Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.
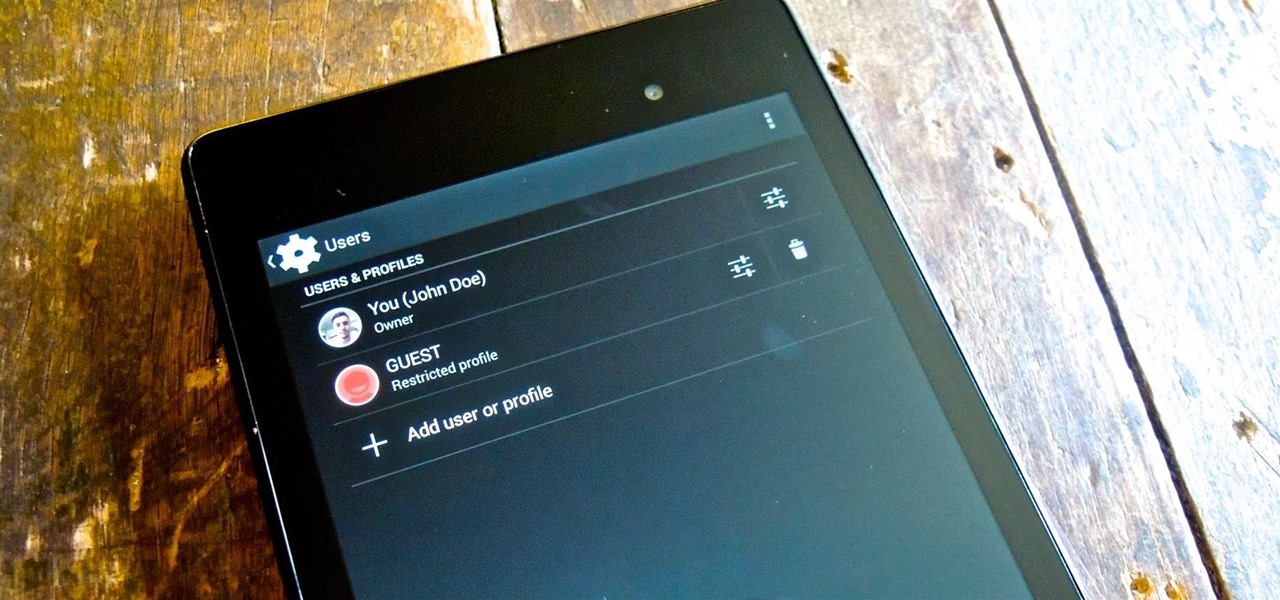
Whenever I hand my tablet over to someone, my heart always races for a second at the thought that they may stumble across my private pictures, texts, and videos. I trust them, and they may not be the snooping type, but it can be easy enough to come across private stuff by accidentally opening a gallery or messaging app.
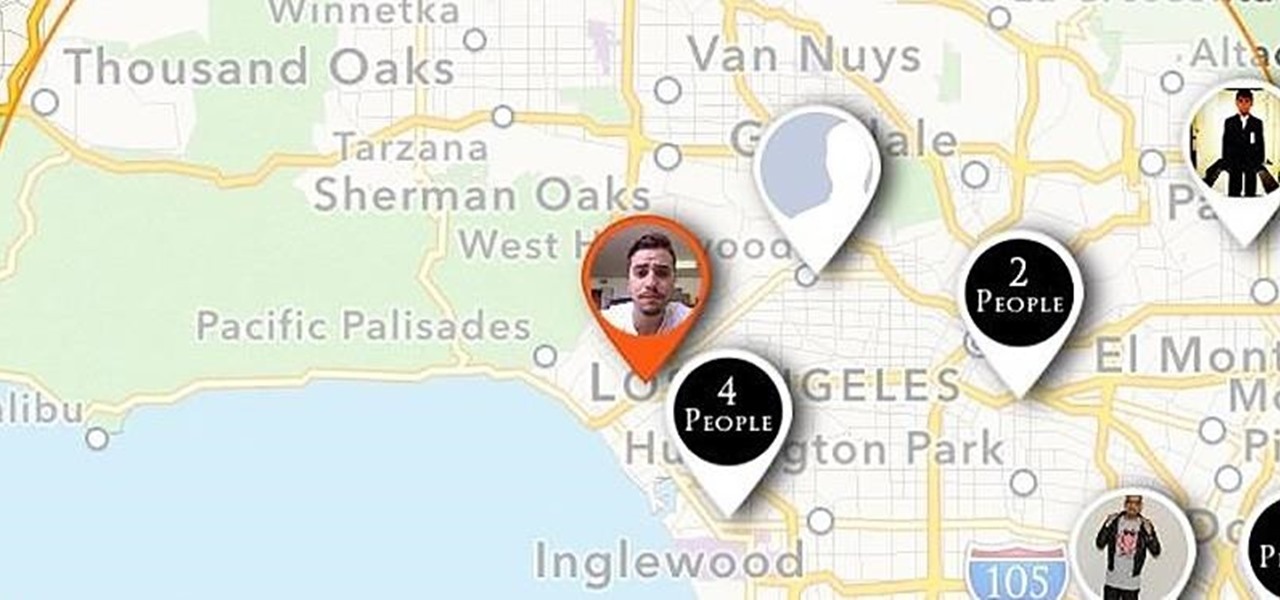
Imagine that Tinder fornicated with Facebook and had a baby. The product of that union would be the hideous, yet overwhelmingly interesting SocialRadar, an app dedicated to stalkers and stalkees.

