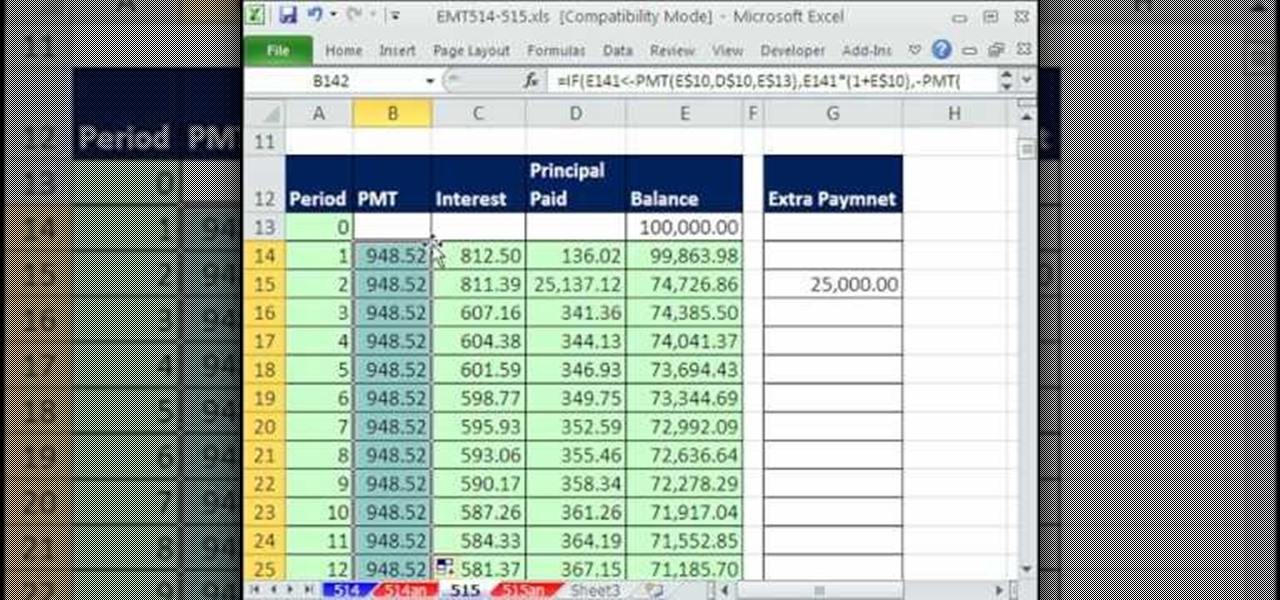
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 515th installment in their series of digital spreadsheet magic tricks, you'll learn how to create an amortization table that will update when you pay extra principal so that loan is paid off early. See also how to make changes to a template, get into trouble, then trouble shoot your way out of it so that you can fix ...

You should watch this video if you want to improve your credit score with just 3 steps. To improve your credit score: Check your credit report. It is where your score comes from. You can also get a free copy of your credit report once a year at Annual Credit Report. Check it for errors. Timing. If you're going to apply for a loan as the application month approaches, stop charging because if your balance happens to be reported while it's big, it will temporary lower your score. Don't close you...

In this video, you'll use Scope and create a simple calculator while learning a little about private, public and protected properties in OOP programming. If you're looking to bone up your PHP coding skills you'll want to check this video out.

If you're Apple computer needs a little cleaning, not the hardware, but the software, then MacKeeper is the way to go. This application will help protect your hard drive from junk and other useless data, freeing up much needed space on your Mac. Also, you can recover files, hide private files, clean up your login items, apps and plugins, and more! Watch this video to see how to use MacKeeper.

