Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.
President Barack Obama and Afghan President Hamid Karzai signed an agreement that provides a framework for a lasting U.S. commitment to Afghanistan after the long and unpopular war comes to an end.

They may not be the coolest looking things in the world, but Google is addressing some of the shortcomings of its Glass hardware by announcing a partnership with Luxottica Group. The company, with over 5000 retail stores in the US, has a strong portfolio of brands under its belt, including Amette, Persol, Ray-Ban, and Vogue. And for this Glass Explorer, the news is welcomed with open arms. Admittedly, these bad boys have come a long way over the past couple of years, just take a look at the i...

From the Leicestershire Teenage Pregnancy Partnership, a teen-friendly PSA uses 8-bit graphics to warn kids about the perils of unsafe sex: "Game On in 2011, Use a Condom Every Time! Have Fun Stay Safe." Previously, How Kids Are Having Sex: Condom Infographic Tells All.

In this video tutorial, viewers learn how to make their information more private on My-Space. Users will need to begin by logging into their account. On your homepage, click in Account Settings and click on the Privacy tab. Under General Privacy, users are able control who sees their online status, birthday and photos. To only allow friends to view your profile, select "my friends only" from Profile Viewable by. Users are also able to block other users by age and to block specific users from ...

Nothing on the web is ever private. If you thought you can control your privacy, you were wrong. Websites may give you security options to better hide your information from the world, but ultimately your privacy resides in the hands of the website itself. We've seen how websites let ad companies track our private usage. We've seen how Facebook mucked up their privacy controls. We even saw how websites like Gawker are prone to hackers stealing user information. And now, Etsy has made what was ...

Private browsing is all the rage with browsers these days. Once you go into private browsing mode, you can traverse the internet without leaving a trail. Your history? Deleted. Your cookies? Destroyed. Your bookmarks and non-private history? Preserved for when you come back to the surface.

Black Ops gamers— you have new Call of Duty maps for your multiplayer adventures. If you have no idea what I'm talking about— you might as well just sell that copy of Black Ops and pick up the newest version of Harry Potter you can find, because you're no Black Ops soldier.

Today's guide is on creating a password protected folder on Windows 7 without any additional software. Yes, you heard that right. No extra software at all! This guide is intended for beginners. But please note, this method should not be used to store financial or otherwise highly confidential material. It might be a good place to hide a planning document for a family member's birthday party or similar occasion where you need to keep something secret temporarily.

Today I will show you how to create a simple keylogger in Visual C# Sharp, which will start up hidden from view, and record anything the user types on the keybord, then save it into a text file. Great if you share a PC and want to track what someone else is writing.
A 12-year-old Minnesota girl was reduced to tears while school officials and a police officer rummaged through her private Facebook postings after forcing her to surrender her password, an ACLU lawsuit alleges.

Since Angry Birds is apparently an "indie game", here's an interesting tidbit. Changsa, China's Window of the World theme park recently added an especially zeitgeisty activity to their collection of diverse attractions: a real-life Angry Birds game, which allows participants to catapult Angry Bird "balls" at targets using an actual slingshot.

Has the new season of Jersey Shore brought out your inner hooligan? Or better yet... does the anticipation of the new Jackass 3D movie have you itching to debase and humiliate your best pals? Fortunately, it's just about time to head back to school. And if you have a roommate, well....we pity him/her.

Mikeyssmail and ALLFREECROCHET are now in video partnership. You will see some videos being presented on behalf of ALLFREECROCHET with me being the instructor. You can find all free crochet stuff at their website http://www.allfreecrochet.com Their website lives up to their reputation. I am totally excited about this opportunity. You will start seeing videos uploading as early as tonight on my You Tube. My videos are already available on their You Tube Space. This is a brand new venture for t...

For those of you familiar with our "The Very Important Dudes & Dudettes in Film History Show" video series (hosted by Matthew Price of the MAMO podcast) you'll be pleased to hear that MAMO & thesubstream.com have teamed up to bring you a more in-depth discussion about our favourite filmmakers every month, straight to your ear-holes!

