One of the most popular things to do on Snapchat is to earn a Snapstreak. This occurs when you and one other friend have sent snaps (not chatted) to each other within 24 hours for at least three consecutive days. One you've passed the three-day mark, then you and your friend will receive a fire emoji next to your names.

Food is both a necessity and a joy. Many people enjoy exploring, cooking, eating, and learning about foods from around the world. But the picture isn't always rosy. A new report from the Centers for Disease Control and Prevention (CDC), highlights the ways and whereabouts of food that make us sick.

There is a reason the Amanita phalloides mushroom is called the "Death Cap." It can kill you. Mushrooms are a type of fungi, an organism that produces thread-like mycelia that often produce spores. Spores allow the fungi to reproduce. Molds, lichens, and yeast are all fungi, but the most visible fungi are mushrooms. Some fungi are delicious, but others can cause disease or, and still others, like Penicillium, can cure it.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.

Put yourself in Google's shoes: You know that business is becoming increasingly mobile, but the mobile operating system you maintain is wide open by design, and it's garnered legions of loyal fans that love to explore and exploit every aspect of it. There's a clear conflict of interest developing.

The private automobile has been an intrinsic part of our lives for around a hundred years. But over the last decade, car sharing has gained a very small but growing part of the mobility market. The more recent rise of companies like Uber and Lyft is witness to a more dramatic shift in mobility and car ownership. Private vehicle ownership to a transportation-as-a-service model has already started, and high capability SAE Level 4 vehicles will complete this trend.

Not only has there been difficulty finding consensus on a name for driverless, autonomous, self-driving, or automated vehicles, there is also the issue of what we actually mean when we say a vehicle is self-driving, automated, and so on.

When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

There's an adage that says "Every plan, no matter how great, goes out the window as soon as you're punched in the face." While our lives are (hopefully) not violent, that saying can easily translate to our daily living. That punch in the face can come in various forms, mainly stress-related. It could be a bad day in the office, rush hour traffic, drama in the family, the list goes on.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

Our future technology has a lot of amazing possibilities, and few have more promise than augmented and mixed reality headsets. But these advancements come with several concerns over privacy, and if we don't understand them, we may lose control of our own data without even knowing.

Fast food is a guilty pleasure in which we all indulge. When you're short on time and long on hunger, being able to whiz through the drive-thru or run 'in and out' of a fast food joint can be a real lifesaver.

Whatever you want to call it for now—Android Nutella, Android Nougat, or Android 7.0—the upcoming "N" release of Android will surely bring in tons of new features and functionality. We know it will be named after a dessert, and we know that Google uses an alphabetical naming system, so something starting with "N" is next in line after Android 6.0 Marshmallow.

These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

Welcome back, my rookie hackers!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

If you took a big step back and really looked at the world, you'd see how downright silly our nations look when they put up fences to separate themselves from one another. Creatures big and small roam free while respecting each other's space, but humans create borders and physical barriers to delineate their cultures.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

