If you have a smartphone, chances are you have something on it you don't want others seeing. Whether it be photos, videos, or documents, some things are best left private. Not everyone is a saint, after all.
If you've got something on your Windows PC that you don't want to share with the world you're going to want to create a private, password protected folder. This simple video shows how to easily set it up. This works for Windows 7, Vista and XP.
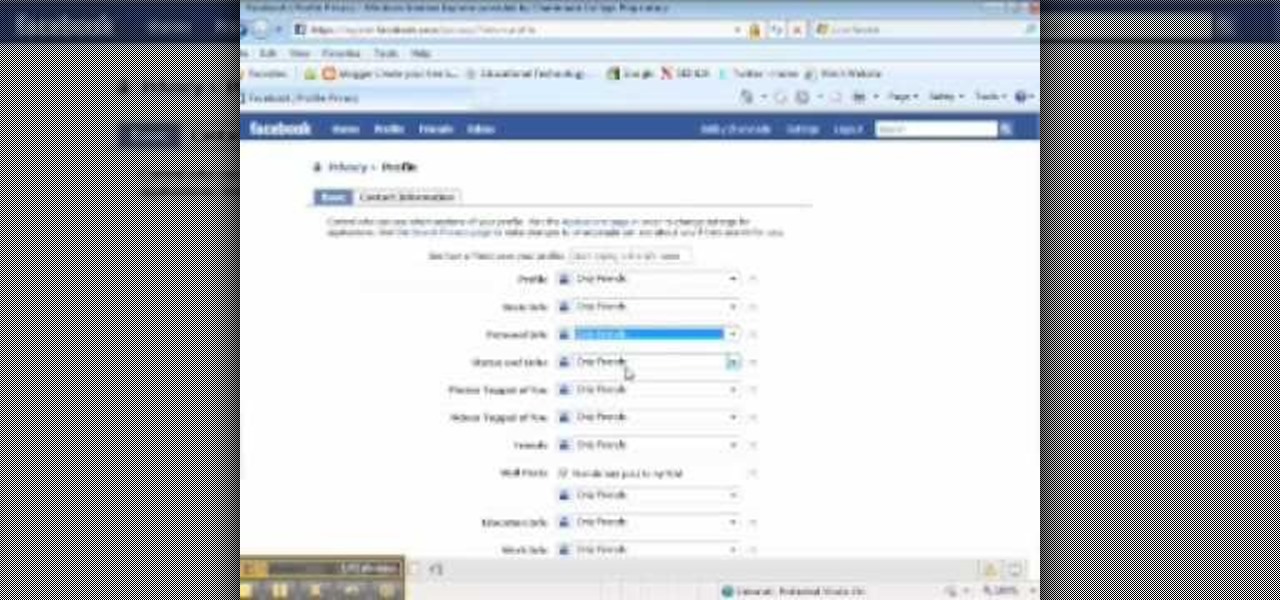
Privacy is important on Facebook, a lot of users don't even realize that their posts are being broadcast to the masses.

For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption.
Despite mounting scientific evidence that viruses can cause changes in learning and memory, the reasons have remained elusive.

Dutch police are using a system very similar to Pokémon GO on smartphones, but they aren't walking around trying to catch little pocket monsters. The purpose of this system is to give augmented reality help to first responders who may be less qualified to work a fresh crime scene. If successful, the idea of a contaminated crime scene could be a thing of the past.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

While many image sites allow you to hide image and video catalogs behind passwords, you can often gain access to these images by "guessing" the URL of the image. This process is called fuskering. Photobucket is one of the popular websites that can be fuskered and this tutorial will teach you how to use Nav.Net 4.2 to fusker private images

