While numerous startups are competing to convert the AR Cloud from a pie-in-the-sky to a reality, Wikitude is thinking smaller with the latest edition of its augmented reality SDK.

Since starting as a simple messenger with self-destructing pictures, Snapchat has grown into a full-fledged social media platform. As features were added, new permissions were requested, and we're all probably guilty of just tapping "OK" to try out the latest and greatest. But at some point, it's a good idea to review your settings to see what personal data you're putting out there for all to see.
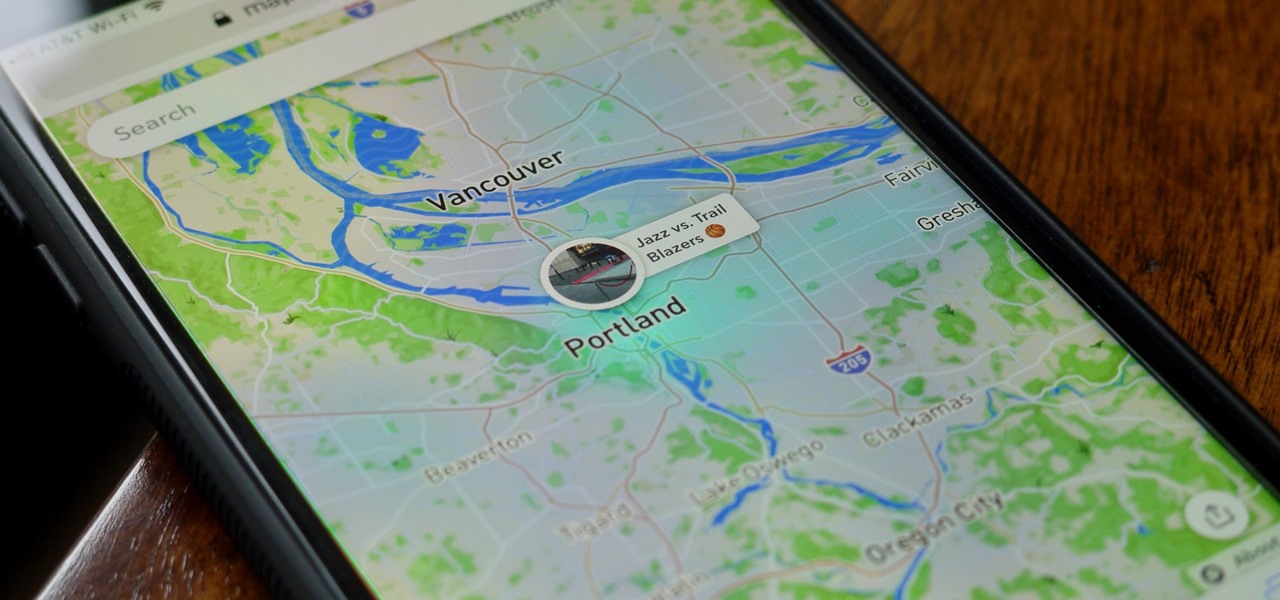
While it's easy enough to make yourself invisible on Snap Map, nothing is quite as private as not having a Snapchat account at all. Whether you're concerned about your privacy or you simply never signed up for the social media platform, Snapchat's web-based map is an easy way to check in on what's happening in your area and beyond.

Messaging apps can be a double-edged sword. Not only do they let you interact with other people, but they also let you go back and reminisce on past exchanges. However, that same archive can be used against you in certain situations. Luckily, Signal can be manipulated to remove any record of past messages.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.
The nice part about creating a song playlist is that it's essentially like your own customized album. You can organize all your different music tastes into one large collection or separate them into each of their own genres.

The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels.

Japan is in the process of curbing its aging population and mature workforce. According to The Diplomat, the country's population has been declining at a steady rate. To meet future productivity demands in commercial and industrial sectors, local officials are turning to self-driving technology, including truck platooning, where three or five vehicles travel autonomously in a string formation. This practice, according to a study by MIT, can reduce fuel consumption by up to 20% (more about thi...

Responding to the rapid emergence of dangerous pathogens around the world, a new initiative to prevent or contain pandemics was announced in Davos, Switzerland, yesterday. If you ever worried that a highly contagious pathogen could take down your community, or the country, this news is for you.

