Lock screen security provides a means of safety when it comes to keeping others from breaking into our smartphones and snooping around on or stealing private information like documents, emails, photos, and videos.

Winterboard for iOS 7 allowed us to use some pretty great-looking themes. Circulus and Space BlueBerry are both great, but a little too "fun" for me. If you want something serious, yet appealing to the eye, then M'flat is for you.

Every day it seems like new information comes to light about how the National Security Agency creeps into our lives. Knowing that they can backdoor into our seemingly private devices is a scary thought, whether you have information to hide or not.

Just days after news spread that Snapchat could be exploited by spammers, an anonymous group of hackers have released the private information of over 4 million users of the popular photo-sharing application.

It's easy to forget sometimes that even when you're sitting in the basement playing Grand Theft Auto 5 Online that you're not really alone. Everything you say into the mic can be heard by anyone else in that same session.
It seems that Facebook doesn't take rejection lightly. After being denied for a $3 billion buyout of Snapchat, Facebook-owned Instagram has updated their popular photo-sharing service with Instagram Direct—a new feature that allows users to send private photos/videos.
When programming an Excel-file with links between sheets and assorted macros for whatever is needed you may want the file to behave as a program so that users can not access the ribbon even by double-clicking on the top bar. Protect the code from being accessed by pressing alt-F8 or alt-F11. Make sure you can run the macro show_sheets_and_ribbon () from the opening sheet before continuing to step 3

When it comes to your smartphone, you don't have to be a cheater to want a little privacy. I don't even like people playing Temple Run on my mobile because I don't want anyone beating the achievements I've been working on getting myself.

The lovely Kato of Steampunk Couture has gone hardcore. For those who prefer to exercise their imaginations a bit more, Voila! Veronique Chevalier in Gearhearts Steampunk Glamour Revue- click here should do... A recent kerfuffle unfolded on facebook's Steampunk Revolution group when a discussion was started by Steampunk R &D''s very own Austin Serkin on the subject of Kato's new foray into steampunk porn, which was, ahem, examined in detail. (Well, figuratively, not literally, since her websi...

Megaupload was one of the very first file-sharing sites I ever used. But since 2005, the beloved (and pretty gangster) Kim Dotcom, has been in a legal battle with the U.S. Justice Department over copyright infringement.

Playlists are a great way to organize and share groups of videos on YouTube. Playlists can consist of your videos, someone else's videos, or a combination of the two.

Remember TwtRoulette? TwtRoulette was an online app that turned you into a so-called Twitter spy, letting you peruse someone's own timeline feed exactly how they saw it themselves. So, if you wanted to see what tweets Ashton Kutcher was seeing in his home timeline from the 700+ people he follows, you could.

Ever been halfway to work or school and suddenly remembered you forgot to log off your computer? A lot of people are constantly logged in to email and social media accounts, so if you have a mischievous roommate or sibling, this situation could be disastrous. That's where TweetMyPC comes in—it's a free Windows application that lets you send commands to your computer just by tweeting. Image by Twittermania