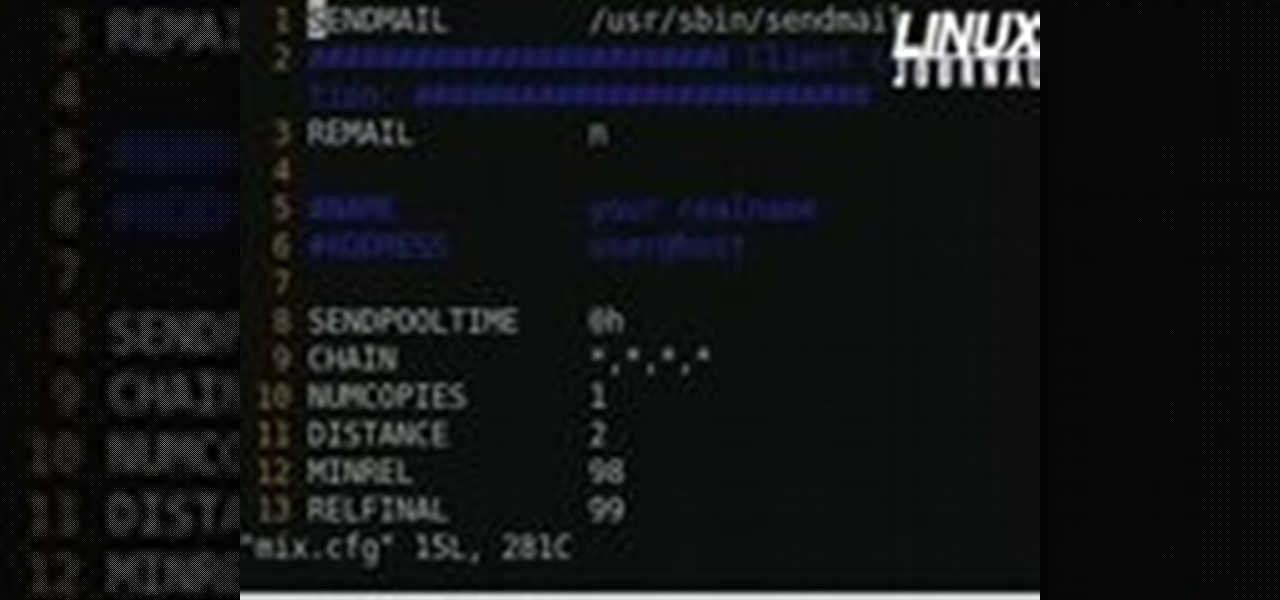
Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.

Google calls it "Incognito," Microsoft says "InPrivate," the other browsers call it "Private Mode," and colloquially it's known as "porn mode." Whatever you call the tracks-free way to browse, here's a trick to force your favorite browser to always start with its privacy protocols activated.

In this video tutorial, viewers learn how to play the game, Borderlands online with Hamachi private network. Users will need to first download the Hamachi private network. Then open Control Panel, and select Network and Sharing Center. Under Tasks, click on Manage Network Connections. Click on the Advanced menu and click on Advanced Settings. Move the Hamachi network up and click OK. Now open the Hamachi and create a new network or create on. Type in the network ID and password. This video wi...

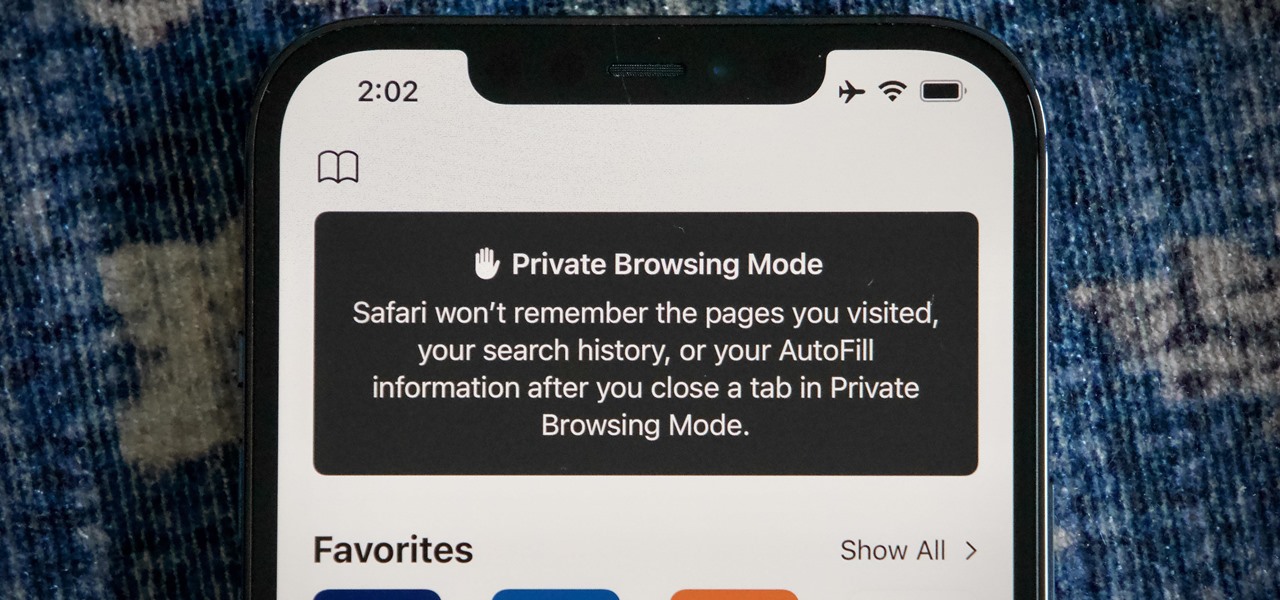
Apple's web browser, Safari, stores information like web history, Google's search history and cookies from websites. There may be certain instances where you want to keep this information private–for example, if you're on a public computer or have borrowed a computer from a friend, you may want to keep that information to yourself. For a step-by-step guide to using the private browsing feature in Safari, watch this OS X video tutorial.

