If you're interested in joining or creating a fantasy football league, take a look at this guide on how to use leagues in ESPN Fantasy Football and learn the differences between the leagues. You can choose to play in a public or private league, depending on if you want to limit your fantasy league to your friends and family or if you want to play against other team owners you meet online.

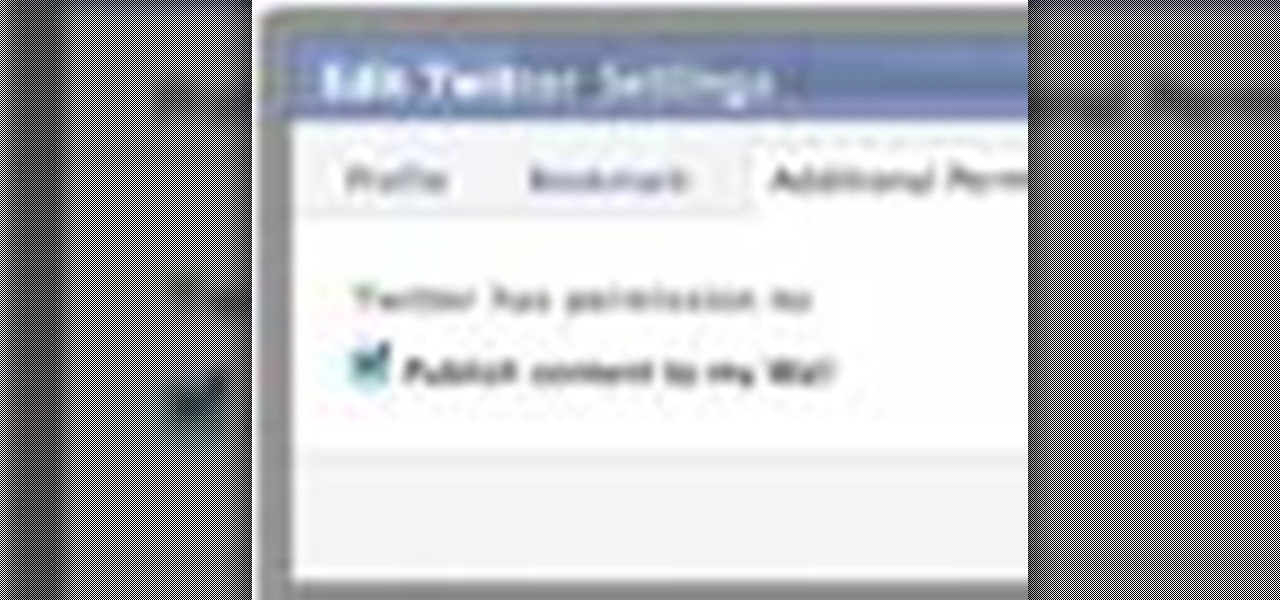
What do President Obama, the Dalai Lama and Justin Bieber have in common? Why, they're all on Twitter, of course. Join the party. Whether you're new to Twitter's popular microblogging application or just missed a few of the essentials along the way, you're sure to benefit from this free video tutorial, which offers detailed instructions on how to create a protected Twitter feed.
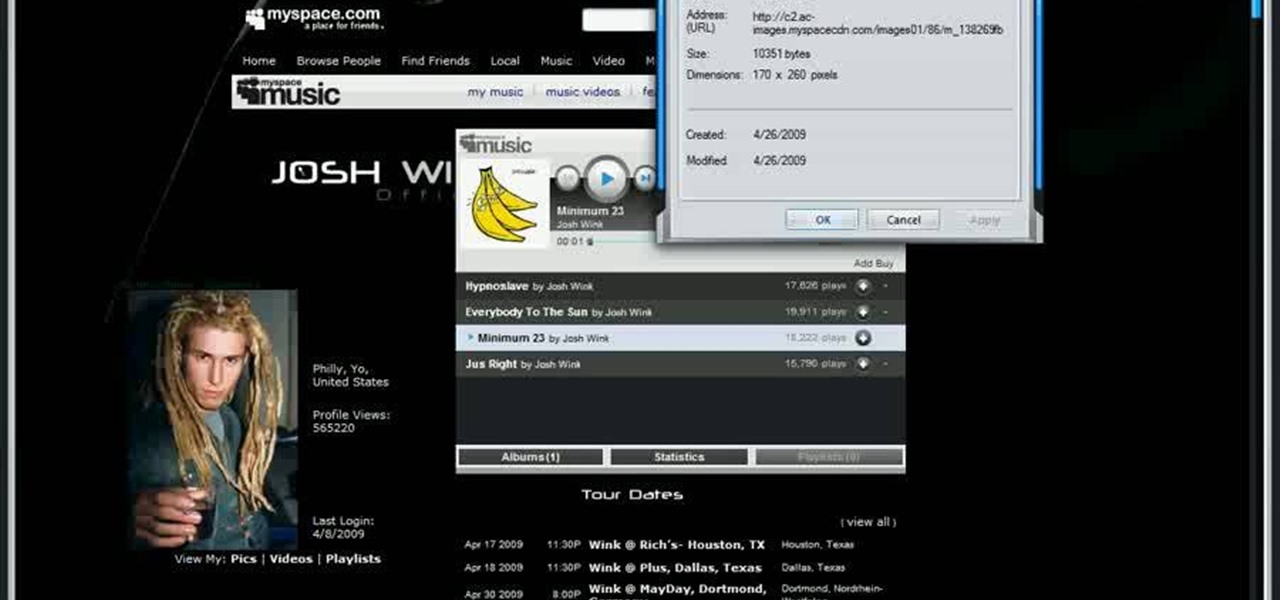
In this video, learn how to view private MySpace profile pictures. The process is easy & quick. In no time you will surfing MySpace freely with no privacy preferences to stop you.
Jared of the TechCentric crew gives you the lowdown on the basics of keeping your VoIP conversations secure and, on the other side of things, how to use the Cain VoIP sniffing application. For detailed instructions on keeping your VoIP conversations private, watch this hacking how-to.

