While it may seem to some like investors are just throwing their money at augmented reality companies simply because the tech is heavily hyped, these money managers do actually want to see a return on their investments.
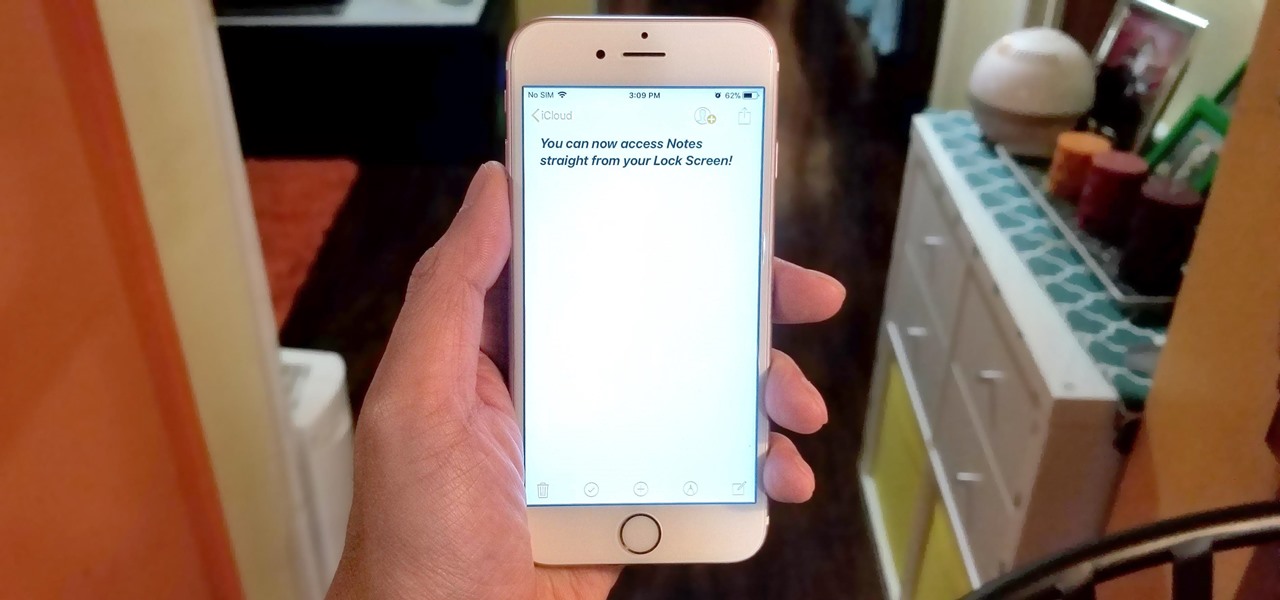
All to often, many of us are struck with a brilliant idea out of nowhere, only to forget about it moments later thanks to the distractions of daily life. Sometimes, the actual process of jotting these ideas down in our iPhones can be a holdup, as the idea we want to record fades from memory before we can even unlock our devices and open Notes to get started.