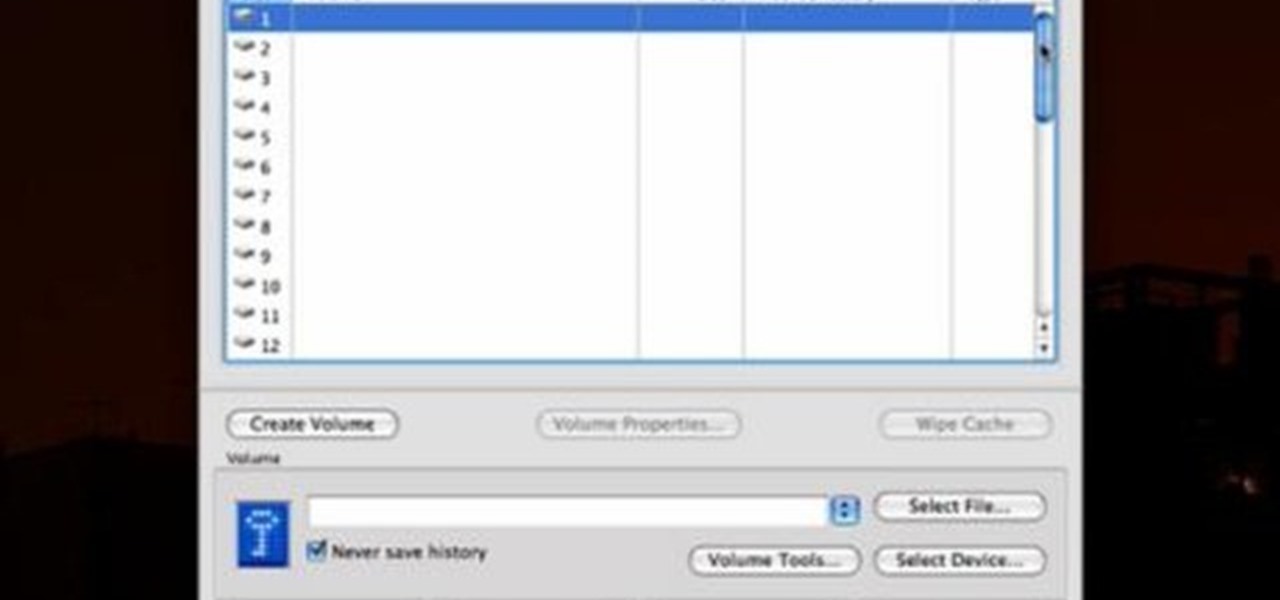
Check out this video tutorial to see how to keep your private files private, even if you have to email them to yourself at your office? TrueCrypt, an open source piece of software, lets you encrypt your files so they remain accessible only to you. This works on any platform; Windows, Linux, or Mac. So, watch this video to see the TrueCrypt download process, how to install it, and how to create an encrypted volume on your hard drive.

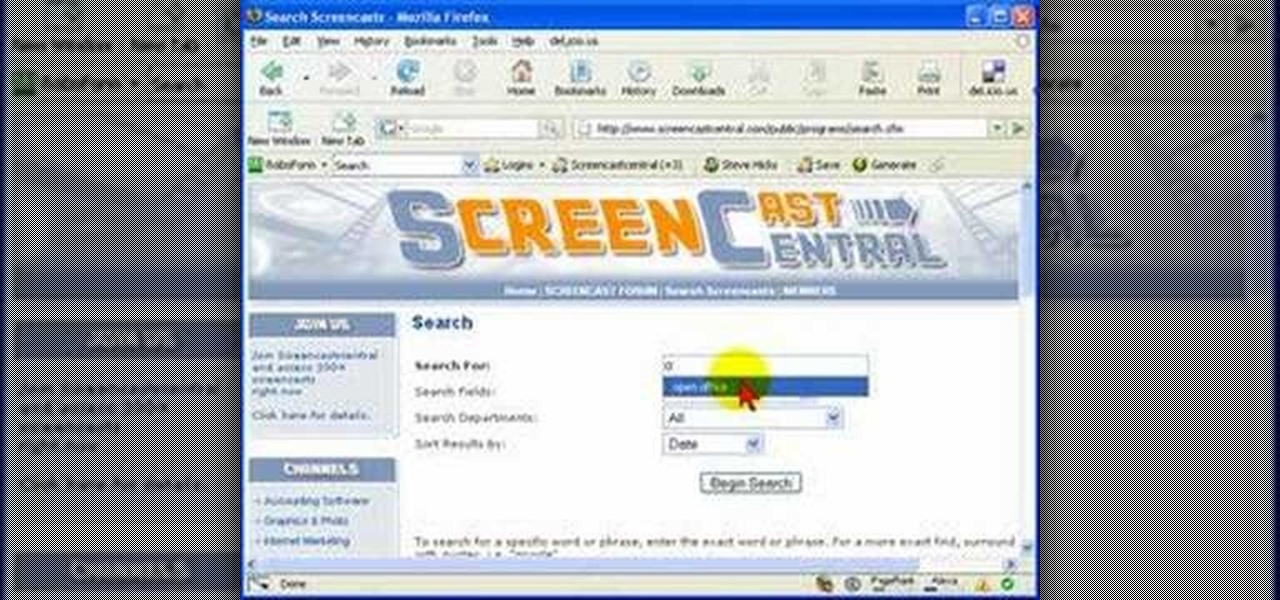
One method you can use to protect yourself, is to ensure you clear your private data, such as your search history, and in this screencast tutorial, we show you how to do just that in Mozilla Firefox.