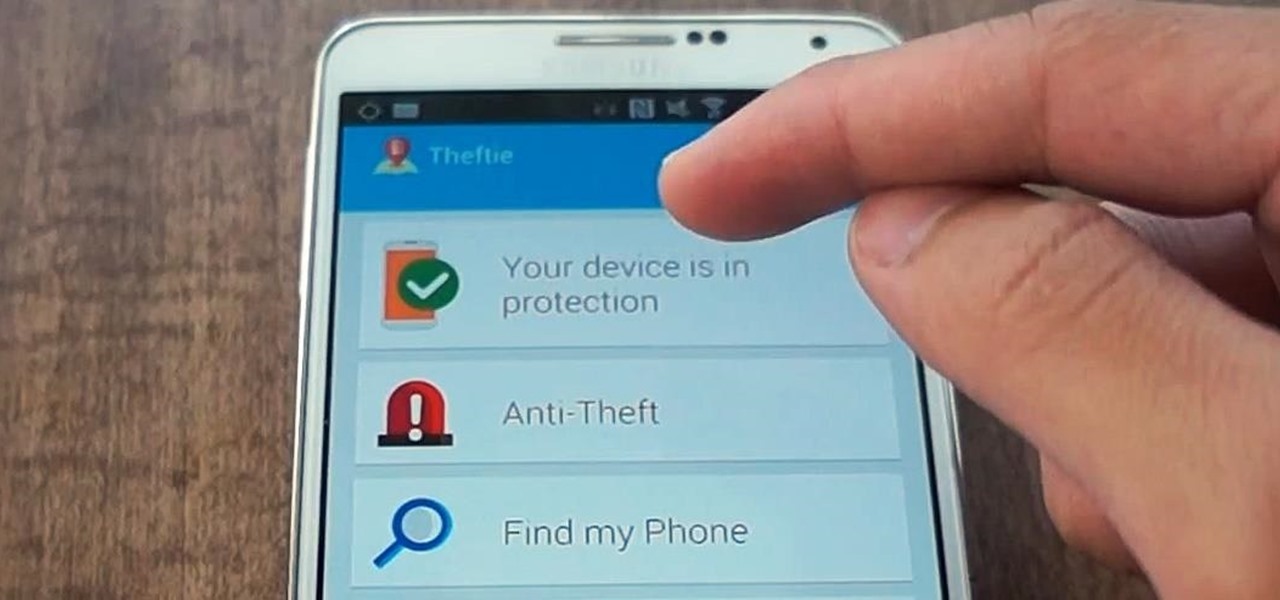
When you misplace your Android device, finding it with the Android Device Manager, or even better, Whistle Me, can help you find it no problem. But what about when your phone is not just hiding under the couch cushions? Your worst nightmare just came true. It's officially gone.

To steal a quote from Mean Girls, Halloween is the one night when a girl can dress like a total slut and no one can say anything about it—but why do girls get to have all the fun?

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

In Minecraft, a large aspect of the game is PVP (Player vs. Player Combat). A hardcore Minecraft fan will remember that back in Beta 1.8, combat was switched up, and it really changed the game around. Here are some tips on what a two-year Minecraft player has to say.

OSAGYEFO DR. KWAME NKRUMAH (1909-72) Founder and Father of the Nation Osagyefo Dr. Kwame Nkrumah, the first Prime Minister and President of Ghana, stands out not only among the Big Six but also among the greatest statesmen of history. It was he who canalized the discontent of the people of the Gold Coast Colony into the highly organized movement of protest against British rule, and within a relatively short period won political independence for Ghana on March 6, 1957. With Ghana independent, ...

Recycling your garbage is noble and, in many places, mandatory. But it also can be very confusing. This guide will clear up the rules.

There are a few significant improvements for your iPhone with the iOS 17.5 software update, released May 13, but my favorite is Apple's enhancements to the Apple News app, which is making its Puzzles section even more fun with Game Center integration and even a new type of word puzzle.

There's a way to get instant access to your most-used websites and webpages on your iPhone, and these shortcuts live directly on your Home Screen. Whatever you need fast, frequent, or more convenient access to, whether it's a vital web document or a web app without a native iOS app, your browser can make it happen.

