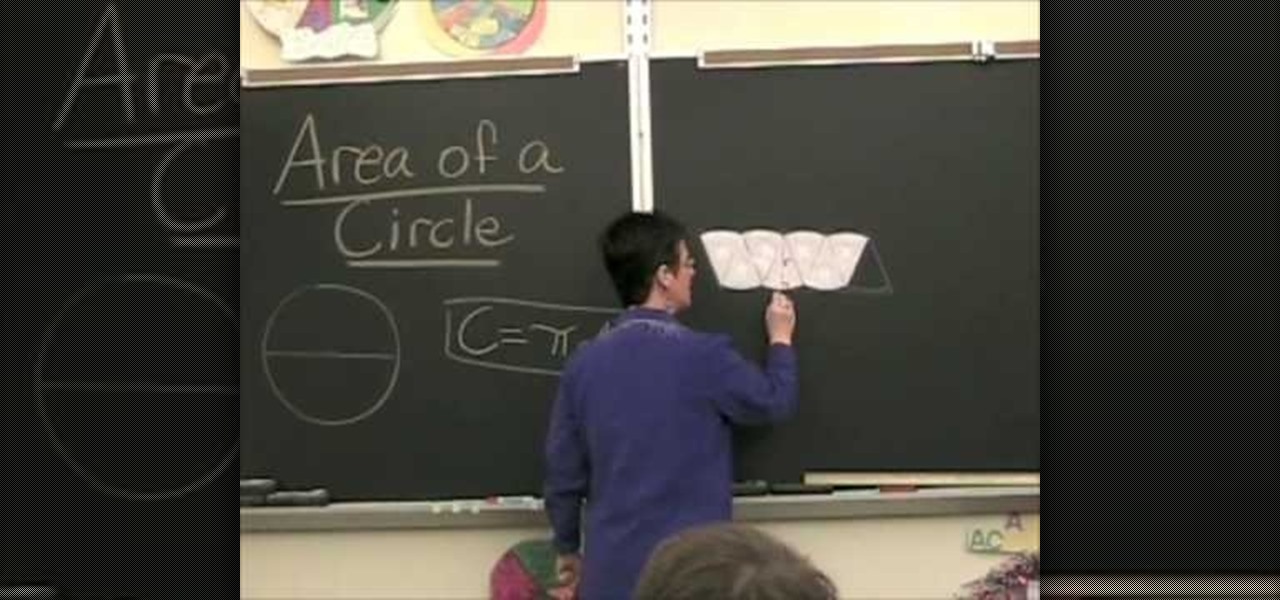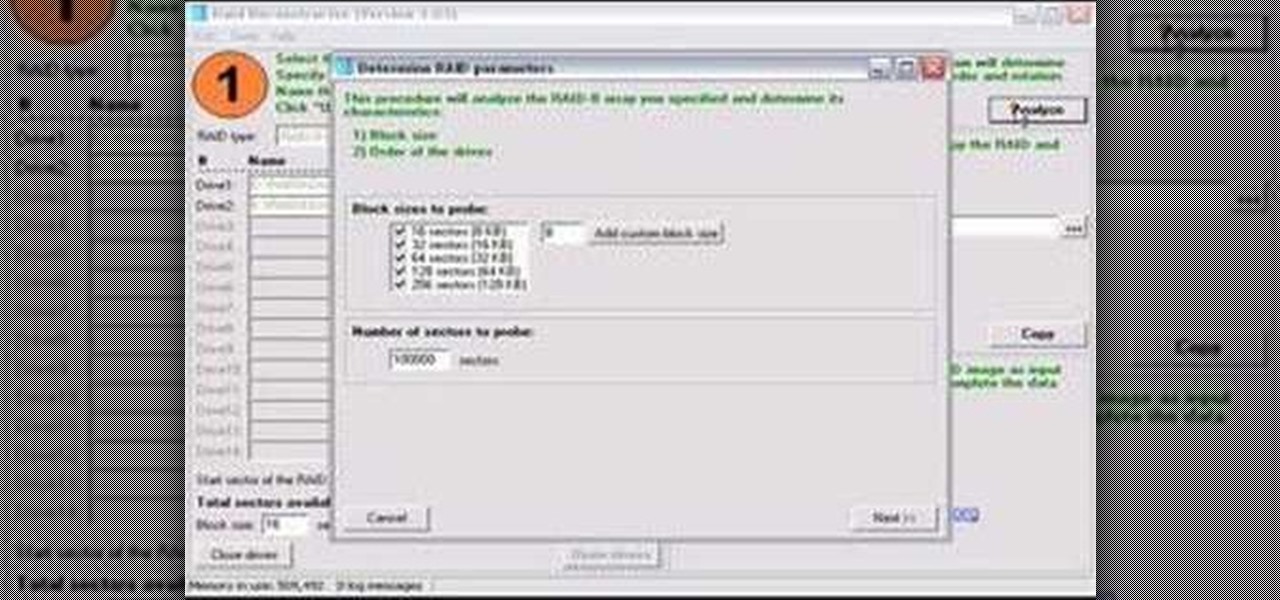
Check out this video tutorial on how to use the Runtime RAID Reconstructor software to create a destriped image with a two drive RAID 0. So, get your data back with this copy of your RAID to have recovery options for your computer. This program will collect, sector by sector.