In this tutorial, we learn how to sound like a biological woman while speaking. There are many different techniques to help you speak like a woman, including going into falsetto. This isn't about getting the sound, it's about learning how to not speak with resonance. You want to focus your voice up in your throat instead of deep down. You probably haven't used the muscles for this voice, so using falsetto is a great way to practice. You may be able to speak a few minutes and feel yourself fal...
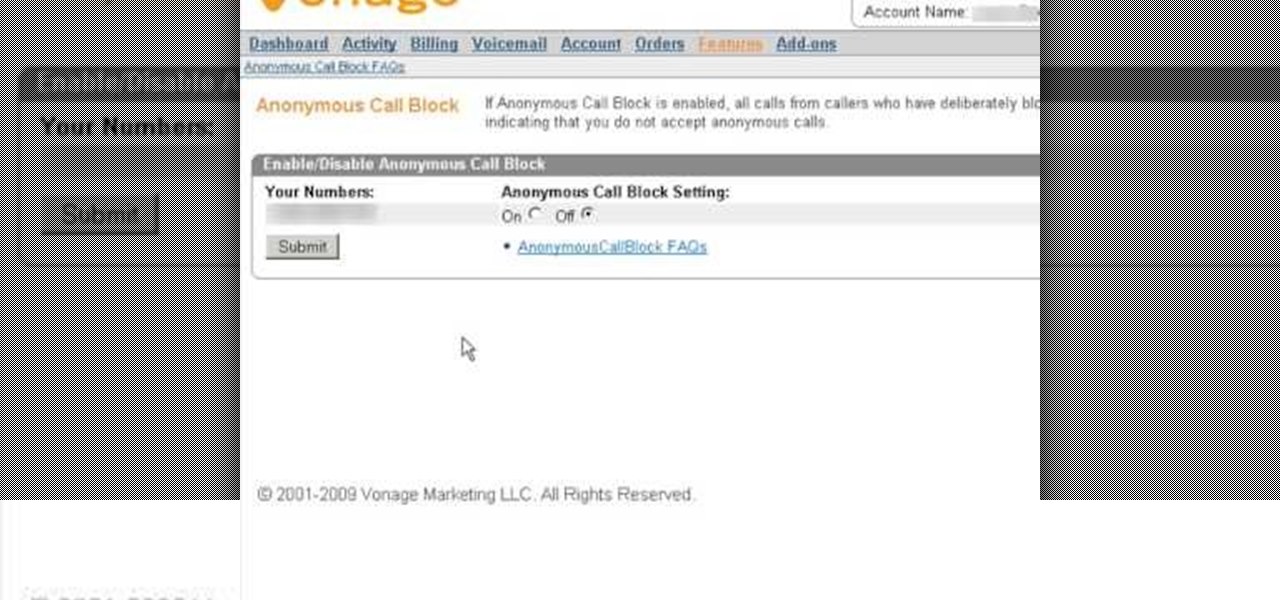
If you are looking for a way to prevent telemarketers and nothing else is working, consider signing up for Vonage's call blocking feature. In this tutorial, brought to you straight from the professionals at Vonage, learn how to set your phone to block any incoming call without a number attached to it.

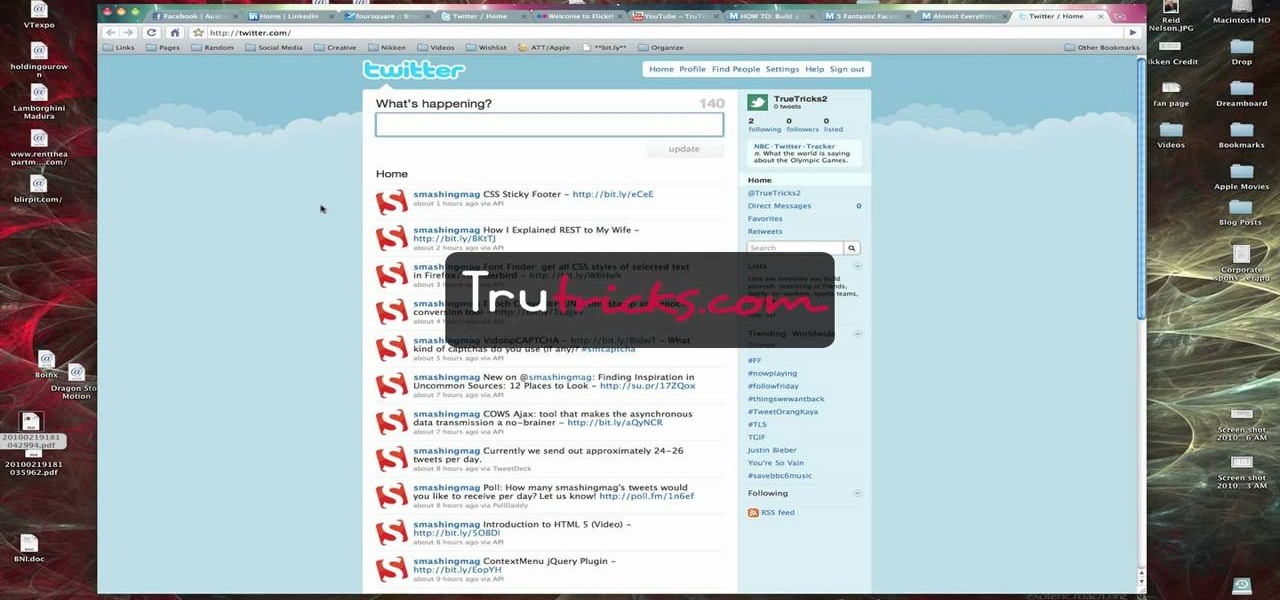
Brian explains us how to use Twitter, one of the best social media networks out there. One thing to notice is that Twitter allows you to send text messages up to 140 characters. In the right corner you can see you account name and your avatar which can be changed from the settings menu. Twitter allows you to follow people and be followed by people. Basically when you follow people you will be able to see messages they post and when people follow you, they will see what you post. Twitter is a ...