Facebook has announced the cancelation of its annual F8 developer conference, citing concerns around the developing coronavirus health crisis.

As it prepares to ship its first product by the end of the summer, Magic Leap has managed to impress yet another high-profile investor in telecommunications giant AT&T.

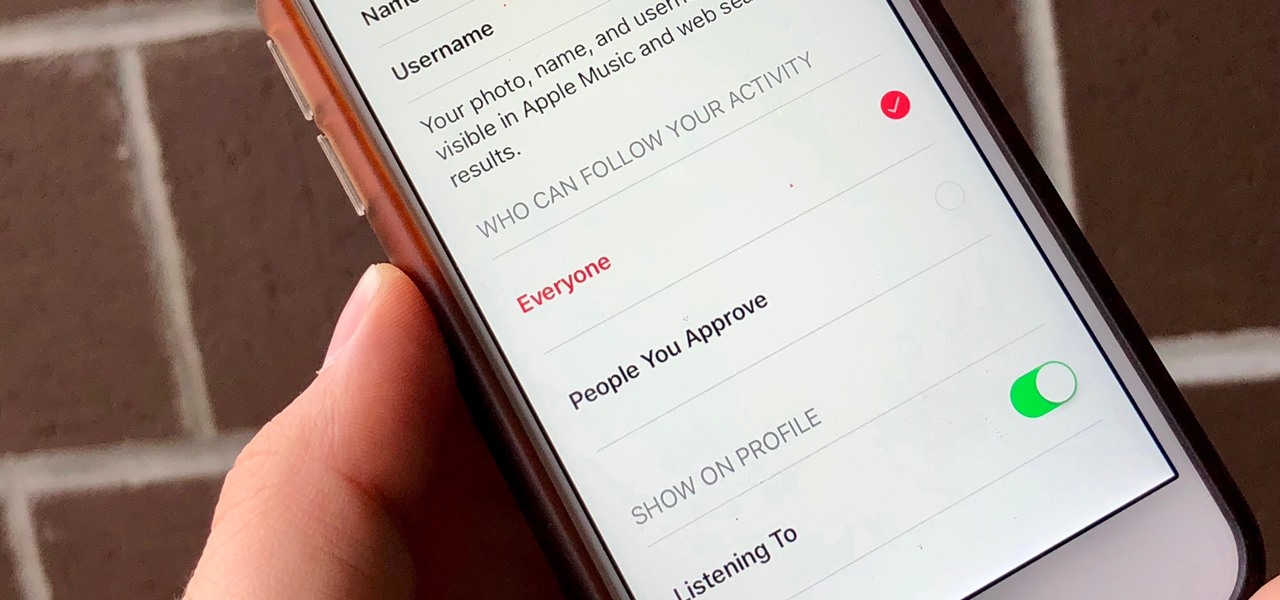
Apple Music, Apple's answer to Spotify, has many interesting features packed in to make that $9.99/month price tag as attractive as possible. One of those features is geared towards social listeners — those who want to follow other Apple Music users and who want to be followed back. But here's the thing: how do you know if your account is public or private?

