Social networks like Facebook and Google+ are great for staying connected with family, friends and coworkers—even fans. But sharing and communicating with practically anyone in the digital realm has alienated us from most of the flesh-and-blood beings we see everyday—our neighbors. How well do you know your neighbors?

I'm not going to lie. I was Catholic. But one of my reasons for my faithful departure was having to tell my innermost secrets— my sins— to a silhouetted figure behind a latticed screen. With the creepy enclosed booth structure and separation of sinner and confessor, its anonymity was clear, yet deceiving. You always knew the priest and he always knew you. If I wanted total privacy, was there really a need for this intermediary to God?

+Nik Cubrilovic discovered last week that Facebook could track your web activities even after you logged out of your Facebook account. After some blatant denials from Facebook spokespeople, Facebook decided to fix the logout issue, but not before +Michael Arrington, on his new Uncrunched blog, made a concise post revealing Facebook's dishonesty: Facebook submitted a patent application for "tracking information about the activities of users of a social networking system while on another domain...

With give or take 250 million cars in America, odds are most city dwellers waste time hunting for parking spots. And while a smartphone app can't make free parking spots magically appear, it can aid in the searching process.

Without Richard Channing Garfield the world would be a much grayer and less interesting place today, at least for all of us. He created Magic in college, playtested it throughout, accidentally found a publisher for it, and wound up the the most well-known and successful paper game designer in the world (sorry Guygax, make something new why don't ya?). He does not seek the limelight, has not had a snappy biography written about him (or his game, amazingly enough) and I thought we should pay a ...

Describe this movie in one word? Hilarious! Could you watch this movie again? Without a doubt!

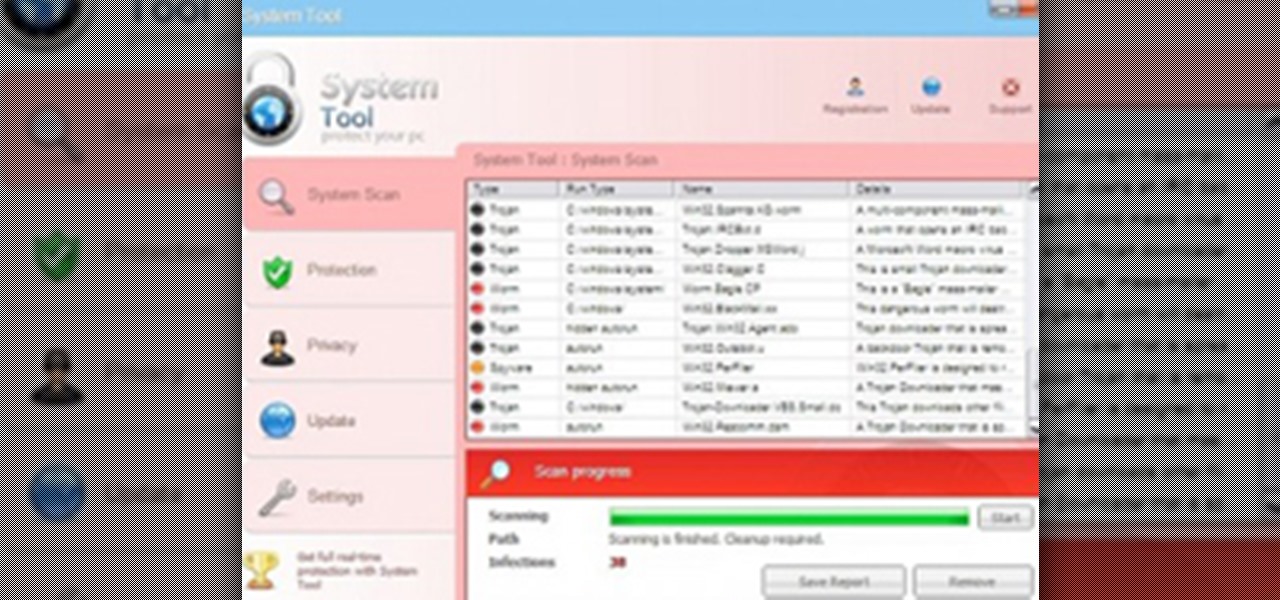
System Tool. It sounds like something your Windows computer might need, but it's the exact opposite.

As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.

The dreaded moment you hope never happens—someone has stolen your laptop. You could have private information, pictures, or even private information belonging to the company you work for, all lost forever. It can cause you pain, money, or even a job.

Learn how to play the improve game "Quirks" at your next party in this free video that will keep your party guests entertained and thinking on their feet.