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

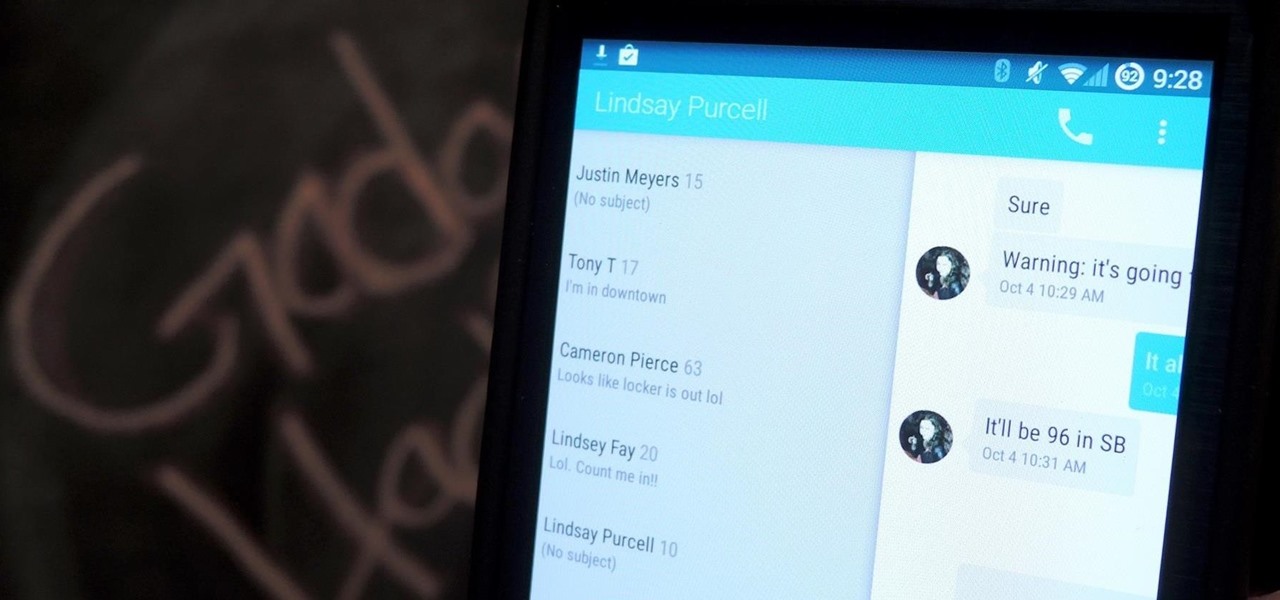
Google's Android L developer preview has given Android a more refined look, with developers excited to update their apps with the new Material Design UI. While some apps are slowly getting updated, QKSMS (QK for quick) is a 3rd-party text messaging app that was built with Material Design in mind.

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

Apps that have no business accessing the internet can share your location, device ID, and other personal information with potentially malicious data snatchers. If you're connected to the internet on your Nexus 7 tablet, you're a potential target for cyber threats.

The Samsung Galaxy S5 was just officially announced at Mobile World Congress. The new flagship device will be available worldwide beginning April 11, 2014, including all major U.S. and international carriers. With over 200 million Galaxy devices sold to date, the S5 doesn't stray too far from the trend, at least not aesthetically. We've still got a high-grade plastic shell with perforated back covers, and four color choices at launch. Our highlights of the release event are as follows.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Need to clear you cache? This guide details how on any web browser (Chrome, Internet Explorer, Firefox, Opera, Safari, Internet, and Dolphin) for any platform (Windows, Mac OS X, iOS, and Android). What Is the Cache Exactly?

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still don't want companies snooping in on your online activities. So just how do you protect yourself when torrenting? Avoid "Open Communities"

This video shows you how to make a footnote in MS Word 2007. 1. Click on the last letter of the word where the footnote refers to. 3. Click on the References tab. 4. Click Insert Footnote. 5. A tiny number will appear beside the word where you clicked and a footnote number with a line on top will also appear on the last part of the page. 6. Type in the words or the notes. 7. You may now continue typing your work.