Using either iMessages or FaceTime on the iPhone is a great alternative for coworkers to stay in touch in the event that messaging services like Slack go down. They're also a handy means of communicating between buyers and sellers, as it provides a more intimate way of either checking out or showcasing a product. But you're not always going to want to give out your real number to everyone.
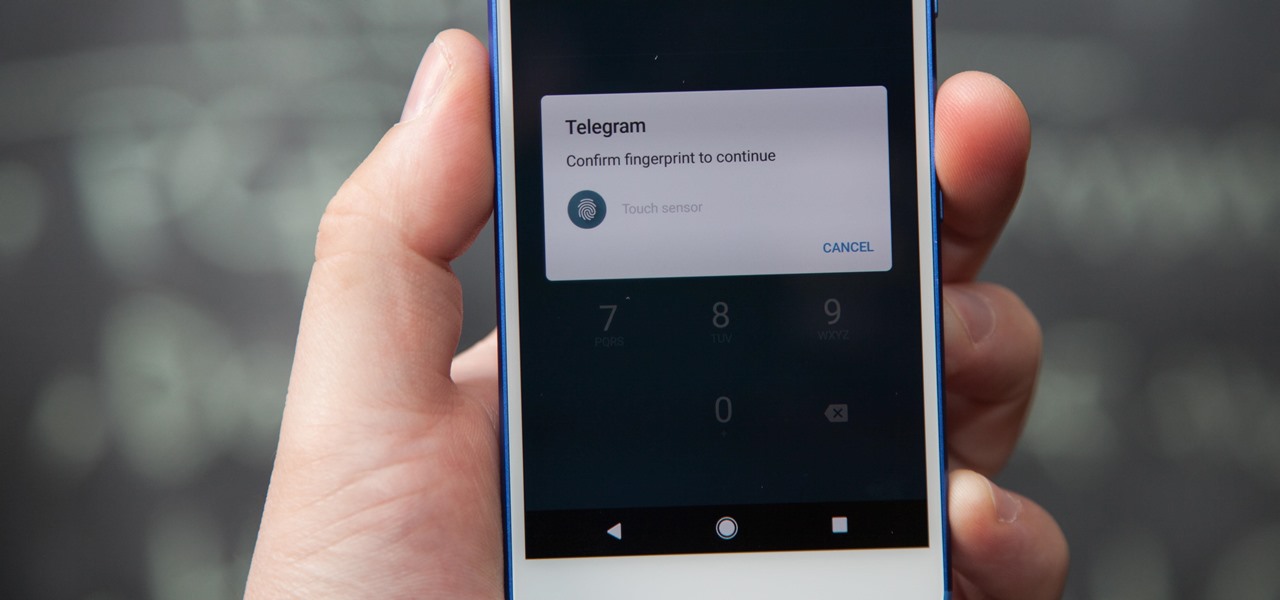
If you're using Telegram for its "Secret Chats" feature, which provides end-to-end encryption for your messages, then I'd highly recommend locking down the app itself with a passcode, PIN, or password. While your phone itself may have a secure lock screen already, if that gets compromised, you'll at least have an extra layer of security on your important conversations.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.
Twitter is a hotbed for abusive accounts. Because it's such an open app, strangers from all over the world can see your tweets. Obviously, not everyone agrees on everything, but sometimes things can escalate to the point where it's considered harassment from people you don't even know.

The new battlefield AR game announced by Skyrocket Toys today is similar to the childhood game "Tag", except the stakes are much, much higher.

Google quickly learned over five years ago electric vehicles (EVs) were the powertrain of choice for its then fledging driverless car program and the industry has since followed its lead.

Self-driving car models and fleets get most of the media attention, but it is the suppliers that design and make the technologies underpinning the driverless revolution, says Guillaume Devauchelle, the vice president of innovation and scientific development for leading tier-one supplier Valeo.

Snapchat announced today that you can now design geofilters in-app, making it easier than ever to customize your snaps. This new feature incorporates a mobile creative studio, so you no longer have to use your computer to create your custom masterpiece.

Waymo claims in court documents filed yesterday in its lawsuit against Uber that ex-Uber CEO Travis Kalanick knew that former Google engineer Anthony Levandowski was in the possession of stolen documents while employed at the troubled ride-sharing firm.

Cruise Automation is actively seeking to recruit a lead engineer to head its development efforts of 3D maps with expertise in city environments, signaling the GM driverless unit's move towards a mobility-as-a-service business model.

People love sex. They don't love talking about the possible repercussions of sex. And with dating apps such as Tinder, Grindr, and Bumble paving new ways for strangers to talk and have casual hookups, people need to be able to more comfortably have a conversation about sexual health and protection. Luckily, now there's an app for that.

Getting support for your mental health is now as easy as opening up Facebook Messenger. By just opening up the Messenger app, you can connect to Woebot, a new chatbot developed at Stanford trained in administering cognitive behavioral therapy (CBT).

Uber's year is going from bad to worse, and they may be subject to a potential criminal probe in the ongoing Waymo legal battle.

