
Hugging the Web (Part 1: Introduction)
Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.


Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

In an attempt to increase advertising revenues, Snapchat introduced Discover back in January of this year, a feature that brought a handful of prominent media partners, such as CNN, ESPN, and Vice to your feed, along with their tailored news stories and videos.

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.
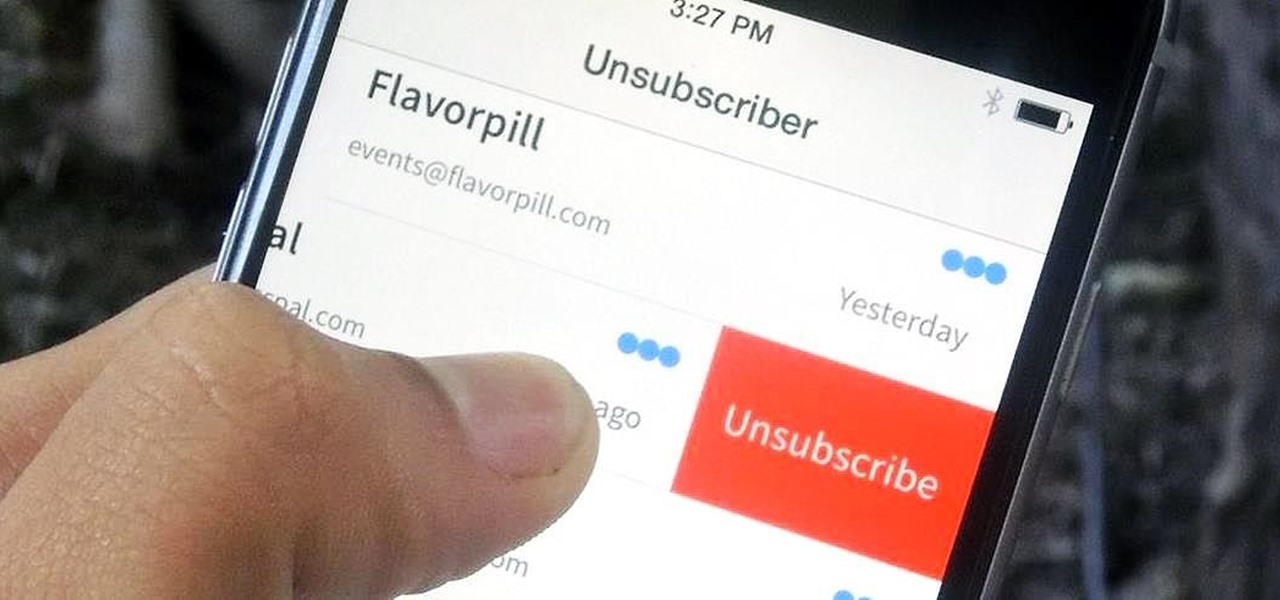
You've undoubtedly used your email address to sign up for a chance to win something online or to purchase something on sale. Often, these offers are too enticing to pass up, and you reason that you'll live with the consequences of handing out your information for the chance at making out big.

