Keep private info from prying eyes and earn some peace of mind when you safeguard your PC or Mac against nosy intruders. You will need several great passwords, virtual desktop software, snoopware blockers, a screen filter, a mirror, a healthy sense of paranoia, WPA encryption, and an understanding IT specialist.

There is a security flaw with any Apple iPhone running firmware version 2.0.2. This flaw potentially gives a person access to your email account and contacts when you have your iPhone locked. This video demonstrates a simple, but impermanent, fix for stopping others from accessing your private information. To protect your own Apple iPhone, watch this tutorial.

This sequence of instructional videos provides a near comprehensive lesson on how you can change your voice from that of a male to that of a female. This video series is aimed at aiding transgender individuals, but is also useful for people who want to learn to do really great voice exercises and impersonations.
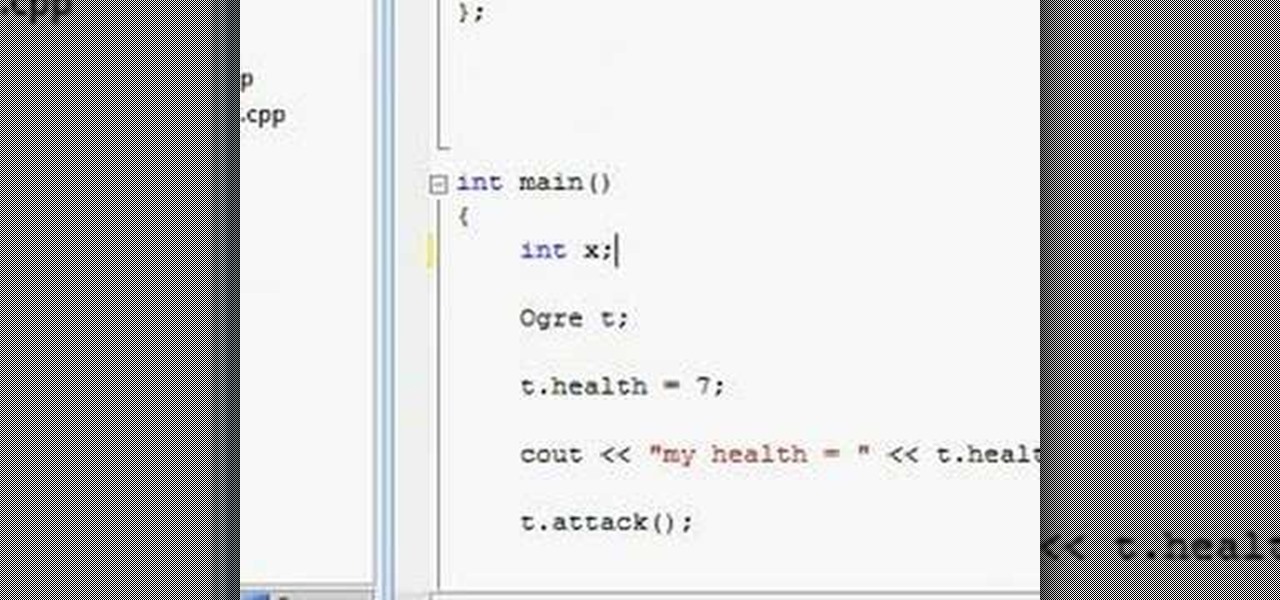
Watch this video to learn how to create OOP design with C++. This video also covers public and private variables and functions.

