Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to secure remote desktop.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to defend your hacker space with a USB missile launcher.

In this video tutorial, you'll find a step-by-step guide to how a n00b hacker (like you?) can get usernames and passwords easily through one of the security flaws of the Ethernet ADSL router. More than half of Internet users never change their default password which makes this "hack" easy. Take your time to read the text on the slide. For more, and to get started testing the security of your own Ethernet ADSL router, watch this hacking how-to.

Notice: This is probably not new to many people. This *IS* new for some people however, and meant for them! Post interesting cameras you find.

A killswitch is exactly what you think it is: A switch that kills an operation in an emergency situation when the operation can't be shut down in the usual manner. It shuts your operation no matter what the consequences.

If you're interested in joining or creating a fantasy football league, take a look at this guide on how to use leagues in ESPN Fantasy Football and learn the differences between the leagues. You can choose to play in a public or private league, depending on if you want to limit your fantasy league to your friends and family or if you want to play against other team owners you meet online.

What do President Obama, the Dalai Lama and Justin Bieber have in common? Why, they're all on Twitter, of course. Join the party. Whether you're new to Twitter's popular microblogging application or just missed a few of the essentials along the way, you're sure to benefit from this free video tutorial, which offers detailed instructions on how to create a protected Twitter feed.

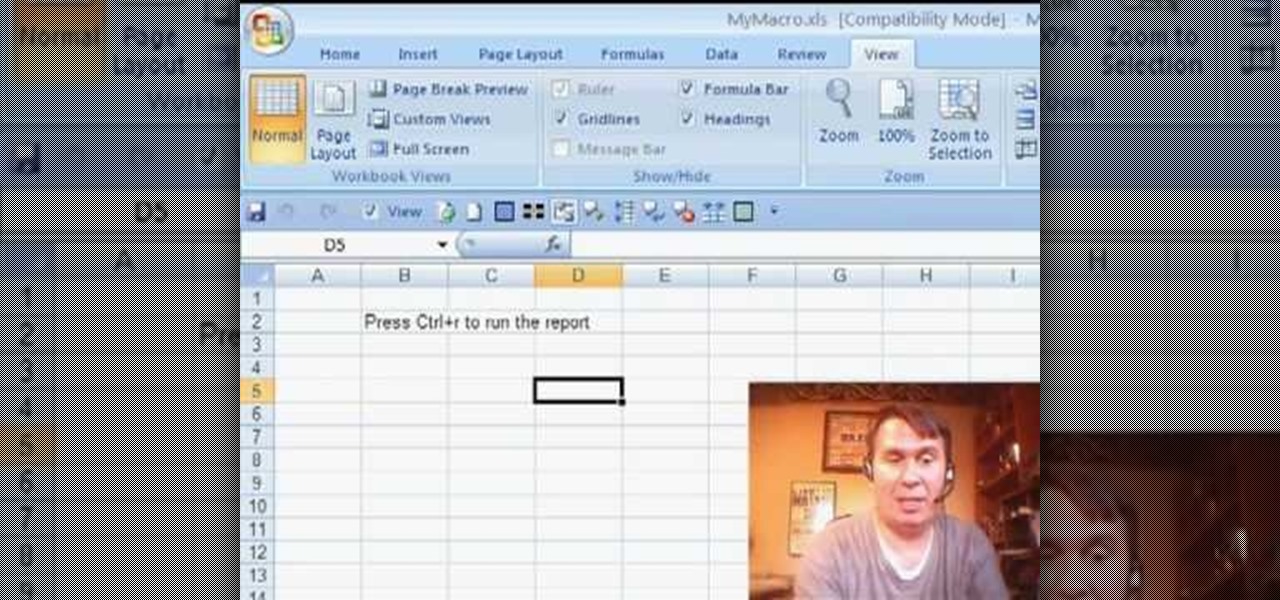
Some times when you upgrade your Microsoft Excel software to Excel 2007 your old macros may stop working. Some times this may be due to the settings and by enabling the macros you can get your old macros to work. Macros are turn off by default in Excel 2007. You can turn this on from the macro security settings. But the settings option is it self completely hidden. You cannot find it in any of the tabs present on the top of the program. Even the macros option present in the view tab has no se...