Kevin Craft takes us through the steps of throwing a football so that you don't have to be a professional to know how to throw the ball. The UCLA quarterback shows how to hold the ball with one's fingertips. He also goes over how to square one's feet toward the target before actually throwing the ball. A short step movement is followed by a hand motion in the shape of a letter J. Craft makes throwing a football look simple and with some consistent practice, anyone can look like a pro doing it.

Watch this instructional video and make an origami hydrangea. It's many tiny pieces can be glued to a flat surface to decorate cards and letters. The video includes verbal instructions in Japanese, although the visual guide is quite clear. You will need a piece of colored origami paper for the flower blossoms and a green piece of origami paper for the folded leaf.

This video demonstration shows the process of putting together a scrapbook layout page. Demonstrator Debbie's theme is "Being Grateful." While replicating this exact page might be difficult, watch this video scrapbooking tutorial to pick up some ideas for painting, inking, sanding, lettering, and generally decorating scrapbook layouts.

This video shows you how to create a blazing font in Photoshop.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!
How Do You Do A Business Plan? Part 1 of 5 (Series designed to discuss the parts of a business plan, what information is involved in each part, and why a business plan is needed.)

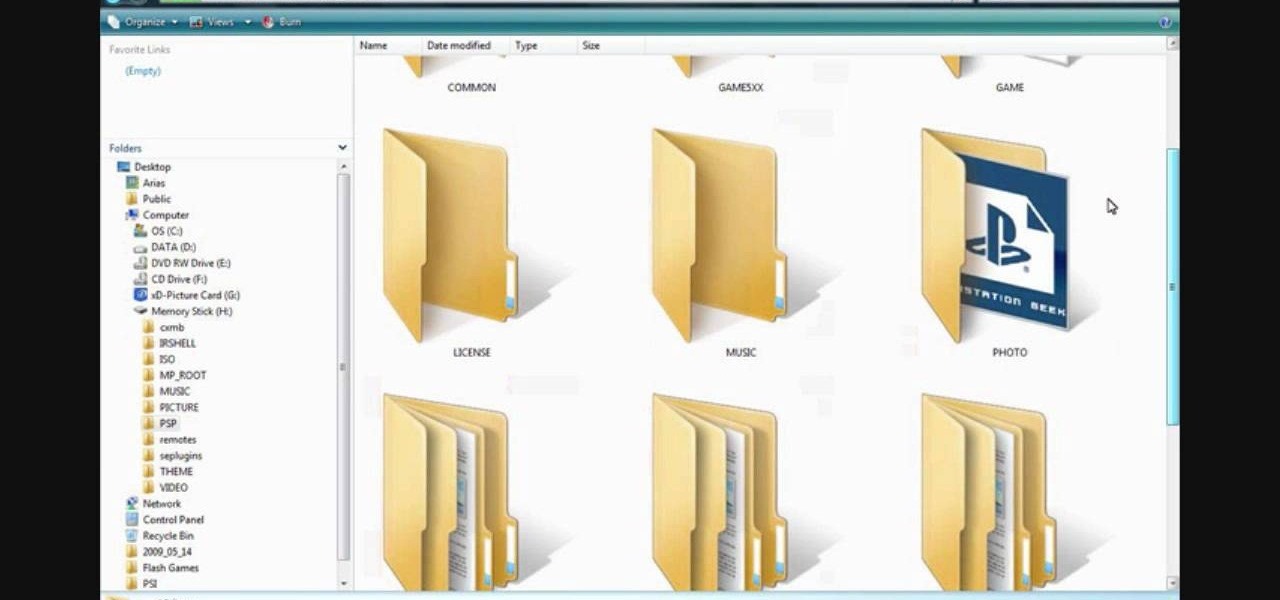
How to install custom themes in your PSP gaming unit. First go to Google and search "Free PSP themes" and then click first link.

Are you looking for a simple math explanation on order of operations? Remember the following sentence: “Please excuse my dear aunt Sally.” What does this sentence have to do with math? The first letter of each word stands for an operation. “P” stands for parenthesis, “E” for exponents, “M” for multiplication, “D” for division, “A” for addition, and “S” stands for subtraction.

It may not seem like a big deal, but sometimes when your filenames are being saved in the incorrect case, it is. If you save a file with uppercase letters in the name, your computer may change them to all lowercase. This occurs when downloading files form a host server to a local hard drive. But what if you want them back how you had them? Well, there's a small Windows tweak you can use to stop it from happening. Learn how!