Today's word is "reticent". This is an adjective which means not revealing one's thoughts, or being reserved.
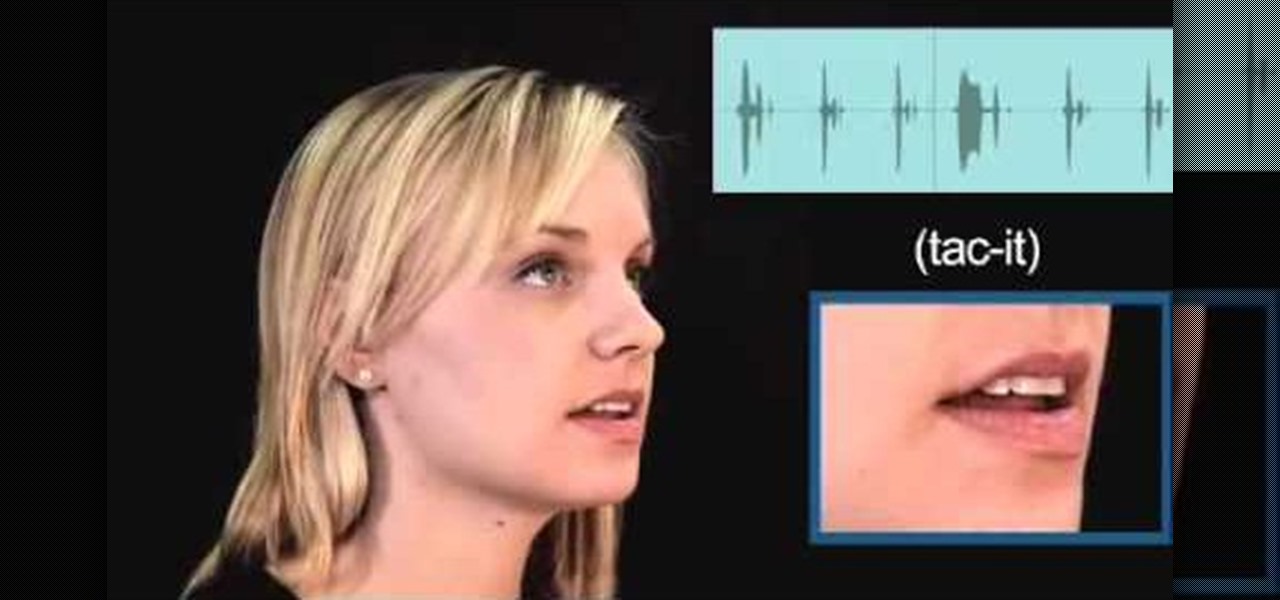
Today's word is "tacit". This is an adjective which means implied or conveyed without words.

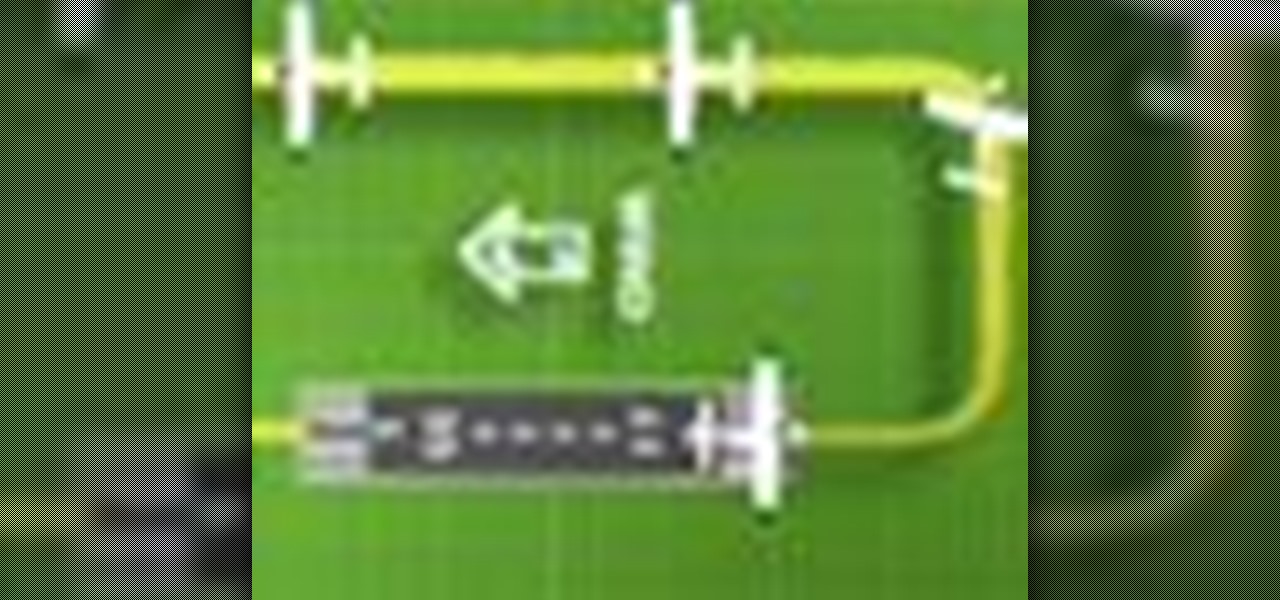
In this AeroCast episode, UND Aerospace discusses the Slow Flight maneuver as performed in the Piper Warrior (PA-28-161), referencing the procedures and standards outlined in the UND Warrior Standardization Manual. All performance tolerances are based on the performance standards set forth by the FAA Private Pilot Practical Test Standards. Since the most critical phases of flight occur at airspeeds less than cruise, a pilot must always be comfortable with his or her airplane’s handling charac...