I can be pretty forgetful. If there's something important to remember, I need to jot it down right away or risk losing it forever.

My friends can be pretty shitty sometimes, but they're my friends nonetheless. On various occasions, they've secretly taken my device and made me look foolish by posting crude and embarrassing posts to Facebook, Instagram, or Twitter. With friends like these, who needs enemies, right? And it's because of these types of friends that we need to substantially upgrade the app security on our devices.

Instagram recently released their new Instagram Direct messaging feature in their Android and iOS apps, which lets users share private photos and videos directly with individuals or groups of up to 15 users. However, there are no restrictions on who you can send private photos or videos to.

Scrabble charms and pendants are gaining popularity in the world of crafts, because they're easy to make and fun to wear. They make great gifts, can be fully personalized and turn Scrabble into more than just a board game!

Learning American English is often difficult when faced with two words of similar spelling or sound. This is certainly true in the case of "we're" and "were".

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to build a sign in Photoshop with 3D lightbulbs.

English can be difficult because few words are spelled phonetically, and every rule has exceptions. But you can become a champ in no time by memorizing a few basic rules.

If you've ever had a little trouble trying to program your calculator, you may find a little relief with this four-part video tutorial. Here, a Texas Instruments (TI-84 Plus) calculator will be used to explain the programming process. The four parts include:

Uncial calligraphy is characterized by rounded strokes. Learn more about forming letters in calligraphy and how to write using the art of calligraphy in this free online video series.

This will show you how to arrange the word "CIVIC" using only the letters T, L, I, M, O, K, W, I, and O. What? No C's? Well, that's what makes it a riddle, right? Why do the letters not look like Scrabble tiles? Well, sometimes there's just too many questions, and sooner or later you're just going to have to stop asking them.

This video will show you how to pronounce the alphabet correctly in English. If you have trouble hearing the correct pronunciation, and telling the difference between "c" and "d" and "b", this video helps you out with clear enunciation of each letter. Watch this video to pronounce each English letter correctly.

Ever want to have a friendship bracelet with your own personal saying on? Well, it's going to take a lot of experience to get there. Start off with learning the basics of friendship bracelet making, such as the basic knots and skills. When you think you are ready for a challenge, try to write your name in a bracelet. This video is ideal for learning the letter "i". "I" is a very common letter to be in first names and it is probably found in yours too! After learning how to make the "i" try to...