In this Tuesday's Brief Reality report, there's a trio of stories from the healthcare world where augmented reality is helping out with surgical microscopes, asthma treatment, and other diagnostic and treatment tools. There's also something for all of you AR/VR storytellers out there.

Apple is notoriously private when it comes to perspective products, but the latest leak from their De Anza office in Cupertino suggests that a new augmented reality device could be coming to a store near you.

A federal judge wants answers after an Uber engineer accused of data theft pleaded the Fifth in the ongoing Waymo versus Uber battle. This privilege would protect the accused, Anthony Levandowski, of self-incrimination and handing over specific documents demanded in a previous subpoena and forthcoming deposition.

A development team in Silicon Valley is nearing early access release of a new hardware-independent augmented reality platform called Phantom AR.

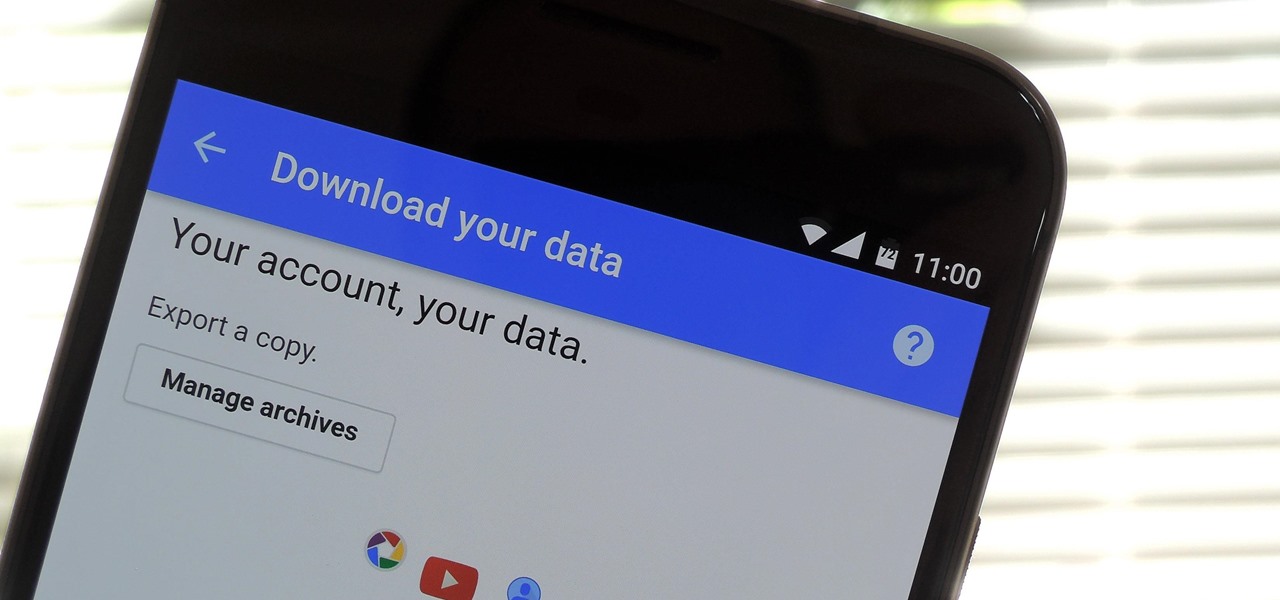
If you're an Android user, Google probably has almost your entire digital life stored on its servers. Family pictures are backed up on Google Photos, your e-book library resides with Google Play Books, videos are on YouTube, chat logs in Gmail and Hangouts, starred places and location history in Google Maps, and so much more.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

With Touch ID enabled, your iPhone needs to scan your fingerprint before you can access your home screen or last app used. Before it unlocks, your iPhone might request that you press the Home button, adding an unnecessary step between you and your data. However, you can turn the feature off so that you don't need to click any buttons to unlock your device.

Are there any benefits to watching a movie in a holographic mixed reality headset, or should you just stick with your TV? It's not as cut and dried as you might think. While TVs have some advantages, so does the virtual screen of a Microsoft HoloLens.

