First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.

In this video tutorial, viewers learn how to clear their cookies in Mozilla Firefox. Begin by opening the web browser. Then click on Tools from the top menu and select Options. In the Options window, click on the Content tab and deselect "Block pop-up windows". Click OK. Now click on Tools and go to Options once again. Click on the Privacy tab and click on Clear Now under Private Data. Make sure that Cookies and Cache are checked and click OK when finished. This video will benefit those viewe...

Do you know what an idiom is? If you don't, this English lesson is sure to make you an expert on idiom usage.

This video tutorial from TutVid shows how to create a simple movie poster text effect in Adobe Photoshop CS4.
New to Windows? No problem... here's a beginner's video tutorial that will teach you how to install Windows 7 Visa with a USB flash drive. See how to take the Windows ISO and put it on a USB flash drive for fast and easy installation.

Learn how to make biodiesel. Maurice Vanegas is an executive for a private charter company. The biodiesel made is used in a fleet of transit buses, executive buses, and diesel trucks. The biodiesel comes from virgin soybean oil and used vegetable oil. Since July 2006, the company has produced in excess of 20,000 gallons.

This 4 part video series is a gift from me to all the other singers out there who have shown me such great love and support. It contains a full vocal warmup that will improve tone, expand range, and increase control. This is pretty much the kind of warmup that I might do with a private client, but it's for you guys - free of charge.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

In Safari for iPhone, as far back as iOS 7, you can request the full desktop version of websites. The process was streamlined starting in iOS 9, but the process remains relatively hidden and easily missed. Now, iOS 13 shines a light on it, as well as adds functionality to set the desktop view for individual websites indefinitely.

In order to increase the security and harden the integrity of an email account and its content, you'll want to use PGP on your Windows, macOS, or Linux computer. This is usually the first thing security analysts do to protect communications with encryption, and everyone else should consider it too, especially since there's an easy way to incorporate PGP that anyone can follow.

It turns out that the government of Saudi Arabia has managed to do something last month's Game Developers Conference couldn't — give us a few new glimpses of the Magic Leap One being worn by someone other than Shaq.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

It seems like there's a cyber security scare every day. Consumers are growing increasingly concerned about the safety of their accounts, and they have reason to be. Hackers will maliciously attack you anywhere — and we mean anywhere — they can to get your private information.

A federal judge wants answers after an Uber engineer accused of data theft pleaded the Fifth in the ongoing Waymo versus Uber battle. This privilege would protect the accused, Anthony Levandowski, of self-incrimination and handing over specific documents demanded in a previous subpoena and forthcoming deposition.

You're only as smart as your communication skills allow you to be, as other people will simply never know your inner genius if you can't effectively express yourself. Regardless of the medium—be it a Facebook post or even a simple text message—this fact remains true.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

After lots of anticipation and leaks, the LG G3 has been unveiled. Sporting a gorgeous 5.5" Quad HD display, the first of its class for smartphones, this flagship device is ready to put some scare into Samsung and HTC. It's currently available for purchase from AT&T and Sprint, and for preorder at T-Mobile and Verizon Wireless.

No matter how careful or decent you are, there will always be pictures or videos that you want to keep private. They say a picture is worth a thousand words, but if someone were to go through my photo gallery, only one word would be coming out of my mouth—"%@&#!!"

I want to talk about growing up with burden of acne. I frequently receive comments and private messages about kids being bullied for having acne, this is not right. Everybody is beautiful in their own way and you should never let the haters put you down! Love yourself =)

Whether or not you believe that the government is snooping around in our private emails, texts, and phone calls, it wouldn't hurt to protect ourselves a little better in the digital realm.

This video features a very handy technique for writing a cover letter in less than a minute- and all you need is a tool called Text Expander, which can be easily downloaded. The basic idea behind this program is that you can create shortcut keys to text that you commonly use, so you can enter in all of your basic cover letter information very quickly, and only have to customize small sections.