Nissan has confirmed reports that the Nissan Leaf's Propilot option will go on sale in the US in September, but when it does, don't expect it to compete against the Tesla Model 3's driverless features.

We continue to field stories underscoring the strong trends of Investment in augmented reality in various sectors. This week, one company strengthens their offerings to the enterprise sector, while two other companies capitalize on the promise presented by augmented reality to consumers – specifically, in gaming.

One inventor wants to bring augmented reality to internet radio and home audio speakers. Meanwhile, a leading consumer electronics company has opened up access its deep learning tools for building augmented reality apps. In addition, analysts examine how augmented reality will impact the design and construction and profile the top developers in augmented and virtual reality.

Volvo Cars' claims it will offer Level 4 models by 2021 means the premium carmaker will likely have to finalize the driverless design to meet the aggressive timeline by next year at the latest.

The automotive industry is traditionally very conservative, so when a carmaker says it will launch a particular model or feature by a certain date, it means a lot.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

The US Department of Education has put together a competition called the EdSim Challenge with a $680,000 purse to facilitate next-gen education. The event calls upon augmented and virtual reality, as well as video game developers, to bring immersive simulation concepts to prepare the workforce of the future.

Ideally, wine would stay as perfect and delicious as the day it was first uncorked forever. But, thanks to a pesky process called oxidation, re-corked wine (no matter how you do it) pales in comparison to a fresh's bottles original magic.

As you may know, your iPhone stores data on your location from time to time. If you'd rather that information be kept private, watch this video for some helpful instruction on how to protect your location information. Encrypt the information being gathered by iPhone tracker.

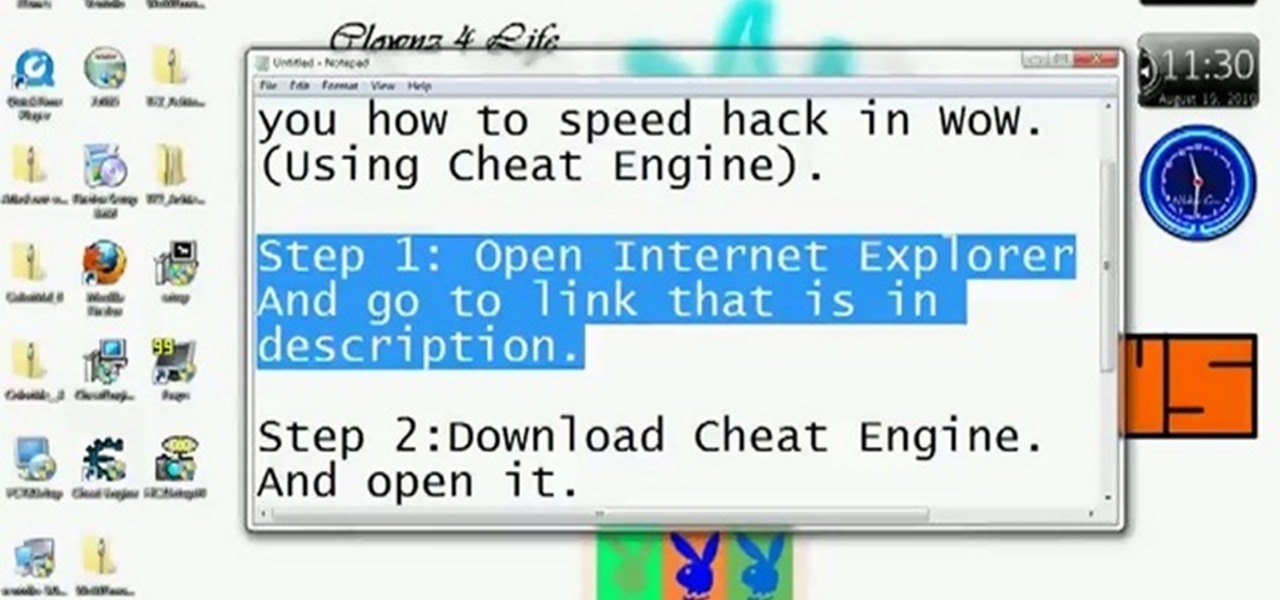
Be careful! If you use this on a public World of Warcraft server, you might get caught and banned by the GMs. However, if you are on a private server, or don't mind the risk, here's how you can use Cheat Engine to hack the game.