In popular music, a slash chord or slashed chord is a chord whose bass note or inversion is indicated by the addition of a slash and the letter of the bass after the root note letter. This how to video explains how to play slash chords on the guitar. This tutorial also briefly covers palm mutes.

QWOP. What the heck is QWOP? It's seems like an acronym, but it's not. Think QWERTY and you'll get the picture.

This video shows us how to use the following functions in Excel: average, count, counta, min, max, and sum. First, start off by create a set of numbers to work with. After that, click on an empty cell that you want to use for the functions. To do an average, click on the functions button on the top right corner of the menu bar, you'll see a list of all the functions that are available. Select average, and then highlight all the numbers that you want to find the average of. Repeat the exact sa...

In this Software video tutorial you will learn how to change the font color in Word 2007. The default font color in Word 2007 is black. But, you can change the color of the font to just about any color that you want. Click on the ‘home’ tab of the ribbon on top of the page and you will see a small window with the letter ‘A’ in it. Click on the arrow next to it and it will display a color palette with automatic, theme colors, standard colors and more colors sections. Here you select any color ...

Whether it be for a school project or just a funky looking journal or letter, making your paper look antique is very easy. Antique paper is great for invitations, props, unique stationary..lots of things! This tutorial will teach you how to age your brand new paper instantly for a neat, old fashioned look.

Tasktutorial teaches you how to create a sound on/off button using Flash. Name the first layer Actionscript. Go to frame 1, then window - actions. Add stop(); Go to frame 2, then window - actions. Add stopallsounds(); Create a new layer and select the text tool. Write off on. Change the color to black. Select the text and hit CTRL + B to break apart the letters. Select off, hit F8 and select convert to button. Name it off. Do the same for on, but name it on. Double click to open the off butto...

You've written the great American novel, and you want to make sure that your story stays yours. Register your copyright and preserve your intellectual rights. In this video, learn how to copyright produced material.

Do you have coworkers who use the hunt-and-peck method of typing? This trick is guaranteed to drive them completely bonkers.

Learn how to remove ink stains from fabric. Getting ink out of fabric is a tricky business, often best handled by a dry cleaner. If you want to try it yourself, though, here's what to do.

Make custom shirts with airbrush designs! Learn how to make letters, designs, and dots on a shirt with airbrushing in this free craft video series from a professional airbrush artist.

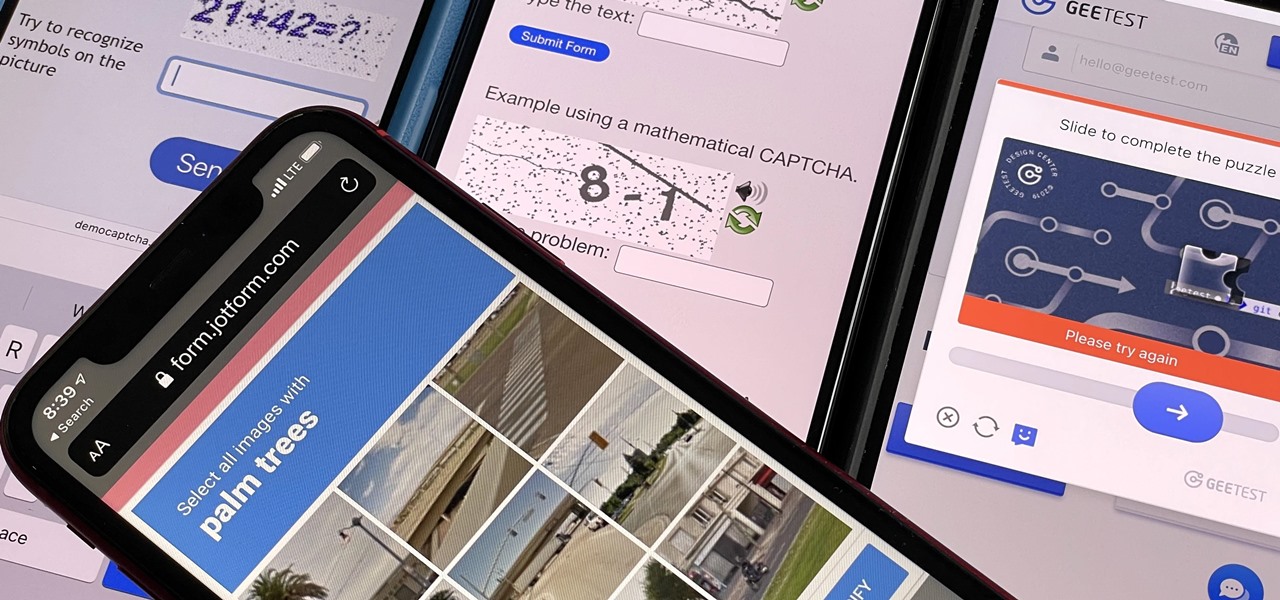
If you hate matching images, typing letters and numbers, solving math problems, and sliding puzzle pieces for CAPTCHA human verification, you'll love Apple's newest privacy feature for apps and websites.

