If you've ever gotten a call from a private caller on your Grand Central number and you want to call them back, now you can. This does not work with Google Voice. Log on to Grand Central and find a message you've received from a private caller. If you know the name of the caller, input it. This will help a lot. Mark the message as new. Now call your number and access the voicemail. Press 2 to return the call. It will return the call, but won't reveal the number. Now you can leave a message of...

Bored with the same old stationary? You can create you own! It's just a few easy steps! *Using the on-screen menu on the printer, scroll to the second page and select "Print ruled papers".

If you're having trouble with the Act 1 quest 'Act of Mercy' in Dragon Age 2, or just want to bask in watching a really good gamer discuss his craft while he pwns, watch this video walkthrough, watch this series of three videos and take them to heart.

Is your French up to par with Parisians? Can your Aussie tongue mingle with the local Australian natives? What about your old-style New York accent? If you're in need of improving your accents in different languages, then Amy Walker can help you out.

This week on Etsy How-Tuesday Kristen Couse aka cakehouse shows us how to make a decorative holiday trivet for the dining table. You can spice up your home decor, whether you're hosting Christmas or a potluck with friends!

Tyson Mao is a renowned world competitor in solving the Rubik's Cube. Not only did this Californian become a world class solver, but he also formed the Rubik's Cube Association with fellow speed solver Ron van Bruchem, which holds competitive events for the Rubik's Cube. If you want to learn how to solve the colorful and mighty puzzle, then who better than to learn from then Tyson Mao?

This educational safety video is geared toward public and private utility workers and linemen who need to remove pole tops while dealing with high-voltage electrical cables and electrical insulators. It discusses the proper pole topping removal procedure and demonstrates effective procedures for removal.

Strings of DNA aren't the only things that contain helixes. With a bit of skill and practice, you can make your own rope helix for fun or bondage and BDSM play by watching this video by Two Knotty Boys.

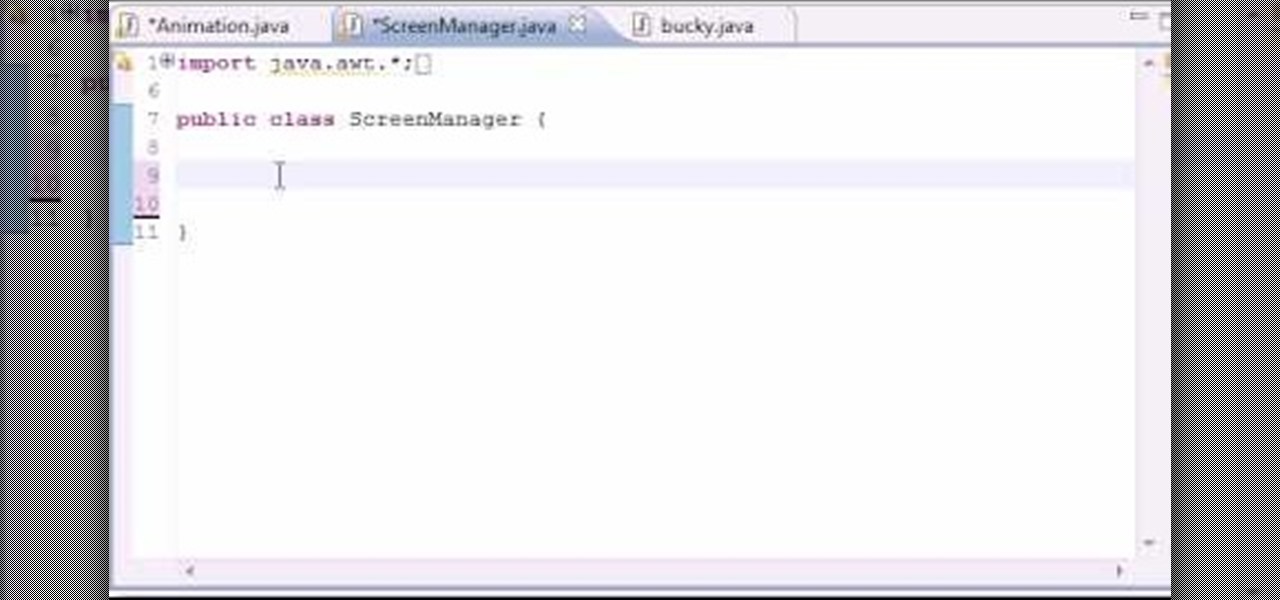
In this 14th video in a series about JAVA game development, "thenewboston" (Bucky Roberts) explains how to redefine your screen to avoid annoying flickering. Flickering in JAVA games often occurs because of time lags as the viewer watches the computer draw a new screen, pixel by pixel. Pre-installed code in JAVA can be used to eliminate this problem by taking advantage of "Buffering" and "Page Flipping". These functions permit you to delay the composition of a new screen until it is finished,...