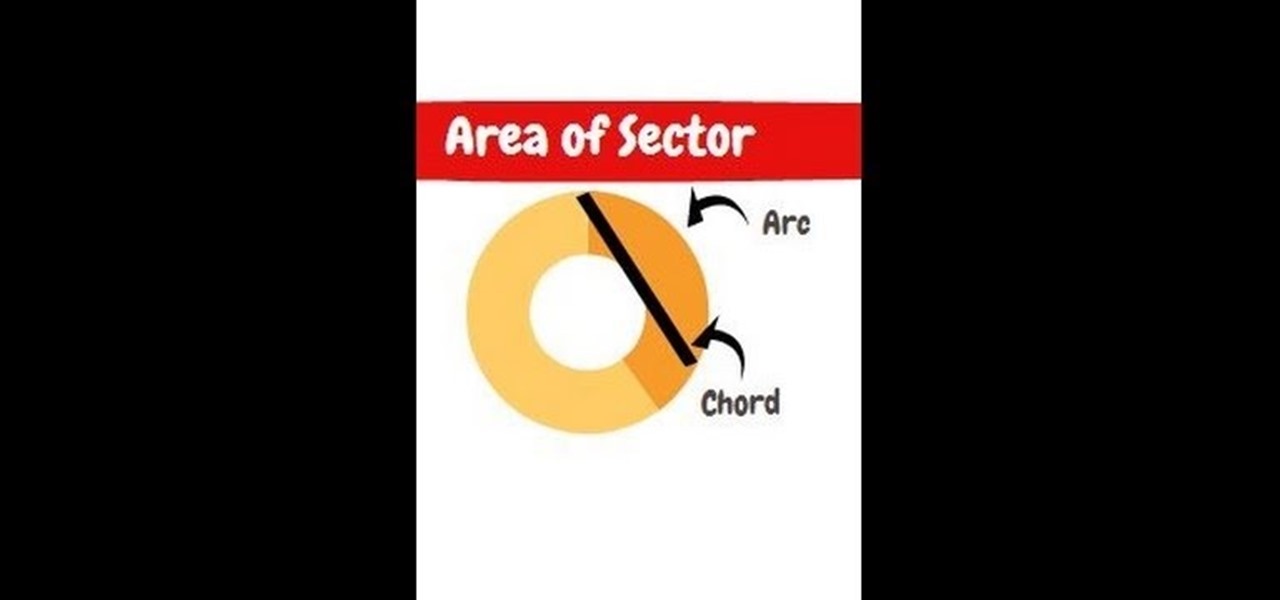
The sector area is a section of the circle. You can think of it as finding the area of a pizza slice instead of the entire pizza.
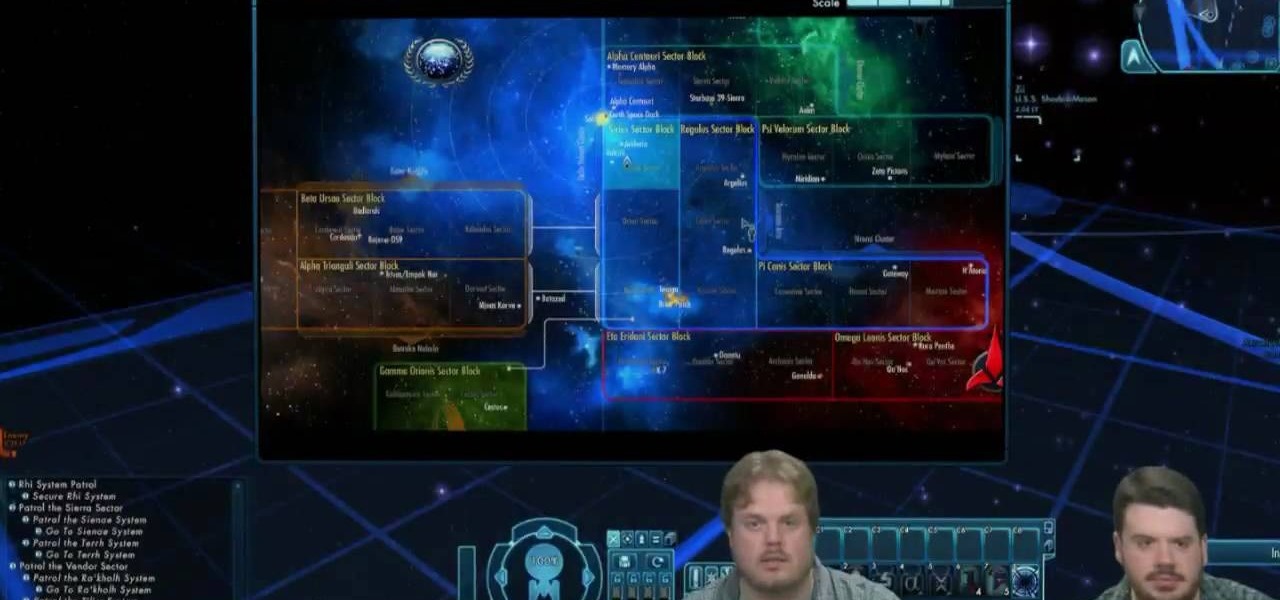
Know your way around sector space when you're playing Star Trek Online. This tutorial shows you how to interact with the sector map in the game and get to where you're