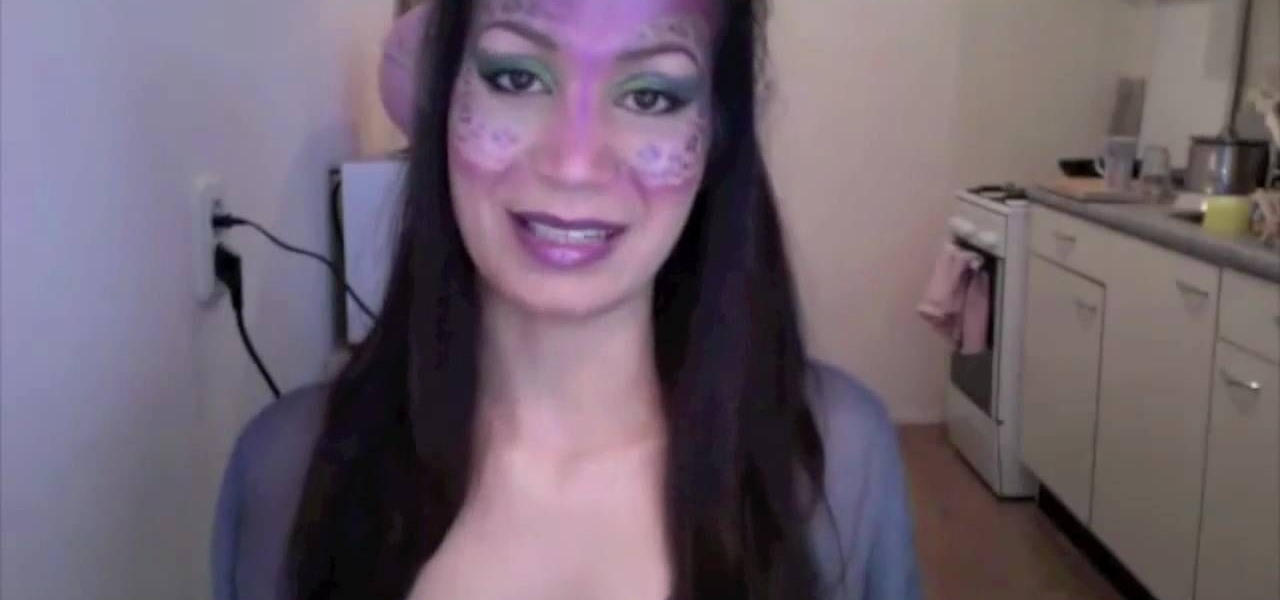This video tutorial shows how to fold a paper pentagon out of A4 sized paper. Instructions for how to convert North American Letter sized paper into A4 size paper are also included. The paper pentagon serves as a base for a paper dodecahedron, which can be made by attaching all the paper pentagons together.

This video shows how to fold a note in the origami style. Learn how to do the compact note fold for letters.

Learn how to pronounce the vowel letters of Tamil language.

Learn how to make the green raining letters Matrix effect in Photoshop. This version is definitely a stylization.

There are two types of people in this world: those who recognize Wordle grids of yellow, green, and gray/black blocks and those who do not. No matter which category you fall in, there's a Wordle-inspired game that's perfect for you.

At first glance, it may not sound like there's much value in doing a crossword puzzle in augmented reality, but The New York Times has managed to revamp the pastime as an immersive game.

Samsung, like other OEMs, partners with third-party companies to include their apps on Galaxy devices. For example, Microsoft pays Samsung millions to pre-install certain Office apps. But one of these partners might not be on the up and up.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

The legal drama surrounding Chinese startup Nreal and Magic Leap continues, and now we finally have an update.

Slack is meant for business, but it's inevitably used for personal reasons too, or even just to goof off with colleagues. However, you never know who's looking over your shoulder (nosy coworker? boss?), and you could get in trouble for something sent to you. That's why you might want to hide images and GIFs to help keep your conversations private.

