If you're a frequenter of Null Byte, I bet you have at least some interest in information security. Furthermore, you have a hobby that if applied in certain ways, will get you arrested. I've received quite a few messages from the community here about federal cybercrime law and how it applies to them, so I decided to get together with my lawyer to come up with some answers.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Are you the expert hacker we're looking for? Do you have a great idea for an article on Null Byte? Do you have a passion to write, and more importantly... teach?

Grab your thinking caps and get your hack on. Null Byte is officially seeking contributors on a weekly basis who are willing to take the time to educate the Null Byte community on anything, from hardware hacks to life hacks. Contributors that write tutorials will be featured on the Null Byte blog, as well as the front page of WonderHowTo (providing it's up to par, of course).

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

I'm sure we've all heard about MSN and Yahoo! Messenger, right? They can be useful, but the setup can be quite time consuming for those who need to use it just once or twice—and the privacy statements are a real bother. For example, we must provide our real details. You could use Fake Name Generator, but if you get caught, you will have your account suspended. I don't have a law degree, but to my understanding the United States recently passed legislation that gives the authorities the power ...

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

Amazingly, a lot of people I know haven't even heard of SOPA or PIPA. Now, every English-reading person with an internet connection will finally have those two four-letter acronyms emblazoned in their minds. For the entire day today, Wikipedia's English-language site will be in total blackout in protest against the proposed legislation in the United States. And that's not all. MoveOn, Reddit, BoingBoing, Mozilla, WordPress, TwitPic and other popular websites are down today in protest.

Google+ is taking over more and more of Google's core properties. This week, we've seen several announcements from Google blogs about new products, new features, new looks, new integrations. If you're like me, you actually want to know where to go for all the latest information on Google products.

Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame and "1337-ness" can get caught, I think my hacker comrades are doing something wrong.

CREMAINS n/pl the ashes of a cremated body 62 points (12 points without the bingo)

BURKITE n pl. -S a burker 63 points (13 points without the bingo)

Cross-Site Request Forgery (CSRF, pronounce "sea-surf") is a common web exploit. However, for unknown reasons it's not used very often. It plays on a given website's trust in a web browser by executing another website's form action, for example, sending money to another person. It's usually placed in abnormal places like HTML image tags.

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...

Last week, Google+ took a crucial step towards becoming exactly like Facebook. As of now, there are games available for download within the service, most notably Angry Birds, which is already available on at least one of the devices owned by everyone in America today. Some of the other popular games include Bejeweled Blitz and Zynga Poker, and out of all of the available titles, all come from four companies that have come to form the four-headed dragon of U.S. casual gaming: EA, Zynga, PopCap...

If you've gained entry into Google+, one of the first things you should do is adjust your Google account settings. Your settings will now look quite different, and you can adjust your notifications, password retrieval methods, and more. There are many settings that you may not have been aware of before.

With the Google+ team members being generous and free-flowing with advice on some of the more advanced features of Google+, we'll be publishing a weekly summary of the latest pro tips. Chances are, if you've been following the Google+ team members, you've seen some of these already but you don't have them all in one handy place.

Google+ is the most exciting new social network to come around this decade, and the only product with a chance of challenging the monopolies we know as Facebook and Twitter. As an Internet addict, I've joined every major social network there is - from Friendster (who?) to MySpace (so ugly) to LinkedIn (yawn) to Twitter (irritating) and Facebook (annoying to manage). Competition is delicious, especially between well-financed monopolies. Google+ really seems to have identified an Achille's heel...

Even with Apple's forthcoming iOS 5 updates to its default camera application, those upcoming features can't match what already exists in Global Delight's Camera Plus Pro. For $1.99, Camera Plus Pro provides users with over 100 tools for every part of the picture taking process, including video recording. It works with all versions of the iPhone, iPod touch, and iPad 2 with iOS 4.1 or the later update. Let's examine what it can do, and why you will want to replace Apple's default camera with ...

