Learning a new language as an adult isn't just hard because your brain works differently from when you were a kid. You also have to contend with having less time and energy to practice. However, if you're looking to add another language to your repertoire at a pace you decide, then the Babbel Language Learning: Lifetime Subscription for All Languages: 2-Pack will be a useful tool for you.

HomePod and HomePod mini are excellent smart speakers if you're entrenched in the Apple ecosystem. They even offer ways to protect your sensitive information from friends and visitors who try to ask Siri to spill your secrets. But there's an extra layer of privacy you can put in place to make sure nobody gains access to any important notes, reminders, and calendar events.

After years of testing and modifications, the US Army is moving forward with its customized version of HoloLens 2 from Microsoft.
Your TikTok videos might be interesting, creative, fun, and appealing, but that doesn't necessarily mean you want the entire world to see them. While you're fine with strangers watching your videos, you may not want your close friends, family, and coworkers to see the kinds of mischief you're up to.

We all know that using a VPN not only has a ton of benefits but is essential in our digital age. But did you know that you can get access to your own industry-leading VPN for life with one one-time payment? Even better, we've found an amazing deal on one right now: for a limited time, a YoData VPN: Lifetime Subscription is on sale for just $17.99. That's 69% off the regular price of $59.
For the longest time, we were simply stuck with Safari on the iPhone. Sure, you could install a third-party browser, but Safari was always the default, so tapping on links would always open Apple's app. Times have changed, however, and now you can set third-party browsers like Chrome, Firefox, and Edge as your iPhone's default choice.

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

While much of the world is currently in some form of quarantine due to the COVID-19 pandemic, augmented reality (AR) gives us all the opportunity to see virtual content while stuck in our homes.

As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you can switch to improve your safety online.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

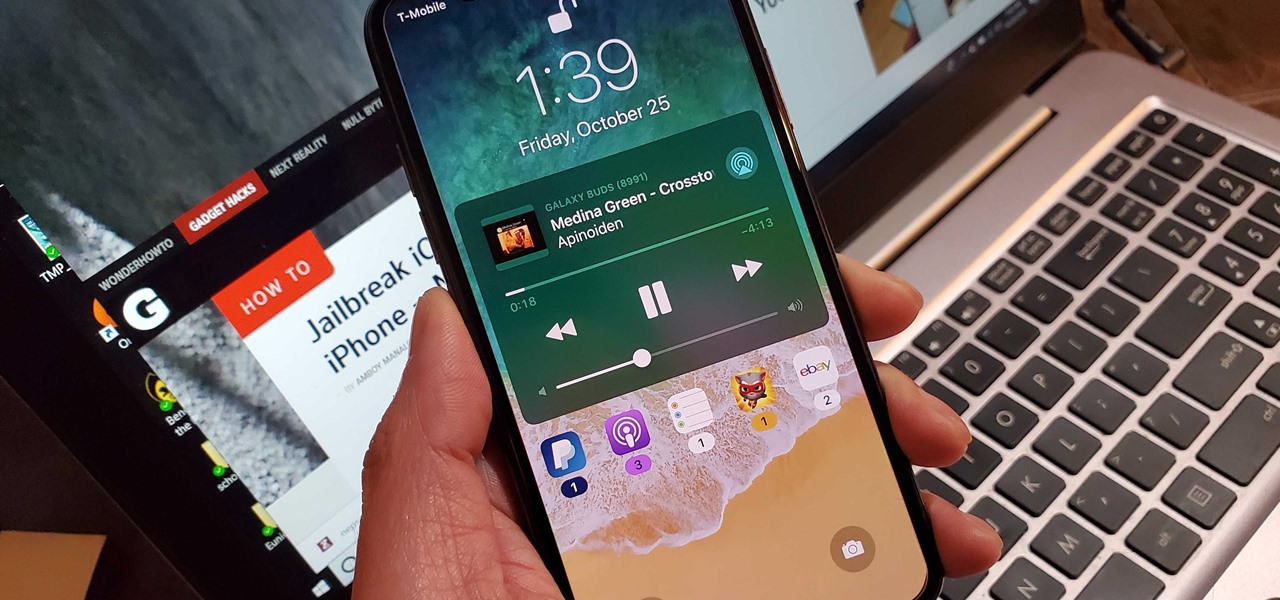
It's easy to take your iPhone's Notification Center for granted. As useful as it is for viewing important alerts, reminders, and more, the feature is pretty drab when compared to the customizable Control Center, Accessibility Shortcuts, and others.