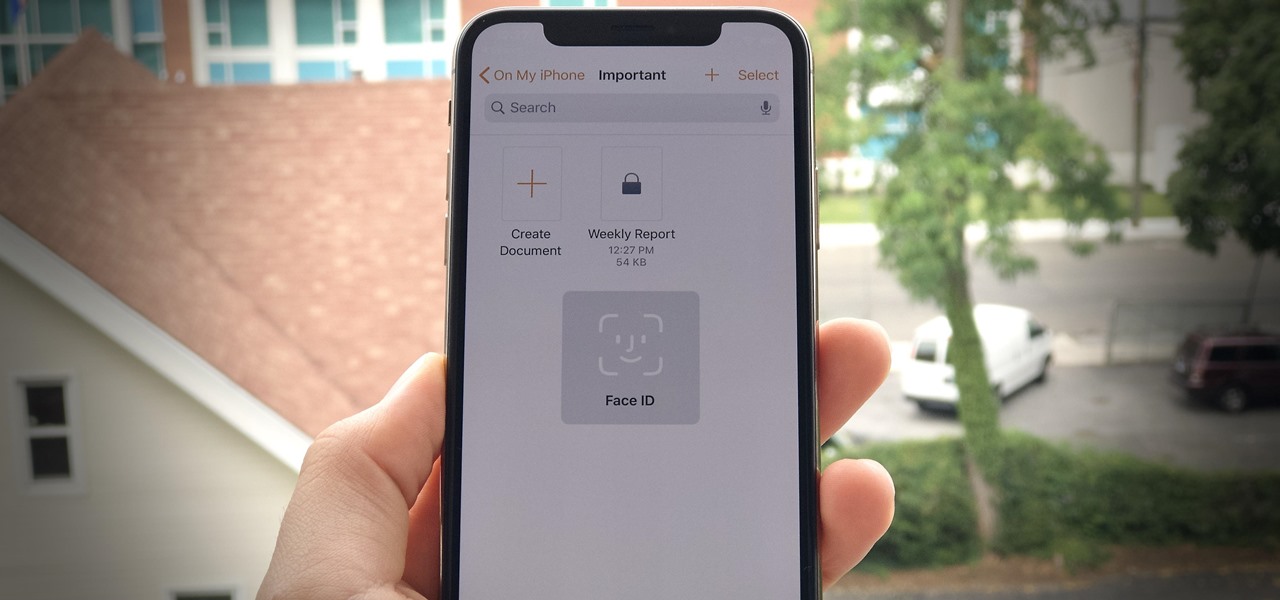
Your writing is just that — yours — so the work you do in Apple Pages should remain private until you choose to share it. Apple seems to share this sentiment. As another symbol of its dedication to user privacy and security, the company includes a feature in its word-processing app for iOS that allows you to lock documents behind a password, as well as with Face ID or Touch ID.