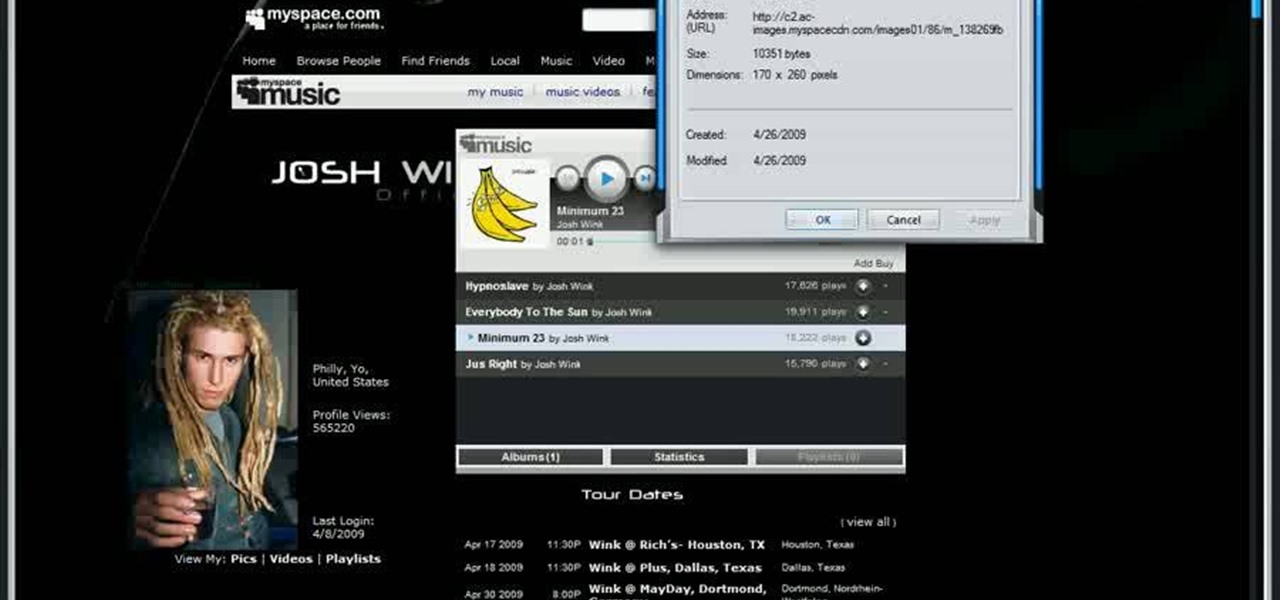
In this video, learn how to view private MySpace profile pictures. The process is easy & quick. In no time you will surfing MySpace freely with no privacy preferences to stop you.

Jared of the TechCentric crew gives you the lowdown on the basics of keeping your VoIP conversations secure and, on the other side of things, how to use the Cain VoIP sniffing application. For detailed instructions on keeping your VoIP conversations private, watch this hacking how-to.

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

Safari's private browsing mode on your iPhone won't sync to other Apple devices or remember your search history, AutoFill data, or visited webpages. Still, it doesn't stop anyone who accesses your iPhone from opening your private tabs. If you don't want anyone snooping through your private tabs, use Chrome instead so you can lock the tabs behind biometric authentication.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

In iOS 13, Apple introduced HomeKit Secure Video, which allows smart home devices with cameras to give iPhone users a private and secure way to store recorded videos. Plus, it has benefits such as object detection and activity notifications. Logitech is the first to add support for HomeKit Secure Video with its Circle 2 cameras, and all it takes is a quick firmware update to get started.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

Chrome is the browser of choice for millions of iPhone and Android users, largely thanks to its user-friendly interface and native Google support. But with concerns over sharing private information with massive companies growing, many people are starting to want a little less Google integration in Chrome.

