You can read at 500 words per minutes. Don't believe me? Here, see for yourself. This amazing technology comes from the startup Spritz, and they're ready to unleash it onto the smart device world, starting with the Samsung Galaxy S5 and the Galaxy Gear line of smartwatches.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.
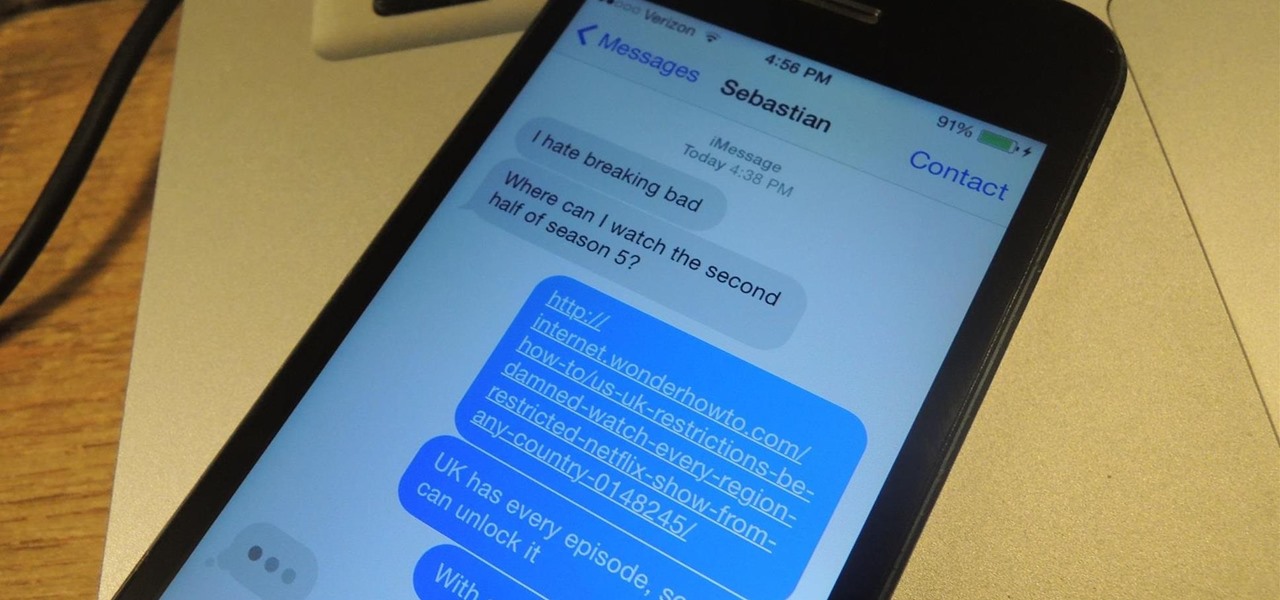
NSA aside, Apple makes it difficult for users to extract and download text messages from their iPhones onto a computer. For whatever reason (legal, devious, neurotic, etc), we've all found a time where we'd like to save backups of certain meaningful, important, or perhaps incriminating conversations (including all MMS or iMessage pictures and videos). While there are a handful of third-party applications that can help with this process, the majority of them cost money and implement certain te...

Video: . Here there are some DIY gift ideas perfect for the Christmas season. They are really easy to personalize depending on what your likes are.

With only a few days left until Halloween, your options might be rather limited if you still don't have a costume. You may have laughed while some people spent the entire month of October painstakingly crafting their ridiculously detailed costumes, but now that the big day is so close, the joke's on you because you still have nothing to wear.

With all of the new features and third-party apps out there making Android better and faster every day, it's quite frustrating to me that keyboard advancements remain relatively static.

Whether you like it or not, certain songs get stuck in your head. You might be driving to work or school when suddenly Cher's 1998 lead single "Believe" plays on the radio.

The U.S. Postal Service has been in trouble for quite some time. With more and more people choosing to go digital to take care of bills, legal documents, and pretty much all other forms of correspondence, they haven't exactly kept up with the times. I mean, let's be honest—when was the last time you sent snail mail?