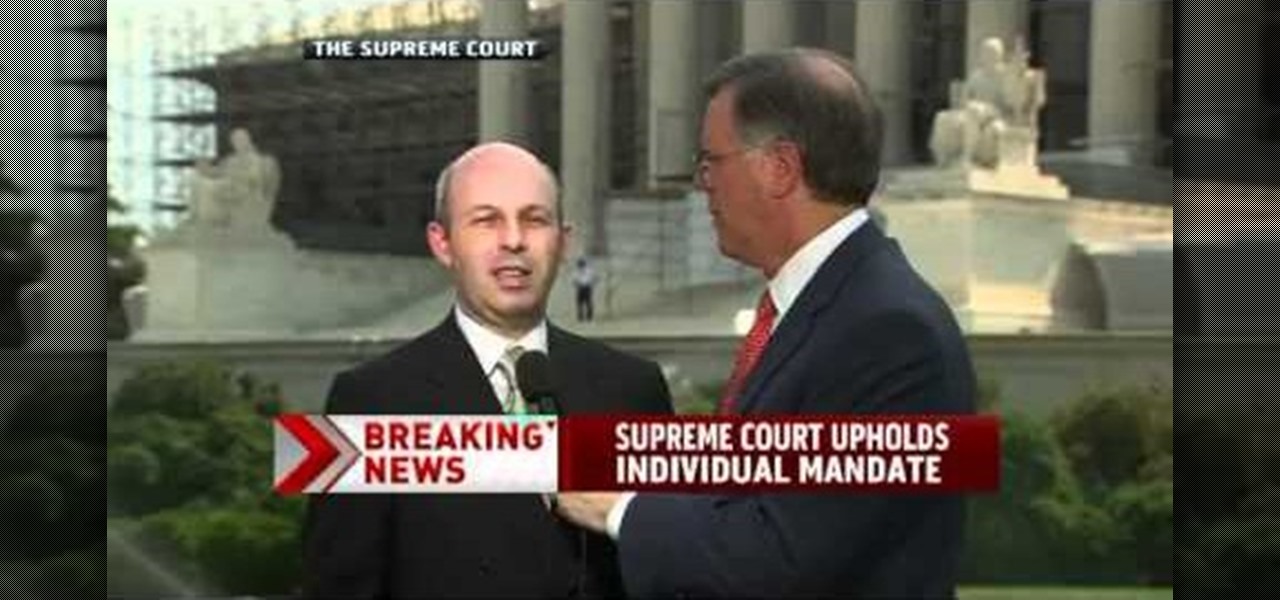
The big question this week would be the controversial Obamacare mandate. And heres the answer: Yes. Obamacare passes Congress' filters and is now an official OK. Texas college hacks drone in front of DHS — RT.

Graffiti— do you have the guts to get out there and tag some property? There's a whole lot more than just spray paint involved. To be great, you'll need things like a sketchbook, pencils, pens, markers, spray can tips, latex gloves, legal (or illegal) wall, and most importantly… creativity. If you think you’ve got what it takes to be an urban graffiti artist, follow these steps to become da ’hood’s next da Vinci.

Learn how to follow proper netiquette rules. You may be a model of decorum in person, but a bonehead online. Check out how much you know about Internet manners.

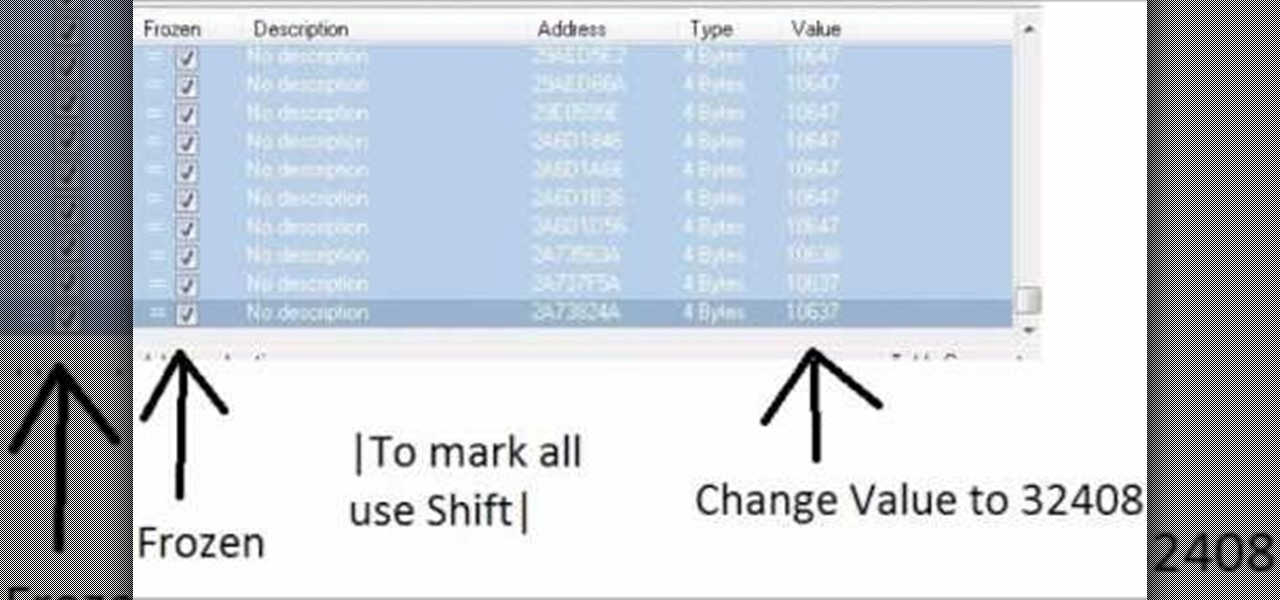
Increase your damage output in World of Warcraft! This tutorial won't work on all servers, and is better on private servers than public. All you need is Cheat Engine - buy some mundane items, and then use the program to turn them into rarer, better items.