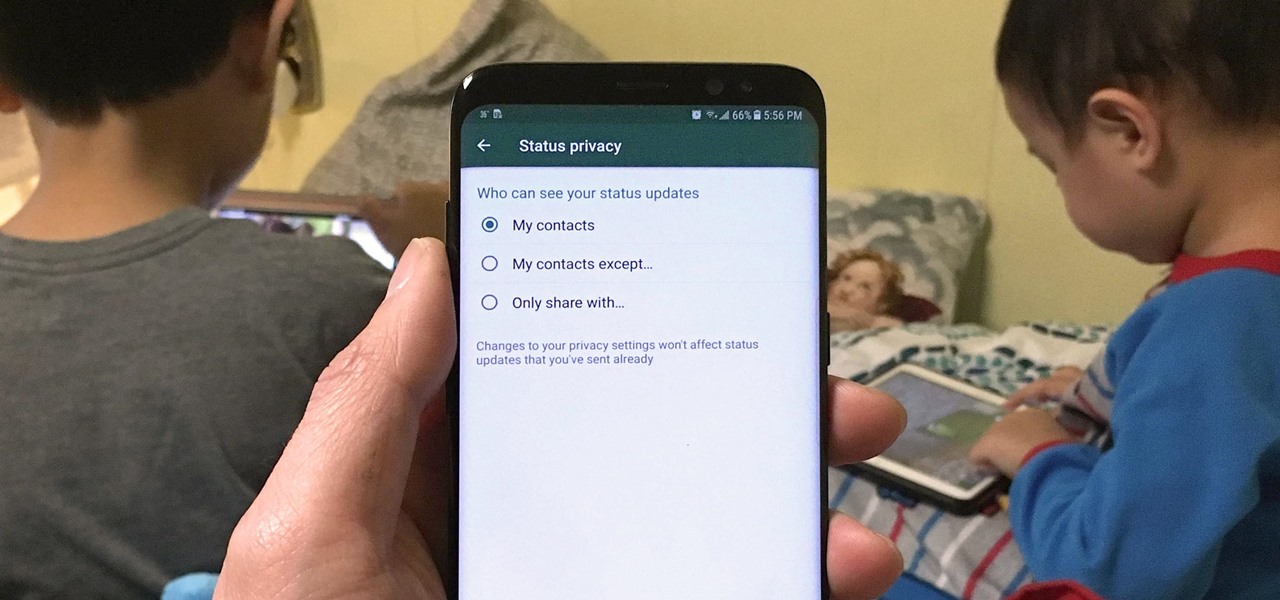
Sharing Stories via WhatsApp Status grants your friends access to your daily adventures in the form of GIFs, photos, videos, or simple texts. Like Snapchat, stories you share with your contacts disappear after 24 hours, giving you an extra layer of privacy since anything you post will not be permanent. And if you want to limit who can see your private stories, WhatsApp also has you covered.

BlackBerry's focus on secure software and their new partnership with manufacturer TCL are two of the biggest factors in their recent resurgence. Last year, the company announced two new devices — the KEYone and the BlackBerry Motion. The KEYone has been available for a while, but after months of waiting, BlackBerry announced the Motion will hit US shores in a few days.

Our smartphones are full of personally-identifiable information. So much of what we do with these devices is tracked and recorded to make our experience more streamlined and personalized. For many users, that's a fair trade — but for privacy-minded folks, it's a raw deal.

The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, implementing three new features to hack-proof your account.

Signal, the encrypted messaging app, has seen 1.4 million downloads in just the first quarter of 2017—roughly twice the downloads it received in the same period last year. Rani Molla at Recode attributes this to Donald Trump's inauguration, as the private messaging service saw a 40% increase in US downloads between Election Day and the end of the first quarter of 2017.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

Some things never change. You'd think that with all the focus on web security, people might take the slightest precaution to keep their online activity private. Maybe there are more people suffering from Paula Poundstone's password troubles than we'd like to believe.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

You would think that with each major iOS update, there'd be fewer ways to bypass the lock screen. Unfortunately, Apple's developers have consistently failed every year since 2013 in this department, leaving open lock screen exploits for iOS 7, iOS 8, and now the latest iOS version, iOS 9, with each exploit being discovered within days of the OS release.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

Hello guys, today I wanna share how to create a drag and drop with listbox using VB.net. Just copy and paste the following code under public class.