Getting your pilots certificate may be on the expensive side, but after only a few weeks of training you can be flying all over the country! We show you some tips on the path to getting a private flying certificate in this video, and if you're afraid of heights, just do what Veronica did -- pretend it's a video game!

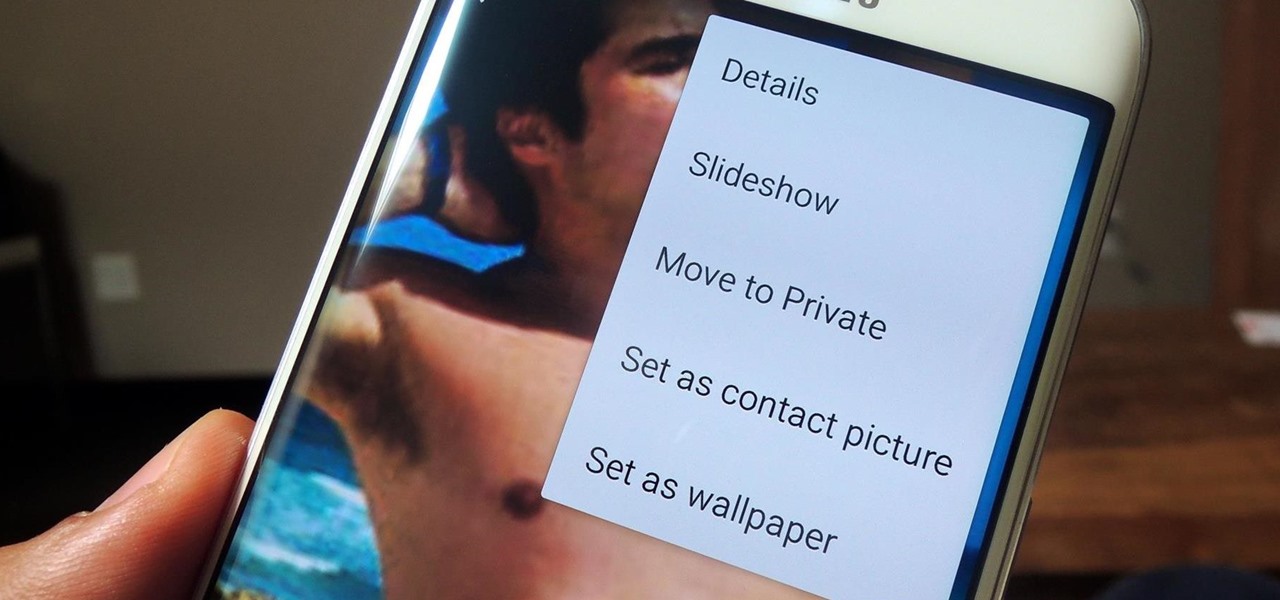
Whether it's embarrassing pictures and videos on your smartphone, or files you just don't want anyone reading, there are plenty of ways to hide them. For most devices, that means installing third-party apps like Gallery Plus - Hide Pictures, Sectos - Photo & Video Vault, TimeLock, or Hi App Lock.

The creation of private browsing was brought upon by the backlash against ad tracking and other ways that sites and agencies take away users' privacy online. People were tired of getting spammed with ads for Vitamin C pills simply because they visited WebMD. Private browsing is now built into all of the major browsers and is used frequently. While private browsing is more infamously known as the "Porn Portal," and does prove to be a great way of keeping racy content out of the sight of others...

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

Whether you're a celebrity or someone with something to hide, Facebook allows you to keep your "friends list" private so you can protect the identities of your Facebook friends. But it only kind of protects them.