How to summon Illidan in World of Warcraft. This only works on a private server.

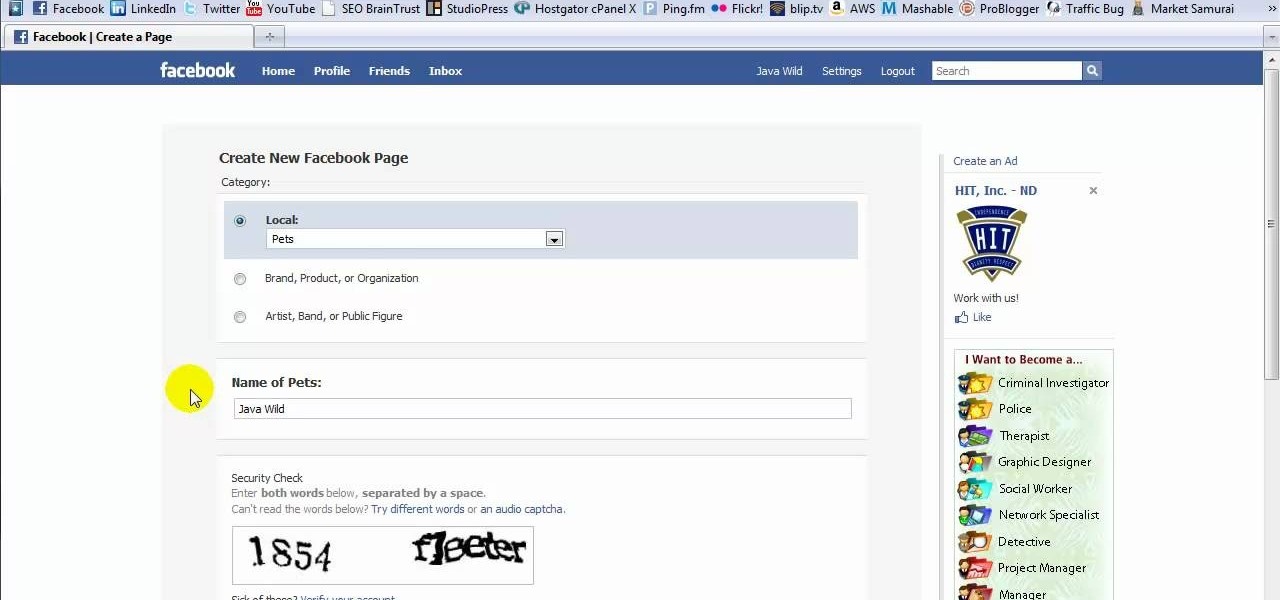
This tutorial is in response to mail to Facebook. Scott Wilde leads you through the process. You can start by creating a brand new profile page. In this case, Mr. Wilde created a profile page for his dog Java Wilde so he could have a fresh new page without having to alter his initial profile page. Fan pages are different than your base profile. Your base profile is not indexed, it is not public, it is private and limited to 5000 friends. A fan page is unlimited up to millions of fans and it c...

Is your BFF getting married? Looks like you have a bridal shower to plan! Organize a bridal bash that people will actually want to attend using these innovative ideas.

Getting angry makes you look weak, especially in an argument. Defuse your temper with these helpful tips.

Learn how to drop in on a quarter-pipe. Dropping in on a quarter-pipe or other vertical ramp is something to try after you have been skateboarding for at least a few months.