The Obama administration has given the Department of Homeland Security powers to prioritize government communications over privately owned telephone and Internet systems in emergencies. DHS emergency power extended, including control of private telecom systems - Washington Times.

Last time, we looked at archaic cryptography, so you should have a basic understanding of some of the concepts and terminology you'll need. Now, we'll discuss one of the most important advances in computer security in the 20th century—public key cryptography.

A random article from India claims that Johnny Depp is actually more a funderwhacker than just as Alice in Wonderland's Mad Hatter.

If you've recently noticed that you're missing Quick Settings toggles on on your Samsung Galaxy S6 or S6 Edge—specifically ones for Mobile data, Private mode, and Mobile hotspot—you aren't alone.

When you really think about it, registering for any website is a little scary. Not only do they now have your name, email address, and a username/password combination you might've used elsewhere, but certain sites and services ask for quite a bit more private information. From phone numbers to addresses to birth dates and more, that company now has all of your information stored.

Use the following Gourmandia napkin folding secrets to impress and surprise your guests at private parties, restaurants, weddings and date dining. Learn how to fold a napkin like a peacock. Fold a napkin like a peacock (Pliage paon).

You never know when you may lose your BlackBerry and expose all your personal information to whoever finds it. That's okay, protect private data on your mobile PDA by setting a password. Now you don't have to worry about strangers stealing your secrets anymore. Set a password for your BlackBerry Bold.

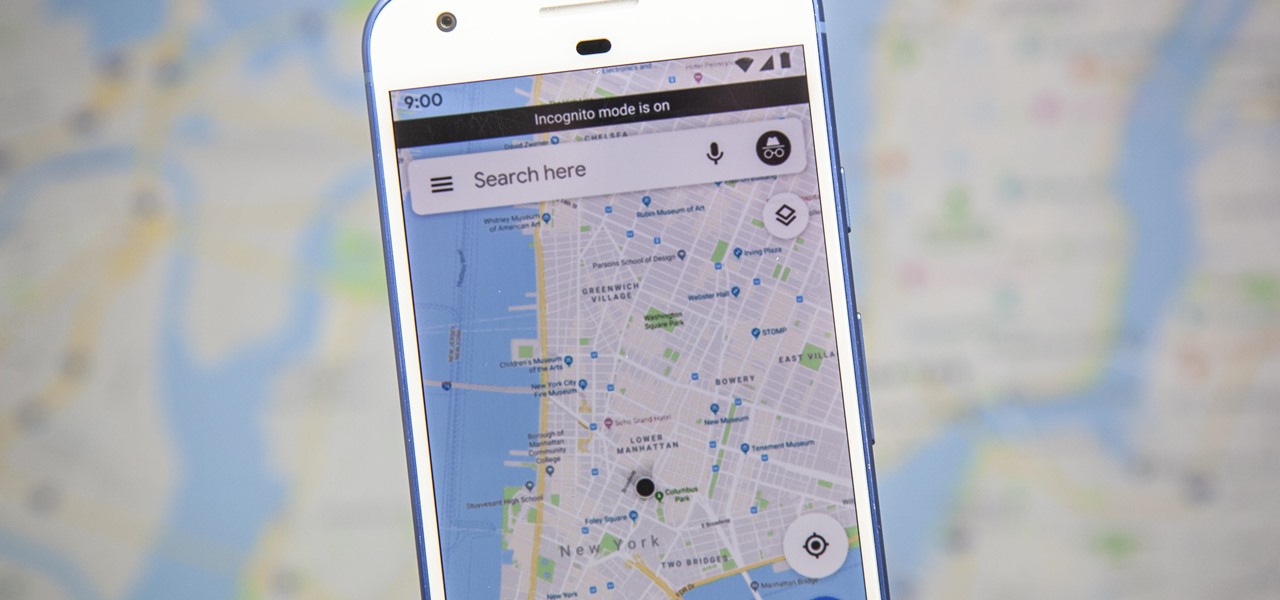
Google just recently added an incognito mode feature to Google Maps for iPhone and Android. With that, you can now use Maps in private at any time, which means you can browse and search with peace of mind.

