In a riveting interview on TruNews Radio, Wednesday, private investigator Doug Hagmann said high-level, reliable sources told him the U.S. Department of Homeland Security (DHS) is preparing for “massive civil war” in America.

SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and encrypted connection. This is handy for a multitude of reasons.

Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm here to teach you how to create a general encrypted container—not the complex hidden TrueCrypt volume.

The battle to be the video editor for your iPhone continues with the debut today of Cinefy at CES. An app that promises to bring 'Hollywood-style' visual and audio effects to your phone, Cinefy comes loaded with over 50 effects to add to your movies as well as a library of copyright cleared songs.

Introduction I will not go into some time-waster of a story about how I came to build this app. It was a prerequisite in a bigger project I am still tinkering with from time to time.

Bluffing is one of the key components of poker. You may have a horrible hand, but if you can play it cool and raise the bet, you might just be able to convince your opponents otherwise and induce a few folds. But if you can't handle a little subterfuge, then you shouldn't be playing the game. Even the slightest tell could give you away. You have to maintain a poker face, no matter what.

Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic function. The encryption header stores the password that you have entered for the archive, which allows the data to be reversed and read from. Encrypted data is safe from anyone who wants to read it, other than people with the ...

Welcome to WonderHowTo's first Weekly Community Roundup! Each week we will be featuring the best projects from the community, as well as ongoing challenges and activities you can partake in. WonderHowTo is made up niche communities called Worlds, so if you've yet to join one, get a taste of what's been happening this week in the highlighted Worlds below...

OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.

Improve your bingo skills with a roundup of this week's Scrabble Bingo of the Days. What exactly is a bingo? It's when a player empties his or her rack in one turn, placing all seven of their letters on the board to create a word that's at least seven letters long.

Web-spying technologies like FaceNiff, Firesheep and Newstweek are out there showing the world just how easy it is to see what you're doing online, but they're amateurish in comparison to what real hackers could do to you if they catch you browsing unsecured websites.

Stuck in a relationship that is going nowhere? Do you wake up and it's nine years later and nothing has changed? Do you also dream of sheep? You know, in the non erotic sense? Well welcome to Catherine, a puzzle game of non-commitment and text messaging.

Inspired by the beauty of traditional signage printed on doors and buildings, Rero is a French graffiti artist who makes a simple, yet heavy mark. Using the universally common Verdena typeface, Rero brands abandoned public spaces in extreme disarray with his own codified messages based on theories of public use of imagery and private property.

Every key on a telephone keypad has its own sonic signature, a sort of calling card composed of two distinct tones: one high, one low. While it's easy to tell the difference between the individual pitches in a single row—see, for example, this article on using your cell phone as a musical instrument—, it's often difficult to differentiate between notes within the same column. Unless, of course, you outsource the work to a computer! Which is what Uruguayan hacker [Charlie X-Ray] recently set o...

In the picture for this post you can see a grab of David Kassan's DVD sales page. The reason it is there, is if you really want to be the best, you should know how to draw. I suggest buying this DVD and anything from David Kassan, Jeremy Lipking or Tony Pro. If you want to learn, why not learn form the best?

Professor Wafaa Bilal of New York University plans to soon undergo a surgical procedure that would temporarily implant a camera in the back of his head. The project is being commissioned for an art exhibit at a new museum in Qatar. The Iraqi photographer will be a living, breathing cyborg for an entire year, during which the implanted camera will take still photos every minute, simultaneously feeding the images to monitors at the museum.

Relax, it's not as messy as it sounds. Pee-on-a-stick, at home STD tests may be available in UK pharmacies soon, complete with an incredibly convenient app that would save you a trip to the clinic. It works like this: if you suspect you may have an STD, you would pee on a device which is then inserted into your mobile phone. The app then "diagnoses" your sample and returns results.

Yes. That's right. The 2010 National SCRABBLE Championship (NSC) is almost here. In fact, it starts in less than 2 weeks! And if you were lucky enough to register for the competitions, you could win a first place prize of $10,000!

Co-Directed by WonderHowTo's Ford Austin. Do any of those actors look familiar? If you like it vote for it here

These are great times. It is about time advertisers invaded our video games in the same way they do our driving (billboards), walking (fliyers, posters), and our private home (emails, bulk mail, text messages).
Cheating ruins everything. Cheating makes game play unfair for others who may be truly competitive and strategic. Cheating makes others disrespect and un-friend you. There can be unforeseen consequences, like getting viruses, trojans or your account hacked from downloading a cheat/bot program. And you will get banned from the game for violating terms of service.

Whoever said crime doesn't pay? Norway's luxury Halden prison may very well be nicer than your home.

What more is there to say about the almighty Conrad Schnitzler? One of the original founders of Tangerine Dream and Kluster (later Cluster), his contributions to the world of German experimental electronic music have been enormous. With album, cassette, and cd releases miles long, his discography would take a lifetime and a pretty penny to catch up to. 'Conrad and Sohn' is a pretty unique release, even for Schnitzler. The album was a private press release that he did with his son in 1981. App...

Bikini vs. The Wave I have always been a fan of the bikini, but it hasn't always loved me back.

Today's WSJ takes a tour of Russian billionaire Andrey Melnichenko's 394-foot insanely luxe yacht, coined "A".

