When conducting covert mobile surveillance with video it is vital to have a good bag that will contain and allow you to get footage in an inconspicuous manner. Always take into consideration the lighting and distance you’ll be at.

You can use surveillance skills to pursue a career as an investigator or to spy on whoever you like. You will need to have a mobile means of making observation and this might include things like pen and paper, camcorder or camera.

When you need to gather information without anyone knowing you will need to utilize covert audio surveillance. There are a variety of ways and technique to most effectively get the information you need.

Do you love a good mystery? Were you a huge fan of "The X Files" or any other freaky movie or TV show? If you are daring and not afraid of the unexplained, Paranormal Investigator may be the job for you. Check out this video to see if you qualify and exactly how you can get into this spooky field.

To become a bounty hunter, you will want to first check your state's laws to see if you need to be a licensed private investigator. If you live in Florida, South Carolina, Oregon, Wisconsin, or Kentucky, don't even try it--bounty hunting is not allowed! Otherwise, your first step is to find a client who needs a target to be caught. Bail bond agents employ bounty hunters to track down people who have refused to show up to court. Find out who your target is. Assemble a file, look into any recor...

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

In this video, Dr.Travis Fox explains how you can tell if your partner is cheating through eye cues. Many people will search and hire even private investigators to find out the truth. Dr. Fox in this video says to "save your money." He tells you about certain indicators that are used to read if they are lying. For example, looking to the left or looking down might indicate that they are lying to you. He does say that it is not 100% always correct but works well in a lot of cases.

In this tutorial, we learn how to unlock the FBI Investigator trophy in Heavy Rain. To get this trophy, you have to get all the clues at the crime scene the first time you play it. While you are in the level, you will need to look at the victim and the things that are surrounding them. There are four clues that are in the video, the last one is harder to find than the rest. Look at the person's hand to help find more. There are a couple clues outside and a couple more outside on the hill. Whe...

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

This is a steamy part of Heavy Rain for PS3. Steamy and sexy. But this is edited for nudity, so don't worry about seeing anything you shouldn't. See how to beat Chapter 5 - On the Loose.

in this episode of Heavy Rain, you confront the Shark. Just try not to get yourself killed when he pulls out that shotgun. Then, are you going to kill him, or are you not? See how to beat Chapter 4 - The Shark.

Now that the identity of the Origami Killer has been revealed, it should be easy to find him. In this walkthrough of Heavy Rain (PS3), you'll be in the killer's apartment. See how to beat Chapter 5 - Killer's Place.

Is the real killer captured now, or is a different man? Will you leave the case or will you continue the hunt on your own? The Origami Killer may still be out there, and it's up to you to find him. See how to beat Chapter 5 - Solving the Puzzle.

The city is full of reptiles, and in Heavy Rain, the lizard is the most treacherous of all. See if the lizard can get you one step closer to solving the murder mystery of the Origami Killer. Porcelain isn't what it used to be. See how to beat Chapter 3 - The Lizard.

Butterflies are usually sweet and innocent, but not in the downpour that is Heavy Rain. In this PS3 walkthrough, see what's up with the Butterfly and if you're ever going to catch the Origami Killer. See how to beat Chapter 3 - The Butterfly.

Can't sleep? Of course you can't, not with a stage called "Sleepless NIght" in the video game Heavy Rain for the PS3. Watch a walkthrough of this level and see if you can get some zzz's, or see if you should be sleeping. See how to beat Chapter 2 - Sleepless Night.

This level of Heavy Rain has you in the Lexington Station, where hopefully you can make it through the crowd without embarrassing yourself. Watch the full video walkthrough to see what happens, and how to continue on. See how to beat Chapter 2 - Lexington Station.

Nothing can beat a father and son. Check out this Heavy Rain video walkthrough for the PS3 on "Father and Son". Do you think you're getting closer to catching the murderous Origami Killer in this level? See how to beat Chapter 1 - Father and Son.

Check out this how-to video to play "Arkham Horror," the board game. You need between one and eight players. The game lasts eight hours! Wow! You play "Arkham Horror" with investigator sheets.

During a Laneway Revitalization project some gang graffiti was encountered and replaced with vibrant art work. The event organizer is a Toronto Police Officer who volunteers for the not for profit organization-The Ontario Gang Investigators Association. In this video an explanation of gang graffiti is offered. The organization Notogangs.org is comprised of sworn members of all areas of law enforcement who network regularly in the mandate of the prevention, intervention and suppression of crim...

The MCL or the medial collateral ligament is a thick fibrous tissue that spans the distance between the bottom of the thigh bone and the top of the tibia on the inside of the knee joint. A MCL injury is caused by stretching or tearing of the MCL ligament in the knee. Learn more about the causes, symptoms and treatments for a MCL injury in this medical how-to video.

The legal drama surrounding Chinese startup Nreal and Magic Leap continues, and now we finally have an update.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

Check out this six-part video lesson on shaving for men. This covers the most uncomfortable places to shave on the body. Body shaving can be sensitive, so do so with caution. Yes, you WILL learn how to shave your private parts with this video.