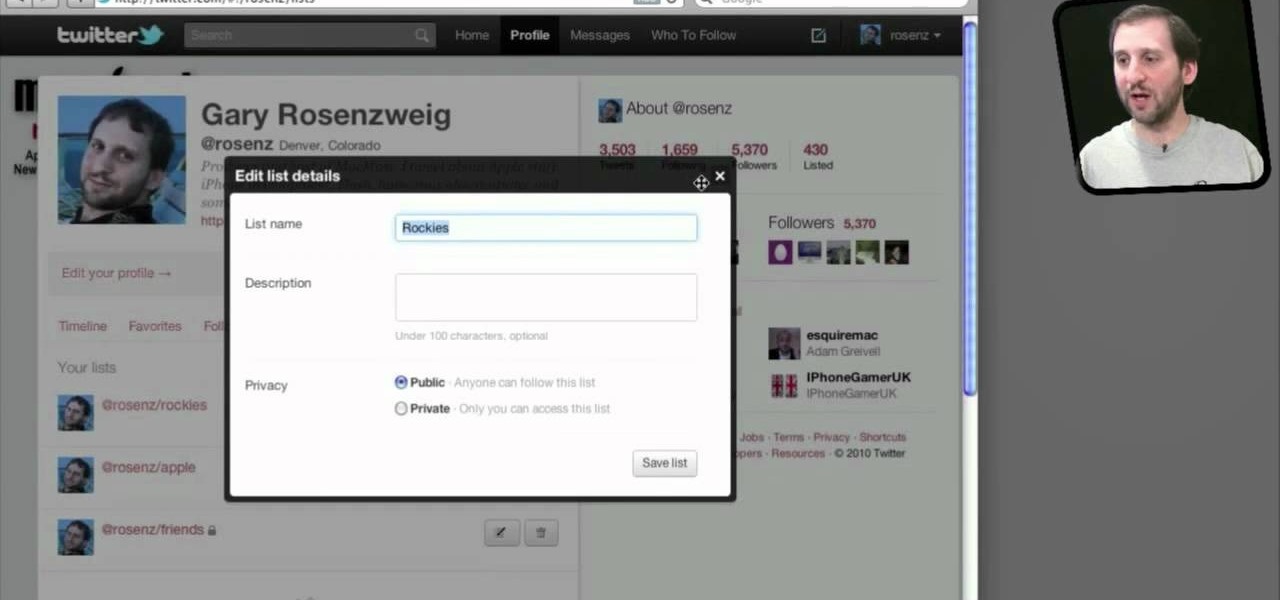
Do you spend a lot of time on Twitter? You can sort and organize the people you follow by grouping them together into Twitter lists and then viewing only that list. These lists are arbitratry categories that you create and can be viewable by others, or made private. You can also view other public lists that people have made. This video shows you how.

When you use Gmail, Google Maps, Google Documents or any of the other Google products, you send trackable information about yourself to Google. By going in and configuring your account settings in Google Dashboard, it's possible to manage the information about yourself that you send them. This informative video shows how.

In this tutorial, we learn how to keep personal information private when using Facebook. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

Big Brother is closer to becoming a reality than ever before, especially in the UK. If you're concerned about whether you phone is being tapped, watch this video to learn about steps you can take to find out whether your phone has been bugged or not and make sure your communication remains private.