In this AeroCast episode, Anthony Bottini discusses the Power On Stall maneuver as performed in the Piper Warrior (PA-28-161), referencing the procedures and standards outlined in the UND Aerospace Warrior Standardization Manual. All performance tolerances are based on the performance standards set forth by the FAA Private Pilot Practical Test Standards. Power On Stall practice is vital in increasing a pilot’s proficiency in regards to stall recognition and stall recovery techniques during an...

Unless you have your own private airport (I’m looking in your direction John Travolta) then you will most likely have to coordinate your takeoffs and landings with all the other air traffic using your specific airport. Whether it be a towered or non-towered airport, this latest UND Video Standardization Lesson is designed to help you, the student pilot, become familiar and hopefully more comfortable with Airport Traffic Pattern operations.

Need internet access and you don't have a login? Hack into a private or controlled network with this tutorial. Thefixed.org also shows you how to build a smoke bomb!

Find the biggest files on your computer ordered by size. Learn to order folder by filesize so you can find the ones harboring the most diskspace terrorists. Learn to clear up your private data automatically and wipe it clean from being undeleted.

Technically it's the California Chardonnay vs. the French White Burgundy but since they both use the Chardonnay grape it's still a battle. In this video Gary tastes and compares two against two: 2004 Pessagno Sleepy Hollow Chardonnay and 2004 Beringer Private Reserve Chardonnay vs. 2003 Caves De Colombe Chassagne Montrachet and 2001 Matrot Puligny Montrachet Comb Ottes. See which Gary puts on top.

Many apps, including Facebook, Twitter, and Facebook, do not let you download videos, even if they are living on your own account. Saving these videos usually requires a third-party app or screen recorder, which is inconvenient and can result in loss of quality. However, TikTok, the newish popular short-form video platform, makes it easy to download videos — even if they're not yours.

With Instagram's archive feature, we have the pleasure of hiding all our stupid photos of #gettingcrunk from back in the day. This wonderful new IG feature will still allow us all to cherish those embarrassing moments in our life, yet hide them from those people we hope would never scroll so far down.

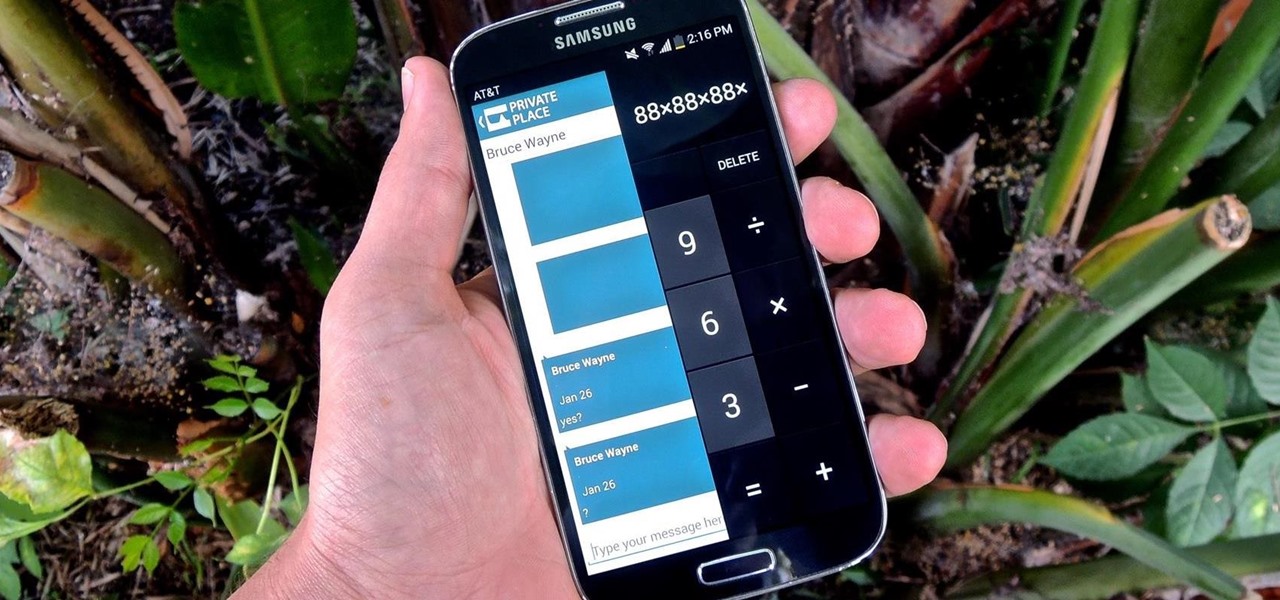
Whether you're a secret spy or just a regular person with a few secrets, you may want to keep certain information on your smartphone private, and it's totally possible on Android to do so.