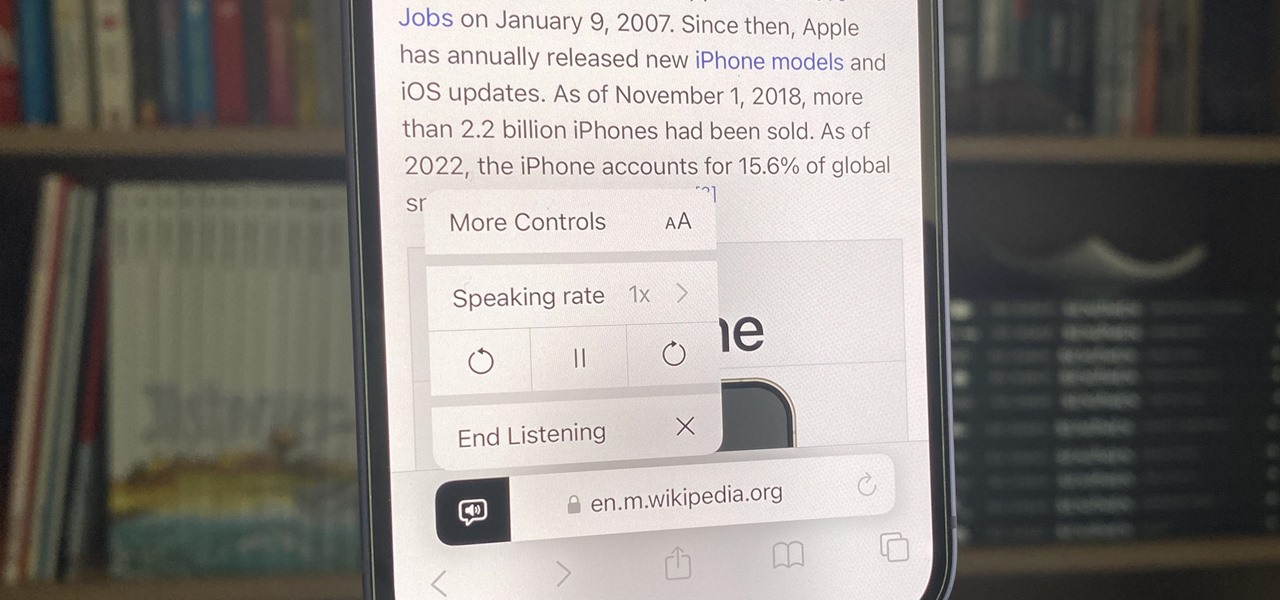
Speech-to-text technology can be seen on your iPhone in various places, from the Dictation tool to Apple's new behind-the-scenes, auto-created transcripts for podcast episodes. Your iPhone also has some pretty impressive text-to-speech capabilities. With them, your iPhone can read webpages, documents, or whatever text is on the screen out loud to you — only some of these tools aren't easy to find.

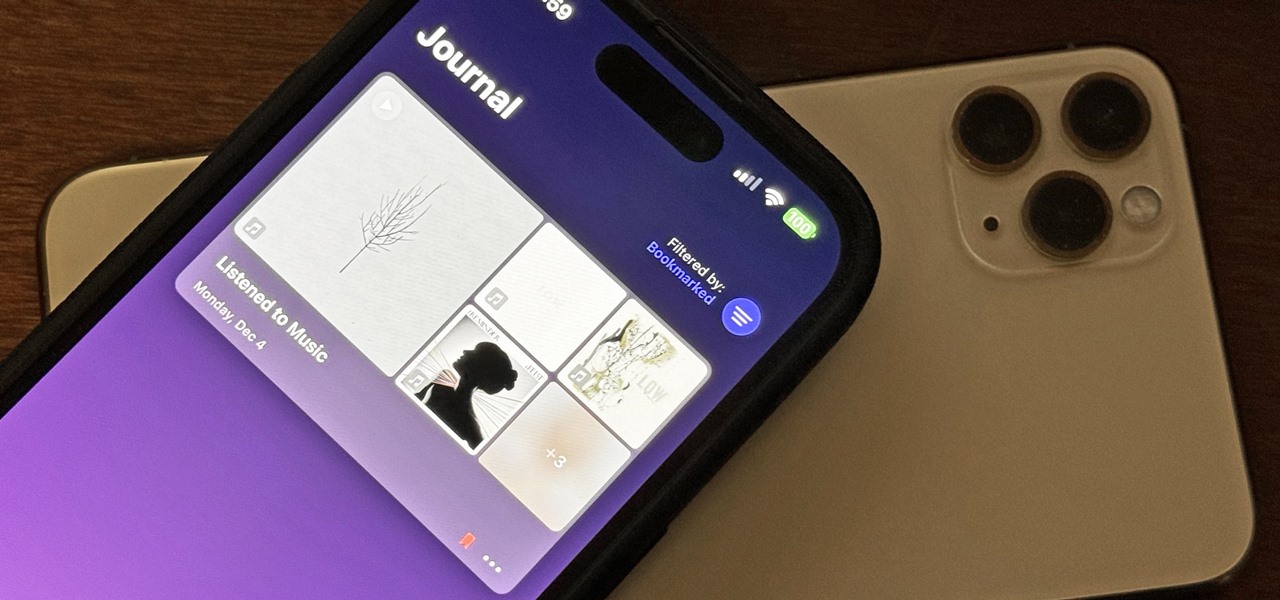
Perhaps the biggest new feature within Apple's iOS 17.2 update for iPhone is Journal, a new journaling app designed to help you take a moment to reflect each day using reflection prompts, recommendations via on-device intelligence, and suggestions for recent activities and events.