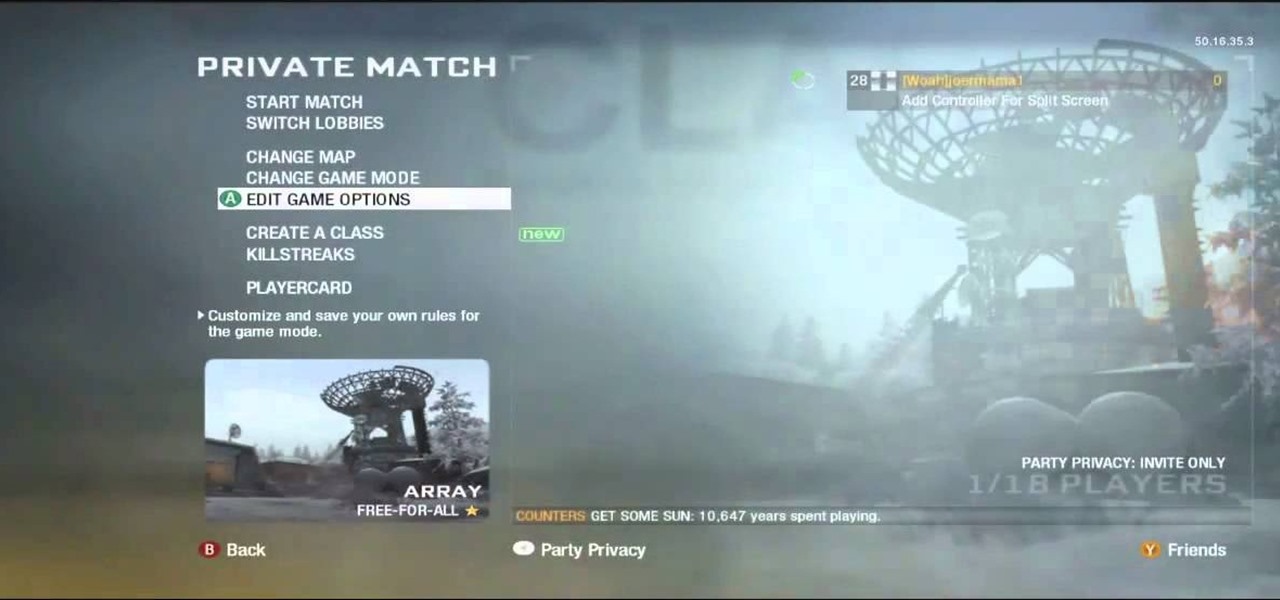
This video shows the viewer how to boost, gain XP very easily, on ‘Call of Duty: Modern Warfare 2’. The first stage is to get a friend to join your game. Then search for the Team Tactical game mode until domination appears. Then back out and go to a private match. Change your clan tag to ‘aaaa’ and hover over Ground War until the game starts. The map usually used for this is Rust as it is so small. The game will behave like a private match but you will be gain XP for all kills. This g...

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

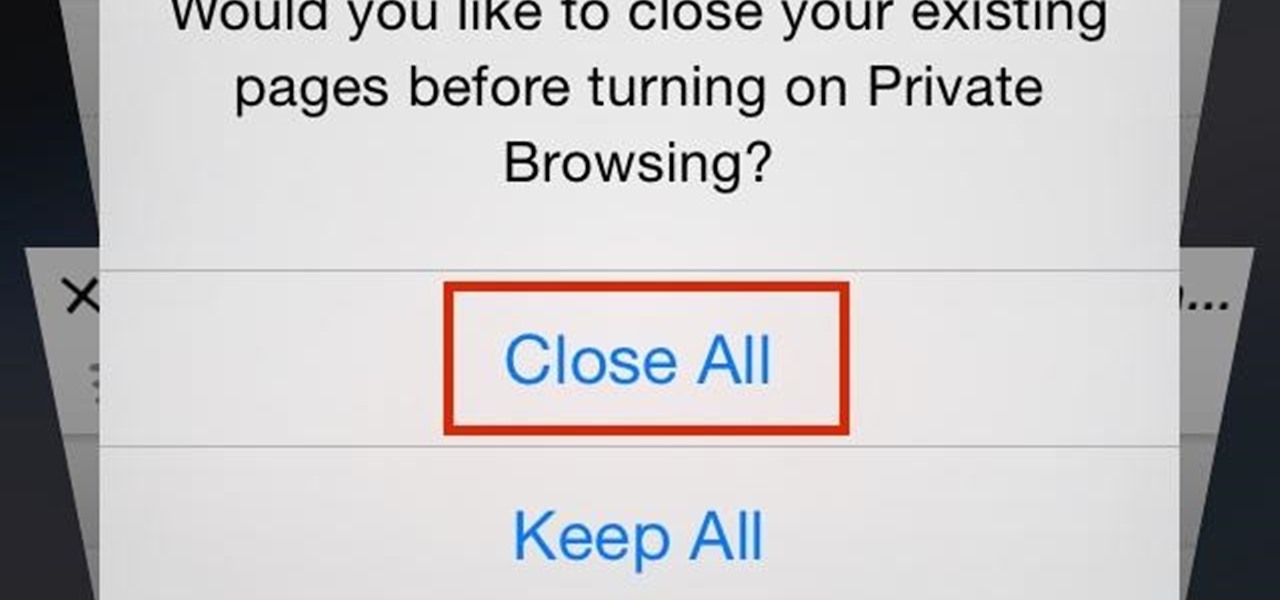
Closing all of your tabs open in Safari is not an exceptionally quick task—you have the choice of either tapping the X on the left edge of each page or swiping each tab to the left of the screen. If you have a load of tabs open, you'll have to swipe or tap through all of them. Instead of wasting time, I'm going to show you the quick way of closing all of the open tabs in Safari.