With over a million apps and counting, it's not exactly easy to browse the iOS App Store to find fresh and interesting new apps for your iPad or iPhone. Even rummaging through the featured apps and games isn't easy.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

Reducing allergies in your home can be done with a couple preventative steps. Learn how to eliminate harmful allergies in your home with expert tips in this free health video series.

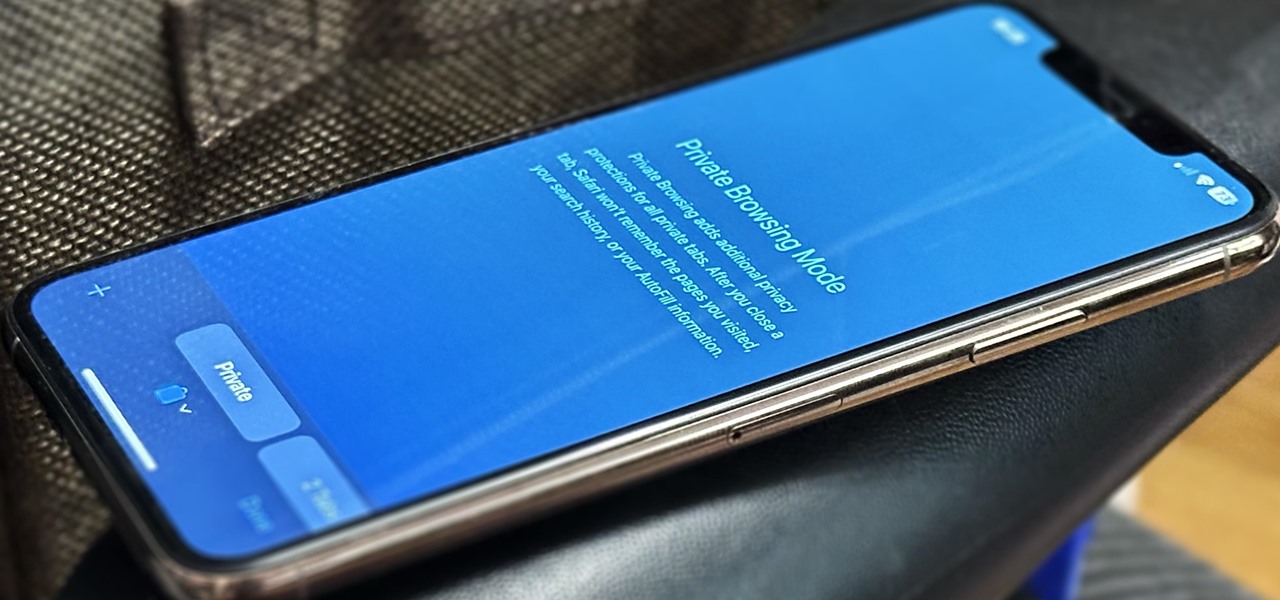
Private Browsing mode finally lives up to its name in Apple's huge Safari 17 update for iPhone, iPad, and Mac. So whether you search for things you don't want anybody to know about or want to ensure websites and trackers aren't eavesdropping on your activity, you'll want to update your devices pronto.

Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

With Touch ID enabled, your iPhone needs to scan your fingerprint before you can access your home screen or last app used. Before it unlocks, your iPhone might request that you press the Home button, adding an unnecessary step between you and your data. However, you can turn the feature off so that you don't need to click any buttons to unlock your device.

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.