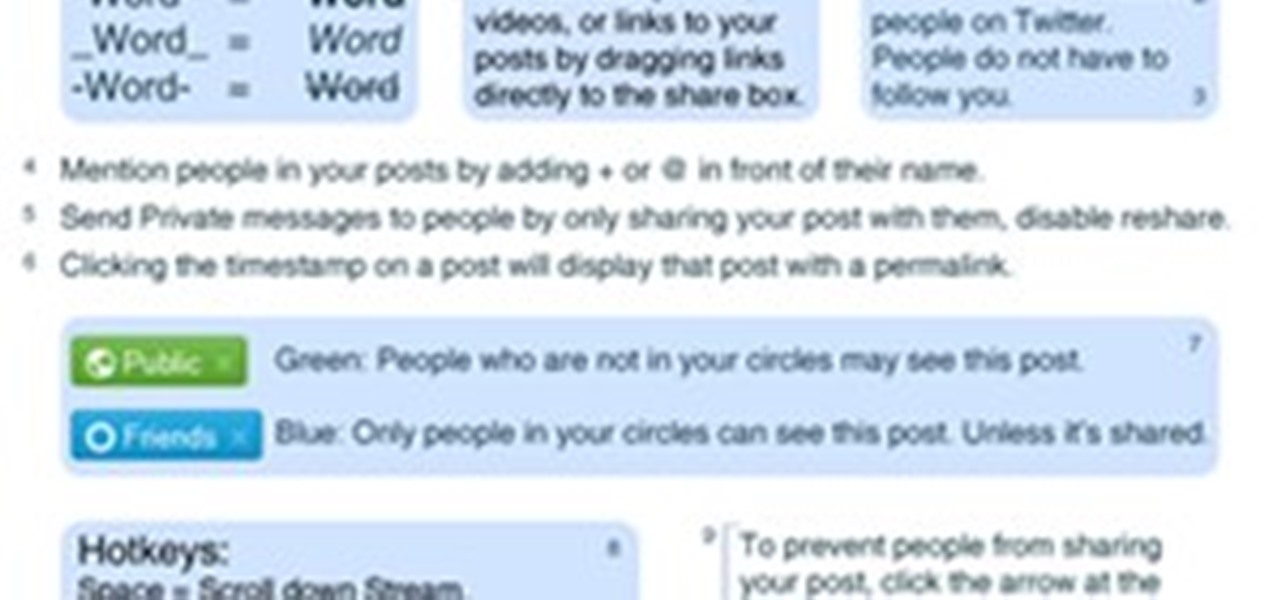
Just how private is your Facebook profile? To some extent, that's up to you. Many Facebook users share and poke their days away, never knowing about the plethora of custom privacy settings that lie just a click away. Facebook's privacy menus can look a little complicated to the newcomer, so today I'm going to give you a basic look at what lies under the hood.

Do you ever really know someone? I mean really really? Super really? Sometimes we can talk and be with people normally for years and then bam: five people dead, house on fire, dog missing. All the while people shake their heads and regret that if they had just put the little clues together all of this could have been averted.

Japanese people are into many things Americans find weird—like YouTube's beloved canine-hosted cooking show or Daito Manabe's light up LED grills or even more insane, a vending machine that distributes live crabs. In light of these cultural oddities, the Japanese phenomenon of visual novels (NVL, or bijuaru noberu), seems relatively normal. A meeting place of books and video games, visual novels are a sort of "Choose-Your-Own-Adventure" for the new generation.

It's officially the last day of the year and there's no better way to end 2010 at WonderHowTo than with our own Top 10 list.

Editing with the Canon 7d and Final Cut Pro couldn't be easier, here are some tips to help you get started.

West LA Seido Karate-do embeds its personal protection program into its on-going classes. Private instruction in this aspect of Seido can also be arranged with Kyoshi on an individual basis.
I’m seeing a flood of posts on youth football forums and even getting a few e-mails from youth football coaches complaining about “player agents” also known as parents. Most of these unhappy coaches are dealing with parents that have non-issues, have an agenda, are misinformed, don’t know much about the game of youth football or are just people that gain great pleasure from complaining. The 80/20 rule is more like 95/5 in youth football, 95 percent of the problems are caused by 5 percent of t...