Safari's private browsing mode on your iPhone won't sync to other Apple devices or remember your search history, AutoFill data, or visited webpages. Still, it doesn't stop anyone who accesses your iPhone from opening your private tabs. If you don't want anyone snooping through your private tabs, use Chrome instead so you can lock the tabs behind biometric authentication.

Almost 190 secret characters are hiding behind your iPhone's default keyboard, and I'm not talking about what you see after tapping the "123" or "#+=" keys. These special composite characters can include accents, dots, and other diacritics, and you'll even see some strange typographical characters like the section sign, inverted marks, and per mille symbol. Here's how you find them.

It's open season on Zoom, the video conferencing platform that has grown in popularity during the COVID-19 pandemic but has come under fire due to privacy issues.

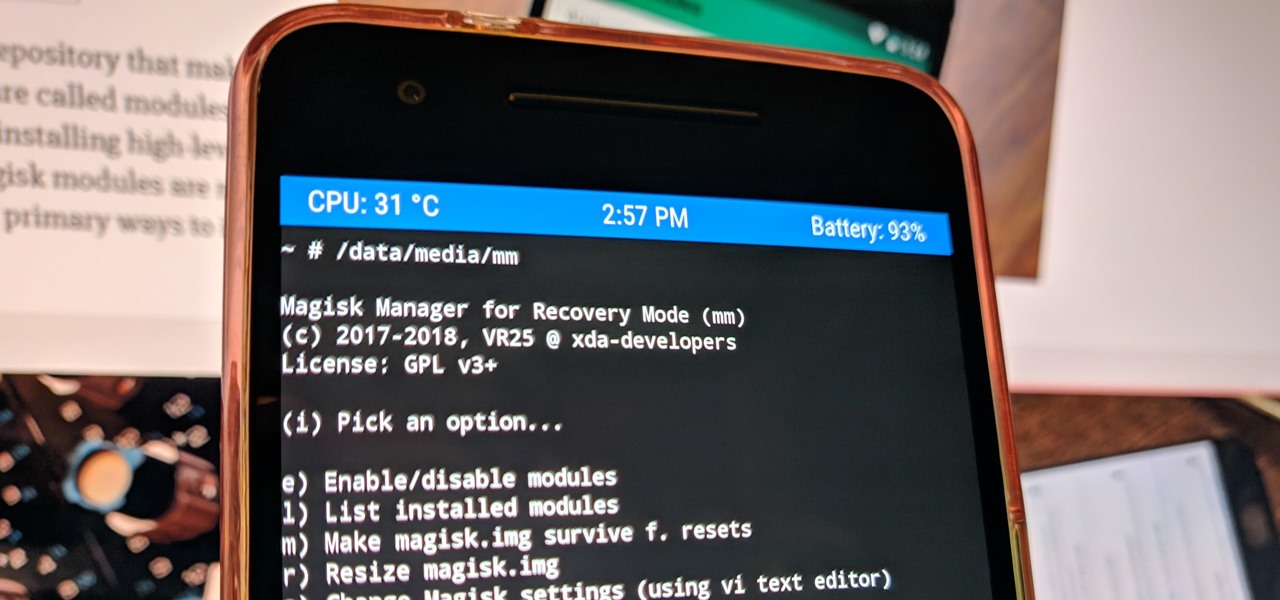
When it comes to customizing Android, there's nothing quite like Magisk. You can potentially combine dozens of modules to create a one of a kind user experience tailored to you, but not all modules will work well together. You might run into a bootloop by accident once in a while, which could cause some issues on its own.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

