In this video tutorial, viewers learn how to play the game, Borderlands online with Hamachi private network. Users will need to first download the Hamachi private network. Then open Control Panel, and select Network and Sharing Center. Under Tasks, click on Manage Network Connections. Click on the Advanced menu and click on Advanced Settings. Move the Hamachi network up and click OK. Now open the Hamachi and create a new network or create on. Type in the network ID and password. This video wi...

Apple's web browser, Safari, stores information like web history, Google's search history and cookies from websites. There may be certain instances where you want to keep this information private–for example, if you're on a public computer or have borrowed a computer from a friend, you may want to keep that information to yourself. For a step-by-step guide to using the private browsing feature in Safari, watch this OS X video tutorial.
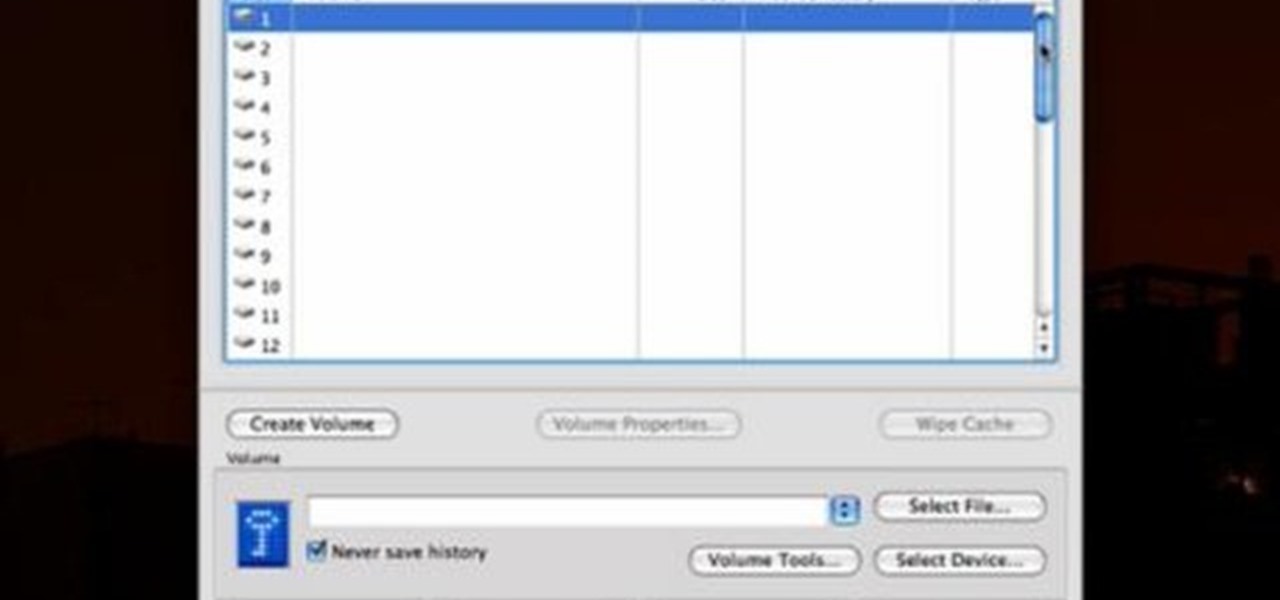
Check out this video tutorial to see how to keep your private files private, even if you have to email them to yourself at your office? TrueCrypt, an open source piece of software, lets you encrypt your files so they remain accessible only to you. This works on any platform; Windows, Linux, or Mac. So, watch this video to see the TrueCrypt download process, how to install it, and how to create an encrypted volume on your hard drive.
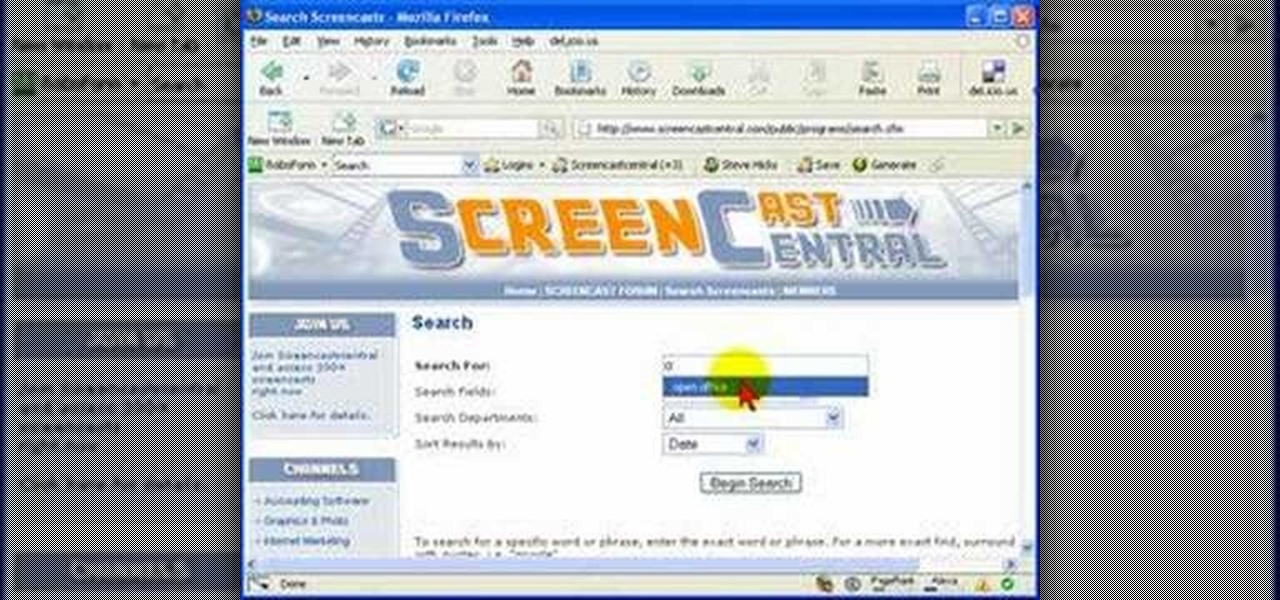
One method you can use to protect yourself, is to ensure you clear your private data, such as your search history, and in this screencast tutorial, we show you how to do just that in Mozilla Firefox.