Stay secure on public wireless networks by making your own FREE virtual private network (VPN). This tutorial shows you how to set up an OpenVPN server and connect to it from your laptop.

In this video, we learn how to clear browsing history and cache in Firefox and Internet Explorer. First, while in Firefox, go to the tools menu, then click on clear private data. In the new window, click on the items that you want to have cleared, then click "clear private data now". After this, the computer will clear out all the internet files. Next, while you're in Internet Explorer, go to the tools menu, then click on "internet options". Once in here, click the appropriate sections to cle...

Ever wanted to find out who stole the cookie from the cookie jar? Take a page from crime scene investigators and get the proof you need.

When you open Safari for the first time after updating to iOS 15, you'll instantly notice its search bar is now at the bottom, and its Page Settings menu has moved with it. For tabs, moving between them is as easy as swiping on the Tab Bar or selecting one from the new grid view, but you may get confused whenever it's time to open a private window.

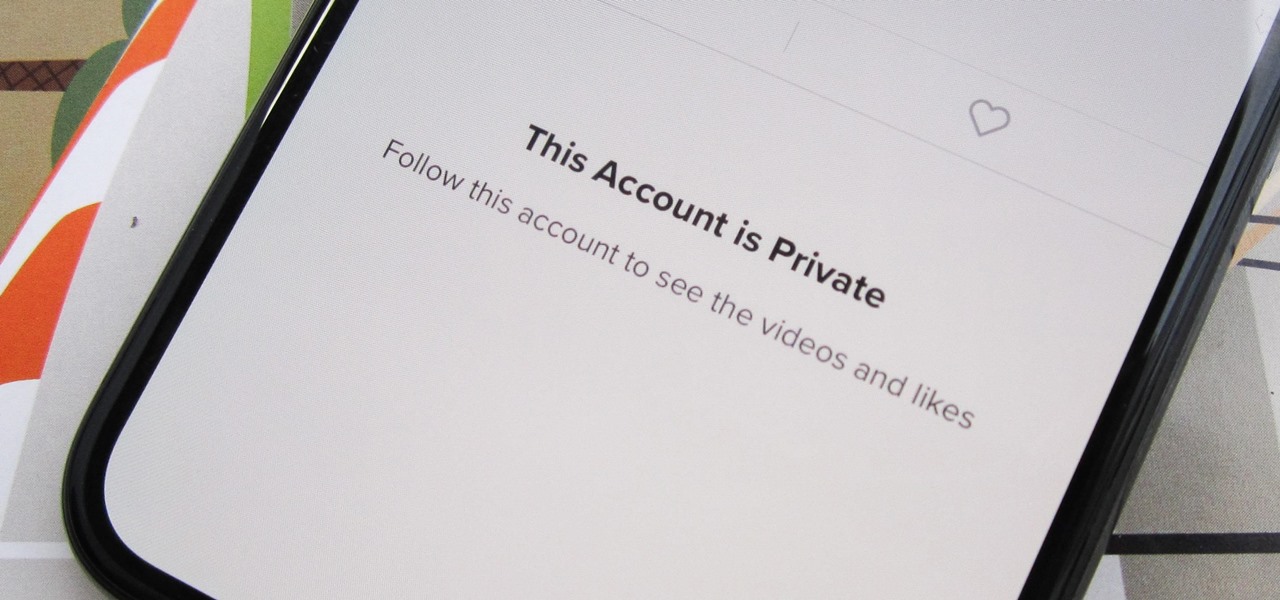
Can you trust every user you come across on TikTok? The answer to that may depend on how use the service, but the real question is — can you trust every user that sees your content? Not everyone on TikTok is someone you want viewing or interacting with your content, and there's a way to prevent them from doing so.

