firefox) and go to the Options tab in the upper menu. Then choose the Clear Private Data or Clear Recent History item. In the pop-up window, check Cookies and Cache and then press the Clear Now button. The Clear Private Data/ Clear Recent History window also can be opened by pressing CTRL+SHIFT+DEL. That's it! Good ...

Communication is a two-way street that will quickly become a dead end if no one is actually listening.

If you're feeling unappreciated, underwhelmed, or just plain trapped, taking some time off may help.

Thanks to the Freedom of Information and Privacy acts, we’re all entitled to see what the FBI has on us. Learn how to get your hands on your FBI file.

Skype is definitely a revolutionary software for keeping in contact with your loved ones. It's a phone on the internet! What couldn't be good about that? If you are in Orlando, your spouse is at a conference in El Paso, your daughter’s at college in Raleigh, and your son is working in Dubai, you can keep the family in touch with Skype, a software application that lets you make free video calls over the internet.

mIQ? What is it exactly? It's a handy web service that helps you manage your mobile life, with free and easy online access to all of the content and information stored on your mobile device. How does it work? Best Buy has answers. The Best Buy Mobile team explains how simple it is to use mIQ to backup all the data on your cell phone, including messages, photos and contacts.

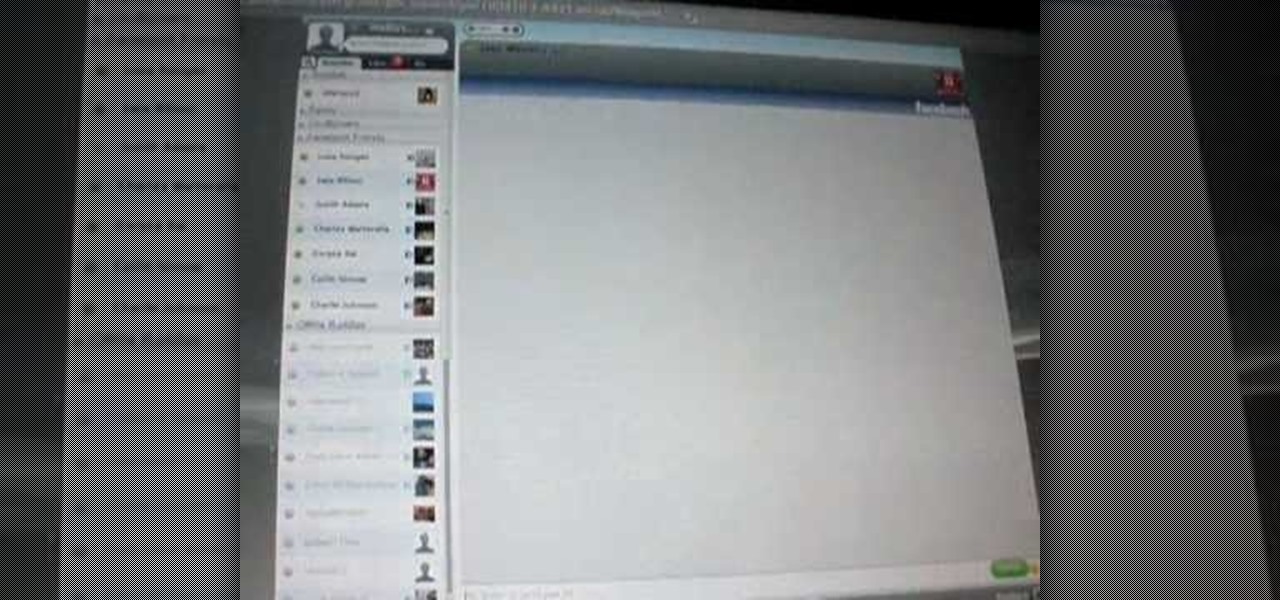
Stay connected with your friends on Facebook, even when you're on your Playstation! Facebook Chat is one way you can stay in contact with your friends, or group chat with fans of a particular page. And now you can stay signed into to Facebook chat with your Playstation. Follow this easy to understand tutorial so you can use chat and your gaming console at the same time.

If you haven't heard of jalebi yet, then you're missing out on one of the most delicious dessert sensations your taste buds will ever come in contact with (no exaggeration).