Starting an independent record label, like starting any other business, requires a well-conceived plan with clear goals. Check out this tutorial and learn how to take your love of music and turn a profit.

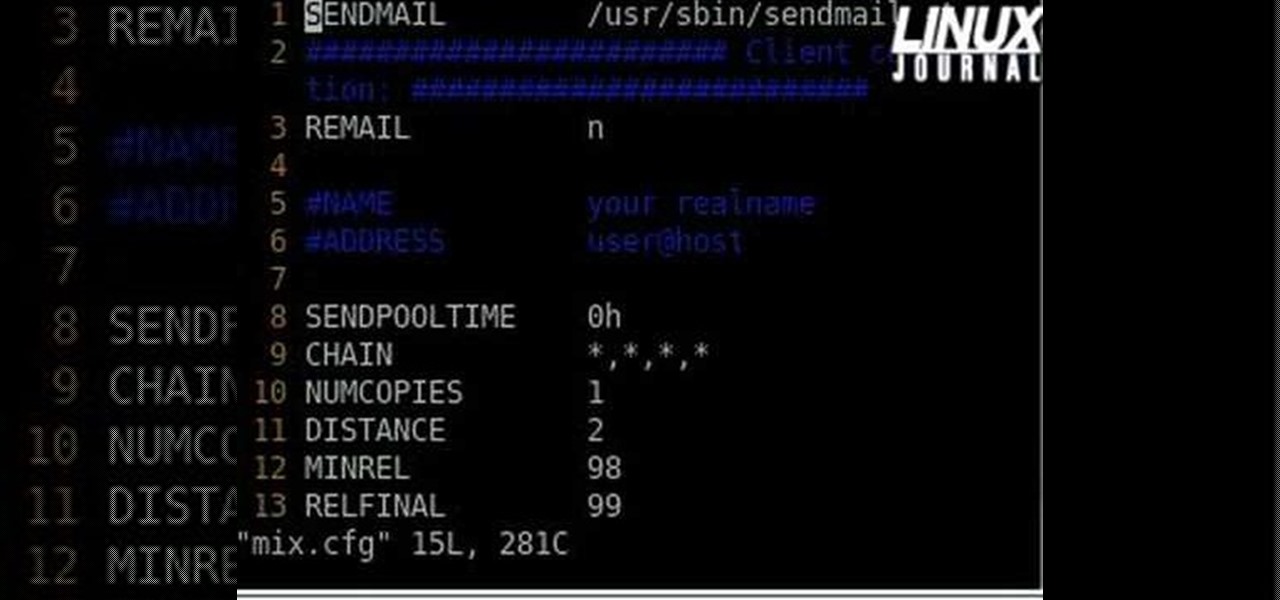
Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.

If you're using the Private Browsing feature in Safari, you'll still need to do more to keep your surfing history secret. This helpful software video tutorial shows you how to cover your tracks in the Apple application Safari.