Indian startup Dimension NXG is launching augmented reality headsets into India's consumer market with a bold idea: focusing on immersive computing in education on the high-end. The plan is to give a new kind of AR headset to schoolchildren in remote Indian villages, starting from class 5 (age 10) until graduation.

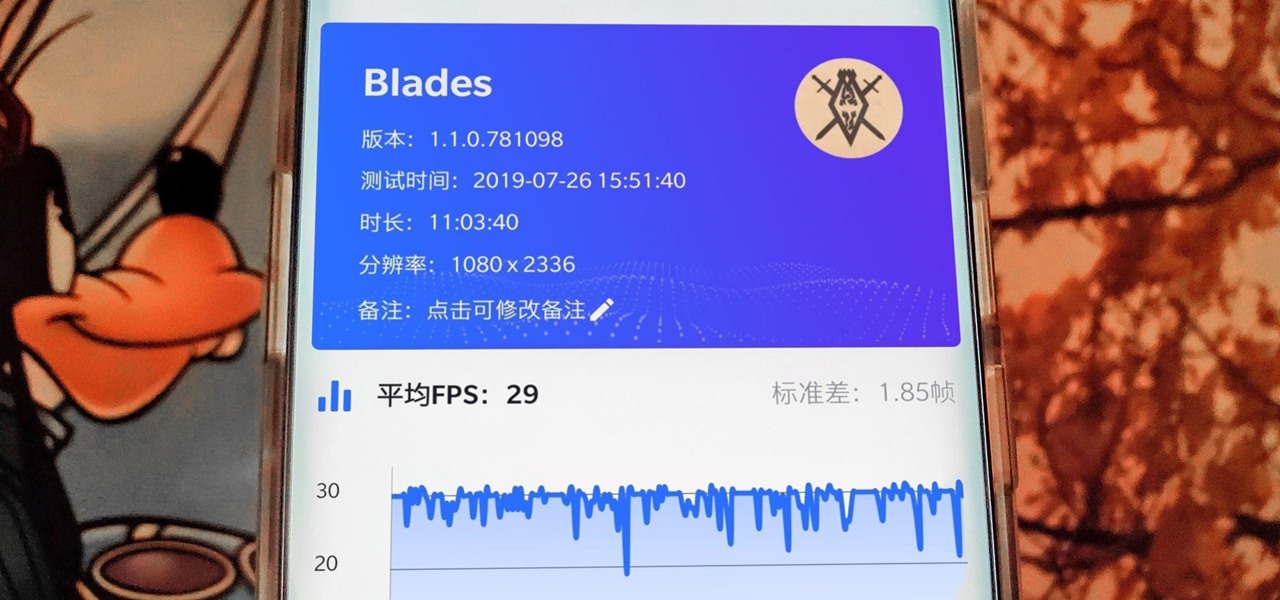
When you're gaming on your Android phone, does it sometimes feel "slow" and you can't figure out why? That means a drop in performance, which is when the frame rate dips, causing some noticeable stutters and lag. There's not really a way to know what's wrong unless you made the game yourself. But on the bright side, you can check any game's FPS with a simple tool.