trying to go, and what you might find as you travel through space.
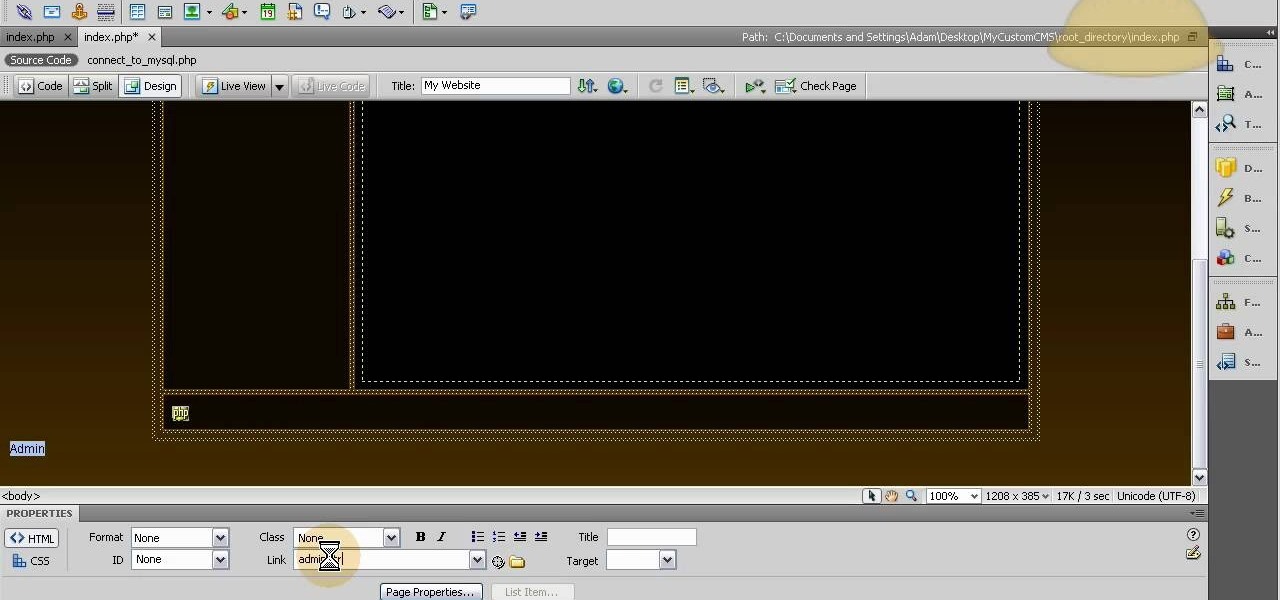
Designate a back end or administrator sector of the website, a place you can use to manage the content on the rest of the site. This tutorial shows you how to use Dreamweaver to set up this area of your website and cordon it off from the rest of your website.