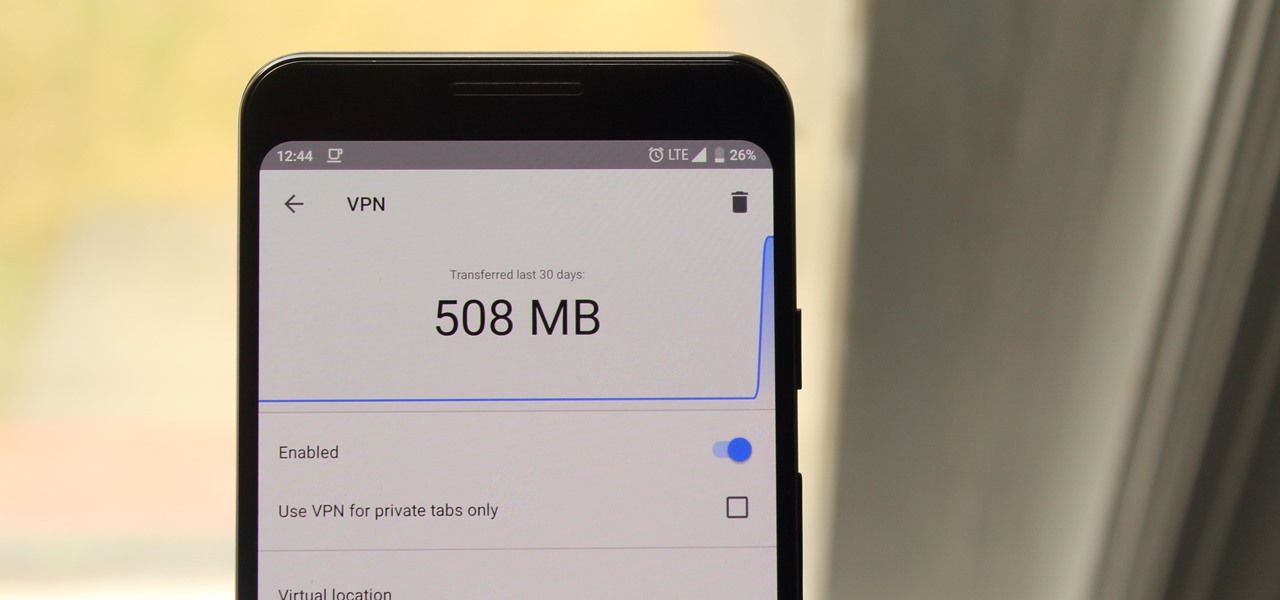
Browsing the web can be dangerous. With all of the various threats out there, it isn't enough to just avoid bad links and visit only HTTPS websites. You need to take advantage of the tools available to you so you don't end up the victim of some scam. Fortunately, Opera is making this a bit easier.

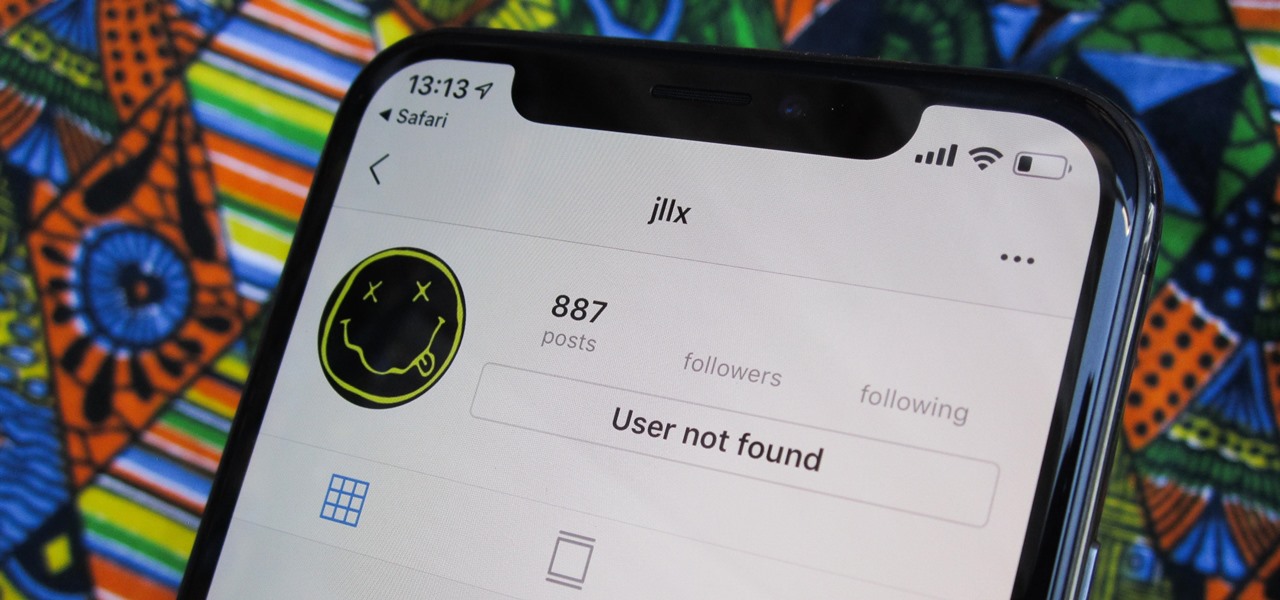
When you don't want certain friends viewing your account or just need to take a break from social media, Instagram lets you do so. While you can completely delete your Instagram account, then start over when you're ready again, it makes much more sense to just disable your account temporarily. Doing so will hide your profile, photos, comments, and likes from everyone, including your friends.