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.

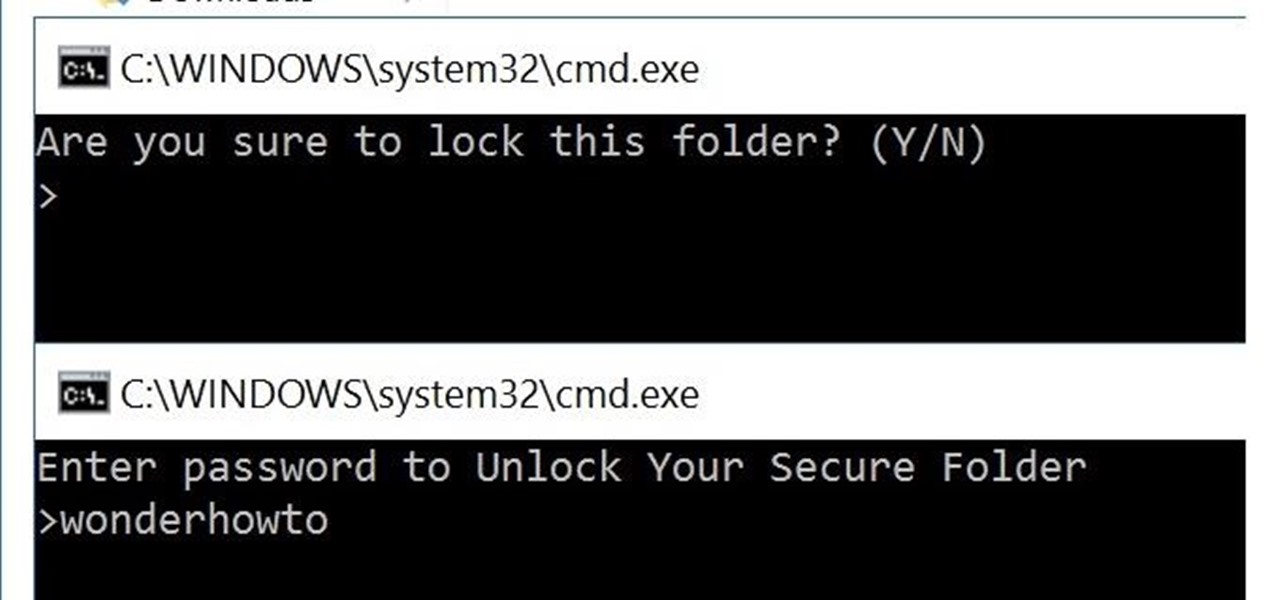
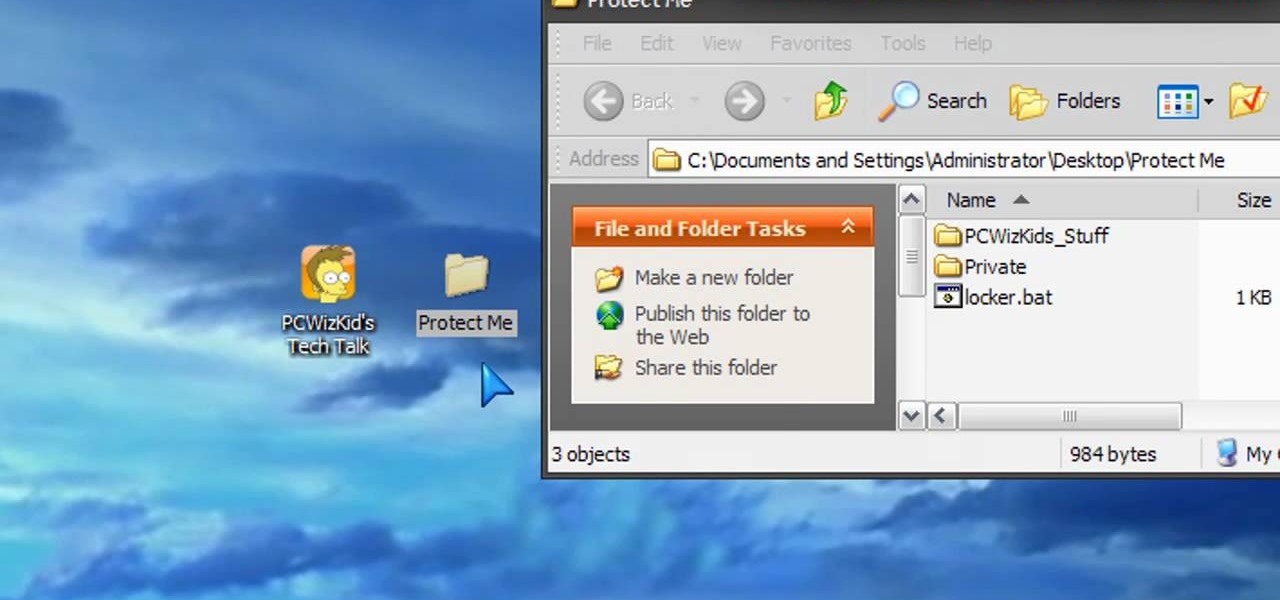
You can easily lock any folder on your Windows computer with a simple Notepad hack. By creating a batch file, you can hide a folder and require a password be entered before it becomes visible and accessible. This is a great tool for locking sensitive information, like pictures, financial statements, and a lot more.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