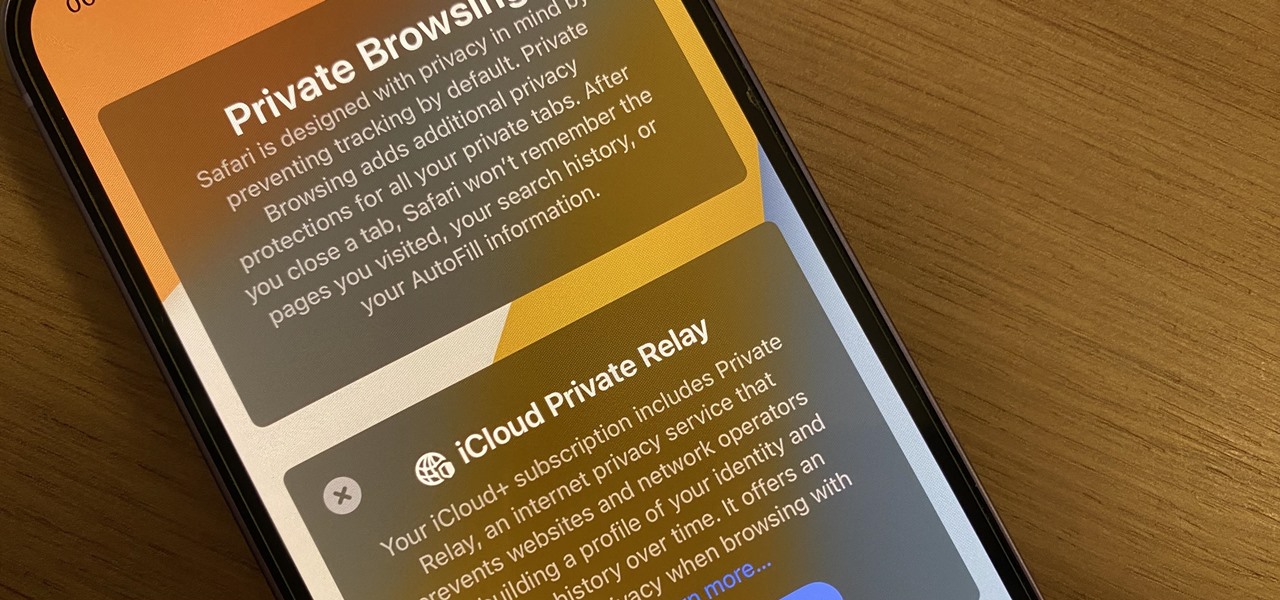
Safari's massive upgrade in Apple's latest iPhone software update includes new features you won't find in any other web browsers on iOS, from better ways to stay organized to enhanced security and further privacy protections.

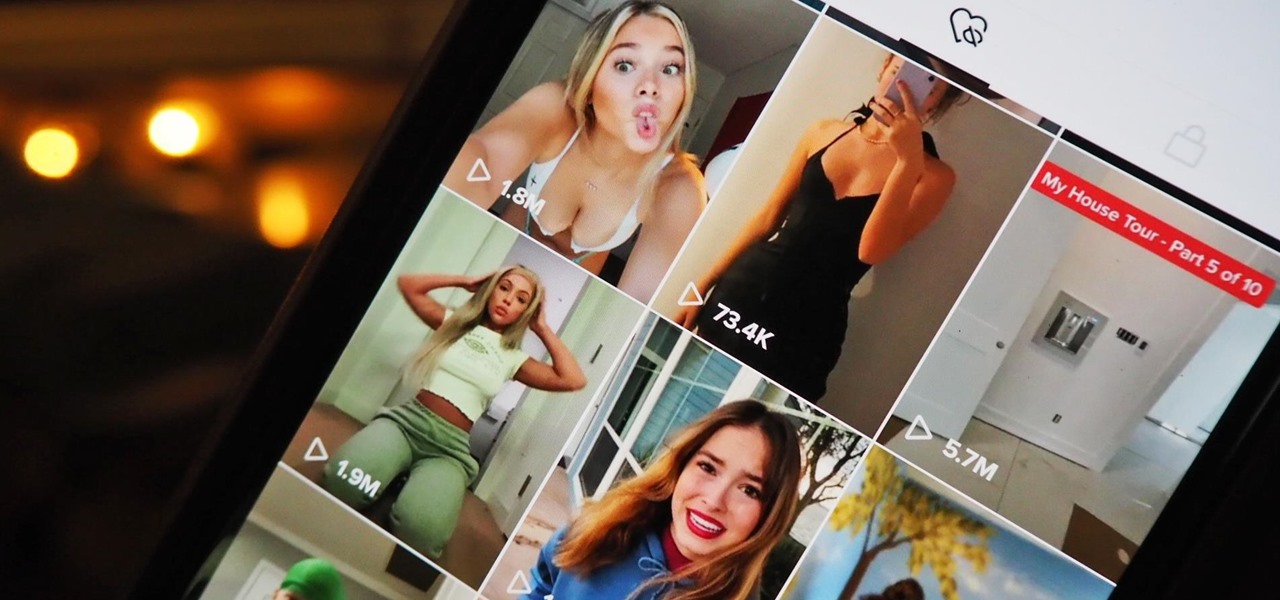
Every video you like on TikTok, whether it's a stranger performing a series of choreographed movements or a celebrity showing off their new workout, is saved to your profile. If you want to watch your liked videos at any time in the future, you can easily do so from your profile — but so can everyone else.