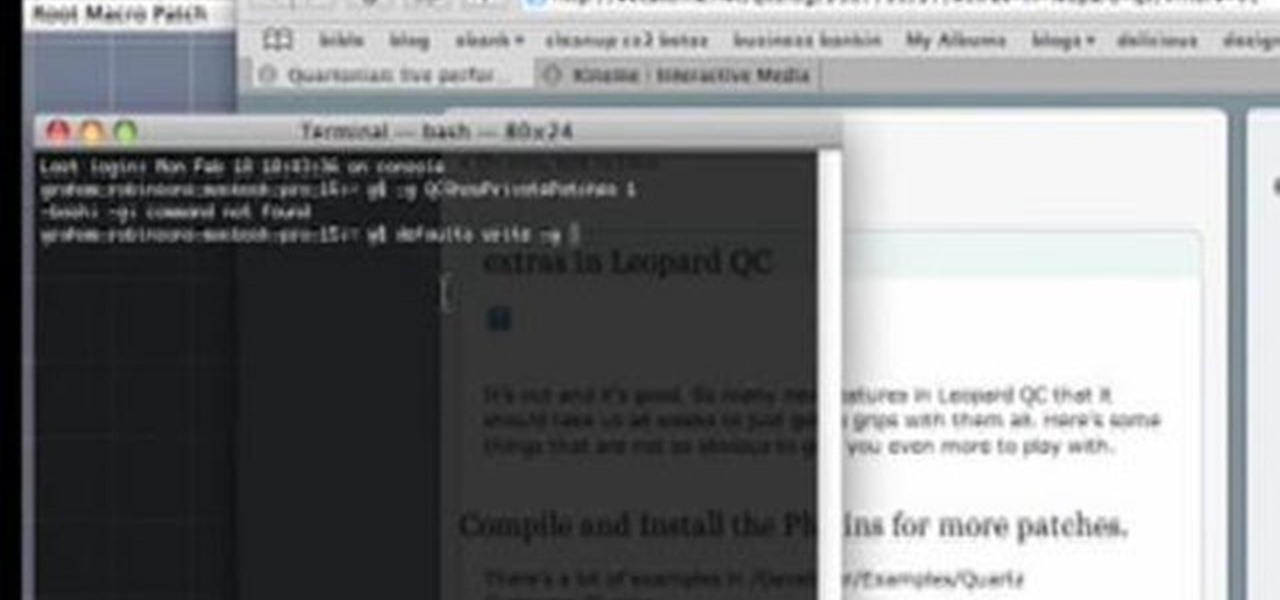
This is a very basic introductory video that teaches you how to successfully install Quartz Composer on your MAC OSX 10.5 Leopard. Quartz Composer is a node-based graphical data software that uses visual programming language. Built exclusively for use on the MAC OSX, it's a handy software for graphic designers.

Some of the new features in iOS 15 take some getting used to, and the biggest one of those is Safari's relocated search bar, aka address bar. There are more than a few reasons why it's a jarring change, but the good news is that you can return Safari's search bar to its pre-iOS 15 position at the top of the screen.

At the Microsoft Build 2017 conference in Seattle this past week, 3D application and game platform Unity, partnering with Microsoft, launched a contest that drives HoloLens developers to realize their ideas into a full-fledged application and possibly win money for it.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

Make sure your private documents are completely secure. This episode by Tinkernut deals with not only encrypting your files, but also hiding them in a hidden volume.

The people of Iceland forced their corrupt government to resign. A public assembly was created to rewrite the constitution.

Is the proper term nudists or naturalists? Doesn't seem to be too much of a difference, because when it all boils down, they're both still butt-naked on the beach. Nude beaches are fascinating places for the adventurous spirit, but unless you’re an old-time nudist, you probably have questions about the proper way to behave on a nude beach. Well, we’ve got the answers.

If you're looking to improve your browsing experience, then a VPN is the right way to go. If you're tired of censored or geographically blocked sites and wary of companies selling your data, then a good VPN can be your answer to a problem that limits every aspect of your experience online.

Whichever web browser you use, each comes with a way to surf the net "secretly." While nothing on the internet is truly anonymous, private browsing modes can help keep your movements hidden from those who might have access to your data. The "secret mode" for the Samsung Internet app goes a step further on Android, by locking your private browsing behind a unique password.

Microsoft is working hard to make Bing a good alternative to Google for more than just looking up images of the "human anatomy" that Google and a lot of other search engines filter out of their results.

To get the "Hail Mary" achievement on Read Dead Redemption, it's going to be quite a challenge. This is almost impossible to do while standing on flat ground, but it is possible.

This achievement can be earned on the Outlaw to the End downloadable cooperative mission in Read Dead Redemption. To get the Dodge This achievement, start a private match with a friend on the Herd mission. Once the mission starts, select the bolt action rifle and the rolling black rifle. Use the bolt action as your primary weapon, and shoot the TNT crate next to the tent on the righthand side. Quickly switch over to your rolling black rifle. Have your teammate use one of the repeaters to weak...

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...

In this video tutorial, viewers learn how to use Flickr photos in their screen-saver. This task can only be done on the Windows computer. Users will need to download the program from the website provided in the video. Once downloaded and installed, there is an option in the Screen Saver Settings. Users are able to take photos from specific users or groups, or can search through tags and contacts. Further options include selecting the size of the photo and delay between switching the photos. U...

In this clip, learn how to add your own personal files to your Barnes and Noble Nook and make it a portable carrying device. This tutorial will show you all the steps you need to get anything from photos, videos, music files and personal documents onto your e-reader. This process is pretty easy and once you view the clip, you should be all set to start side loading. Who needs an iPad when you have a Nook?