There aren't a lot of games with 3D maps where you can't break out of the levels in some way, and Black Ops is not different. This video will teach you a barrier breaker that you can use to get out of every multiplayer map in the game. Only use this in private matches unless you want it to go away!

Ever wish there were a way to upload a video to YouTube without making it available to anyone with an Internet connection? While you might know about the option to make your uploaded clips private, limiting their viewing to 25 users of your choosing, you might not know about the newly introduced "Unlisted" status, which allows your videos to be viewed by only those people who know the video's direct URL. For more information, watch this free video guide from Tekzilla.

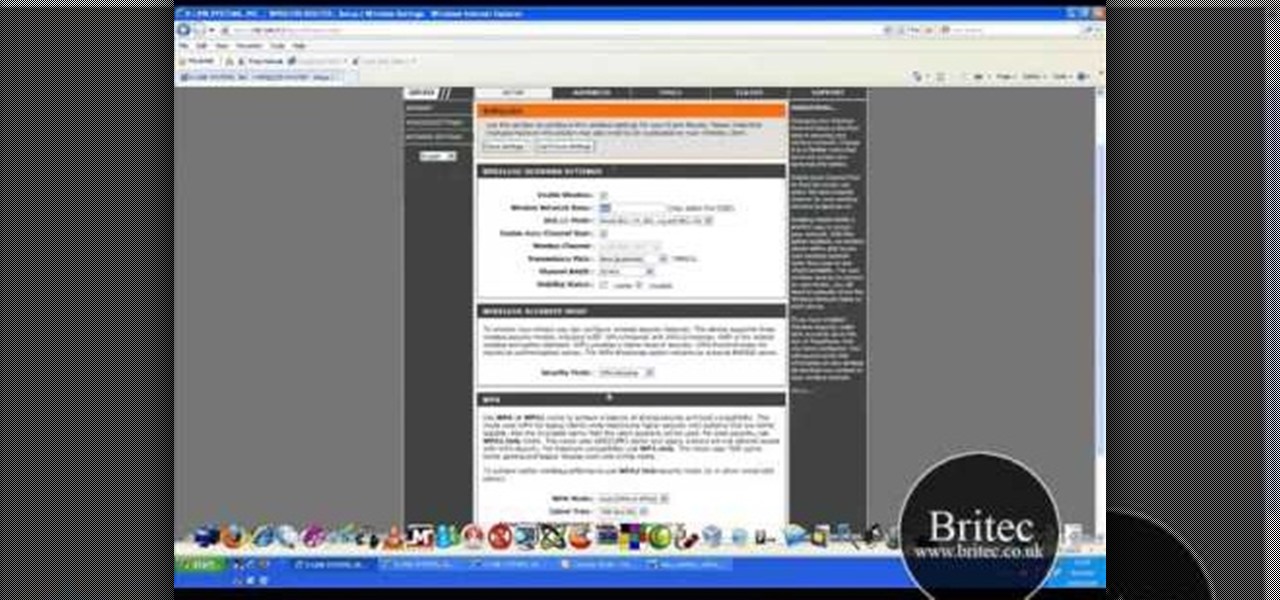
In this tutorial, Brian teaches us how to make your wireless network secure. First, go to the start menu, then go to run and type in "cmd", then type in "iconfig /all". Now a new window will pop up and you will look for the default gateway. Find the IP address to log onto the routers you have. Now, type in your IP address into your address bar on your internet browser. You will be asked to log into your account with your password and user name, which you can find at the manufacturers website....

Lady Gaga is one of the most secretive women in show business, hiding behind her stage performer mask and outrageous costumes so often that we can hardly believe there's a real person underneath all that fluff.

If you're worried about having your private information taken away from you by hackers and other malicious people, this tutorial may help you. This tutorial will help show you how to easily use and understand the phishing filter in Internet Explorer 8. It only takes a couple of clicks to activate and can be the difference between making sure your private information is secure or out in the open for others to use. Good luck and enjoy!

This video tutorial from ChaminadeENN shows how to set your Facebook account to private mode. First what you need to do is to sign in to your Facebook account.