This video will show you how to record video on your Apple iPhone 3G for free! This is a complete guide to installing the iPhone Video Recorder on your iPhone 3G, which also works on the First Generation iPhone.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

There's a handy new feature in Windows 7 called the Ease of Access Center, which brings together settings and programs that can make your PC easier to use. This is where you get quick access to programs like Magnifier, Narrator, On-Screen Keyboard and more. Learn about the accessibility.

The best way to win friends over in a foreign country is by breaking the ice and showing your enthusiasm with your best effort at their language. Practice your Gaelic for travel or just for fun with friends.

Researching genealogy takes a little enterprise and the skills of a master sleuth.. Watch this video to learn how to research your genealogy and family tree.

Your sensitive personal data should be strongly protected, and it's never more vulnerable than when you are online. The internet connection is a prime avenue of exposure, and email is one of the least secure forms of communication. Fortunately, there is an easy solution to both of those problems.

Many of us install TikTok just to see what it's like, but most of us stay for good. Inevitably, that involves creating an account. The problem is, TikTok assigns you a username, usually based on your email address — an odd choice for a platform made for self-promotion. If you're not happy with your random TikTok handle, you can change it.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

We know that Microsoft's HoloLens 2 is due to start shipping later this year, but despite the trickle of news about the device, we still don't know when.

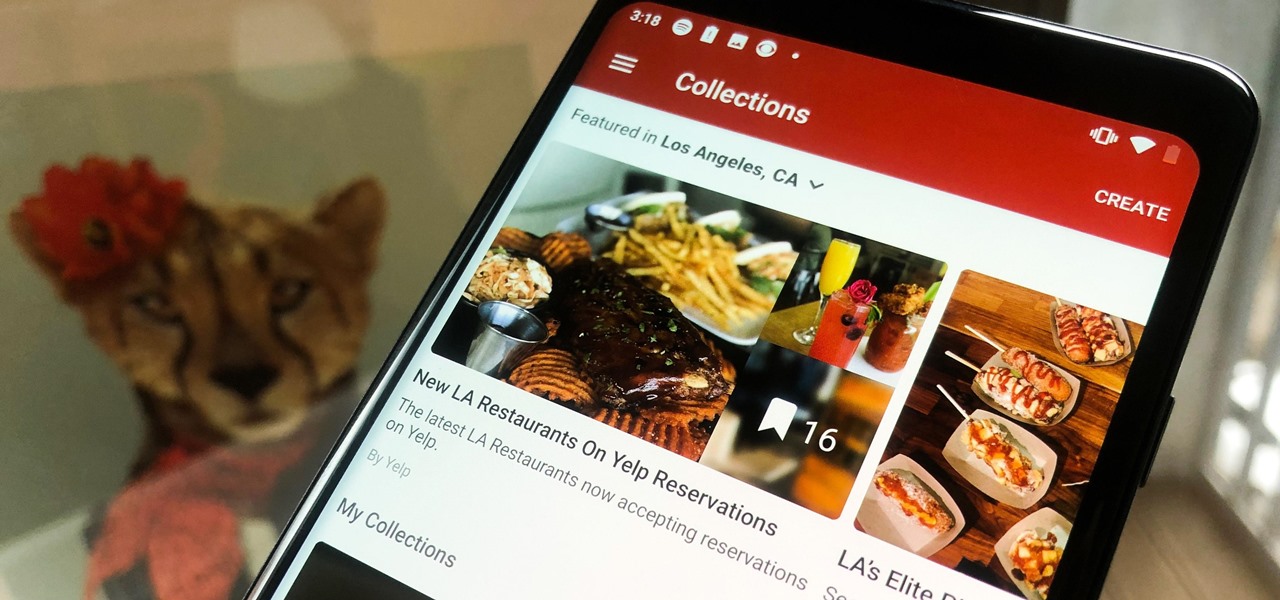
In the past, if you stumbled upon a Yelp listing you liked, you could bookmark it and check it out later on your profile. You can still take advantage of this feature in the mobile apps, but it's more refined now than it ever was thanks to Collections, a feature Yelp first added back in May 2018. You get more power over organizing, accessing, sharing, and discovering favorite businesses.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

Chrome is the browser of choice for millions of iPhone and Android users, largely thanks to its user-friendly interface and native Google support. But with concerns over sharing private information with massive companies growing, many people are starting to want a little less Google integration in Chrome.