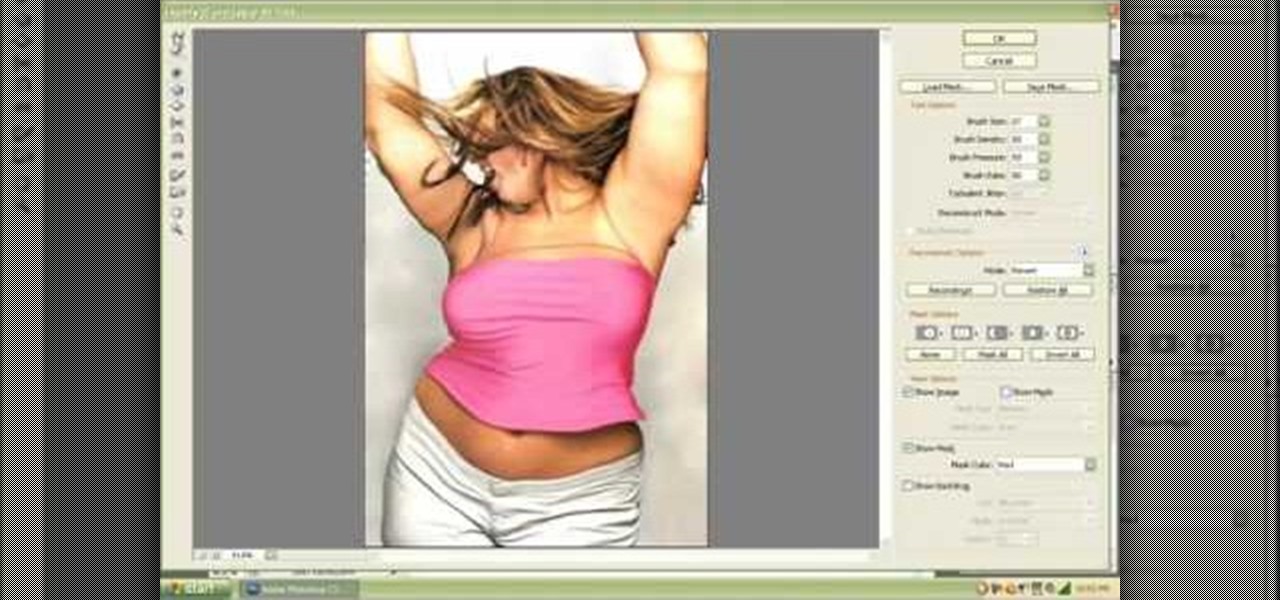
Want to know how to remove a digital tag from a garment for (in this case) a pair of shoes? This clip will teach you what you need to know. Whether you're new to Adobe's popular raster graphics editing software or a seasoned professional just looking to better acquaint yourself with the program and its various features and filters, you're sure to be well served by this video tutorial. For more information, including detailed, step-by-step instructions, watch this free video guide.

I recently posted a link to what seemed to be a very useful guide on Lifehacker for creating a TOR button in Chrome. However, when I tried it myself, it did not work. Also, it lacked a warning on the limits of Tor, which I think are important. Therefore, I decided to create an updated and more comprehensive tutorial.

Introduction I will not go into some time-waster of a story about how I came to build this app. It was a prerequisite in a bigger project I am still tinkering with from time to time.

Skype is a great service. It allows a free solution for VoIP to VoIP calls, and cheap VoIP to landline calling. However, a very disturbing, little known fact that might push you away from Skype does exist. If you closely read the terms of service agreement, it clearly says that Skype is allowed to decrypt your messages whenever they please. Here at Null Byte, we tend to enjoy our anonymity, don't we?

The lack of a search function within Google+ is driving me crazy. It takes me way too much time to find the posts I want to save and refer back to, and it's counter-productive for Google to launch their social networking product without an integrated search.

We're ending the week with a lot of big announcements and updates. To date, Google+ has updated its name policy, but is still forbidding pseudonyms. Blocking people on Google+ became even easier, and yesterday, games on Google+ launched.

Do you know how you are perceived by your peers? In real life and online? In the physical world, you could be seen as intelligent, thoughtful and hard-working, but on the Web you could be looked at as irrational, selfish and slothful. There's just something about the Internet that takes away a person's judgement and replaces it with impulsiveness—especially when it comes to Facebook.