With iOS 12, iCloud Keychain has become a more useful password manager for your iPhone with strong password suggestions, password reuse auditing, and Siri support. However, before you jump ship from your current password manager, you should consider all the reasons why iCloud Keychain doesn't make sense as your primary password manager.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

The augmented reality business was all about audiences this week. Vuzix looked for an audience with the Supreme Court of New York regarding a defamation lawsuit against an investor. Magic Leap held an audience with royalty, showing off the Magic Leap One in a rare public appearance. And Snapchat wanted to remind its consumer audience of all the things its camera can do.

BlackBerry has formally unveiled its latest flagship, the KEY2, during an exclusive event in New York. The Android-powered KEY2 retains its distinctive BlackBerry aesthetics with a physical QWERTY keyboard. Here's all the juicy details regarding Blackberry's followup to the venerable KEYone.

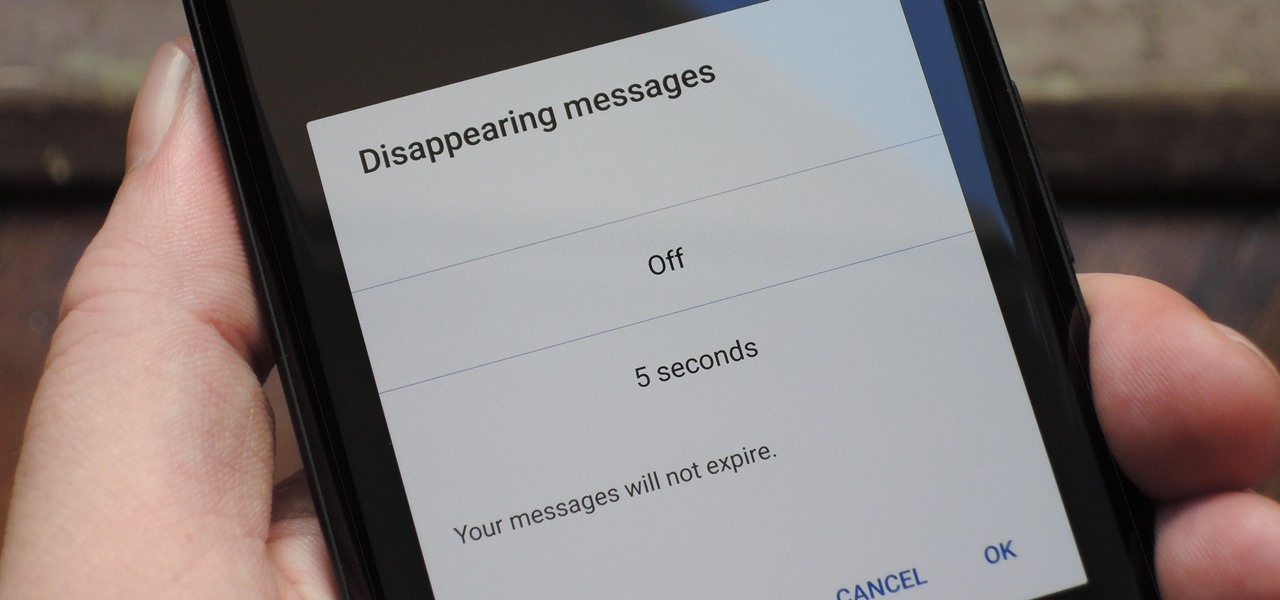
With Signal's class-leading end-to-end encryption, you can be sure your messages will remain secure as they travel to the recipient. However, once the message arrives, its privacy is completely dependent on the receiver, who could share it anywhere if they wanted. To patch this vulnerability, Signal added disappearing messaging.