When you leave your iPhone on a table or anywhere within somebody else's eyeshot, a private message may pop up on your lock screen that could be read by anyone who sees it. But there's a way to keep others from reading your possibly sensitive text messages and emails without giving up the convenience of lock screen notifications entirely.

When a photo or video is just too sensitive to leave laying around in your Photos app, you'll want to either delete it for good or hide it away in safe, secure location on your iPhone. As for the latter, Apple actually has a few tools available to make photos and videos hidden — even password-protected — on your iPhone.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

Chances are, you just point, shoot, and share photos and videos on your iPhone without a second thought about how your privacy is affected. It's fairly easy to do so since the Camera and Photos apps that Apple provides seem so innocent. But there are a few things you need to know when it comes to shooting media, sharing it, and even deleting it.

Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.

Good news for those suffering from the "i" glitch, otherwise known as the "A [?]" bug: Apple has just released an official patch to fix the issue, in the form of a software update named iOS 11.1.1.

I've possibly been really out of it for a long time not to have realized that Instagram has a bunch of hidden filters. Clarendon seems to be by number one filter for pics and videos, but maybe that's exactly what I've been doing wrong.

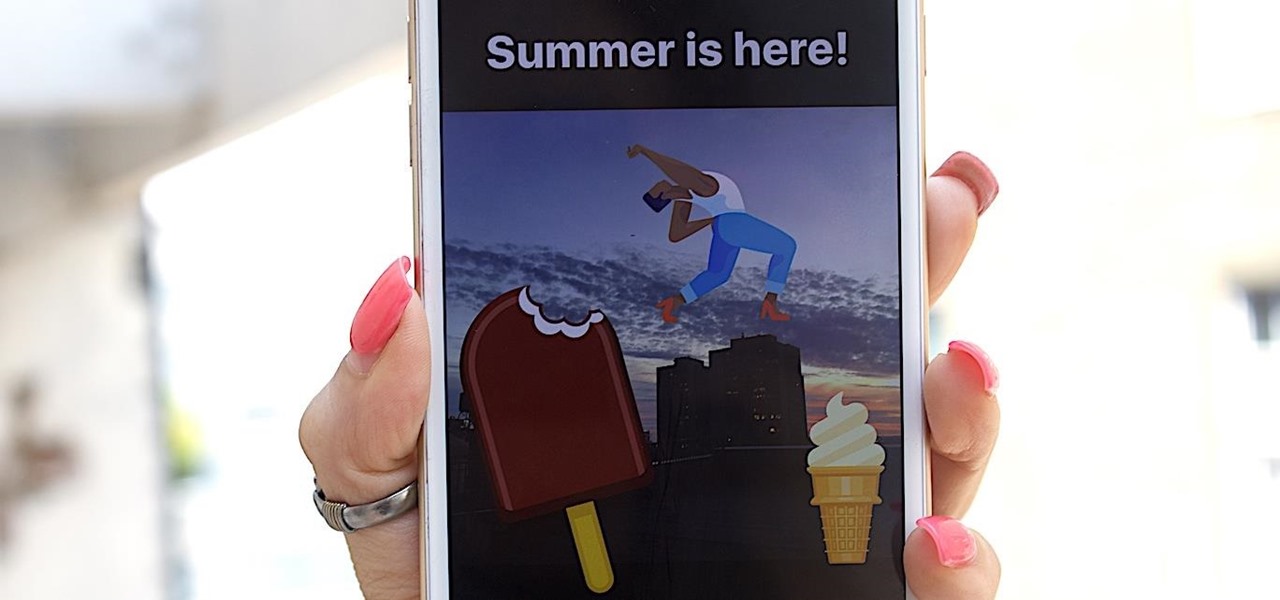
Although Instagram's summer stickers will only be here for the summer, the ice cream cone is still currently one of the most fun ones to play around with in Stories. It's also one of the stickers that lets you pick your preferred flavor of ice cream, rather than forcing just one type of flavor on you.