Although people said that a discus tea cake is hard to break, this how to video will show you how to use a letter opener to open one. Tea cakes can be broken up to make tea for drinking to serve with cake. Watch and learn how simple it is to break up a discus tea cake.

This how-to video demonstrates methods for breaking up a Puerh tea cake. Puer tea cake refers to a type of Chinese tea for drinking, and not cake served at tea time. Watch and learn how simple it is to break up a hard Puerh tea cake with a letter opener.

Tech tends to move forward without looking back, but that doesn't mean new is always better. One feature that dominated mobile phones in the late '90s had made a comeback thanks to Apple, and you can take advantage of it on your iPhone when making calls.

Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning.

Following someone on Twitter is an investment. You virtually agree to have their opinions, tirades, and hot takes spewed across your timeline. It can get annoying real quick if they're known to post controversial comments periodically. However, there are other ways to stay updated on someone's tweets without you having to hit the follow button and go all in.

Not all threats to our privacy come from hackers thousands of miles away. Often, we just want to keep our data safe from those around us, who may snoop in our phones or demand we reveal our secrets. That's where BlackBerry Locker comes in.

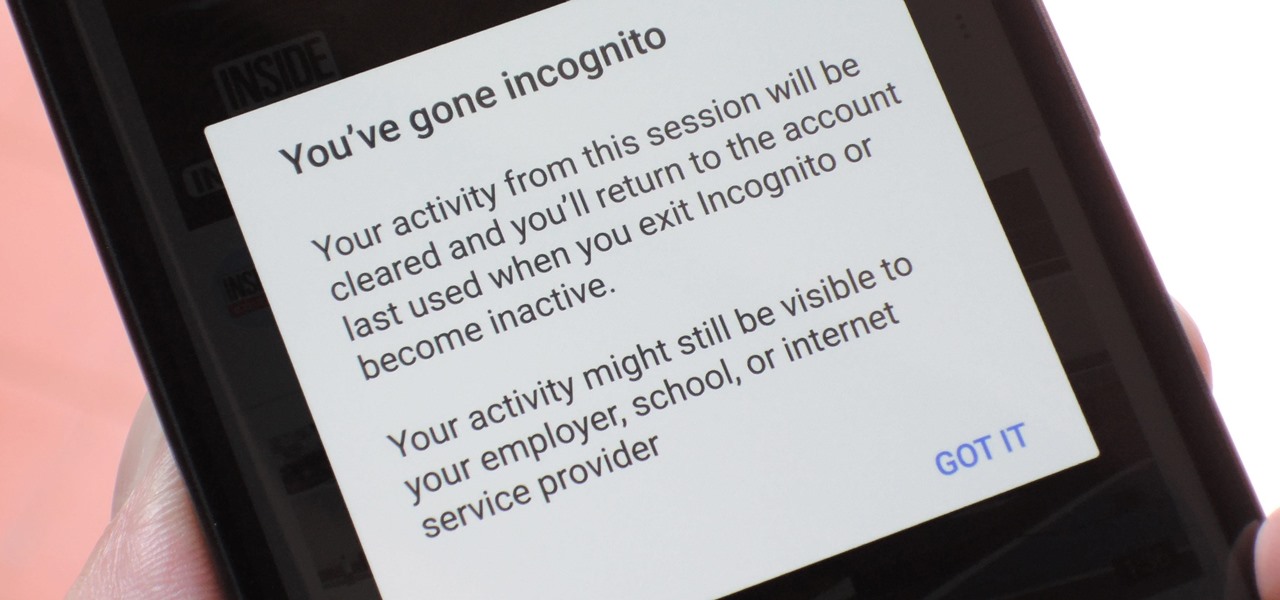
Incognito Mode is a privacy feature that was popularized by Google Chrome, and it recently made its way to GBoard. Now it's coming to the YouTube app to help make your video watching experience truly private.

Another AR cloud savior has emerged this week in Fantasmo, a startup that wants to turn anyone with a smartphone into a cartographer for spatial maps.