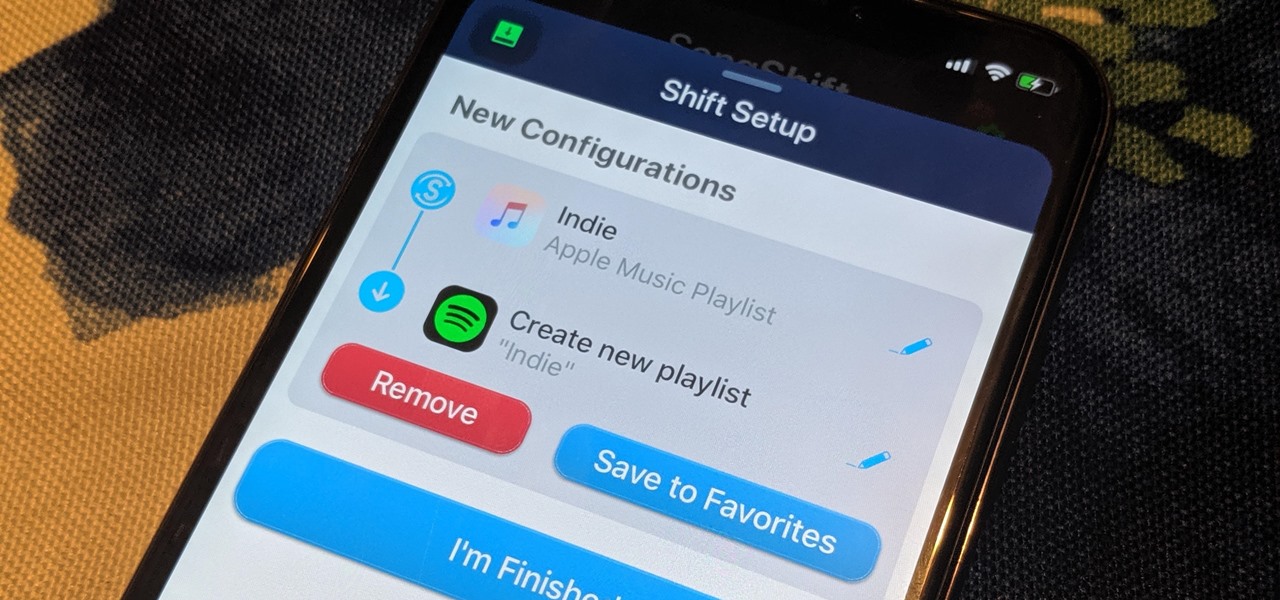
Switching from one popular music streaming service to another shouldn't have to be a hassle, but it is if you want to transfer all your favorite music over. No popular service offers a built-in feature to export or import playlists, so if you want to move your favorite Apple Music playlists over to Spotify, you'll have to use a third-party service.

Many popular apps automatically share your personal data. While I have accepted a certain amount of data collection from Google, to know companies such as Facebook perform this without my consent bothers me. After some researching, I've found a great solution, and it doesn't require root.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.

While Microsoft dominated the augmented reality news at this year's Mobile World Congress, a small AR startup we've covered in the past arrived in Barcelona, Spain, to unveil the next phase of its mission.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Switching phones has never been easier. Google backs up most of your app data on the cloud, which can then be restored onto your new phone. Sadly, Signal doesn't use this feature since it could compromise your security. Instead, Signal stores encrypted backups locally, requiring a bit of work to restore these messages.

Open TikTok, and you might find yourself spending hours watching video after video. While each video is usually pretty short, it's highly possible to binge-watch hundreds at a time. It's even more fun to create your own. But as a parent, you may not want your children falling into this same trap, and it's easy to limit how much time they spend watching TikTok videos on their iPhone.

In a way, Twitter is the town square of our era, where people can share and discuss ideas on a wide variety of topics. While the tech giant has its own app for Android, it's pretty bare-bones when it comes to features. This has paved the way for third-party clients that are rich with customization options.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

You can never replace the skills and expertise of a professional graphic designer, but Canva comes pretty damn close. It's ridiculously easy to use the drag-and-drop design tool for both professionals and people like me who don't have the need (or knowledge required) to use more advanced graphic design software.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

As we enter the second half of 2018, rumors for the second season of flagships have started to emerge. On the Android side, this means the latest iterations of the Google Pixel, Galaxy Note, LG V series, and Huawei Mate. Thanks to FunkyHuawei and XDA, we now have some solid rumors regarding the Huawei Mate 20.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

One feature in iOS you're likely underutilizing is 3D Touch, a highly useful, unique tool for iPhones ever since it first appeared on the iPhone 6S. Apple's pressure-sensitive interactivity gives iOS an extra layer of functionality, which can be clearly seen across the entirety of your device. From the lock screen to the home screen to the apps in between, there are plenty of ways to use 3D Touch.