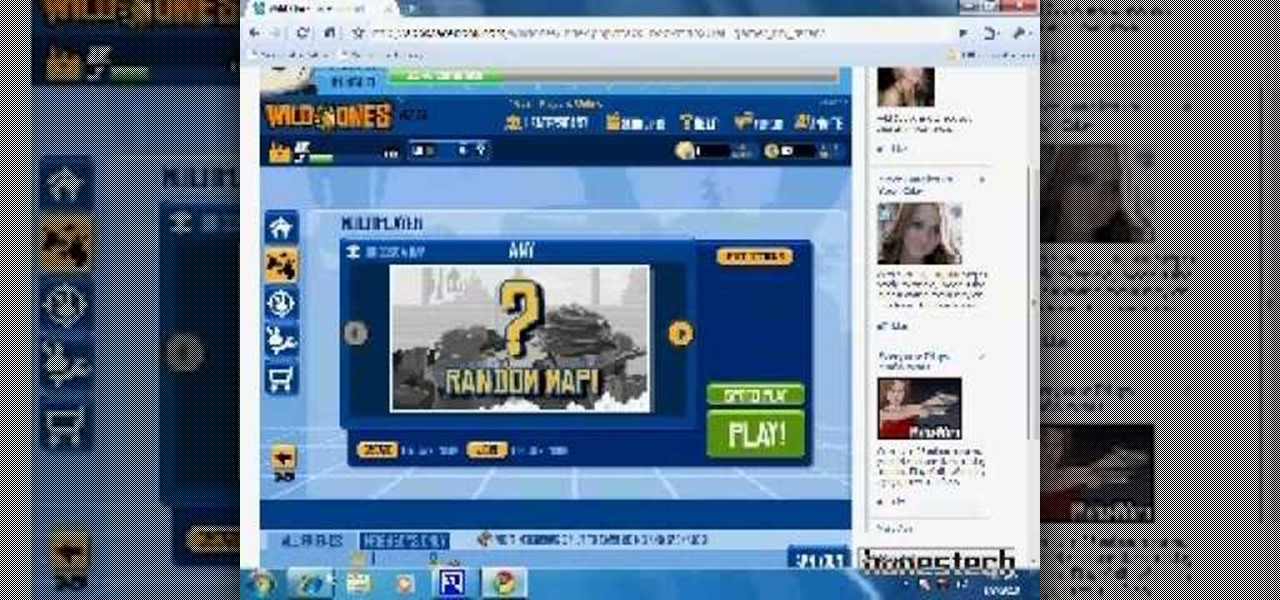
Do you find yourself getting rocked by your friends and relatives whenever you play Wild Ones on Facebook? A little more money would help right? This video will teach you how to use an easy cheat to acquire a theoretically infinite amount of money and coins. All you need are two Facebook accounts and two different web browsers and you can do this easily. Now get in there and buy yourself a better pet!

In this tutorial, we learn how to sound like a biological woman while speaking. There are many different techniques to help you speak like a woman, including going into falsetto. This isn't about getting the sound, it's about learning how to not speak with resonance. You want to focus your voice up in your throat instead of deep down. You probably haven't used the muscles for this voice, so using falsetto is a great way to practice. You may be able to speak a few minutes and feel yourself fal...

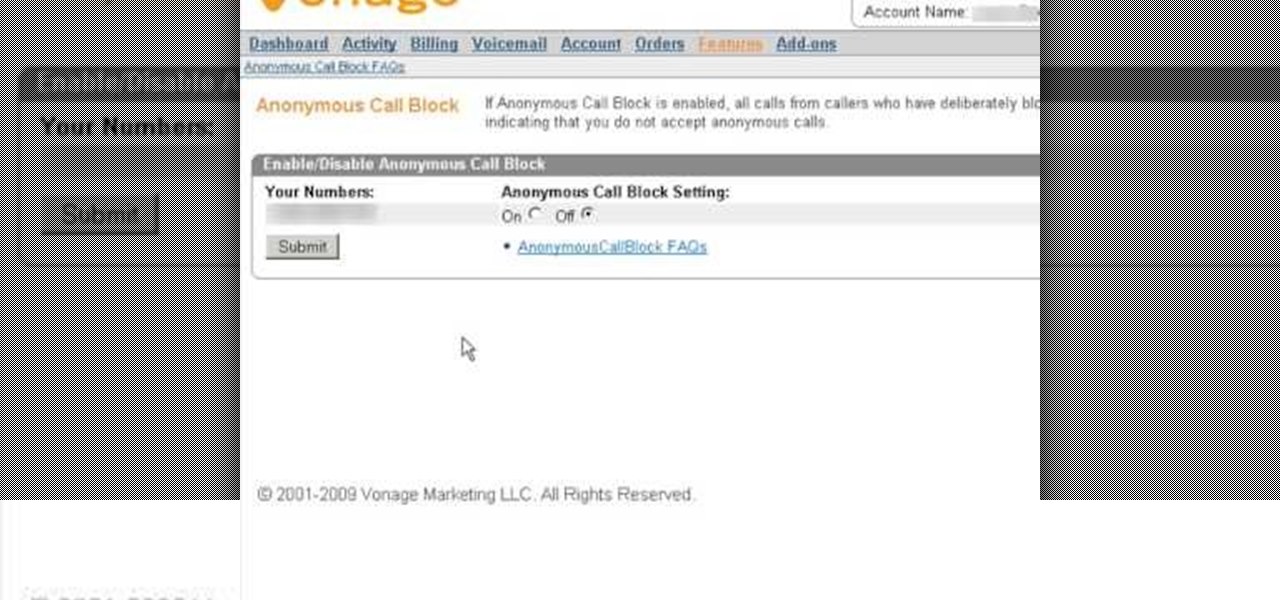
If you are looking for a way to prevent telemarketers and nothing else is working, consider signing up for Vonage's call blocking feature. In this tutorial, brought to you straight from the professionals at Vonage, learn how to set your phone to block any incoming call without a number attached to it.