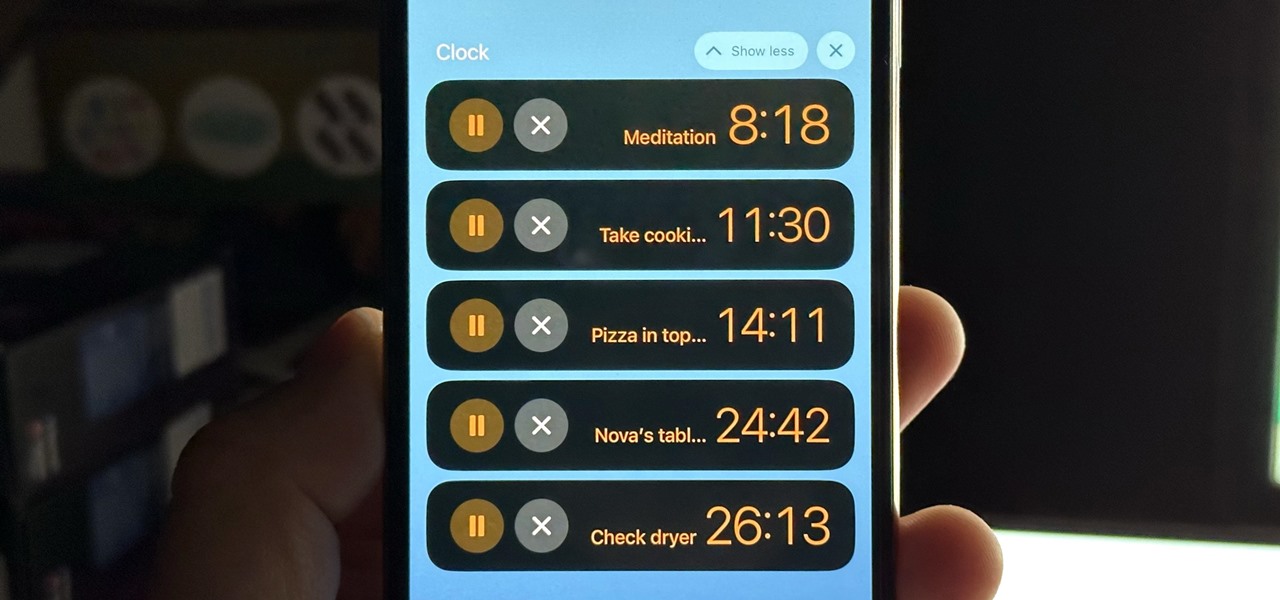
Aside from the addition of bedtime sleep schedules five years ago, Apple's Clock app has largely been ignored with each new iOS software update. But that just changed with Apple's iOS 17 software update. With the updated Clock app, you can finally set more than one timer to run at the same time.