Austin Paranormal Investigations shows how

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

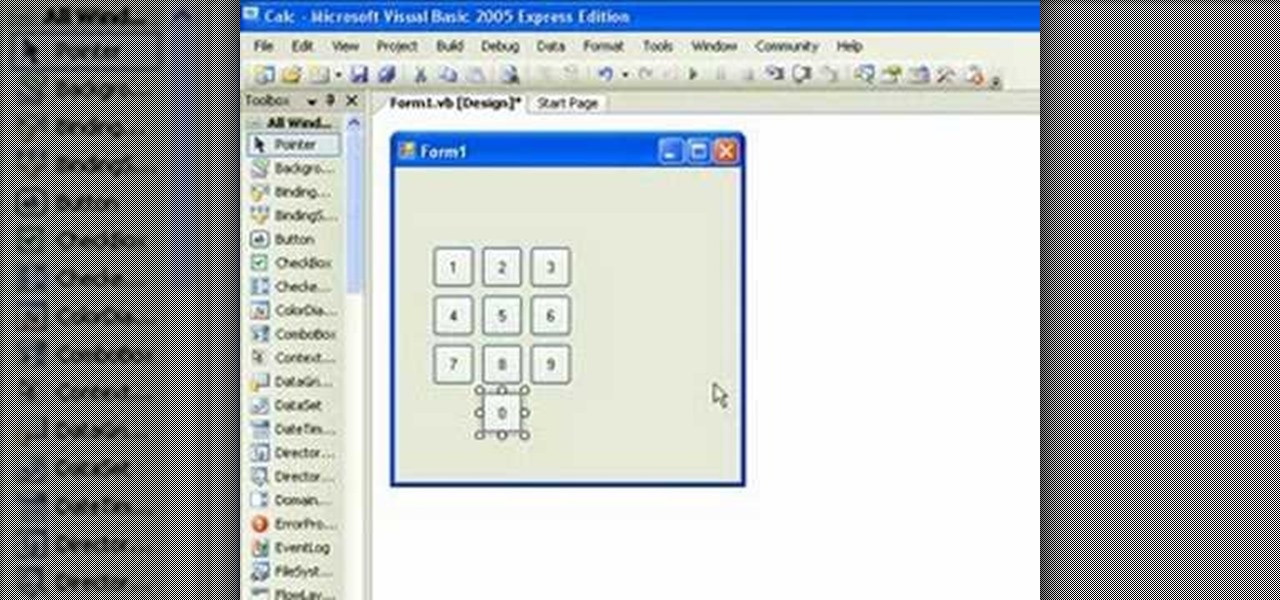
If you're new to the Visual Basic IDE, looking to brush up on your VB programming skills, or simply have a burning desire to code a simple calculator, this three-part video lesson is for you.

Watch this internet video tutorial to learn how to enable Private Browsing in Safari for Windows. This how-to video will help you use private browsing in Safari just in case there's something you want to keep private.

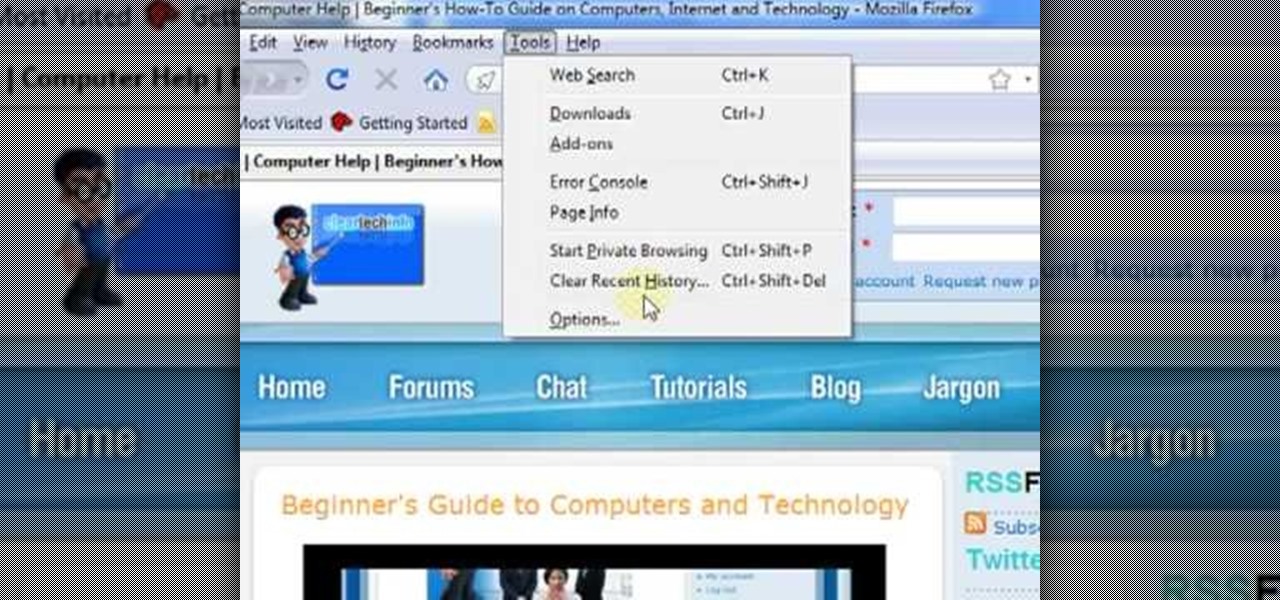
In this ClearTechInfo video the instructor shows how to use the Firefox 3.5+ private browsing feature. To use this feature you need a Firefox version 3.5 or more. Now to start a private browsing session go to tools and click on Private Browsing button. This will trigger a new private browsing session that will now store any browser history, search history or any temporary internet files for that session. But this will still allow you to download and keep files and also add bookmarks. This vid...