An app with overabundant features can make it more customizable, but too many options can also be overwhelming, even on a mobile web browser. If you're tired of Safari or Chrome on your iPhone, try out Frameless from developer Jay Stakelon, a simpler web experience using just the essentials.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.
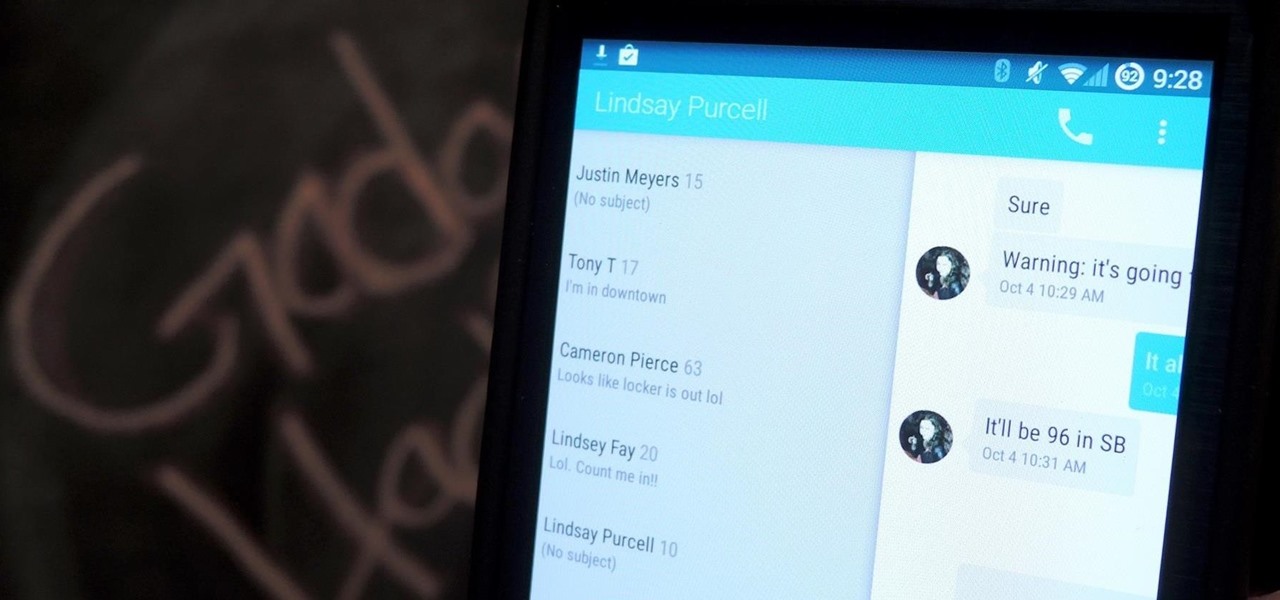
Google's Android L developer preview has given Android a more refined look, with developers excited to update their apps with the new Material Design UI. While some apps are slowly getting updated, QKSMS (QK for quick) is a 3rd-party text messaging app that was built with Material Design in mind.
Anytime you surf the web on your iPad or iPhone, Safari saves which webpages you visit, the information you enter into them, and other types of data. This not only make your internet experience quicker, but it'll also keep track of everything you're doing.

When I stumble upon a new song that I'm really into, I don't just listen to it repeatedly—I share it with family and friends that I think might enjoy it just as much as I do. Now, thanks to a new iOS app called Craaave, sharing those tunes are a cinch, no matter if I'm using Spotify, SoundCloud, or any other music streaming app on my iPhone.

Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left frustrated and sent back into the Wi-Fi menu for another access point.

Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.

When it comes to blocking unwanted calls, your Android device comes stocked with a native blocking feature that allows you to reject certain phone numbers. That being said, the native blocking feature on the Samsung Galaxy Note 3 isn't the prettiest or the smartest, with its non-obvious setup and lack of features.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

Apps that have no business accessing the internet can share your location, device ID, and other personal information with potentially malicious data snatchers. If you're connected to the internet on your Nexus 7 tablet, you're a potential target for cyber threats.

The Samsung Galaxy S5 was just officially announced at Mobile World Congress. The new flagship device will be available worldwide beginning April 11, 2014, including all major U.S. and international carriers. With over 200 million Galaxy devices sold to date, the S5 doesn't stray too far from the trend, at least not aesthetically. We've still got a high-grade plastic shell with perforated back covers, and four color choices at launch. Our highlights of the release event are as follows.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

What you watch in the privacy of your own home should be no one's business but yours. That was the case until Prime Minister David Cameron decided that there was too much porn available to minors in the United Kingdom.

For a photo- and video-sharing app based around privacy, Snapchat sure has a lot of security holes floating around. At one time, you were able to take screenshots of Snapchats in iOS 7 without the sender knowing, which is something that you can still do on rooted Android devices.