I loved The Amazing Adventures of Kavalier and Clay for so many reasons. For its fantastical sense of adventure, set against the real world action and tragedy of the Jews in Europe during World War Two. I loved the opening chapters of Josef in Prague – a city I spent several months in a few years ago and one of the most beautiful places I’ve been. Reading scenes set in Prague and descriptions of places I’ve seen made the story that much more personal for me.
LAKE JACKSON, Texas – 2012 Republican Presidential candidate Ron Paul was endorsed today by the Hon. Jordan Mason, City Councilman, Ward 4 of Rapid City, South Dakota.
In a riveting interview on TruNews Radio, Wednesday, private investigator Doug Hagmann said high-level, reliable sources told him the U.S. Department of Homeland Security (DHS) is preparing for “massive civil war” in America.

SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and encrypted connection. This is handy for a multitude of reasons.

The battle to be the video editor for your iPhone continues with the debut today of Cinefy at CES. An app that promises to bring 'Hollywood-style' visual and audio effects to your phone, Cinefy comes loaded with over 50 effects to add to your movies as well as a library of copyright cleared songs.

Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic function. The encryption header stores the password that you have entered for the archive, which allows the data to be reversed and read from. Encrypted data is safe from anyone who wants to read it, other than people with the ...

OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.

Web-spying technologies like FaceNiff, Firesheep and Newstweek are out there showing the world just how easy it is to see what you're doing online, but they're amateurish in comparison to what real hackers could do to you if they catch you browsing unsecured websites.

+Tom Anderson of MySpace has been very active on Google+ over the first week, and he's not shy with his thoughts on the evolution of the industry he once owned. Here's his take on this morning's Facebook announcement and Mark Zuckerberg's response when asked about Google+.

Inspired by the beauty of traditional signage printed on doors and buildings, Rero is a French graffiti artist who makes a simple, yet heavy mark. Using the universally common Verdena typeface, Rero brands abandoned public spaces in extreme disarray with his own codified messages based on theories of public use of imagery and private property.

Every key on a telephone keypad has its own sonic signature, a sort of calling card composed of two distinct tones: one high, one low. While it's easy to tell the difference between the individual pitches in a single row—see, for example, this article on using your cell phone as a musical instrument—, it's often difficult to differentiate between notes within the same column. Unless, of course, you outsource the work to a computer! Which is what Uruguayan hacker [Charlie X-Ray] recently set o...

In the picture for this post you can see a grab of David Kassan's DVD sales page. The reason it is there, is if you really want to be the best, you should know how to draw. I suggest buying this DVD and anything from David Kassan, Jeremy Lipking or Tony Pro. If you want to learn, why not learn form the best?

Professor Wafaa Bilal of New York University plans to soon undergo a surgical procedure that would temporarily implant a camera in the back of his head. The project is being commissioned for an art exhibit at a new museum in Qatar. The Iraqi photographer will be a living, breathing cyborg for an entire year, during which the implanted camera will take still photos every minute, simultaneously feeding the images to monitors at the museum.

Relax, it's not as messy as it sounds. Pee-on-a-stick, at home STD tests may be available in UK pharmacies soon, complete with an incredibly convenient app that would save you a trip to the clinic. It works like this: if you suspect you may have an STD, you would pee on a device which is then inserted into your mobile phone. The app then "diagnoses" your sample and returns results.

FOXBORO, Mass. - The New England Patriots Alumni Club (NEPAC), announced that more than a dozen former Patriots players are gearing up to host a "Football for You" youth clinic in Worcester on Saturday, May 29 from 12:30-5:00 p.m.

Co-Directed by WonderHowTo's Ford Austin. Do any of those actors look familiar? If you like it vote for it here

These are great times. It is about time advertisers invaded our video games in the same way they do our driving (billboards), walking (fliyers, posters), and our private home (emails, bulk mail, text messages).
Cheating ruins everything. Cheating makes game play unfair for others who may be truly competitive and strategic. Cheating makes others disrespect and un-friend you. There can be unforeseen consequences, like getting viruses, trojans or your account hacked from downloading a cheat/bot program. And you will get banned from the game for violating terms of service.

Whoever said crime doesn't pay? Norway's luxury Halden prison may very well be nicer than your home.

What more is there to say about the almighty Conrad Schnitzler? One of the original founders of Tangerine Dream and Kluster (later Cluster), his contributions to the world of German experimental electronic music have been enormous. With album, cassette, and cd releases miles long, his discography would take a lifetime and a pretty penny to catch up to. 'Conrad and Sohn' is a pretty unique release, even for Schnitzler. The album was a private press release that he did with his son in 1981. App...

Bikini vs. The Wave I have always been a fan of the bikini, but it hasn't always loved me back.

Today's WSJ takes a tour of Russian billionaire Andrey Melnichenko's 394-foot insanely luxe yacht, coined "A".