A spokesperson from the Nissan and Renault Alliance told Driverless the group is testing self-driving electric "robo-vehicles" for future mobility services and is "not ruling out anything" for future services the group might offer, as the alliance widens its driverless business model to include both fleets and private sales.

Check out this six-part video lesson on shaving for men. This covers the most uncomfortable places to shave on the body. Body shaving can be sensitive, so do so with caution. Yes, you WILL learn how to shave your private parts with this video.

First of all launch the program "Nero 7". Now click on "cd" and then click on "cd-rom boot'. From the new screen choose ' image file' and then click on 'browse'.Now go to the 'drive d' and select 'windowsxp-boot image' folder and then select 'boot.ima' file. Now click on 'open'. Now click on 'advanced' and then click on 'no emulation'. Select the ‘number of loaded sectors' and increase it to '4'. Now click on 'ISO' and then make sure that all the data is same as that on the tutorial.

Watch this internet video tutorial to learn how to enable Private Browsing in Safari for Windows. This how-to video will help you use private browsing in Safari just in case there's something you want to keep private.

If you're new to the Visual Basic IDE, looking to brush up on your VB programming skills, or simply have a burning desire to code a simple calculator, this three-part video lesson is for you.

In this ClearTechInfo video the instructor shows how to use the Firefox 3.5+ private browsing feature. To use this feature you need a Firefox version 3.5 or more. Now to start a private browsing session go to tools and click on Private Browsing button. This will trigger a new private browsing session that will now store any browser history, search history or any temporary internet files for that session. But this will still allow you to download and keep files and also add bookmarks. This vid...

This is a four part video where I simply talk about the business-related aspects of teaching English to private students.

If you're looking for some manscaping tips, this how-to video is for you. Learn the tips and tricks to go smooth down there and impress the ladies. Be careful, follow the steps and you too can trim the grass and make the tree look larger. So if you want to shave your private parts, look no further.

When it comes to back to school, you probably already have enough on your plate as it is to think about. From new books to new classes to new crushes, you're probably feeling overwhelmed by the kick off of the school year.

If your computer is acting funky, you may need to run a full Checkdisk or chkdsk. Chkdsk is a program that is included with your Windows operating system and is meant to find and diagnose any potential problems with your PC. Check disk will find errors in your boot sector and fix them, as well as point out any issues you may not be able to normally see.