You're only as smart as your communication skills allow you to be, as other people will simply never know your inner genius if you can't effectively express yourself. Regardless of the medium—be it a Facebook post or even a simple text message—this fact remains true.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

If you're ever lost or hurt out in the middle of nowhere with a dead cell phone, you might be able to "flag" down help as long as you're near some railroad tracks.

Whether you're ready to admit it or not, we've all got our alter egos—especially when it comes to the internet. Perhaps you have one Facebook account that you use publicly, while maintaining a second account for more private interactions.

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

If you have some photos, videos, and documents that you want to keep completely hidden and encrypted on your Android device, Andrognito is the app you need. We showcased this app in the past, but since then, CODEX has rebuilt it from the ground up with new and improved features.

When setting up a new Mac, there can be a bunch of settings that need to be changed in order to get the system running the way you like it. That usually involves going through tons of System Preferences panes and app settings—but it doesn't have to.

If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achievable. Plus, we've got 50 promo codes to give away for a free year of service!

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

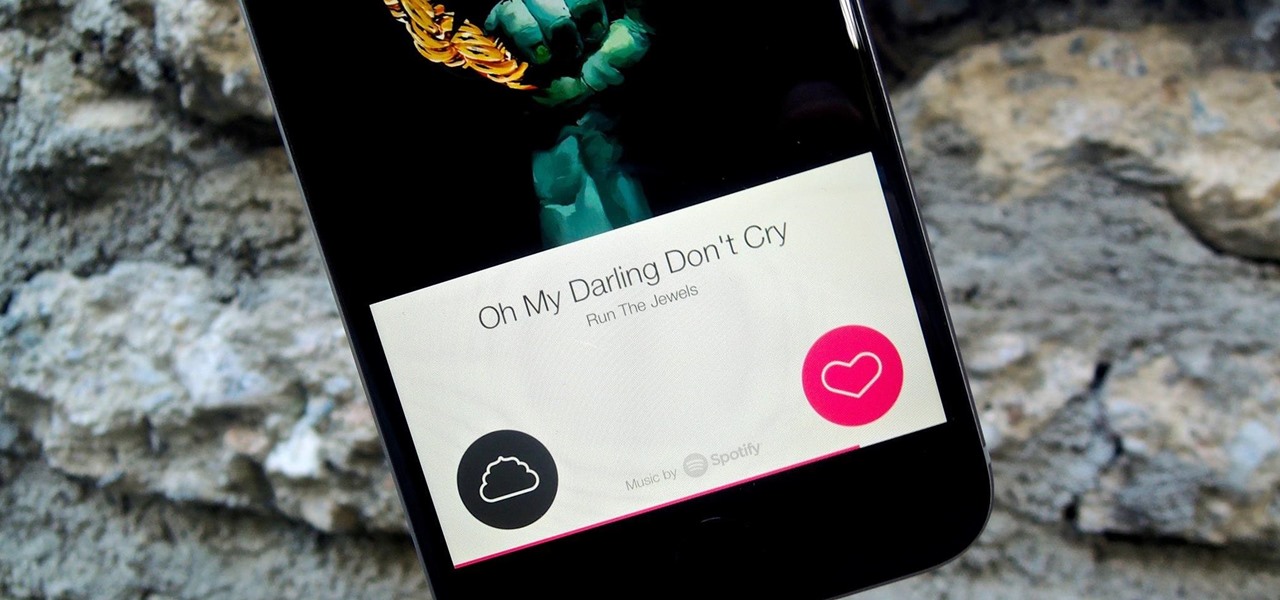
Everyone's a music aficionado these days. Whether you're having a party or on a road trip with friends, someone is always complaining about the music. There's no possible way to satisfy everyone, so instead of having your music drowned out by persistent nagging, turn Spotify into a democracy, allowing the consensus to pick what plays.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

While we now know that iCloud was not exploited by hackers to steal private celebrity photos, Apple did admit that guessed (aka brute-forced) passwords and/or iCloud security questions were to blame for the breach.