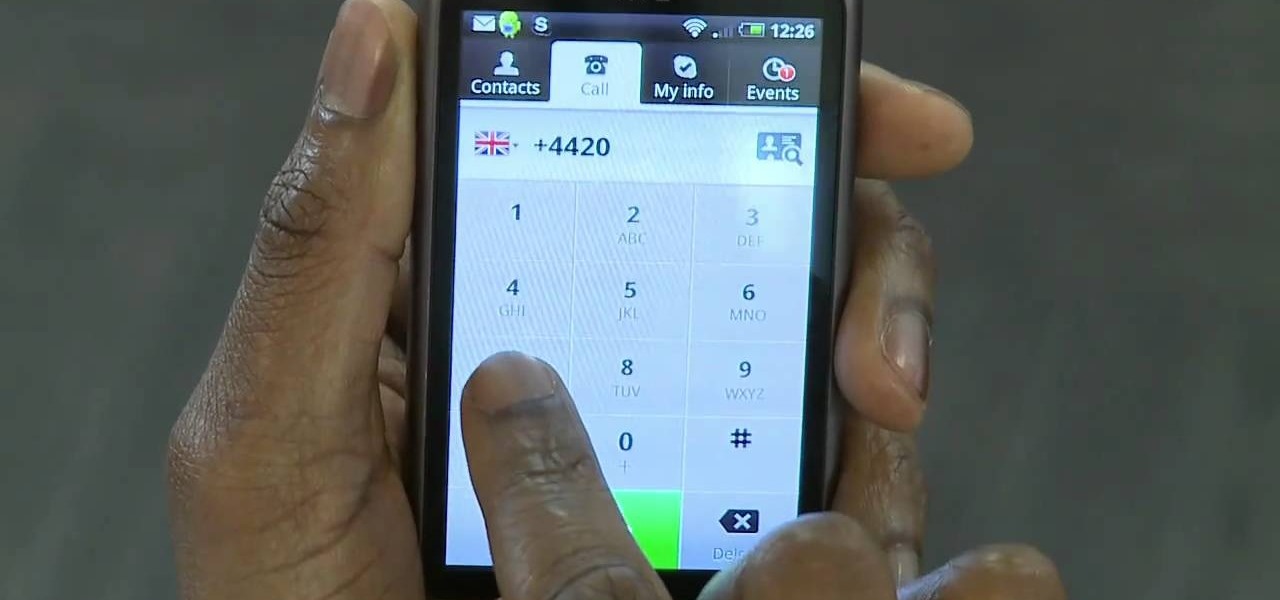
In this video tutorial, we learn how to use the official Skype app on a Google Android smartphone. Specifically, this video addresses how to find your contacts and place phone calls. For all the details, and to get started using Skype on your own Android mobile phone, take a look!

If you're running a business and have employees, chances are you may have to write up a Employment Verification Letter. The tricky part is knowing what to put down on the letter itself. In this video you will learn what layout you will need and the information to put into the letter including: Company Letter Head, contact information, description of the employee's duties, ect.

Watch and learn how to stay in touch with your friends and family on the HTC Droid Incredible cell phone. Verizon Wireless shows you around the Android platform on the Incredible, highlighting the "People" widget and "Friend Stream" icon to work with your contacts and social networks (Twitter, Facebook, Flickr).

Video game controllers can get pretty grimey. The more greasy hands that come into contact with your Xbox, the grosser your device will get. In this tutorial, learn how to clean your controller using gloves, water and dishsoap. Follow along and make sure you know what you are doing so that you don't ruin your controller.

This video shows you how to make your liquid dance. Its happens like so, at around 300 degrees Fahrenheit a phenomenon in which a liquid, at close contact with a mass significantly hotter than the liquid's boiling point, rides upon an insulating vapor layer which keeps that liquid from boiling and evaporating. What is this strange phenomenon? The "Leidenfrost effect" of course, and with Mr. G at the helm it's also a lot of fun.

This video series thoroughly lays out topspin tennis forehand progression. Be sure to click on every video chapter to see the full tennis lesson series.

Instead of using Photoshop, why not give Apple's Aperture a try? Aperture is designed more for post-production work for professional photographers, letting you cull through shoots, enhance images, manage massive libraries, and deliver stunning photos.