Betty describes how to make spicy flour tortilla crisps: little crispy rounds, or squares, make a great appetizer. Use them with various spreads! Or serve them as the bread to start off a steak dinner. Start with your flour tortillas. After cutting them into sectors, baste them in extra virgin olive oil. Apply the oil to the top and bottom sides. Sprinkle a bit of salt. Use paprika (or any flavor you want!) to add a little spice! Sprinkle from high above so that your spices don't clump. Now p...

In this tutorial the instructor shows how to compute the Surface Area of a Cone. He explains that you need to find the individual surfaces areas first. Hence the bottom part of the cone which is circular can be calculated as Pi*r*r, where r is the radius of the base circle. Now for the sides surface of the cone, it looks like a sector and he derives its area thorough some deduction. Now he adds both the base surface area of the cone, and the lateral surface of the cone which finally gives the...

In this video the instructor shows how to calculate the area of a circle using squares. She starts with the formula of the circumference which she says is circumference C = Pi * D, where D is the diameter of the circle. Now she says that you can turn the shape of circle into a square and compute the area of the square there by calculating the area of the original circle. She shows how to do this by cutting up the square into sectors and arranging them in the form of a rough square and calcula...

Hyundai Motor Company says it will launch its driverless tech ahead of schedule, but the Korean carmaker will remain behind mainstream rivals, including General Motors (GM), Nissan, and Honda.

A warning to all of you iPhone users with parents, significant others, and nosy friends: Private Mode in the Safari browser isn't as private as you think. At least, not as private as it used to be back in iOS 7.

Allow for your community to grow and expand by adding in a private messaging system to your website. Even if you're not experienced with PHP or MySQL, this tutorial walks you through the process of setting up the messaging system.

Nothing on the internet is ever truly private and this hack proves it! Learn how to use PhotoFucket to hack into Photobucket with this video. You'll be able to access Photobucket without a password and view private photos from users. Be careful what you leak though...you might unwittingly create the next big reality TV star!

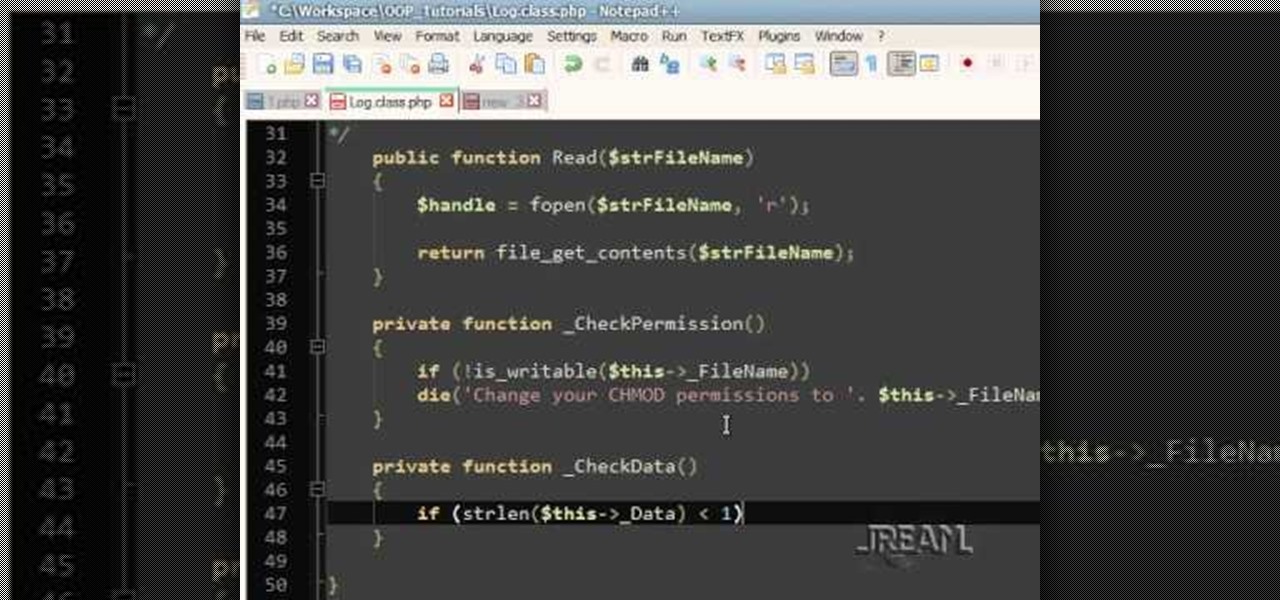
In this tutorial, learn to setup private properties(variables) and private methods(functions) with your PHP OOP programming. This tutorial will have the file logger run through some private methods. Check it out and open the door to the world of PHP programming.