A huge part of the fun that comes with TikTok is watching your videos go viral. To that end, the popular social media app has a simple way to let you instantly see how many people viewed your videos and photos

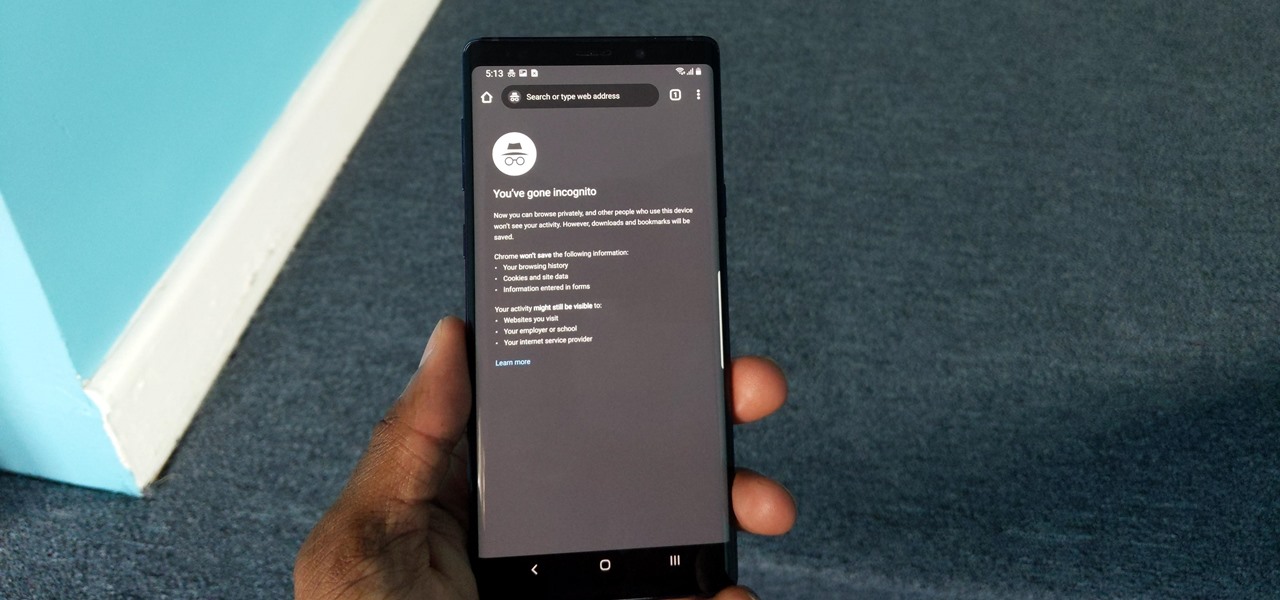
Chrome's Incognito Mode gives you a layer of privacy when browsing. While it's enabled, your browsing history, cookies, site data, and information entered in forms is not saved, making it perfect for, cough, more private web usage. With an Android smartphone, you can jump right into this mode.

Snapchat has added three new features, letting you personalize your snaps more than ever. One of those is links, which was not allowed at all before. The other features allow for greater personalization of snaps, with both visual and auditory choices.

In light of his recent controversial firing, Former FBI Director James Comey will testify to the Senate Intelligence Committee in a highly anticipated open session today at 10 AM EST / 7 AM PST. The testimony will be in regards to alleged Russian involvement in the 2016 presidential election. It will be the first time the former FBI director will speak in public since the firing. So, you do NOT want to miss it.

Encryption is on everyone's mind these days, from the FBI's battles in court with Apple to WhatsApp's recent announcement of end-to-end encryption for their one billion users. Now you can add Signal, whistleblower Edward Snowden's favorite messaging app, back to that whirlwind discussion. Created by Open Whisper Systems, Signal is an encrypted messenger app that allows you to send text, images, video, and audio messages without the fear of prying eyes. They already have an Android and iOS app...

Almost everyone uploads their very personal photos in facebook trusting facebook's privacy settings. But question is - is facebook's privacy settings really that trustworthy? Few months ago, while browsing facebook, I found that one can easily access your private photos using the same browser you used to browse facebook.

Do you want to know what's better than a bouquet of a dozen red roses? How about a bouquet of bacon roses? Or, if you aren't a meat-eater, a bouquet of hand-crafted origami roses or ones made of duct tape that won't wither away within a couple of days?

PDF files are awesome because they're easy to share and they prevent the format on your document from being messed up, no matter what system or program it's opened in. Their biggest downside, though, is how difficult they are to edit or change once they're made.

In an effort to help posters see the various ways that people discover their posts, Q&A site, Quora has decided to make who views each post, public, along with information on how each viewer came to see the question (ex: through an email, a followed tag, or other public stream). This would probably be an interesting, helpful, and universally liked feature, except for one thing...

The EcoJet. No, it's not a economy-sized jet engine aircraft. It's Jay Leno's version of an eco-friendly car. A very, very fast eco-friendly car.

It is Saturday. Party. Dance. I have wanted a tutorial/breakdown of the booty dance for more than a year. Hell, I did not even know what to call the move before this video entered my life.

Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information you want to keep private, private, should be important to you.

If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! moment. Your private info is both your biggest weakness and your biggest weapon in your battle to remain anonymous. You must learn how to use it as both.
The recent report of the ubiquity of extrasolar planets coupled with the fact that it bodes well for searches for life friendly Earth twins, brought me back to my reading of Carl Sagan's 1966 Intelligent Life In The Universe and later article in Sky & Telescope where he came up with a remarkable number in favor of such.