I can definitely say that my MacBook is one of my best friends, but I was still very disappointed when I realized that the only game my laptop came with was chess. For starters, I'm not very good at chess. I haven't even beat the computer once, which really grinds my gears. But, it has come to my attention that chess isn't the only pre-installed game on my Mac—there seems to be some hidden gems that I simply wasn't cool enough to know about. For some of you, this may be old news, but for me, ...

As a kid, I was always interested in what was beyond our world. I remember lying down on the top of my dad's car and watching the stars for hour, gleefully excited whenever a shooting star streaked across the night sky.

This post has been brought to you by the letter S. With the Christmas season fast approaching, it's time to ask one of the most important questions of our lifetime:

I chose to make this a Steampunk iPad case, but you can change the details and make it look as modern as you'd like. As I said earlier, Steampunks probably shouldn't buy iPhones or iPads, but if you're going to get one, you may as well make it look cool, right? The iPad pictured below was borrowed from a friend of mine, though I should add that this design will easily work with tablet computers of any variety, Apple, Android, or otherwise.

Always downing a glass of red wine in the evening? Don't be ashamed. Red wine has some great health benefits when consumed in moderation, including improved memory, lower risk of heart disease, and even bone strengthening. Photo by Joe Shlabotnik

Today we're going to draw Spongebob! He's going to be facing forward, so even beginners should find drawing this guy to be a piece of cake! 1) Begin by sketching out a rectangle with a broader top and a narrow bottom, make sure it's not too skinny though. This will be the base of Spongebob's body.

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

In this video tutorial, viewers learn how to use a nursing cover to breastfeed a baby. This process is very easy, fast and simple to do. It allows the mother to have more privacy when feeding her baby, without having to wear any special nursing clothes or go to somewhere private. The nursing cover simply goes over the mother's head like a apron. People everywhere will not be able to see the mothers nursing, but she can still see everything as she looks down. This video will benefit those view...

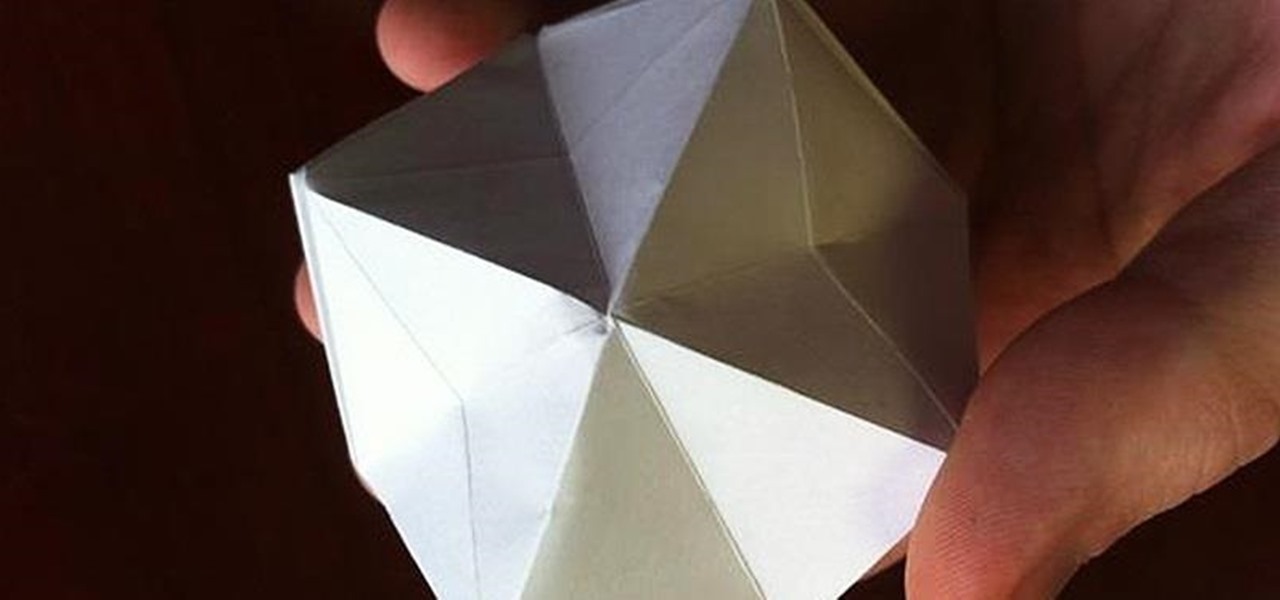
One of the most popular and basic origami geometric shapes is the "water bomb," which is a simple inflated cube. With a few extra folds and only a minor shift in approach, a more complex geometric shape can be achieved.