We're living in uncertain times. The sudden outbreak of the novel coronavirus and subsequent self-isolation of roughly half the world's population has led to a massive reorganization of the economy, countless layoffs, compromised security networks, and a variety of other significant disruptions that will forever alter the landscape of our daily lives.

Some investors play the short game, placing their bets on industries that show the quickest return on their investment, and, in the augmented reality space, that means the enterprise sector.

If you have a smartphone, chances are you have something on it you don't want others seeing. Whether it be photos, videos, or documents, some things are best left private. Not everyone is a saint, after all.

If you're serious about keeping your diary for your eyes only then you might have to take some drastic steps. There are some very clever ways to distract from, encrypt, hide, or disguise a diary if you're willing to put in the work.

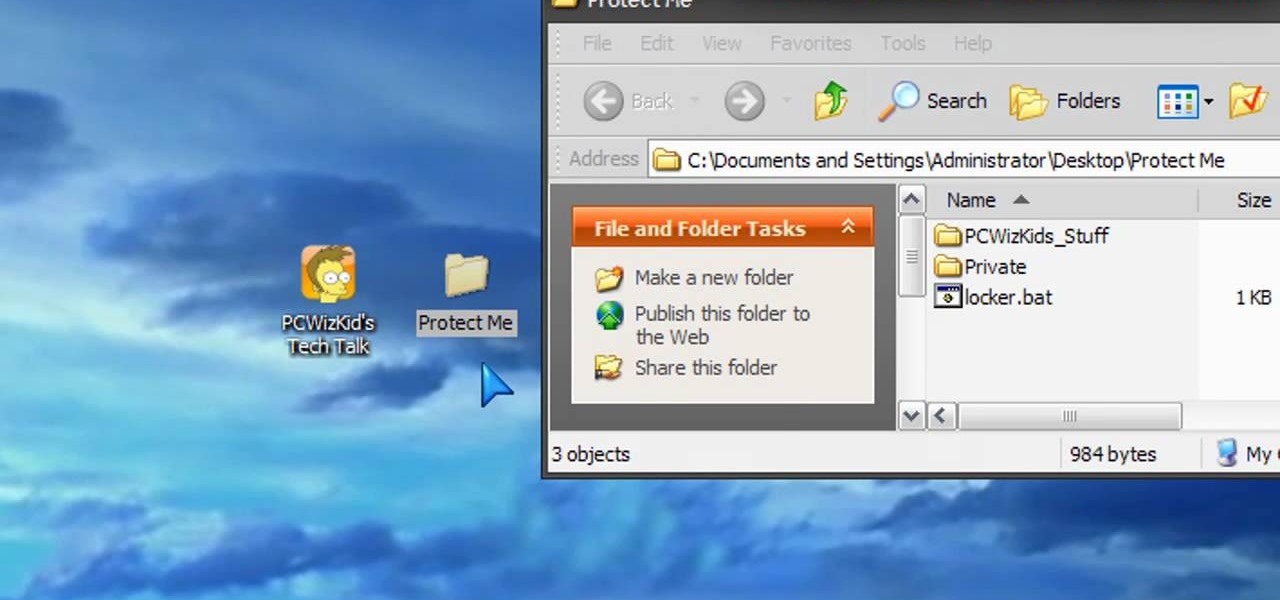
If you've got something on your Windows PC that you don't want to share with the world you're going to want to create a private, password protected folder. This simple video shows how to easily set it up. This works for Windows 7, Vista and XP.