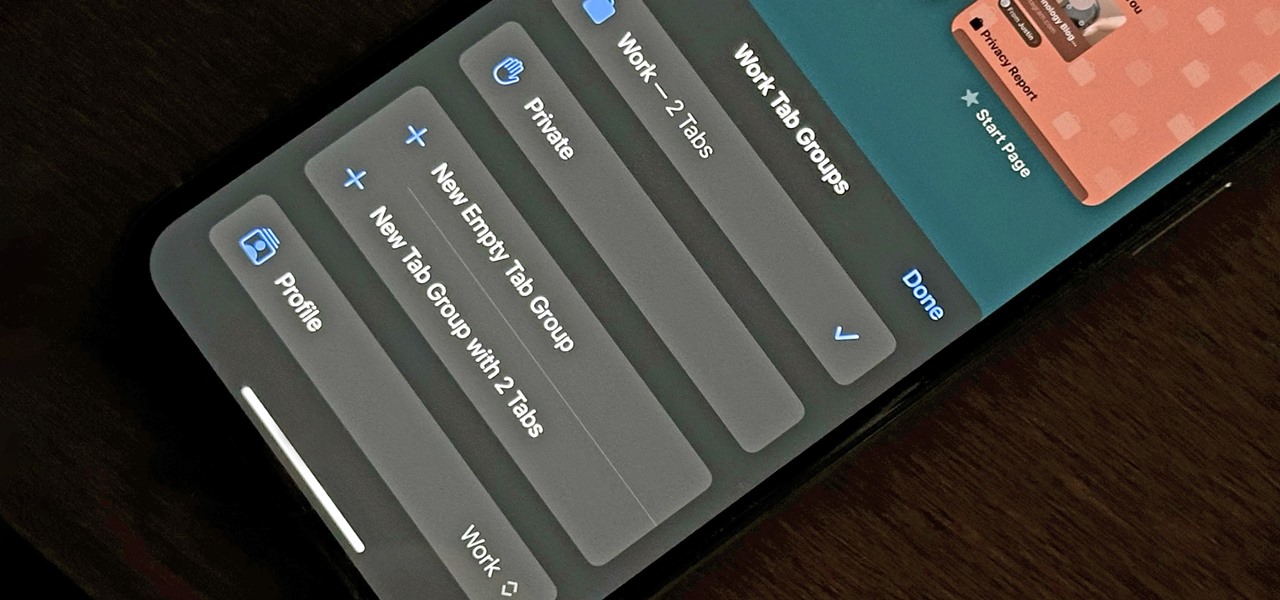
Apple is finally adding profiles to Safari, so you can now keep your personal, work, and other topical browsing totally separate in their own instances, with their own history, cookies, website data, and active extensions.