Safari isn't the only web browser on your iPhone or iPad that will let you add icons to your Home Screen for progressive web apps and website bookmarks. Apple gave developers the key to its "Add to Home Screen" feature, and your favorite iOS or iPadOS web browser may already support it.

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

It's easy to accumulate hundreds of Safari tabs on your iPhone, which makes hunting for specific tabs more difficult, especially when they're spread across different groups. Having too many tabs can even slow down Safari itself. You can close all tabs in a group quickly, but not if you want to save some. To prevent this mess, Safari can automatically weed out the tabs it thinks you don't need.

When you first open Safari after updating your iPhone to iOS 15, you might be a bit surprised by the design change. Apple attempted to make browsing the web on its smartphones more natural and cohesive, but it may leave you wondering just how to actually navigate your tabs.

Niantic first unveiled its AR cloud back in 2018, using it to enhance the immersive capabilities of its gaming portfolio.

Many of us choose to use an iPhone — as well as other devices in the Apple ecosystem — because of the company's dedication to user privacy and security. If you need more proof of that commitment, look no further than iOS 14.5, released April 26, which adds new tools to protect our data while browsing the web and more control over the data installed apps collect on us.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

This week, the beginning of an epic legal battle was set to begin between augmented reality players Magic Leap and Nreal, the small China-based startup accused by the former of stealing trade secrets.

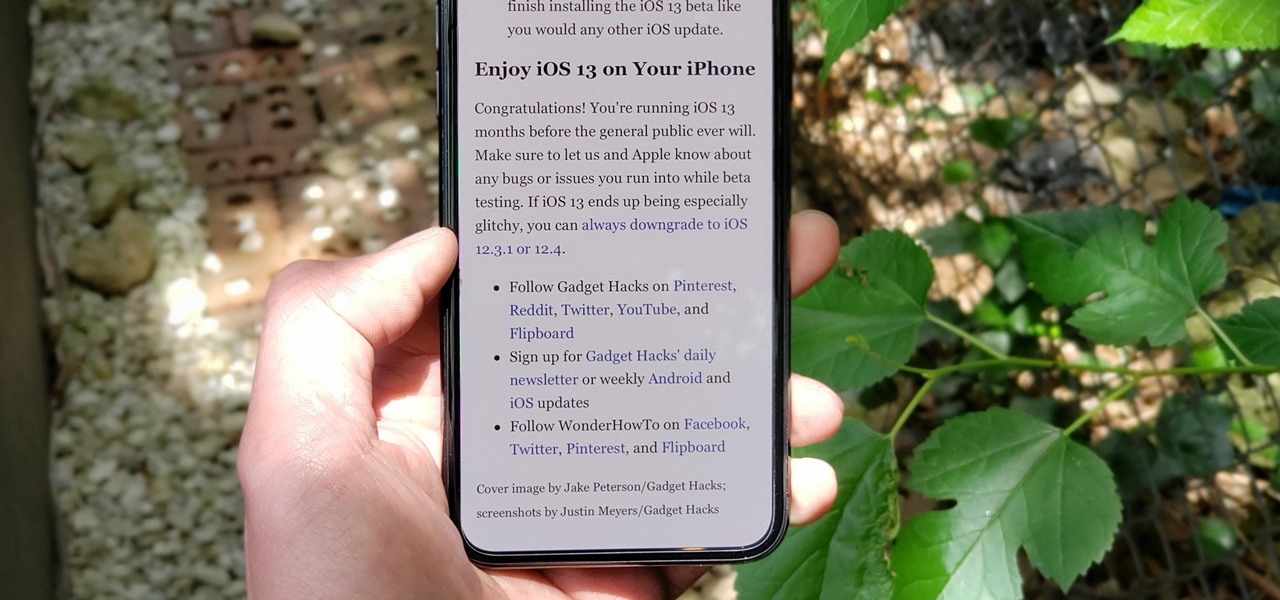
Apple's iOS 13 for iPhone includes new features in Safari that make browsing the web a little bit better when compared to iOS 12. Some changes are small while others add functionality that just wasn't there before. Plus, there are more security enhancements.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