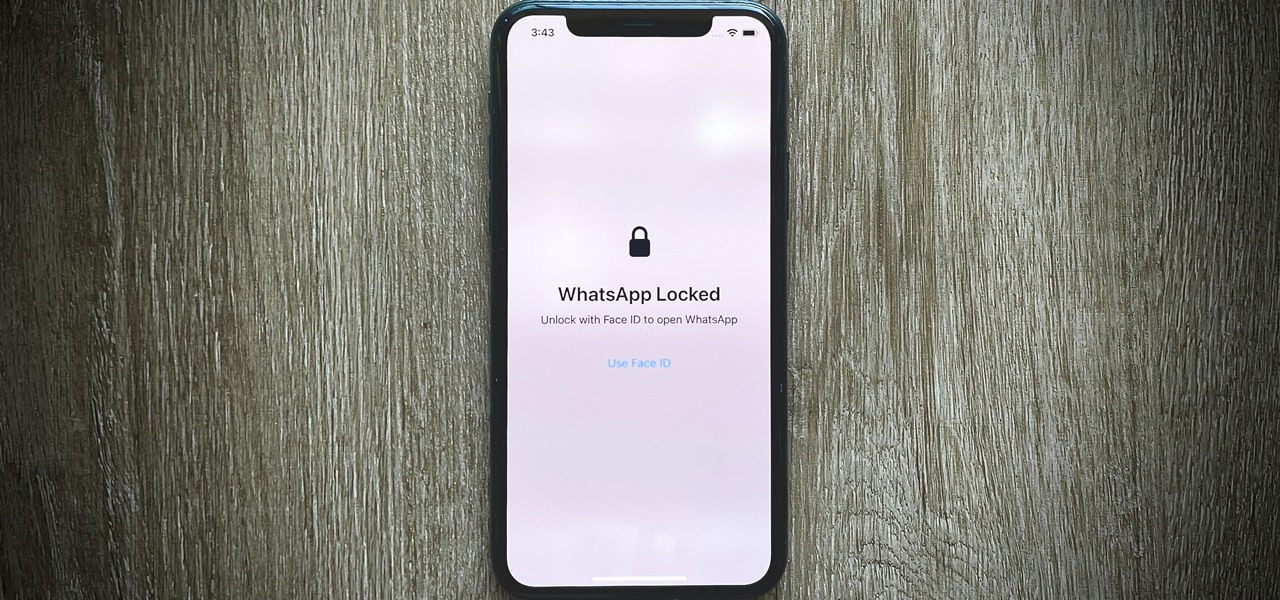
End-to-end encryption makes WhatsApp chats private and secure. However, if someone has access to your iPhone, they can easily open the app and browse through all of your personal conversations. Luckily, there's an easy way to block any would-be intruders at the gates — just lock the app behind Face ID or Touch ID.