This is a four part video where I simply talk about the business-related aspects of teaching English to private students.

If you're looking for some manscaping tips, this how-to video is for you. Learn the tips and tricks to go smooth down there and impress the ladies. Be careful, follow the steps and you too can trim the grass and make the tree look larger. So if you want to shave your private parts, look no further.

Allow for your community to grow and expand by adding in a private messaging system to your website. Even if you're not experienced with PHP or MySQL, this tutorial walks you through the process of setting up the messaging system.

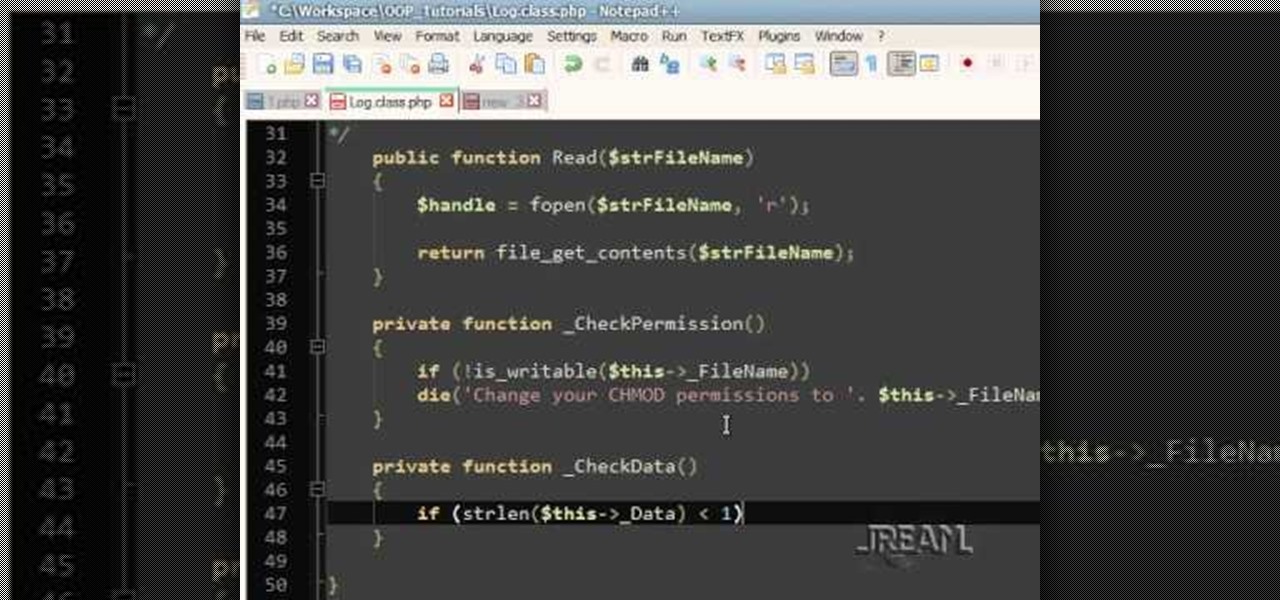
In this tutorial, learn to setup private properties(variables) and private methods(functions) with your PHP OOP programming. This tutorial will have the file logger run through some private methods. Check it out and open the door to the world of PHP programming.

A warning to all of you iPhone users with parents, significant others, and nosy friends: Private Mode in the Safari browser isn't as private as you think. At least, not as private as it used to be back in iOS 7.

If you're serious about keeping your diary for your eyes only then you might have to take some drastic steps. There are some very clever ways to distract from, encrypt, hide, or disguise a diary if you're willing to put in the work.

Nothing on the internet is ever truly private and this hack proves it! Learn how to use PhotoFucket to hack into Photobucket with this video. You'll be able to access Photobucket without a password and view private photos from users. Be careful what you leak though...you might unwittingly create the next big reality TV star!

Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornography cases. In other situations, the graphic images may tell us something about where and when the suspect was somewhere specific.