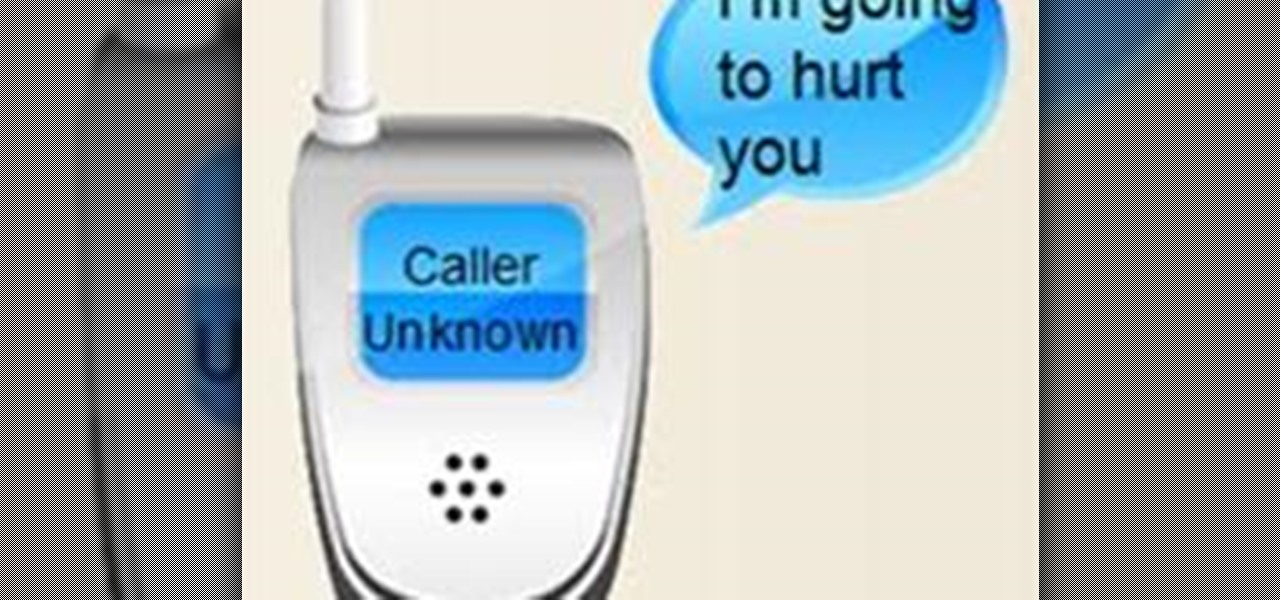
Prank Calls, Masked NumbersWho is calling your phone or your child's? Pranksters use a lot of tricks to make sure they can get on your nerves. Being able to trace prank calls is important because you're not going to learn much from your Caller ID, since most prank callers use an unlisted number - such as, a cell phone number. Many also use special code *67 to mask the number so your Caller ID will show "Blocked Number" or "Private Number". There are a lot of mild cases of so-called phone bull...

Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program.

It's great to see proof that Google+ is listening to feedback from their users. As a result of the discussion surrounding gender and privacy, Google+ Profiles Product Manager +Frances Haugen announced that Google+ will allow users to hide their genders on their profile.

Instead of watching one of the most cliché-ridden war movies of our generation (modelled after Spielberg's Saving Private Ryan), why not watch a really, really well-made documentary about the Oka crisis of 1990? Huh?

Some really good tips in here, like using "private sale" sites or booking your flights on Tuesday.