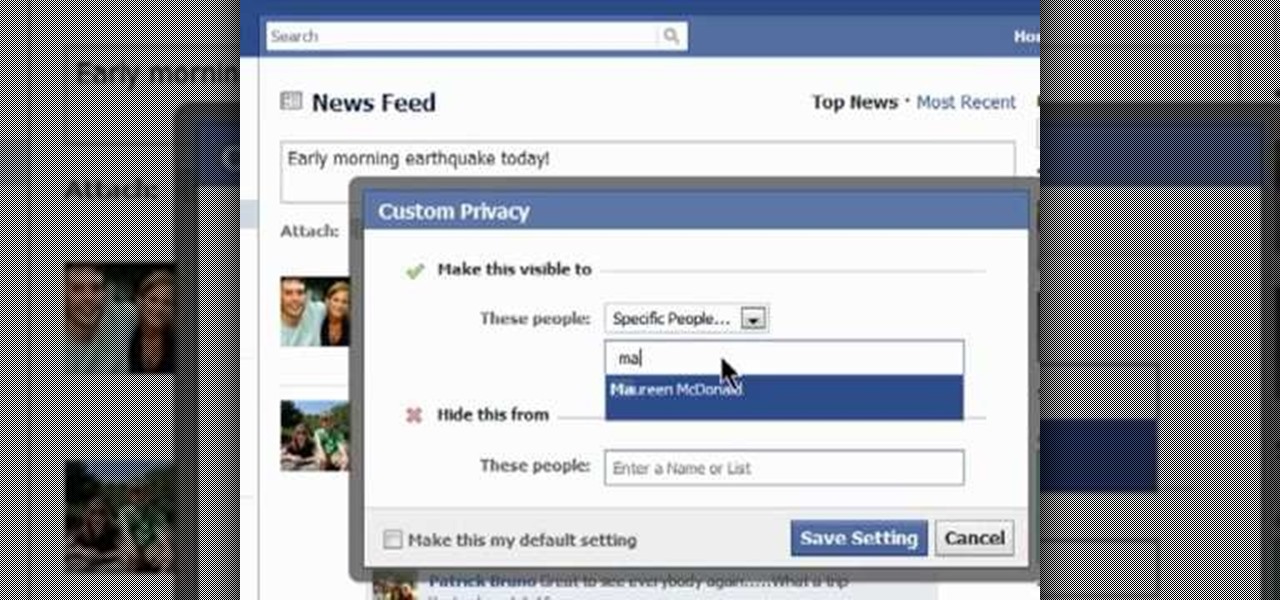
Protect your Facebook posts! This clip will show you how it's done. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to perform a particular task on Facebook, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.

The bleach bypass effect is a classic, and is large part of what gave Saving Private Ryan it's distinctive look. This video will teach you how to apply bleach bypass yourself using Adobe Premiere Pro. Give your video that old-school look using the most modern of technologies.

Curious about all those jailbreak videos and what they mean when they say "SSH into your phone"? In this video, learn how to SSH into either an iPhone, iPhone 3G, or an iPod Touch. Additionally, learn how to download videos from Cycorder on an iPhone and iPhone 3G with Cyberduck. Links & codes you will need:

Keep private info from prying eyes and earn some peace of mind when you safeguard your PC or Mac against nosy intruders. You will need several great passwords, virtual desktop software, snoopware blockers, a screen filter, a mirror, a healthy sense of paranoia, WPA encryption, and an understanding IT specialist.

There is a security flaw with any Apple iPhone running firmware version 2.0.2. This flaw potentially gives a person access to your email account and contacts when you have your iPhone locked. This video demonstrates a simple, but impermanent, fix for stopping others from accessing your private information. To protect your own Apple iPhone, watch this tutorial.

This sequence of instructional videos provides a near comprehensive lesson on how you can change your voice from that of a male to that of a female. This video series is aimed at aiding transgender individuals, but is also useful for people who want to learn to do really great voice exercises and impersonations.