Getting your pilots certificate may be on the expensive side, but after only a few weeks of training you can be flying all over the country! We show you some tips on the path to getting a private flying certificate in this video, and if you're afraid of heights, just do what Veronica did -- pretend it's a video game!
Cyber Security is a horrible computer virus. It mimics a virus protection program and invades your system, making it nearly impossible to remove. In this tutorial, learn how to remove this annoying trojan horse from your PC and save your computer.

Ever wanted to learn how to pick a lock? Well, there's no better time than now to start learning the craft of so many locksmiths out there... lock picking. Just watch this video tutorial to see how to pick a Brink's high security lock.

Have you ever been the victim of theft? It sucks. Why would these lazy scumbags rather steal from us than work hard like everybody else?

Video tutorial showing how to make your own solar-powered wireless security camera using an off-the-shelf solar panel and any wireless webcam. See creator site for more detailed graphics.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.

It's no secret that there's a lot of surveillance going on these days. It's easier than ever to end up in a database, and even former government agents are speaking out about the atrocious amount of spying being done against our own citizens. They've targeted our laptops, cars, IP addresses, and now they're coming for our iPhones. AntiSec hackers managed to get their hands on a list of over 12 million Apple UDIDs (Universal Device IDs) from an FBI computer, and they published 1,000,001 of the...

In this tutorial, we learn how to remove security tool in less than one minute. First, restart your computer, then press "ctrl+alt+del" when your new window starts up. After this, wait for a few seconds, then if you see the security tools pop up, end the task for it. Then, go to the start menu, then all programs, then look for any security tools. Right click, on "find target" then delete it! After this, your security tools will be deleted and will stop annoying you. You will be able to delete...

Today is the day before Thanksgiving. It's also the BIGGEST travel day in North America. Everyone is taking flights home to their family and friends for a nice Thanksgiving dinner. But this holiday will be one to remember thanks to the TSA.