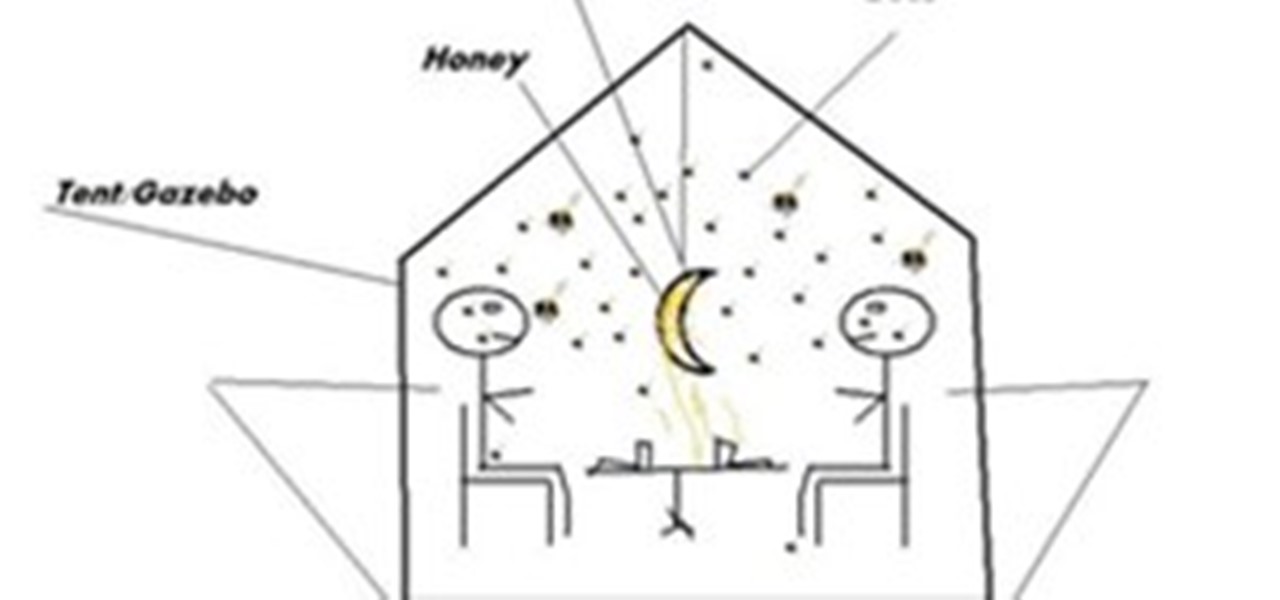
Spend all day together, laugh together, go on bike rides, go to the zoo, orgo on a romantic Honey Moon, all expenses paid.Set up your private location in a tent, gazebo, or a giant glass cube, anywhere completelysecluded, set up your table, two chairs, maybe some romantic musicpossibly a candle, whichever you desire, hang a fake moon in the middlelather it with sweet sweet honey, then add the last ingredient, see how long your lover can lastwhen the bees are added, this tests true commitment....

Would you glue fly legs to your eyelids? More or less stomach churning than gluing your eyelids to your...eyelids? (Shudder.)

Check out K 59 if you get a chance. North of El Zonte and Sunzal, it's a wave you want to check out.

BBC captured jaw-dropping HD super slow motion footage of surfer Dylan Longbottom in a 12 foot monster barrel.

The menstrual cycle can be very stressful and painful for women at times. This video will show you how to relieve menstrual pains using massage techniques. You will need to find a quiet, private area to do this. Massage away menstrual pain.
Step 1: New User for Android System in Galaxy Note 2..Need Advice for How to Protect My Privacy

Whether you are part time or full time as an entertainer, anyone can use help in marketing or advertising. Below are a few suggestions for helping get your name out as an entertainer in your area. For a more detailed list, be sure to check out www.BalloonLibrary.com where you can find an eBook on market domination and restaurant entertainment as well.