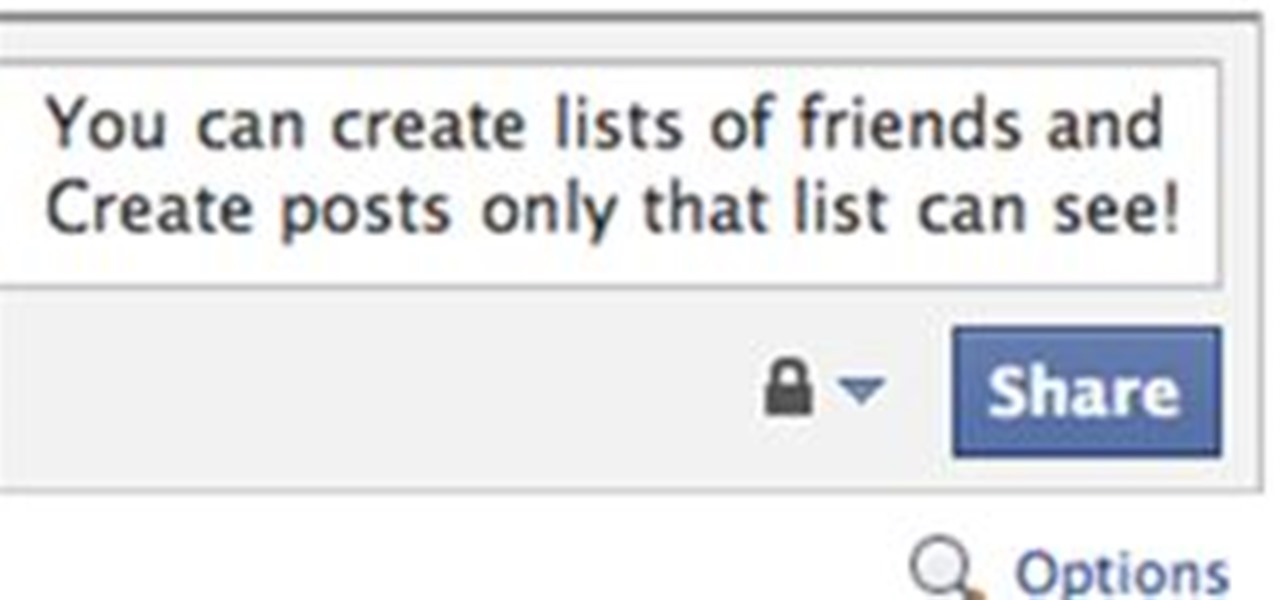
You may want to create a list of certain friends so that you can post certain status updates, photo albums, links, or application posts for just them to see. I'll show you how to set up lists

Tip If some of your friends did not get the email, find one of the 5-15 people you selected who did, ask them for the link and fix it using the steps below then share it on your feed so it can get clicked by anyone!

Good news. Facebook has finally listened. After severe criticism for ignoring the world's privacy norms, Facebook will finally release simplistic, user-friendly privacy settings soon.

This one smells like a fish story. It is not. Tuesday April 13, Dave and I got up to surf westward at 7 in the morning. First rate waves. Headache cold water....sun blocked by the cliffs. Fast, clean, beach break. 3-4 foot sets, mostly lefts. About 15 dolphins swam by. Blase blase. We always see dolphins. But then some bigass whale with barnacles breaches. We are speechless. It is about 20 feet from us. We follow it for about thirty seconds and pinch ourselves. Have-you-ever? No...

It's 1976. The hottest arcade game on the market is Blockade (or Blokade), an 8-bit maze game for 2 players. You and your opponent must move your characters around the screen in 90-degree angles, leaving a solid line behind them. Whoever runs into one of the solid lines first, loses. But soon you'll be able to play this fascinating game from the comfort of your own home—

Collision Repair Related Careers When you think of a career in collision repair you probably think of a body repair or paint technician. However, there are a lot of related careers that collision repair can lead to. For Example, you can work in auto parts stores, dealerships, insurance companies, paint representatives, trainers, etc. In this article we are going to examine a career as an auto estimator.

It was brought up a while back in a Community Call to Arms that *math* is handy for encryption (and let's face it, everything) so let us go over things you just have to know. "In its simplest meaning in mathematics and logic, an operation is an action or procedure which produces a new value from one or more input values."[source]

Creating any object you want is as simple as point and click if you have a 3D printer at home. If you don't have one handy, there are a few companies that offer printing services online. But to help services realize your design in extruded plastic, you have to make a 3D computer model for the printing machine. For beginners, the free Google SketchUp application is the best choice of software. Using only a few tool bar buttons and a scroll wheel computer mouse, you can model literally any obje...

How many of you know all the amendments of the Constitution? Do you even know how many there are?? Well, many of the people I speak to don't. And let me tell you, that's a bad thing. Knowing even the basics of the Amendments can have a profound effect in your lives. Ever got pulled over by a cop? Did you know you can deny his request to search your car (unless he sees something 'suspicious')? If you own a gun, you sure know about the Second Amendment. Here's a neat one: a public phone booth i...

For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. I can not stress that point enough.

You've probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images are accurate to a point, but most are just making things up.

SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

When you're out and about in the dangerous world of Wi-Fi, it's hard for the average computer user to stay protected, or even know what being protected entails. Little do most people know, Windows 7 has a built-in security that few people take advantage of: a VPN (Virtual Private Network) server and client.

Shadows of the Dammed (360/PS3) is a polarizing game. It's not shy of being crass and crude. Go ahead and judge the game by the following examples (click to enlarge):