Instagram is a great platform to share photos and videos with the world, but sharing with smaller groups is near impossible. You can directly message pictures, stories, or post links to friends, but that only works for one person at a time or in group chats you create. To share your content with a small group of people you care about the most, you'll want to use the "Close Friends" list.

For a company who hasn't released a product and has a reputation for being secretive, Magic Leap sure has a tendency to make waves. Over the past few weeks, they've refreshed their website design, released an abstract YouTube video, and announced a partnership with Madefire to offer mixed reality comics on its device whenever it launches. Next, they are gearing up for another round of funding.

YouTube is a giant platform — over 300 hours of video are uploaded every minute. It can be difficult to keep track of your favorite videos in such a chaotic sea of content. Difficult, but certainly not impossible.

The latest video game developer to hit the scene is a hotel chain, and they're offering big prizes for high-scorers.

We haven't had a working jailbreak method since October of last year, and that only worked for about a month until iOS 9.2 came out and shut down the loophole it was using. So all of those cool Cydia tweaks have been out of the question for quite a while now, unless you downgraded your firmware to keep jailbreak compatibility.

Counter-Strike is one of the most popular first-person shooters of all time, and deservedly so. What originally started out as a third-party Half-Life mod garnered such a cult following that Valve had to hire the developers and purchase the intellectual property to make it an official standalone release.

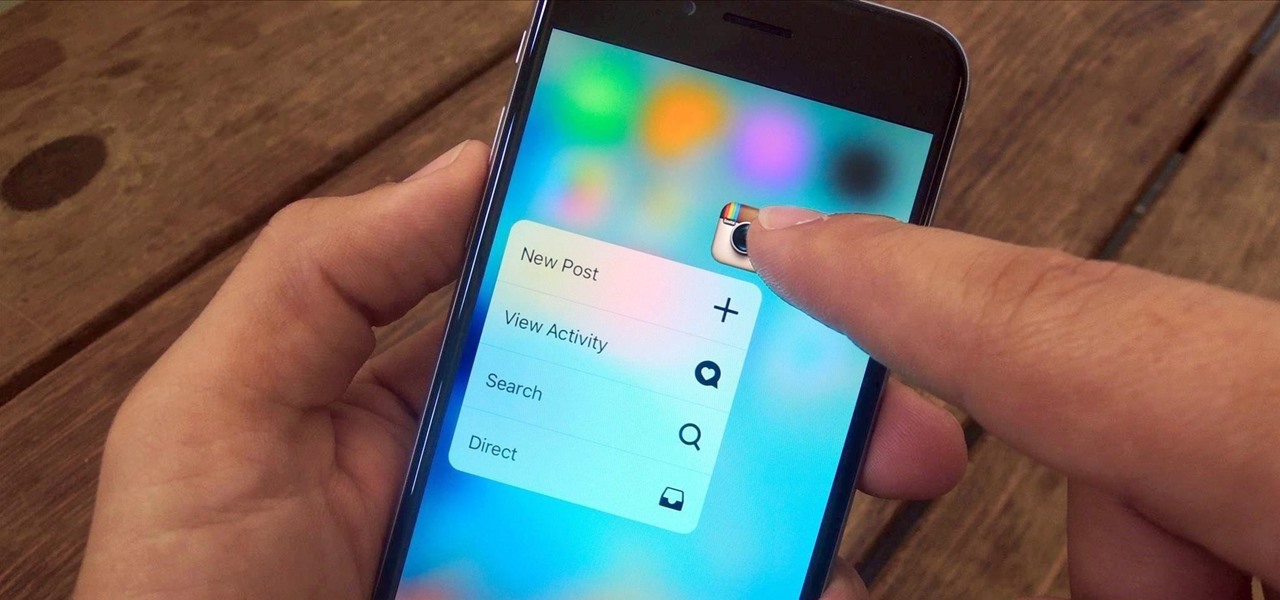
3D Touch is a new feature on the iPhone 6S and 6S Plus that's reinventing the way we interact with our smartphones. With just a little bit of added pressure when tapping on the display, you can perform Quick Actions from an app's home screen icon, "Peek" at emails, stories, and photos in-app, as well as perform other app-specific gestures. Since 3D Touch is such a new concept, here are some of the apps that currently support it, along with the shortcuts you can use.