Oscar the cat is one lucky feline. After losing his two hind legs in a combine harvester, his loving owners had Oscar outfitted with two prosthetic paws, or metallic pegs to be more specific. This revolutionary veterinary procedure is nothing to scoff at - biomedical engineering experts and a neuro-orthopedic surgeon were both called in to create the world's first bionic cat. Via BBC:

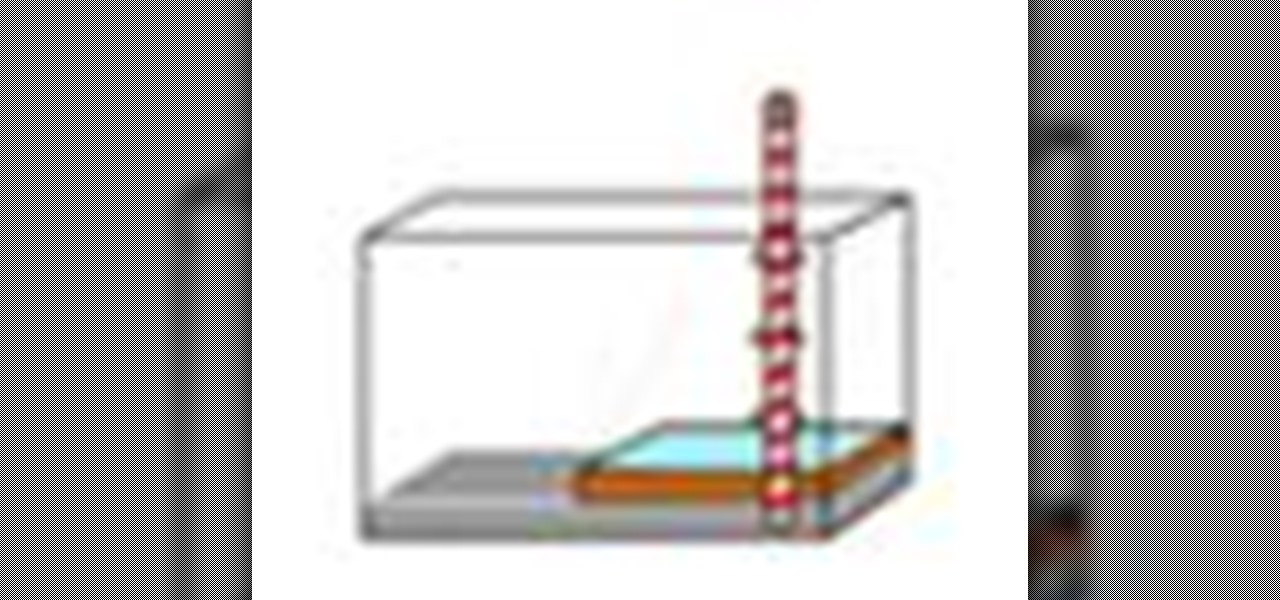
Many communities obtain their drinking water from underground sources called aquifers. If a surface water source, such as a river, is not available, water companies will drill wells into the soil and rock to a water source below. Some homes have their own private wells and must tap into the same ground water sources. In this video tutorial, you'll what aquifers are, how they work, why they are important and, of course, how to build your own model! Build your own aquifer.

Google announced that they are selling Motorola to Lenovo for $2.91 billion, seemingly marking the end of their partnership that began 19 months ago.

The team behind the Pwn Plug, a little white box that can plug into any network and access it remotely, is at it again. This time, Pwnie Express is working for DARPA to create a hacking machine that looks like a power strip, cleverly called the Power Pwn. The device has wireless, ethernet and Bluetooth capabilities and can do a full-scale penetration test as well as bypass NAC and other security measures automatically. It has three modes: Evil AP, stealth mode and passive recon. In stealth mo...

Incredible. A company called Berry Plastics (in partnership with the U.S. Army Corps of Engineers) has developed a working bomb proof wallpaper. The technology has the ability to protect against both natural disasters and warfare.