When it comes to global warming, most of us think of carbon dioxide emissions. While carbon dioxide is the most important greenhouse gas, carbon dioxide emissions have stayed constant for the last three years. On the other hand, methane, the second most important gas, has been steadily rising since 2007.

Welcome to my tutorial where Voidx and I will be expanding on my previous article to provide more clarity into the logic of the code.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

If you've been using Windows 10 for a while, you already know that Microsoft incorporated lots of new features into it. So you're probably familiar with Cortana (the new voice assistant), the Edge browser (their replacement for Internet Explorer), the newly resurrected Start menu, and all of the other big changes.

Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds.

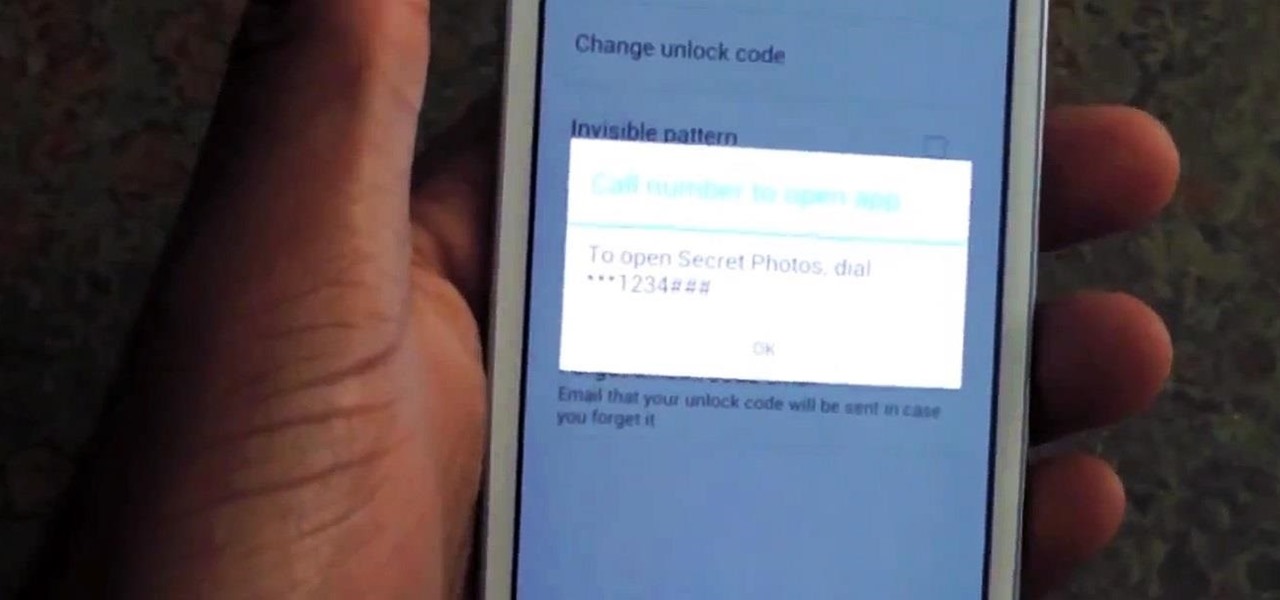
Whenever a friend borrows my Samsung Galaxy S3 to browse the web or make a quick call, I always pause to make sure there's nothing incriminating on it. I'm no superfreak, but some of my friends are, so I have more than a few photos on my device that I wouldn't wish upon anyone. I like to avoid these kinds of looks.

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.