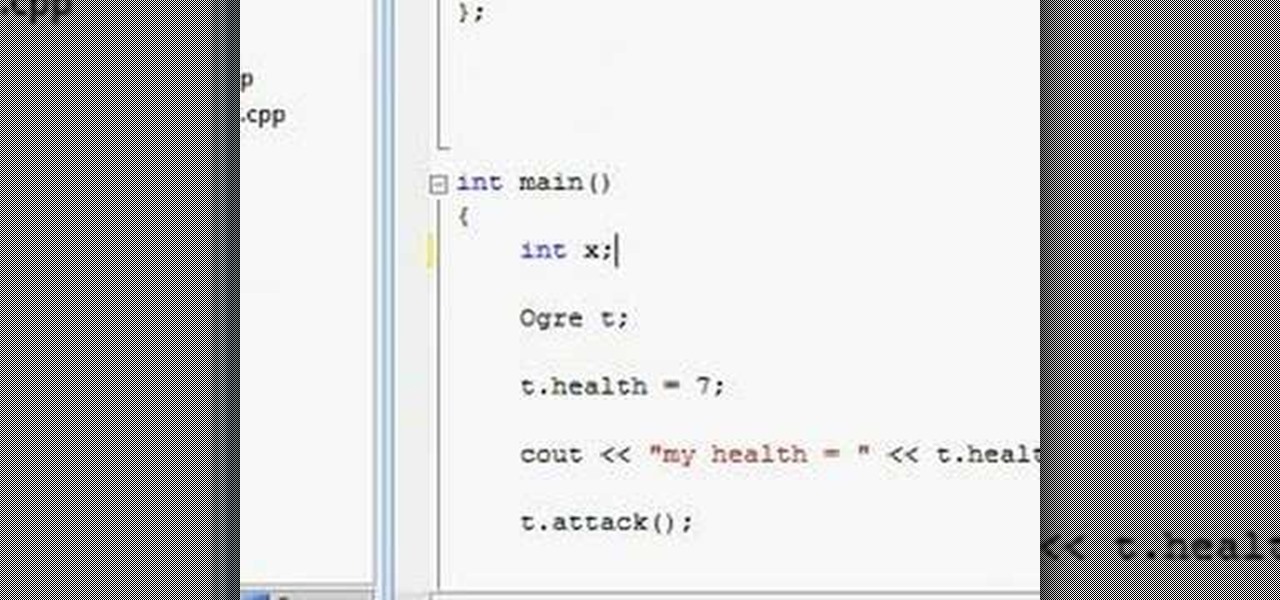
Watch this video to learn how to create OOP design with C++. This video also covers public and private variables and functions.

Today's word is "reticent". This is an adjective which means not revealing one's thoughts, or being reserved.

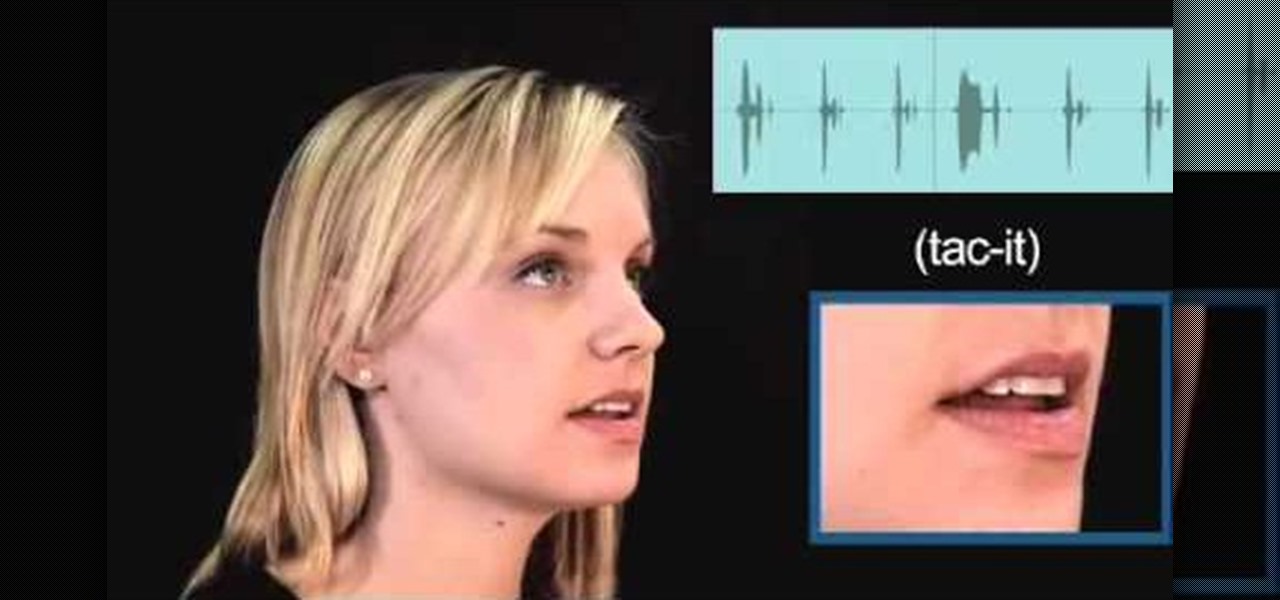
Today's word is "tacit". This is an adjective which means implied or conveyed without words.