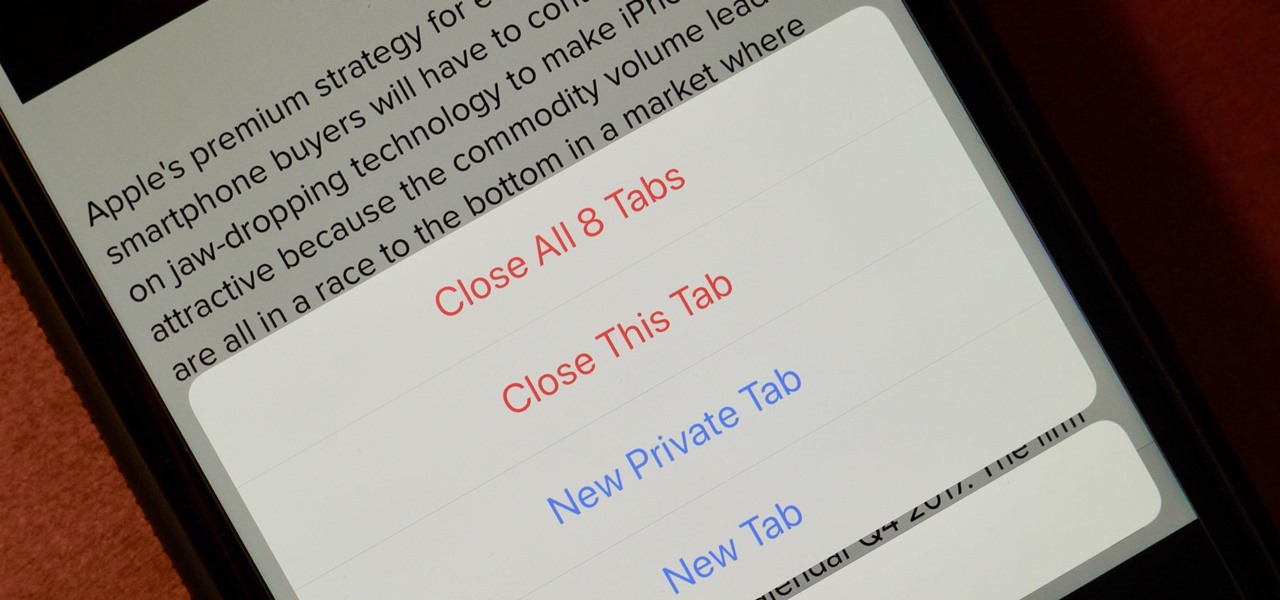
If you're like me, your iPhone has way too many Safari tabs open. Links from other applications open up new tabs automatically, it's too easy to open up new tabs to search, and sometimes you're skittish about closing pages you don't want to forget about. This all creates a massive mess that requires cleaning house, and there's an easy trick to doing just that.

While many analysts predict that the market for augmented and virtual reality will continue to grow over the next five years, now is the time for investors to get in on the ground floor.

The $25 million development alliance Jaguar Land Rover's mobility unit InMotion has formed with US-based ride-share firm Lyft reflects how the British luxury carmaker is leaning towards a fleet service business model for its driverless offerings.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

Hello My Fellow Hackerzz.. This is my first How-to and i'll be updating the “Hacking Android Using Kali” to msfvenom and some FAQ about known problems from comments. So Here we GO!!

There are many reasons to keep adult websites off your iOS device. They can pop up accidentally at the least opportune moments, can give your device malware, and are not welcome in a kid-friendly home.

Now that you've updated your iPad, iPhone, or iPod touch to iOS 8, there's a lot of cool new things to explore. If you felt a little overwhelmed from all of the detailed information available in our Coolest Hidden Features of iOS 8 post, then I've got a simple breakdown of all of the new features available with quick links to their walkthroughs and pictures, if available. Watch the short video roundup, or skip below for the list.

When browsing the web, you may not be quite as anonymous as you think, especially if you are using public WiFi. The easiest way to stay as anonymous and safe as you are going to get, is to use a VPN (there are a number of great free ones). In this tutorial, we will show you how to set up a VPN on Android, and how this protects you.