Let's just say it's been a pretty bad year for spies and government agencies and an even worse one for the privacy of U.S. citizens. Edward Snowden blew the lid off the NSA's spy program, and the FBI was recently discovered to have the ability to access your webcam any time they want—without triggering the "camera on" light. Yeah, that means those Justin Bieber lip sync videos you recorded weren't just for your private collection.

Snapchat was created for the sole purpose of removing evidence from your mobile that a photo or video ever existed. That way, snoopers can't find any of these questionable selfies in your photo gallery. Of course, there are plenty of ways around this safeguard, but it's still more private than the standard social networking app.

Facebook knows who all of your closest friends and family are. When you backpacked across Europe last summer, they went along on the trip. Remember that break up two years ago? Yeah, they were there. The breakfast you ate this morning? They probably have a picture of it. They're even right under your own feet.

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

One of the very first Photoshop skills we learned in my tenth grade photojournalism class was cropping the background out of images. I hated it. It was extremely time consuming, and the magnetic lasso tool never seemed to want to cooperate with me.

Social media is where we post our thoughts for the world to see, but sometimes a little more exclusivity is needed. And that's where Scrambls comes in.

The convenience of storing things on the cloud can definitely make life easier, but if you're storing sensitive files, it could be a total disaster if anyone hacked your account. Some encryption services can be expensive, but if you just need it for personal use, there are some really great ones that don't cost anything. Here are three programs that let you encrypt your cloud storage for free. BoxCryptor

We use smartphones for just about everything, and while that may be beneficial to us in our day-to-day lives, it can also be used against us in the court of law.

If you're tired of your roommate stealing your Cheetos out of the pantry or simply want to indulge in something creepy, then keep reading. With the iPhone 5 finally released, many people will soon be selling or giving away their older iPhones. But should they? Instead of ditching your old iPhone, why not use it to engage in some Big Brother type espionage? There are some really awesome ways to use your old iPhone, but spying on people is definitely the most bang for your buck. First, you'll w...

I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still don't want companies snooping in on your online activities. So just how do you protect yourself when torrenting? Avoid "Open Communities"

Considering how often many of us fly on commercial airlines, the idea that a hacker could somehow interfere with the plane is a very scary thought. It doesn't help to learn that at Defcon, a researcher found that the Automatic Dependent Surveillance Broadcast (ADS-B), transmissions that planes use to communicate with airport towers are both unencrypted and unauthenticated.

Want to know someone's private website password? It's the biggest wanted hack: passwords, but how do you do it? Well, this tutorial shows you how to hack any password on any site with JavaScript. But this works best on public computers because multiple people log on to them, which means a better chance at unintentionally stored passwords. It helps to know a little bit about JavaScript before attempting this password hack.

This is an educational tutorial on the basics of taxi operations in Flight Simulator (FSX). Watch and learn ground operations and taxiing a few different planes like the DC-3 and the cub in this aviation tutorial.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

In this video tutorial, viewers learn how to use a nursing cover to breastfeed a baby. This process is very easy, fast and simple to do. It allows the mother to have more privacy when feeding her baby, without having to wear any special nursing clothes or go to somewhere private. The nursing cover simply goes over the mother's head like a apron. People everywhere will not be able to see the mothers nursing, but she can still see everything as she looks down. This video will benefit those view...

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

It's easy to accumulate hundreds of Safari tabs on your iPhone, which makes hunting for specific tabs more difficult, especially when they're spread across different groups. Having too many tabs can even slow down Safari itself. You can close all tabs in a group quickly, but not if you want to save some. To prevent this mess, Safari can automatically weed out the tabs it thinks you don't need.
When you're a writer with work published across various online platforms, building a portfolio of your work can be pretty time-consuming. That's where Authory comes in.

When you first open Safari after updating your iPhone to iOS 15, you might be a bit surprised by the design change. Apple attempted to make browsing the web on its smartphones more natural and cohesive, but it may leave you wondering just how to actually navigate your tabs.

Niantic first unveiled its AR cloud back in 2018, using it to enhance the immersive capabilities of its gaming portfolio.