While many image sites allow you to hide image and video catalogs behind passwords, you can often gain access to these images by "guessing" the URL of the image. This process is called fuskering. Photobucket is one of the popular websites that can be fuskered and this tutorial will teach you how to use Nav.Net 4.2 to fusker private images

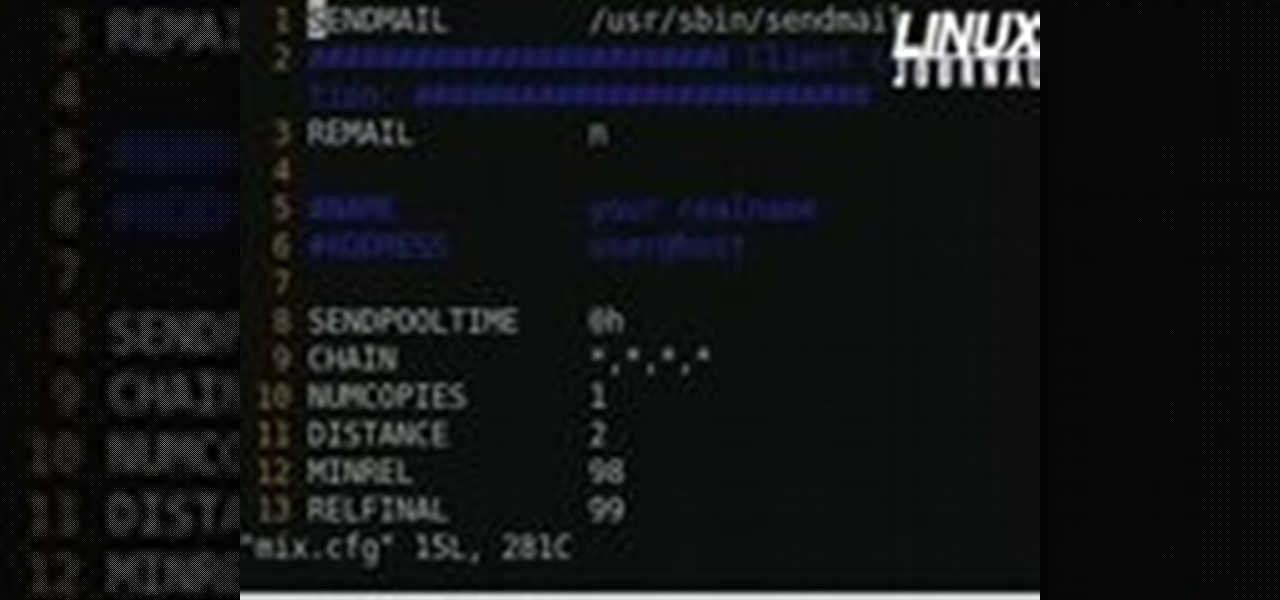
Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.

Privacy is important on Facebook, a lot of users don't even realize that their posts are being broadcast to the masses.

Google calls it "Incognito," Microsoft says "InPrivate," the other browsers call it "Private Mode," and colloquially it's known as "porn mode." Whatever you call the tracks-free way to browse, here's a trick to force your favorite browser to always start with its privacy protocols activated.

Apple's web browser, Safari, stores information like web history, Google's search history and cookies from websites. There may be certain instances where you want to keep this information private–for example, if you're on a public computer or have borrowed a computer from a friend, you may want to keep that information to yourself. For a step-by-step guide to using the private browsing feature in Safari, watch this OS X video tutorial.

One method you can use to protect yourself, is to ensure you clear your private data, such as your search history, and in this screencast tutorial, we show you how to do just that in Mozilla Firefox.

Getting your pilots certificate may be on the expensive side, but after only a few weeks of training you can be flying all over the country! We show you some tips on the path to getting a private flying certificate in this video, and if you're afraid of heights, just do what Veronica did -- pretend it's a video game!

For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption.