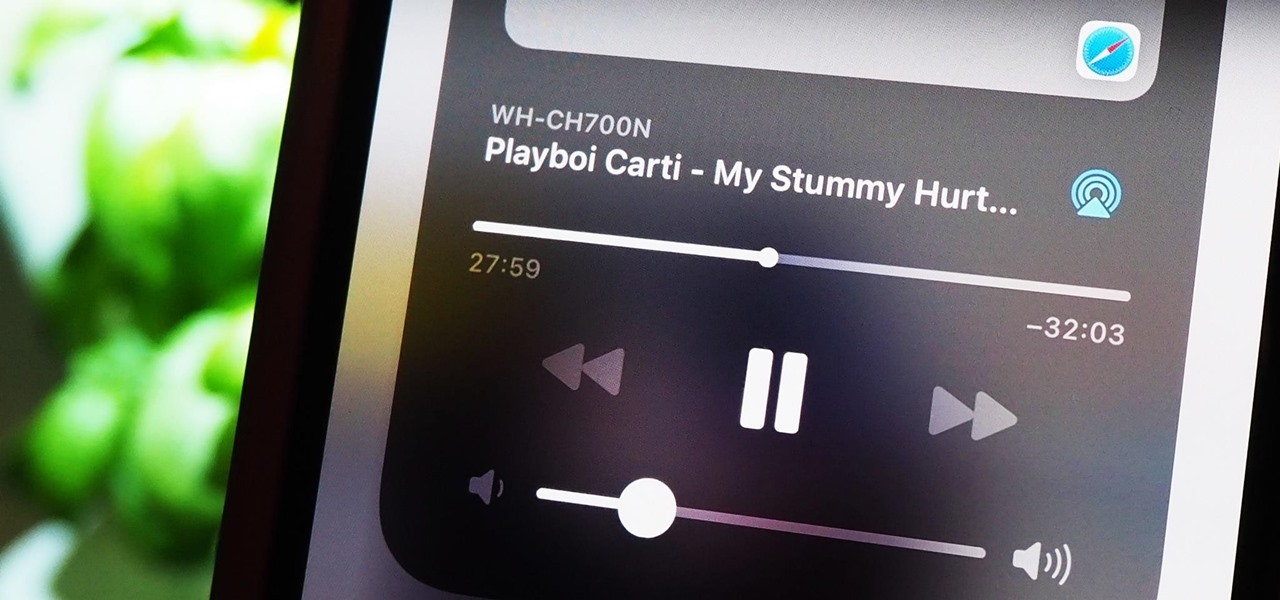
It's pretty clear with all of the annoying "Get YouTube Premium" pop-ups that litter the YouTube app that Google really wants you to pay for its Premium membership tier. That's why you'll see that "Get background play with YouTube Premium" ad after closing YouTube with a video playing — even in iOS 14 which supports Picture in Picture playback. But there are workarounds for background listening on iPhone.

Now that more people are working from home on unsecured networks and personal devices, hackers are having a field day accessing everything from private browsing histories to personal banking information. A virtual private network (VPN) is the first and most important line of defense when it comes to protecting all of your devices from digital intrusions, but not all VPNs are created equal.

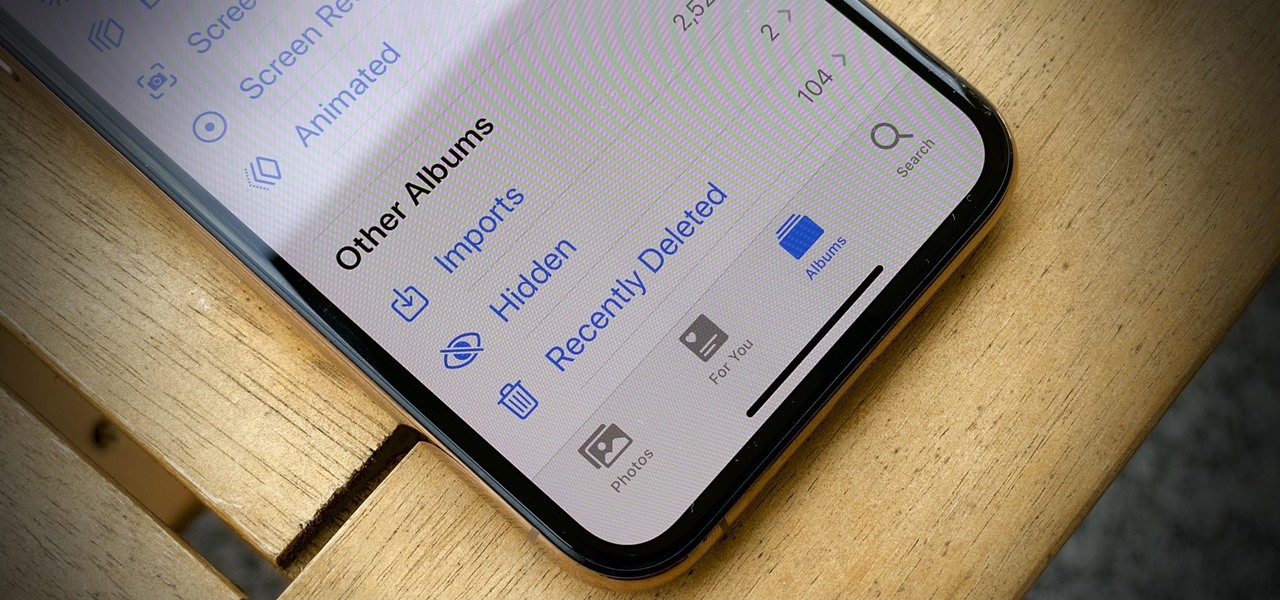
The "Hidden" album on your iPhone has always had one problem — it was never truly hidden. Since iOS 10, when the feature was introduced in the Photos app, any image or video that you conceal in the private folder could be seen by anyone with access to your unlocked device. Finally, that has changed.