In this video series, our expert will show you what, how, and why a number of steps are taken to perfect the illusion. You'll be shown how to pronounce problem letters, how to practice your technique, and how to develop unique voices.

Every mainstream Android home screen app looks and behaves almost exactly like Google's Pixel Launcher. It's the trendsetter, like the Nexus Launcher before it. But when all your options are modeled after the same thing, that really takes the "custom" out of "custom launcher."

The average iPhone user has between 60 to 90 applications installed. On one of my devices, I have over 600. With a ton of apps to sort through, it can sometimes be challenging to find the one you're looking for without having to use the Search tool (which is even better in iOS 14). Even then, you may still come up dry.

There are countless ways in which you can turn your love of tech and coding into a full-fledged career — from developing apps and websites as a freelancer to working in the IT departments of small startups or major tech companies. But one of the best ways that you can put your programming skills to good use is to join the increasingly important world of cybersecurity.

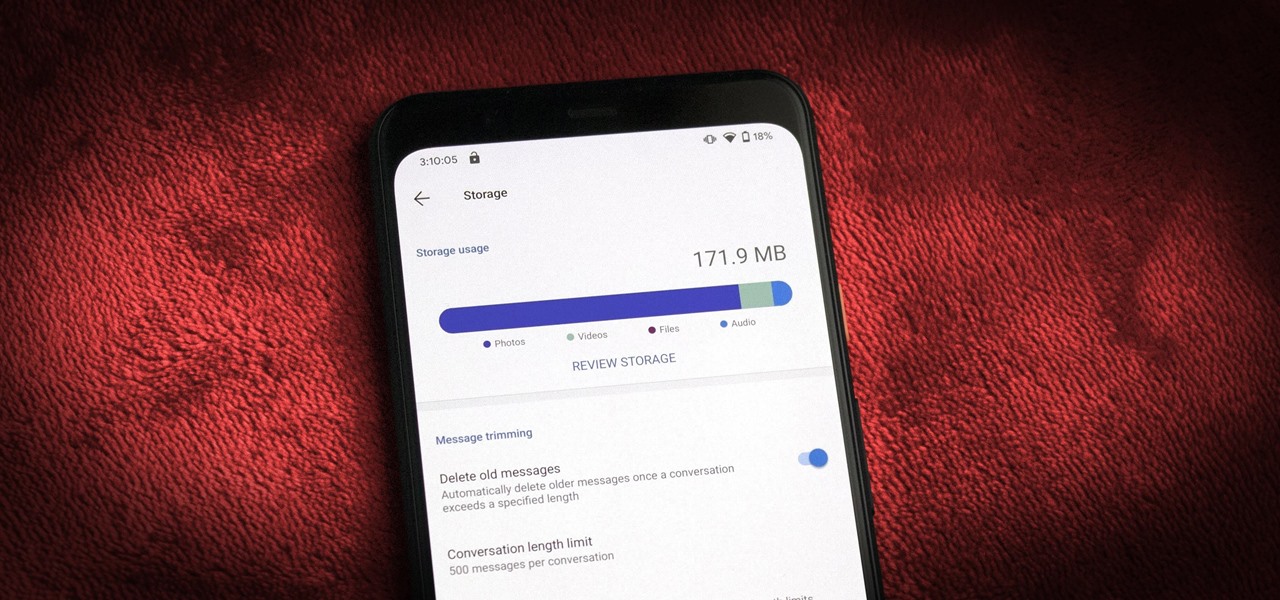
Thanks to backups, Signal conversations can span over multiple years and multiple phones. These archives can get rather large as you share photos, videos, and other files with friends. But between the other apps and large files on your phone, you might not be able to afford to keep all those messages.

In recent years, Google's Arts & Culture project has been leading the way in terms of innovating the practice of using technology to preserve landmarks and great works of art via digital 3D copies. Increasingly, these efforts are also giving history buffs the chance to experience classic works and spaces with unparalleled intimacy through the wonders of augmented reality.

As one of the household brands in creative software, Adobe is now ready to lay its claim to the artistic side of augmented reality.