In this video, presented by the experts at the St. Louis Community Credit Union, learn how to prevent thieves from stealing your identity or account information. These days, between paper bills, Internet banking, social networking and all the other ways we interact, there are many ways for crooks to get into our private lives.

When conducting mobile convert surveillance, you will be following someone and it is important to dress appropriately for the environment and carry your surveillance equipment in a bag that will fit into the scene.

When you need to gather information without anyone knowing you will need to utilize covert audio surveillance. There are a variety of ways and technique to most effectively get the information you need.

Have you ever had to close an application with private info in order to let someone else use your PC? LockThis! is a windows application that lets you secure individual programs without the hassle of having to save your progress and closing the program. To use LockThis! just hold the control key and click on the application that needs to be locked and simply enter your password on the dialog that pops up and your done. Now anyone can use your pc without you having to look over their shoulder....

Hak5 is at it again, with a plethora of somewhat accessible solutions to your technological problems. If you've ever needed to get through your school's firewall, or secure traffic tunneling, or try out applications in a fast, efficient manner? This video has it all and more.

The augmented reality space is brutal, and that means shifting directions quickly to meet whatever need the market demands.

Unless you want to make your TikTok account totally private, anyone that uses the app — with or without an account — can view your profile and all the videos of you performing new dance moves, singing along to popular songs, and recreating your favorite TV show scenes. Even worse — they can download those videos.

A new augmented reality cloud platform from German startup Visualix is working to give enterprises the capability to scan their own warehouses, factories, and stores and create maps for augmented reality navigation.

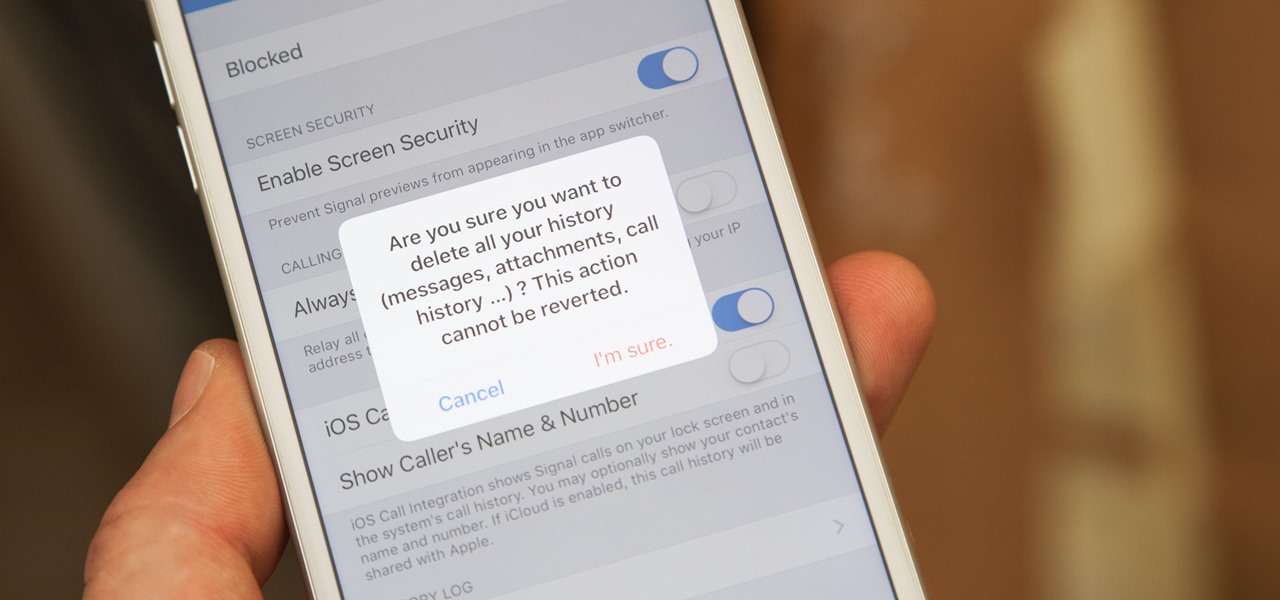
If thieves, hackers, law enforcement, or other would-be enemies should ever gain entry to your smartphone, they could also access conversations you've had in Signal Private Messenger. To better secure your encrypted communications, you can password-protect the whole app and its contents — but only on Android. Even then, it's necessary to perform data deletion on a periodic basis, if not immediately.

A spokesperson from the Nissan and Renault Alliance told Driverless the group is testing self-driving electric "robo-vehicles" for future mobility services and is "not ruling out anything" for future services the group might offer, as the alliance widens its driverless business model to include both fleets and private sales.

With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.

As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache has been vulnerable for up to two years.