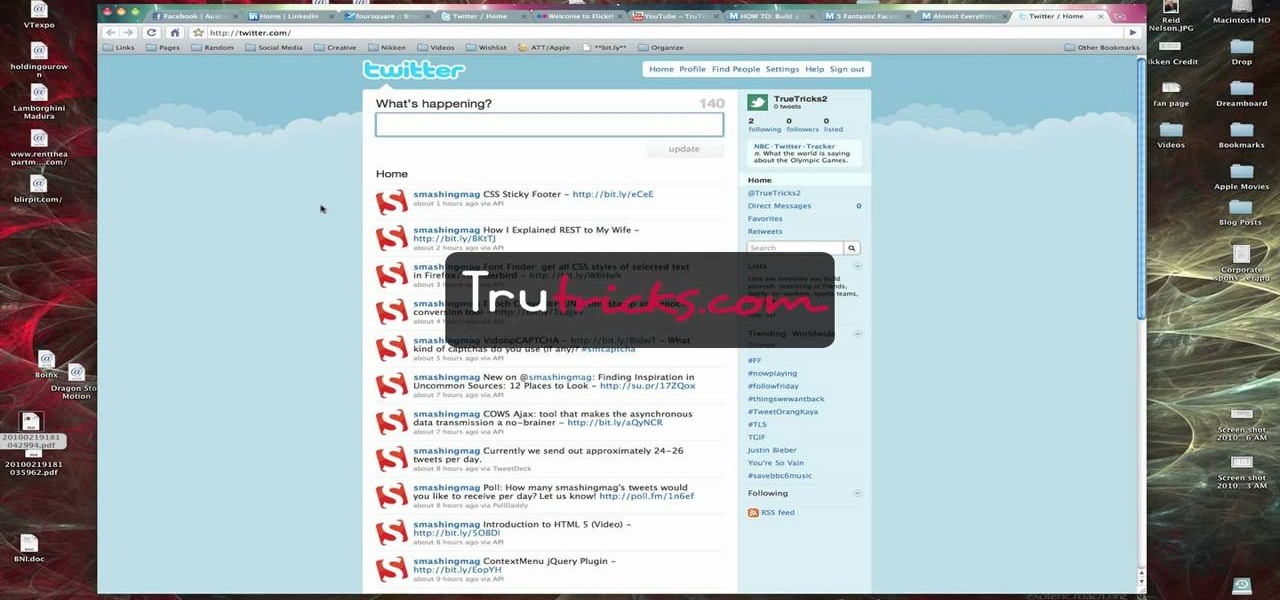
Brian explains us how to use Twitter, one of the best social media networks out there. One thing to notice is that Twitter allows you to send text messages up to 140 characters. In the right corner you can see you account name and your avatar which can be changed from the settings menu. Twitter allows you to follow people and be followed by people. Basically when you follow people you will be able to see messages they post and when people follow you, they will see what you post. Twitter is a ...

In this video, you'll use Scope and create a simple calculator while learning a little about private, public and protected properties in OOP programming. If you're looking to bone up your PHP coding skills you'll want to check this video out.