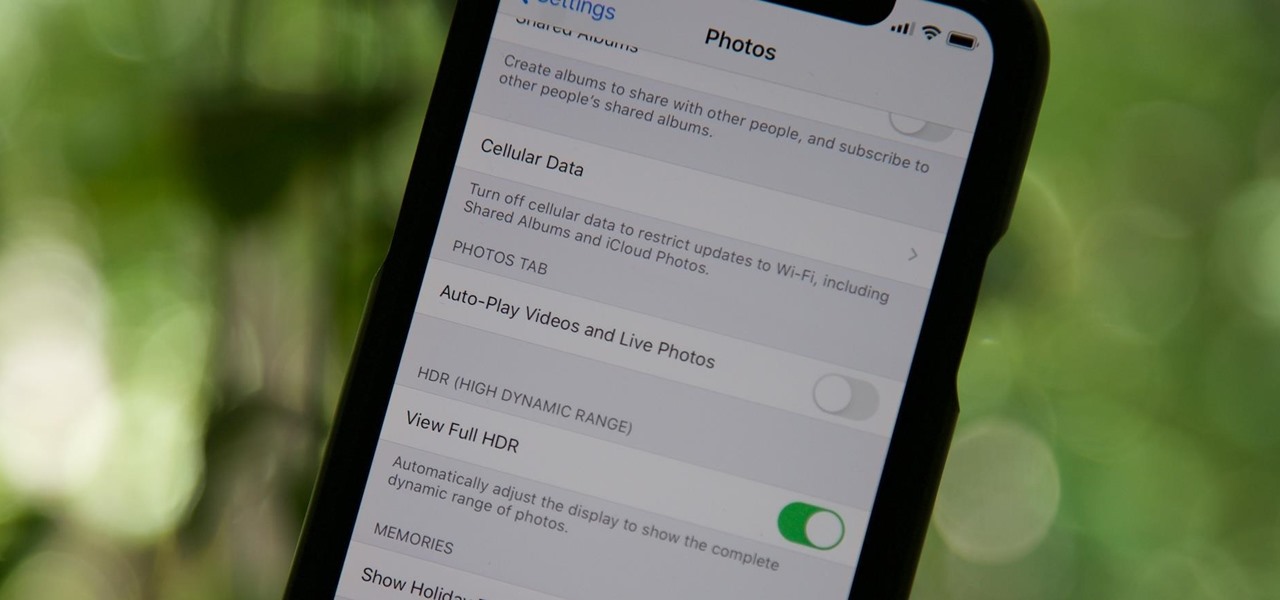
By default, videos in the Photos app auto-play in several instances on iOS 13, making it a great way to get a quick, extended glimpse when you're browsing. But this isn't always ideal — especially when you're flipping through private or embarrassing videos and other eyes are on your screen. Fortunately, Apple has an easy way to disable this feature.

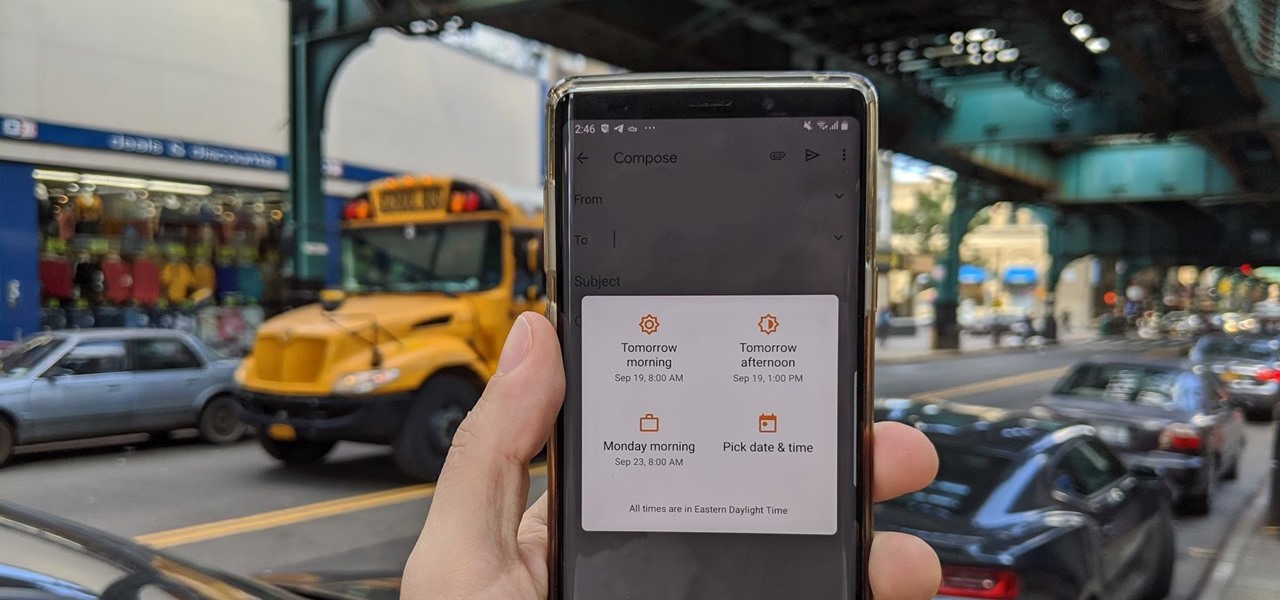
There is power in the detail. Sending an email at a specific time can give you an edge. Depending on what you are doing, it can help your email get read or it can put you at the top of someone's inbox. With the Gmail app for Android and iOS, you can now schedule your messages to maximize the efficiency of your email.