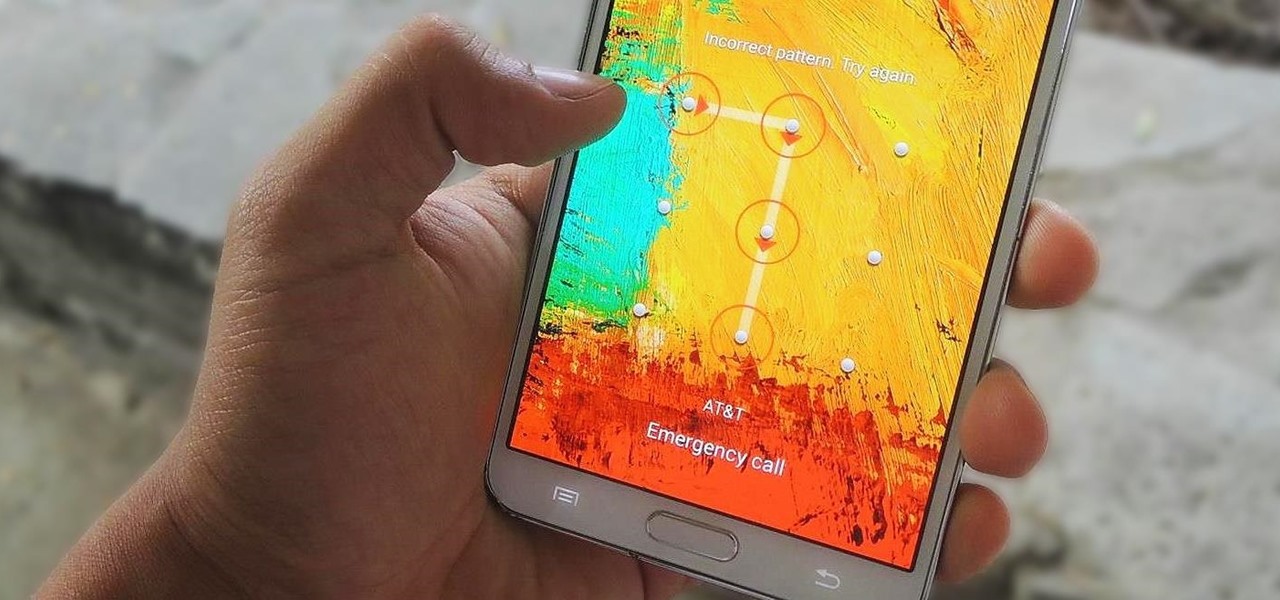
Mobile privacy is one of the most pressing security issues in existence. Since we carry our phones with us everywhere we go, we need to ensure that we're safe from prying eyes.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basically, whatever you can afford.

Throwaway phones aren't just for seedy criminals and spies—they can be useful for many everyday situations.