Pokémon GO updates will have new deterrents for cheaters, and these seem to use shame more than just prevention. The changes were mentioned by a Pokémon GO support account on Reddit. (There are other updates coming soon to Pokémon GO as well.)

Universal Studios and Cinemark Theaters have enlisted mobile augmented reality game Seek to promote The Mummy, a reboot of the action-adventure film franchise starring summer movie mainstay Tom Cruise.

It looks like Samsung's Bixby finally got one up on Apple's Siri — when it comes to which virtual assistant can spit better rhymes, that is. Mhm, that's right. It's a rap battle between one AI and another, and Siri just can't spit.

When it published its 2016-2017 catalog last year, Savannah College of Art and Design (SCAD) became the first college to leverage augmented reality technology for a college catalog.

Google is reportedly working on an iOS keyboard that brings key features to the iPhone, including Google's image and text search functions. (GIFs, yay!) According to The Verge, the keyboard has been in development and testing for months, and will act much like the Android version.

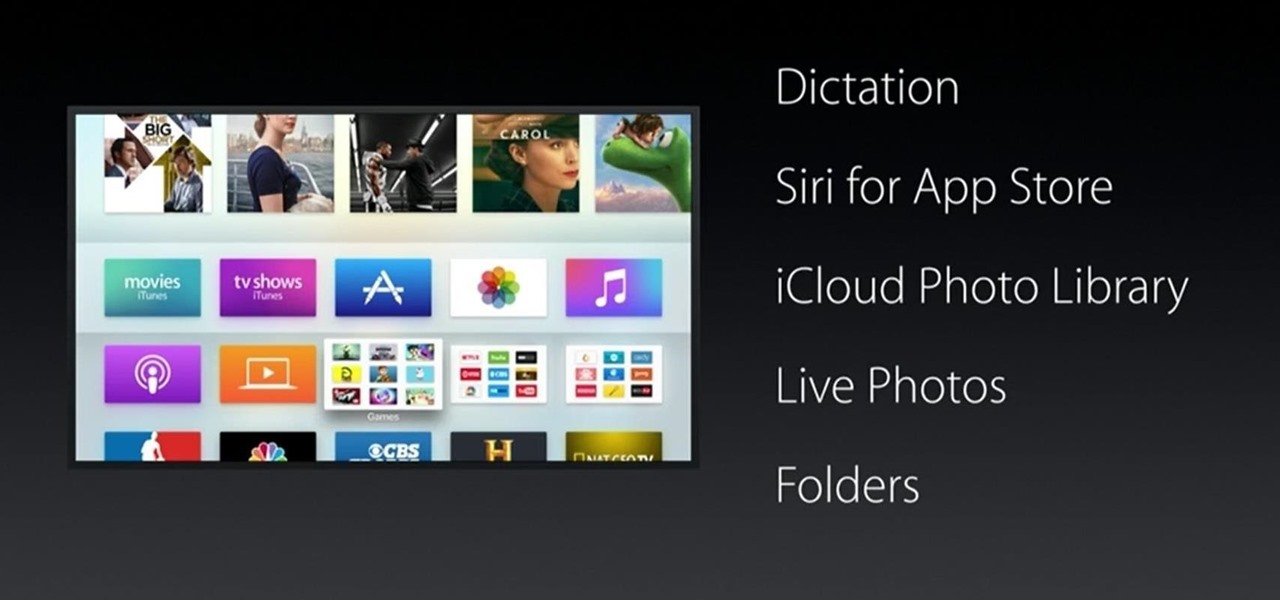
Apple will release tvOS 9.2 for the latest Apple TV today, bringing some major features to the streaming device. The software update, announced at today's Apple event, comes with Siri voice dictation, full iCloud photo viewing, and support for Bluetooth keyboards. Since Apple has already been beta-testing tvOS 9.2 for months, it's ready for a public rollout.

In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

Hello all. It's time for level 6 all, password encrypting. Step 1: Looking for ASCII Table

One of Android's biggest strengths relative to iOS was the ability to switch to a third-party keyboard. While Apple has finally included this feature in its latest OS and leveled the playing field a bit, the variety of options still pales in comparison to what's available on Android.

Yes, they're called volume keys, but they can do much more than adjust your volume. With minimal effort, you can do some amazing things with these physical buttons, like secretly record videos, toggle on your flashlight, scroll through pages, control your music, and much more. And while using them to wake your screen is useful, let's take it a step further and show you how to use them to completely unlock your device, even if the screen is off.