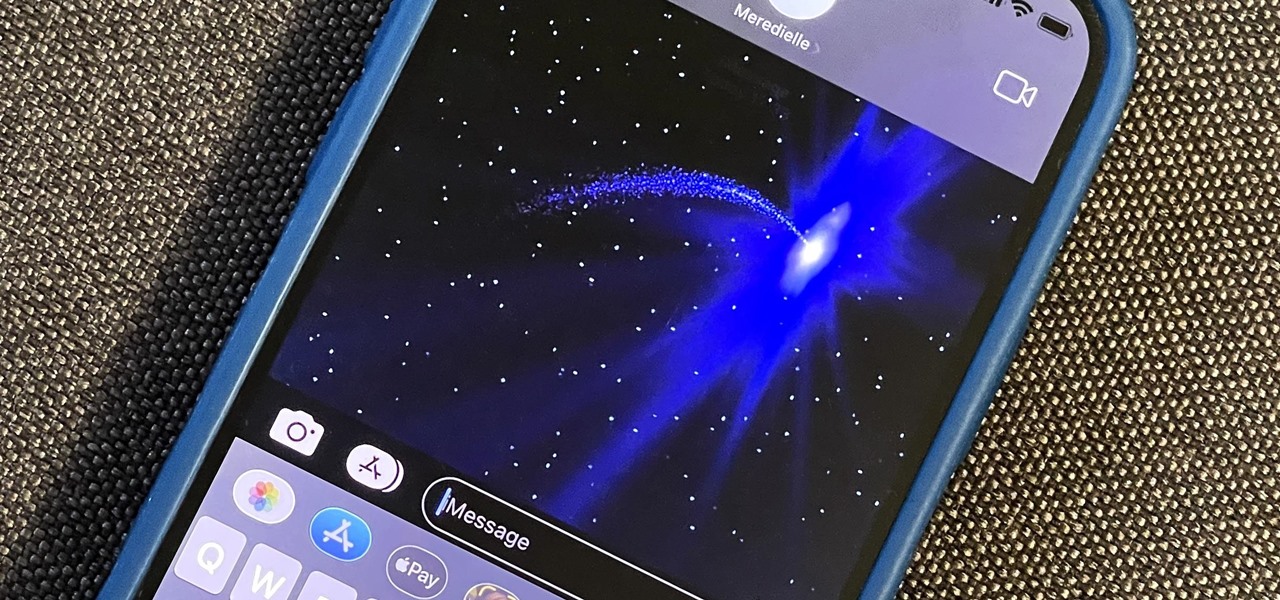
Apple has a secret iMessage effect so hidden that there's only one way to unlock it, and it's not by digging through the Messages app's settings, tools, effects, or interface. However, it's used the same way whether you're messaging from an iPhone, iPad, or Mac, so it's easy to remember once you know.

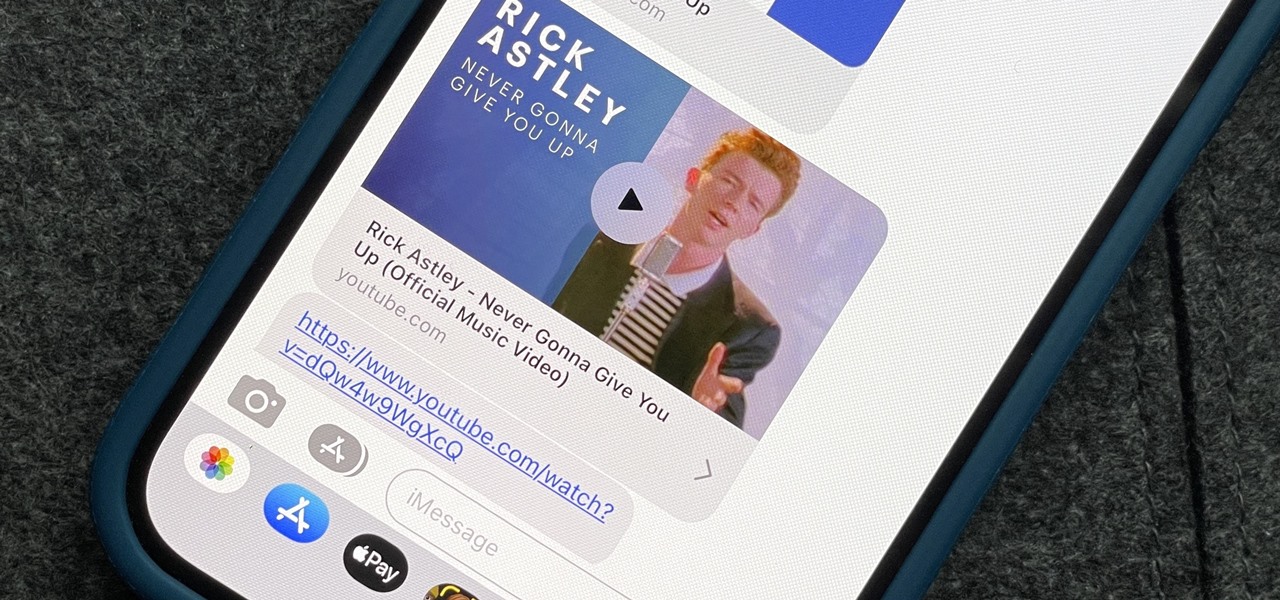
Apple automatically converts most URLs in the Messages app into rich link previews, but they aren't always pretty, and sometimes you just want to see the full URL instead. While there is no setting on iOS, iPadOS, or macOS that disables rich link previews in the Messages app, there is an easy way to show the URL complete with the scheme, domain name, and path.