The Reader mode in Safari is a great way to view a webpage on your iPhone in a stripped-down manner, removing unnecessary images, videos, and advertisements for a streamlined experience free of distractions. Apple's iOS 13 improves upon Safari Reader when it comes to choosing which sites you want it to run automatically on, so everything is more accessible with more controls to work with.

Whether gabbing via cloud chat or Secret Chat, there's no denying that private messaging is one of Telegram's strengths. Communications can often occur at night, where Telegram's default bright white theme can be a bit uncomfortable to use, but Telegram supports dark mode on Android and iOS — with a few different themes to match any late-night chatting style.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

When your iPhone goes missing, it's serious business. Depending on your usage, your whole life might be connected to your iPhone, not the least of which includes debit cards, credit cards, and Apple Pay Cash stored in Apple Pay. While it's nearly impossible for someone to use your money with Apple Pay, it's still a good idea to disable it until you find your iPhone, just in case.

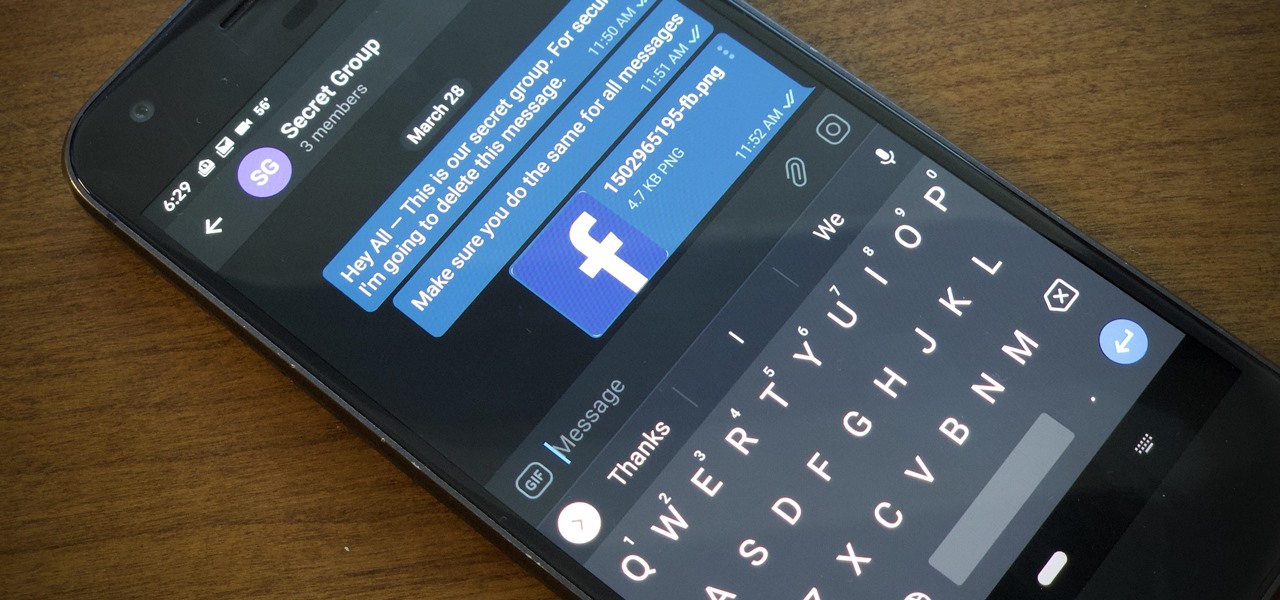
Traditionally, if you were looking for end-to-end encrypted messaging, you'd stick with something like iMessage, WhatsApp, or Signal. However, if you already use Facebook Messenger, you have all you need for truly private chats with its built-in E2E encryption. It's available to all users, on Android and iOS — you just need to know where to look.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.