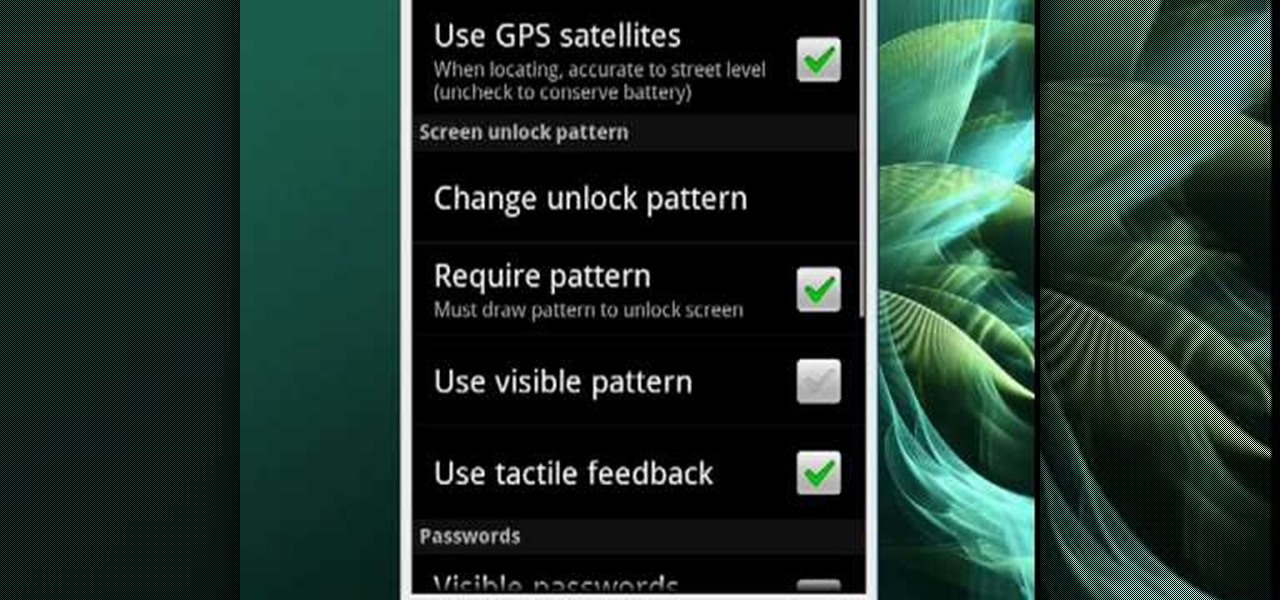
In this video tutorial, viewers learn how to change the lock pattern on an Android phone. The lock pattern allows minimum security on the phone to prevent other people from tampering with your mobile files. Begin by going into the Settings and click on Location & security. Under Screen unlock pattern, select Change unlock pattern. In order to change the unlock pattern, users will have to type in the current unlock pattern. Now type in the new unlock pattern and press Continue. Then retype the...

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

Watch this video tutorial, and learn how to turn an ordinary inexpensive webcam into a hidden home security system, viewable anywhere in the world from your cell phone! With a cute and cuddly teddy bear and a cheap webcam, you can make the perfect homemade security camera, or just a camera to spy on your sister and her friends during sleepovers. Follow along with the steps in this how-to video and learn how to set up this spy system. Note: this video is NOT recommended for people who are perv...

By DevonLocks.Com - Security pins can be a pain. This video shows you how to bypass them. See our other video on how to spot them.

The first step to getting your life together? Getting your online security together. After all, security when you're shopping, video calling, and more means more than ever in a digital age when anyone can copy your info or try to pose as you on the web. This Premium Privacy Bundle featuring Zenmate and StartMail will give you a secure VPN and encrypt your emails, all at a bundled price. The security duo is on sale for 60% off for a limited time, which means it's just $44.99 (regularly $113).

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

If you own the Galaxy S8, S8+, or Note 5, be on the lookout for a new security update. These Samsung devices are the latest to receive the December security update to patch issues from both Samsung and Android.