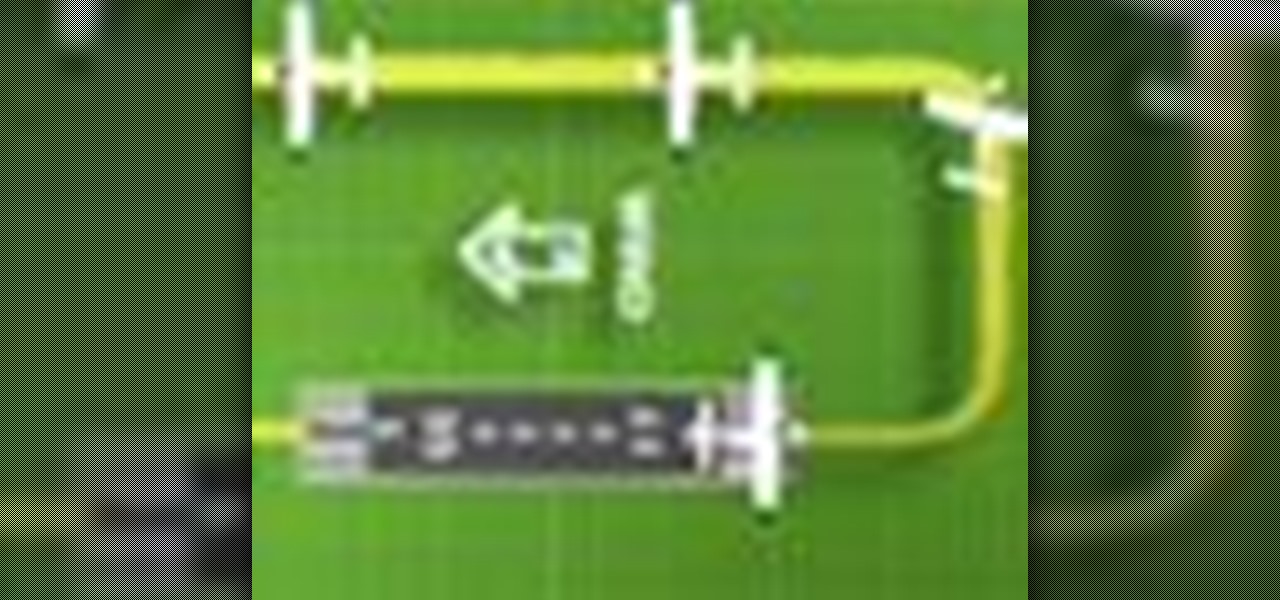
In this AeroCast episode, UND Aerospace discusses the Slow Flight maneuver as performed in the Piper Warrior (PA-28-161), referencing the procedures and standards outlined in the UND Warrior Standardization Manual. All performance tolerances are based on the performance standards set forth by the FAA Private Pilot Practical Test Standards. Since the most critical phases of flight occur at airspeeds less than cruise, a pilot must always be comfortable with his or her airplane’s handling charac...

In this AeroCast episode, Anthony Bottini discusses the Power On Stall maneuver as performed in the Piper Warrior (PA-28-161), referencing the procedures and standards outlined in the UND Aerospace Warrior Standardization Manual. All performance tolerances are based on the performance standards set forth by the FAA Private Pilot Practical Test Standards. Power On Stall practice is vital in increasing a pilot’s proficiency in regards to stall recognition and stall recovery techniques during an...

Unless you have your own private airport (I’m looking in your direction John Travolta) then you will most likely have to coordinate your takeoffs and landings with all the other air traffic using your specific airport. Whether it be a towered or non-towered airport, this latest UND Video Standardization Lesson is designed to help you, the student pilot, become familiar and hopefully more comfortable with Airport Traffic Pattern operations.