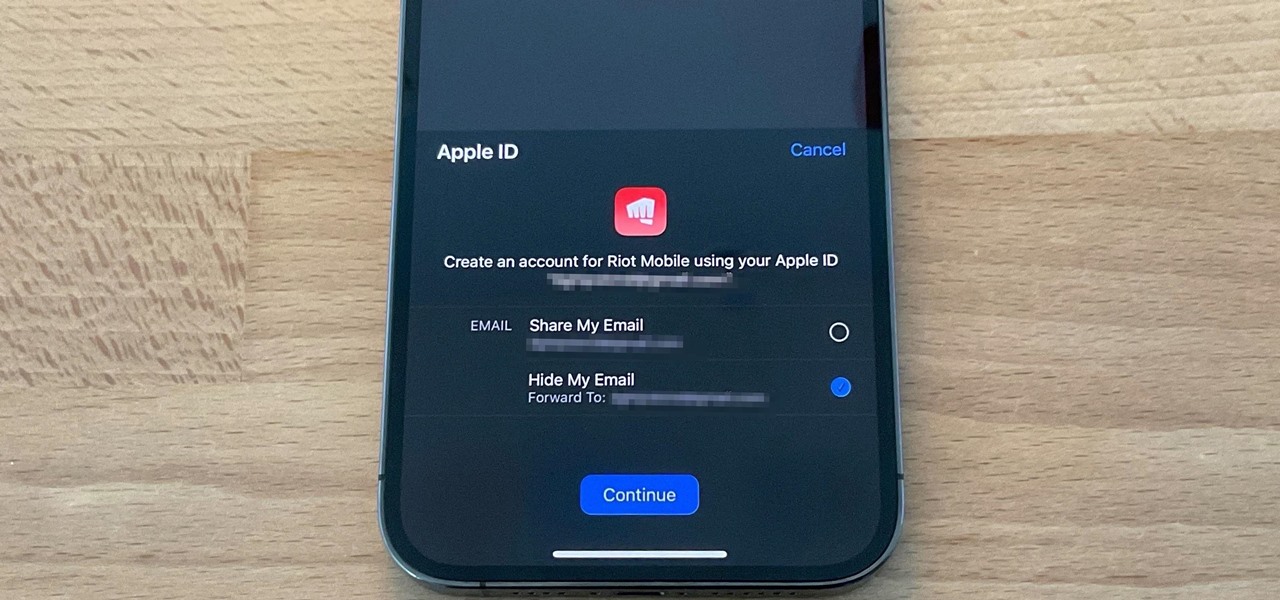
The "Sign in with Apple" service lets you create accounts with third-party apps and websites more easily using your Apple ID. More importantly, it can hide your personal email address using auto-generated disposable email addresses. However, it's easy to lose track of the accounts you use with Sign in with Apple, as well as any throwaway email addresses you used to hide your actual address.

The standard way to sort your notes and to-dos in Reminders has always relied on you putting them in the correct list and group. Then came smart lists for flagged and scheduled tasks, followed shortly by a smart list for tasks assigned to you. In iOS 15, Apple brings yet another way to find your reminders more easily — tags.