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

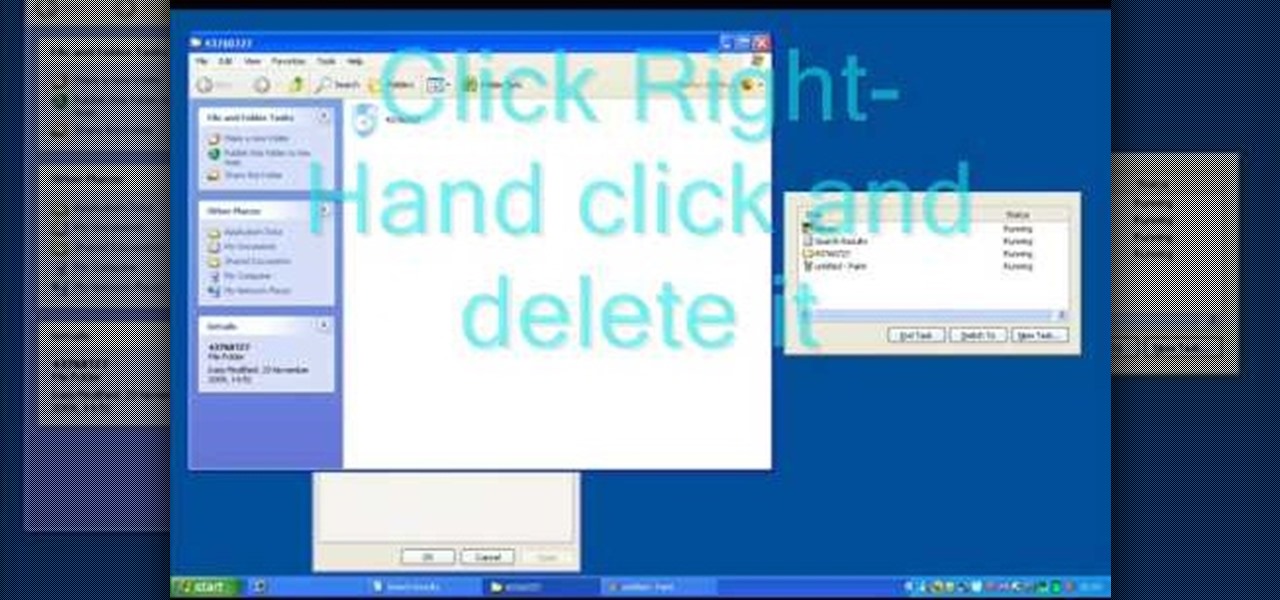
In this video, we learn how to remove Security Tool the simple way. Most ways will not remove this from your computer, but this way will. To start, you will need to restart your computer. After this, press ctrl+alt+del the moment Windows shows up. Then, go to the Task Manager and look through the programs that are open. When your security tool opens, press the same buttons to get the mouse free. Then close the security tool from the Task Manager. Now, go to your desktop and press on the icon ...