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

At any moment, you can open up Meerkat and start live-streaming a video from your smartphone, available for anyone to watch. Thanks to its popularity at SXSW and the backing of several big Hollywood players, the app just announced that it's receiving $14 million in funding.

With over a million apps and counting, it's not exactly easy to browse the iOS App Store to find fresh and interesting new apps for your iPad or iPhone. Even rummaging through the featured apps and games isn't easy.

Welcome back, my greenhorn hackers!

While landing a job isn't the easiest thing in the world, you can probably blame your résumé for a number of lost opportunities. Writing up a cover letter and résumé is frustrating and time-consuming, but if you spend the time to get them right, the effort will drastically increase your chances of getting employed.

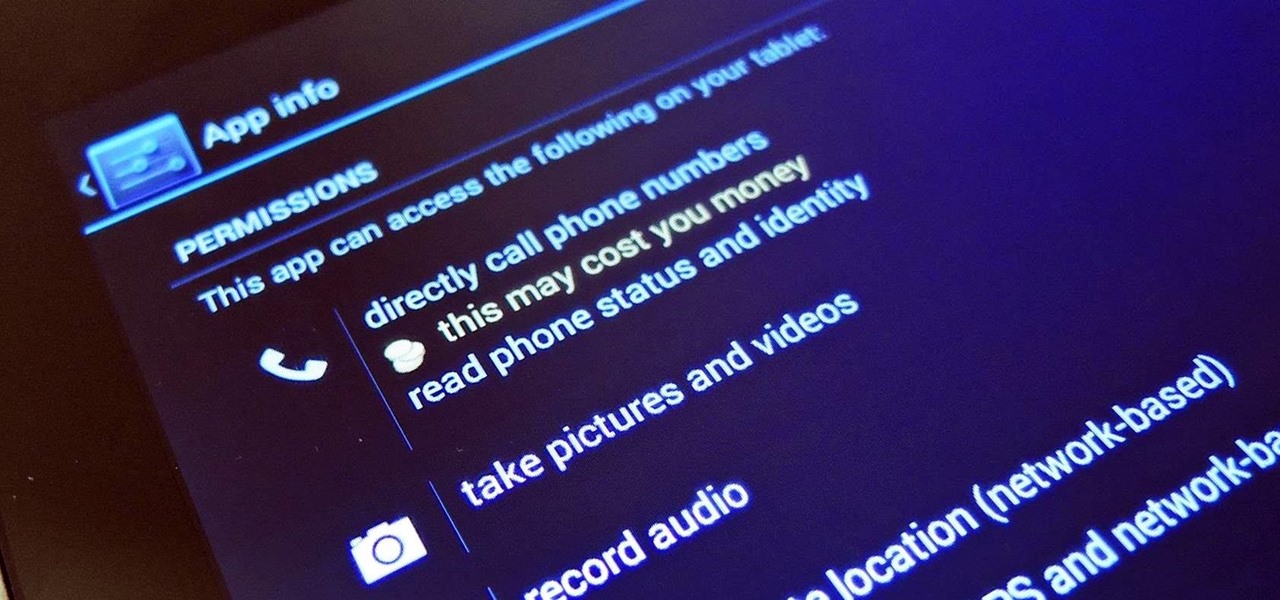
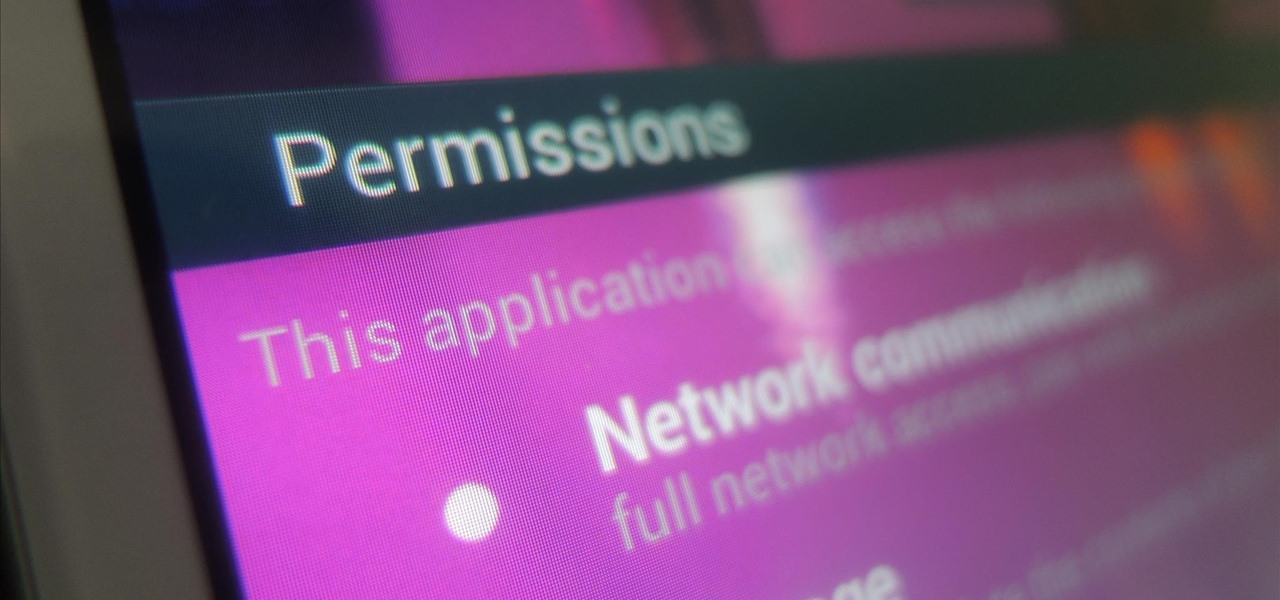
Privacy has been a heated topic in recent months, with everyone now up in arms over unauthorized leaks and exposures. And guess what—tablet and smartphone users are just as vulnerable.

While we're usually responsible for leaking our own private information through mediums like Facebook, there are other times when we mistakenly and unwillingly allow certain applications to scour through our personal data. Some apps may have enabled permissions for internet access, thus allowing it to share said data with its external servers.

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

There's really nothing safe about transmitting sensitive information electronically, but even if it gets there safely without being seen by prying eyes, there's no guarantee what happens to it once it reaches its destination. And let's face it, there are some things that you just don't want floating out there forever. So what can you do? Whether you want to send an email, a text, or a link, there are ways to send messages that self-destruct so that once they're read, they immediately vanish. ...

Steampunk is a tremendously interesting phenomenon because of its reliance on science fiction, and fiction in general. Steampunk can arguably be broken down into two categories: the fiction, and the aesthetic. Sometimes these categories cross over, but they're often more distinct than most people suspect; that said, the aesthetic is firmly based in works of fiction.