Need internet access and you don't have a login? Hack into a private or controlled network with this tutorial. Thefixed.org also shows you how to build a smoke bomb!

Find the biggest files on your computer ordered by size. Learn to order folder by filesize so you can find the ones harboring the most diskspace terrorists. Learn to clear up your private data automatically and wipe it clean from being undeleted.

Technically it's the California Chardonnay vs. the French White Burgundy but since they both use the Chardonnay grape it's still a battle. In this video Gary tastes and compares two against two: 2004 Pessagno Sleepy Hollow Chardonnay and 2004 Beringer Private Reserve Chardonnay vs. 2003 Caves De Colombe Chassagne Montrachet and 2001 Matrot Puligny Montrachet Comb Ottes. See which Gary puts on top.

Hello guys, today I wanna share how to create a drag and drop with listbox using VB.net. Just copy and paste the following code under public class.

Apple's new iOS 8 has a ton of new features, and so does their revamped Safari app, only some of the features aren't quite as obvious as others. In this guide, I'll show you my 5 favorite Safari secrets in iOS 8 for your iPad, iPhone, or iPod touch.

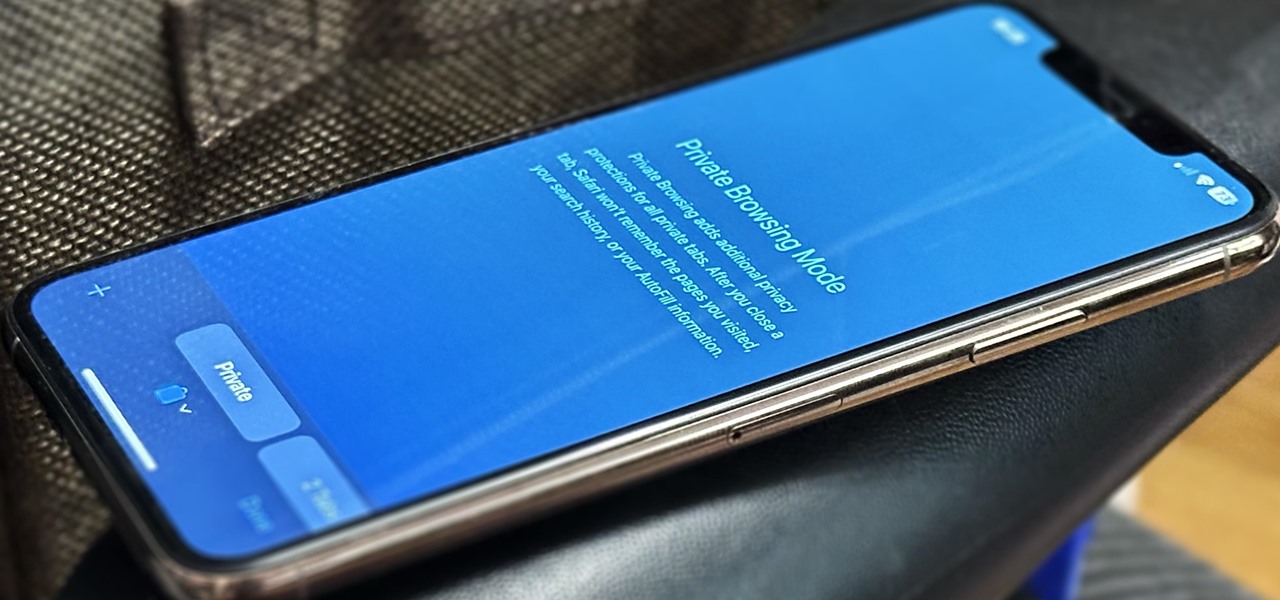
Private Browsing mode finally lives up to its name in Apple's huge Safari 17 update for iPhone, iPad, and Mac. So whether you search for things you don't want anybody to know about or want to ensure websites and trackers aren't eavesdropping on your activity, you'll want to update your devices pronto.

While the rest of the world is scrambling to figure out how to adopt augmented reality and VR tools for remote meetings, one company is building its war chest to serve the growing space of corporate clients who need this kind of immersive computing training.