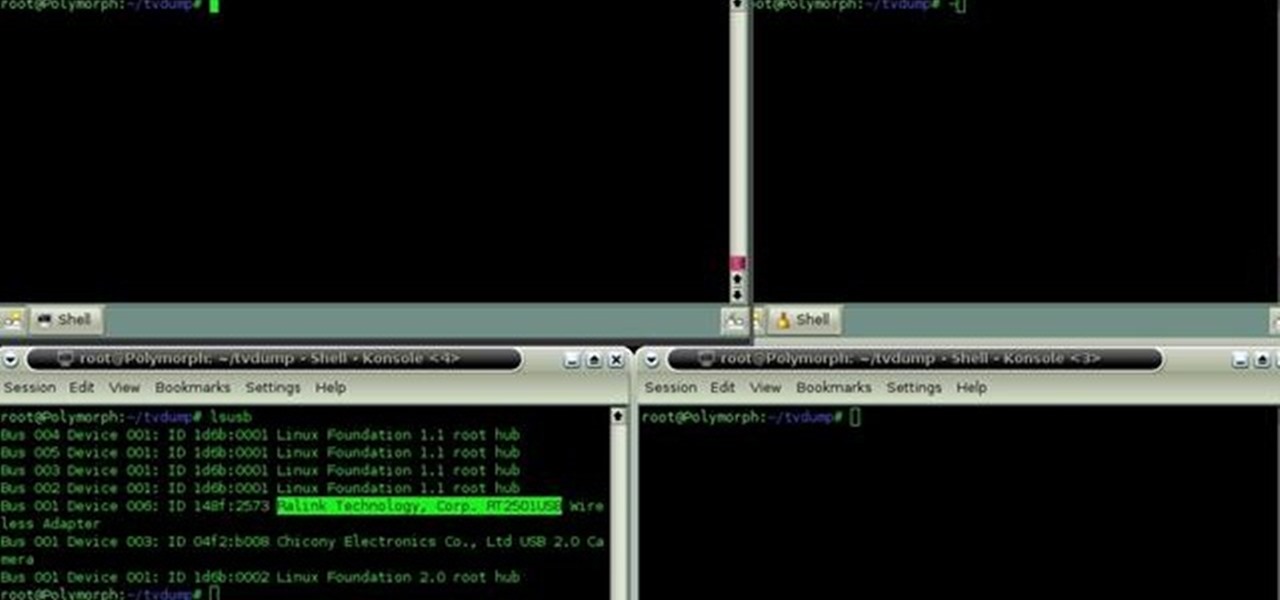
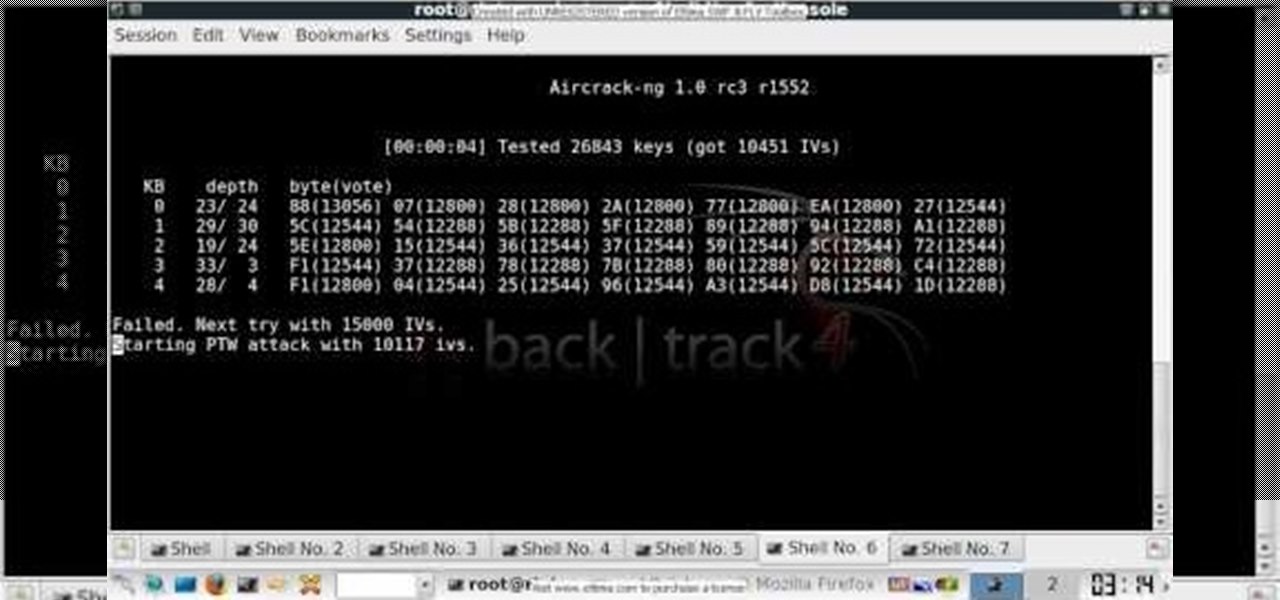
In this clip, you'll learn how to use the BackTrack Linux distro and the Aircrack-ng WiFi security app to hack a WEP network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a 64-bit WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack 3 Linux distro and Aircrack-ng WiFi security app to crack the password to a WEP-protected wireless network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Wish there were a way to turn your webcam into a bonafide security camera? Well, there is! And it's easy! So easy, in fact, that this home-computing how-to from the folks at TekZilla can present a complete overview of the process in just over two minutes. For more information, including step-by-step instructions, take a look.