It's no secret that there's a lot of surveillance going on these days. It's easier than ever to end up in a database, and even former government agents are speaking out about the atrocious amount of spying being done against our own citizens. They've targeted our laptops, cars, IP addresses, and now they're coming for our iPhones. AntiSec hackers managed to get their hands on a list of over 12 million Apple UDIDs (Universal Device IDs) from an FBI computer, and they published 1,000,001 of the...

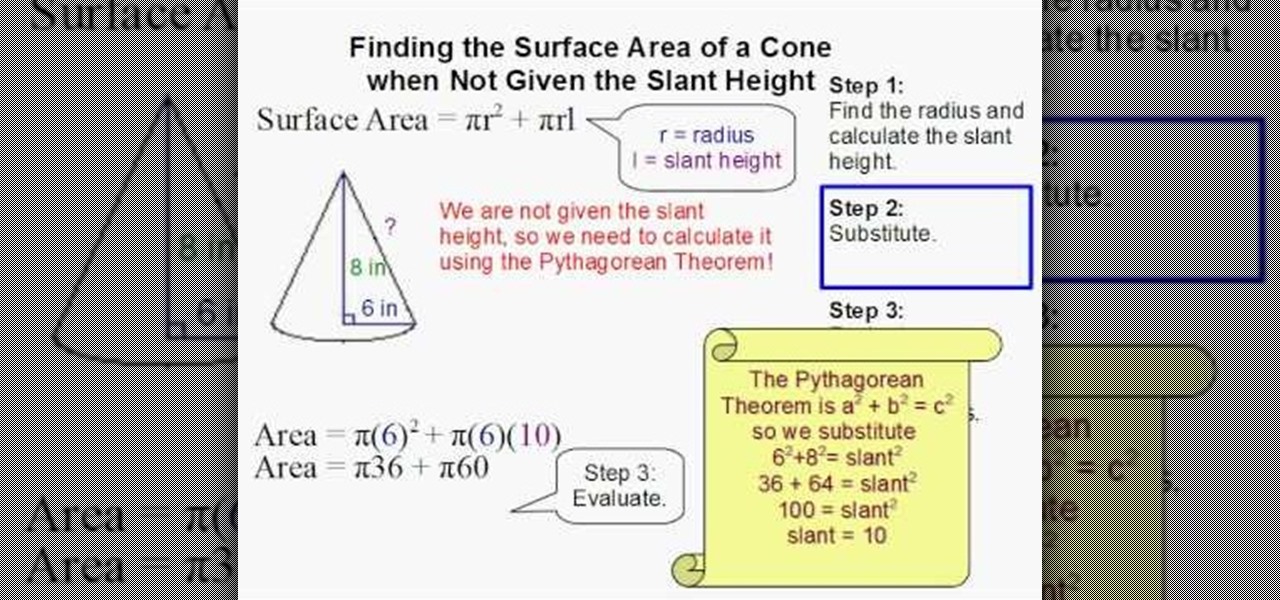
Math always seems hardest until someone shows you how to do the problem and then it all seems just so simple. This video will walk you through the process of finding the surface area of a cone when you also have to derive the slant height. Use this example to help with your other cone problems.

Notthecoolmom gives a craft lesson on how to make a diaper wreath for a baby shower. To make the wreath you will need the following materials: a package of 56 size 1 diapers (preferably with a design of some kind), a Styrofoam wreath, a spool of ribbon, and rubber bands (optional). Start by laying your diapers around the wreath to get an idea of spacing. Be careful not to make your wreath too full. You don't have to use all of the diapers it depends on the size of your wreath. To put the diap...

This video demonstrates how to create a fancy elf look using simple makeup techniques. This look is complimented by a pair of elf ears that can be purchased on the web. To get this look you should colors that are inspired by nature such as deep purples and greens. To create the design, use paper coasters that will provide the stencil for your look. First, lightly apply moss green eyeshadow pencil as a base on the cheek bone, on the temple, and above the eyebrow. Use your finger to blend the p...