Whether it's embarrassing pictures and videos on your smartphone, or files you just don't want anyone reading, there are plenty of ways to hide them. For most devices, that means installing third-party apps like Gallery Plus - Hide Pictures, Sectos - Photo & Video Vault, TimeLock, or Hi App Lock.

The creation of private browsing was brought upon by the backlash against ad tracking and other ways that sites and agencies take away users' privacy online. People were tired of getting spammed with ads for Vitamin C pills simply because they visited WebMD. Private browsing is now built into all of the major browsers and is used frequently. While private browsing is more infamously known as the "Porn Portal," and does prove to be a great way of keeping racy content out of the sight of others...

When conducting covert mobile surveillance with video it is vital to have a good bag that will contain and allow you to get footage in an inconspicuous manner. Always take into consideration the lighting and distance you’ll be at.

In this video tutorial, viewers learn how to play the game, Borderlands online with Hamachi private network. Users will need to first download the Hamachi private network. Then open Control Panel, and select Network and Sharing Center. Under Tasks, click on Manage Network Connections. Click on the Advanced menu and click on Advanced Settings. Move the Hamachi network up and click OK. Now open the Hamachi and create a new network or create on. Type in the network ID and password. This video wi...

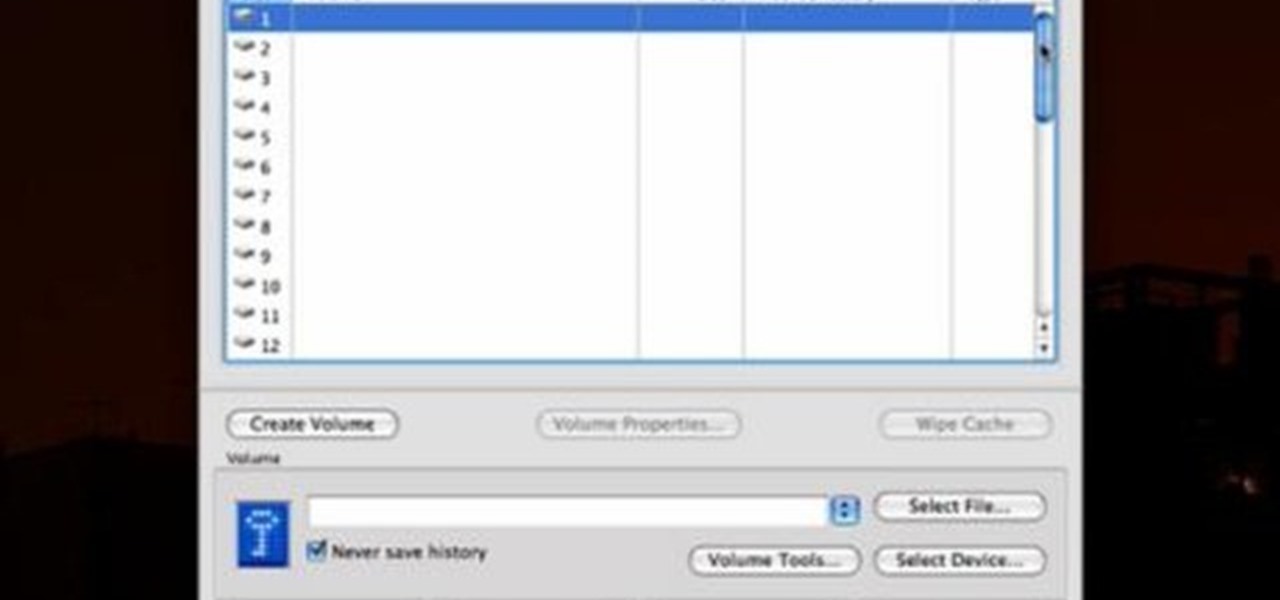
Check out this video tutorial to see how to keep your private files private, even if you have to email them to yourself at your office? TrueCrypt, an open source piece of software, lets you encrypt your files so they remain accessible only to you. This works on any platform; Windows, Linux, or Mac. So, watch this video to see the TrueCrypt download process, how to install it, and how to create an encrypted volume on your hard drive.