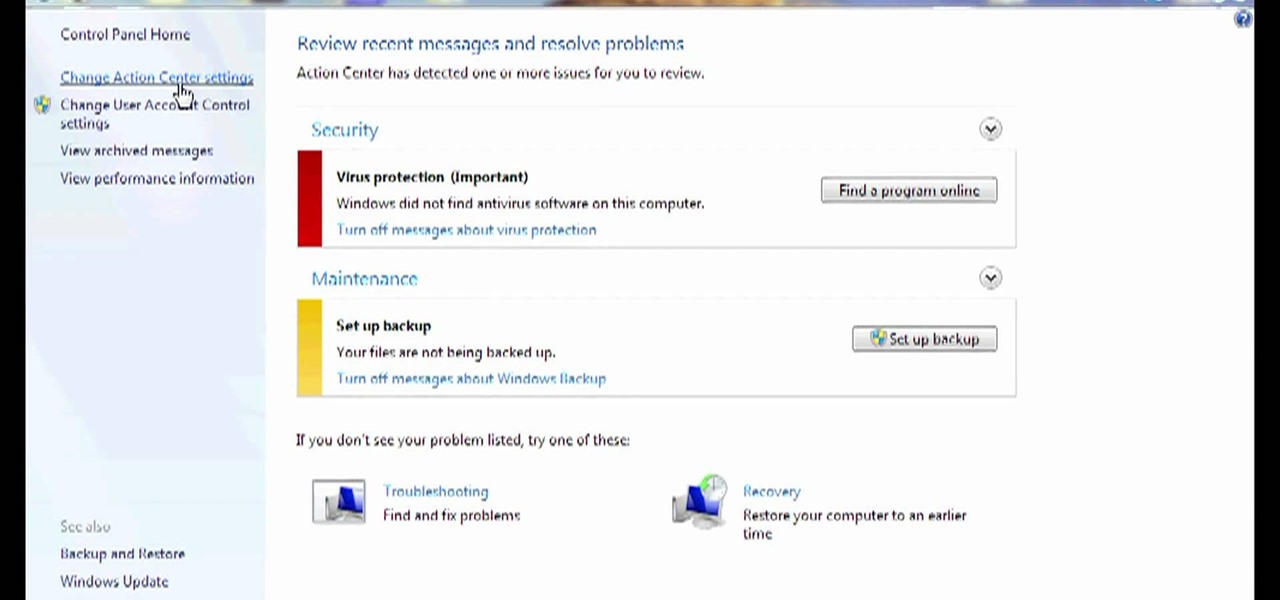
Need some help figuring out how to disable potentially annoying popup security notifications in Microsoft Windows 7? This video tutorial will show you how it's done! It's easy! So easy, in fact, that this home-computing how-to can present a complete overview of the process in just over a minute's time. For more information, including detailed, step-by-step instructions, watch this Win 7 user's guide.

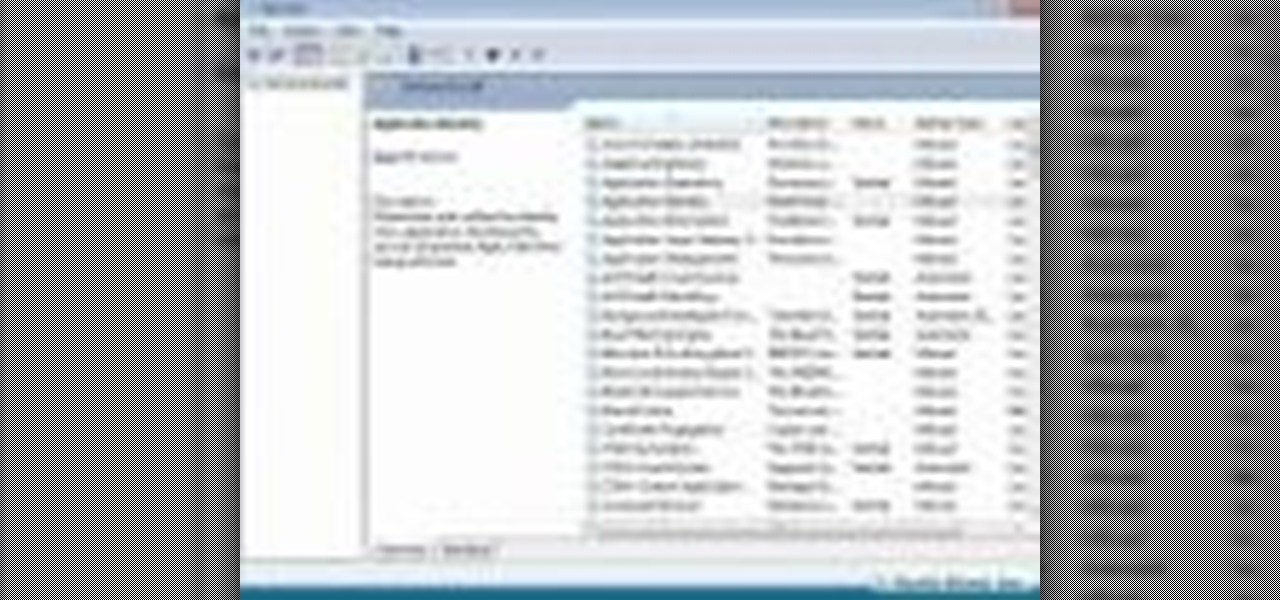
In this Microsoft Windows 7 users guide, you'll learn how to take advantage of the operating system's new Applocker security feature. It's easy! So easy, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in about a minute and a half. For more information, including complete, step-by-step instructions, take a look.