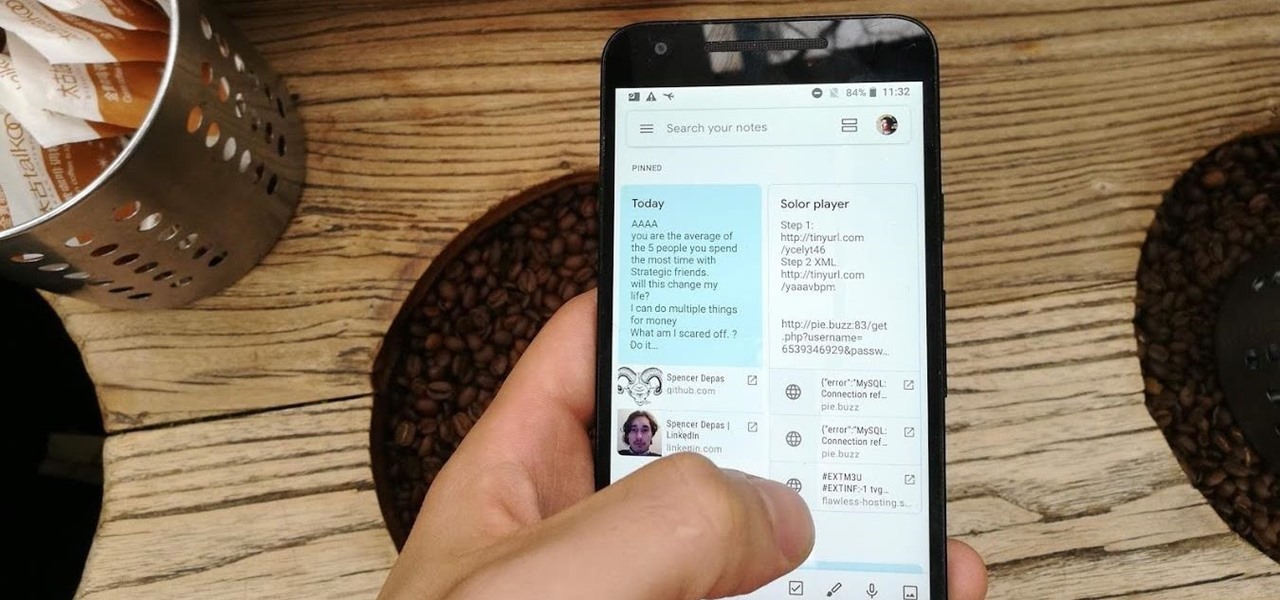
Disabling clunky, revealing link previews on Google Keep can serve multiple purposes. You know, those expanded versions of the same URL you pasted into your note, except duplicated, tacked onto the bottom of your note, and showing a preview picture. Removing these can help optimize your productivity formula.

Increasingly, cutting-edge platforms like blockchain technology and augmented reality are overlapping, forging new digital frontiers that promise to change the way we interact with the virtual and the real world.