If you're Apple computer needs a little cleaning, not the hardware, but the software, then MacKeeper is the way to go. This application will help protect your hard drive from junk and other useless data, freeing up much needed space on your Mac. Also, you can recover files, hide private files, clean up your login items, apps and plugins, and more! Watch this video to see how to use MacKeeper.

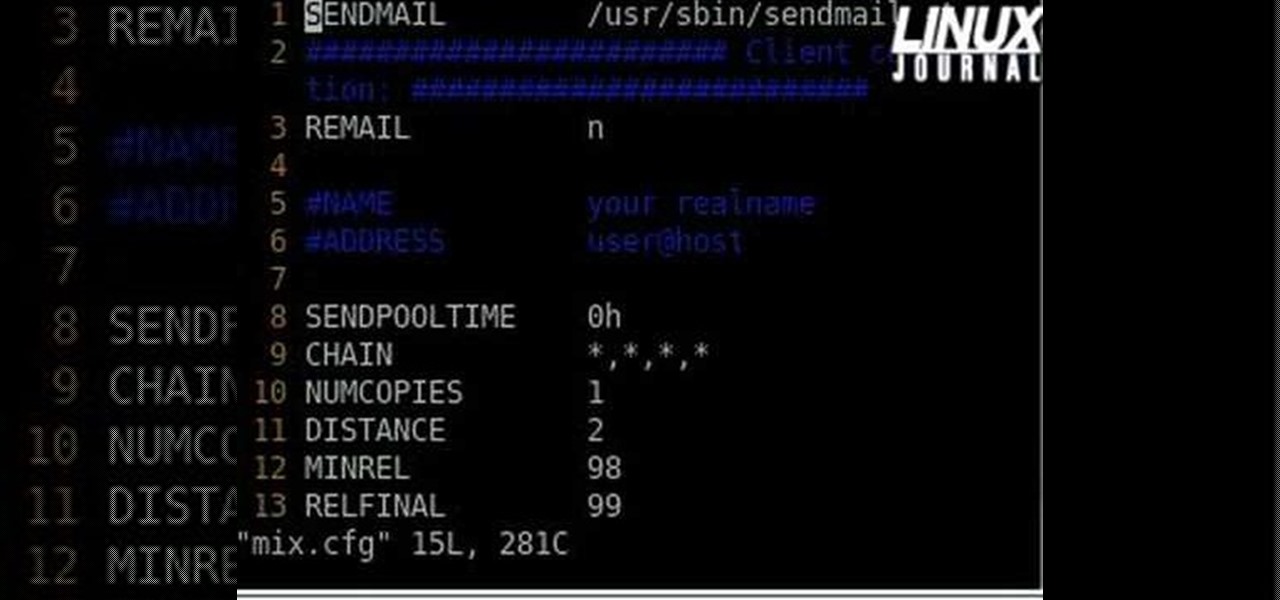
Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.

If you're using the Private Browsing feature in Safari, you'll still need to do more to keep your surfing history secret. This helpful software video tutorial shows you how to cover your tracks in the Apple application Safari.

This is a very basic introductory video that teaches you how to successfully install Quartz Composer on your MAC OSX 10.5 Leopard. Quartz Composer is a node-based graphical data software that uses visual programming language. Built exclusively for use on the MAC OSX, it's a handy software for graphic designers.

It's open season on Zoom, the video conferencing platform that has grown in popularity during the COVID-19 pandemic but has come under fire due to privacy issues.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

There are many reasons to keep adult websites off your iOS device. They can pop up accidentally at the least opportune moments, can give your device malware, and are not welcome in a kid-friendly home.

Make sure your private documents are completely secure. This episode by Tinkernut deals with not only encrypting your files, but also hiding them in a hidden volume.

The people of Iceland forced their corrupt government to resign. A public assembly was created to rewrite the constitution.

Is the proper term nudists or naturalists? Doesn't seem to be too much of a difference, because when it all boils down, they're both still butt-naked on the beach. Nude beaches are fascinating places for the adventurous spirit, but unless you’re an old-time nudist, you probably have questions about the proper way to behave on a nude beach. Well, we’ve got the answers.

Some of the new features in iOS 15 take some getting used to, and the biggest one of those is Safari's relocated search bar, aka address bar. There are more than a few reasons why it's a jarring change, but the good news is that you can return Safari's search bar to its pre-iOS 15 position at the top of the screen.