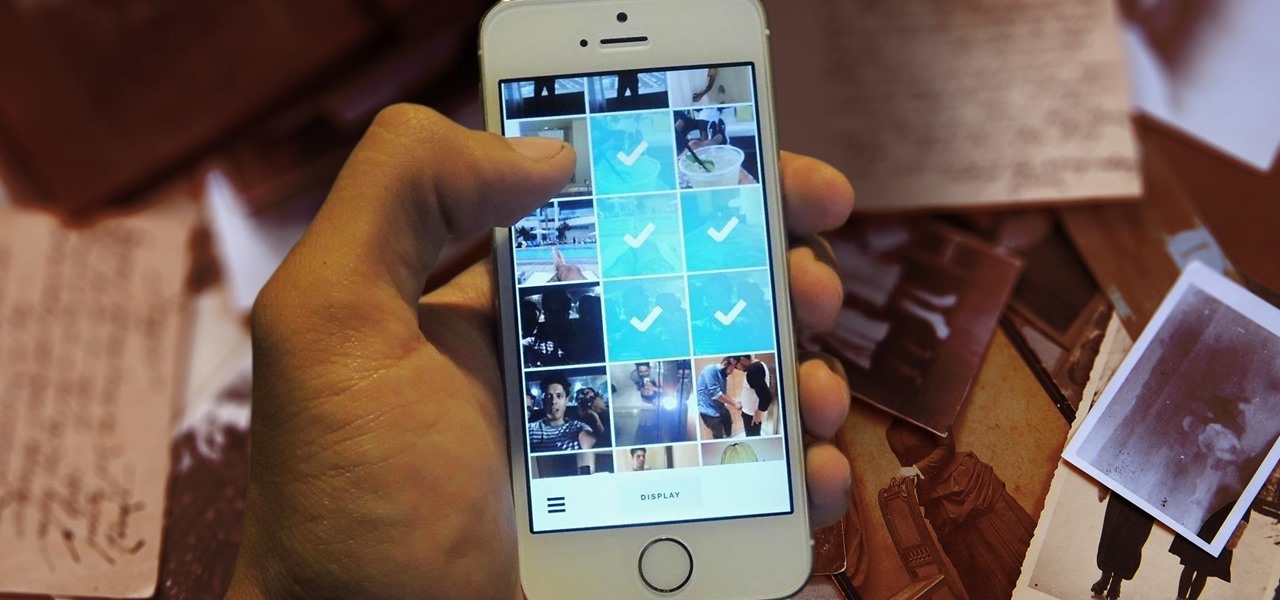
Last week, I showed off a deeply buried accessibility feature built into iOS 7 and 8 that lets you disable screen touches in certain apps. While useful for many reasons, I found it most helpful for preventing nosy family and friends from swiping through the Camera Roll when showing them a photo.

Every day it seems like new information comes to light about how the National Security Agency creeps into our lives. Knowing that they can backdoor into our seemingly private devices is a scary thought, whether you have information to hide or not.

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

As you may know, your iPhone stores data on your location from time to time. If you'd rather that information be kept private, watch this video for some helpful instruction on how to protect your location information. Encrypt the information being gathered by iPhone tracker.

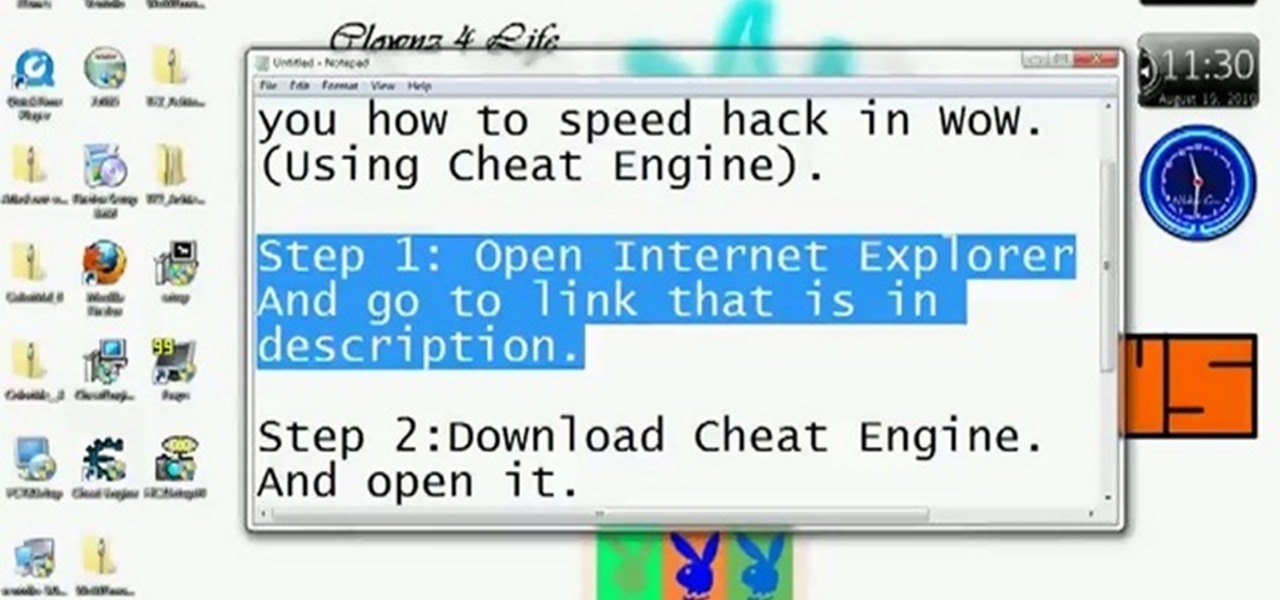
Be careful! If you use this on a public World of Warcraft server, you might get caught and banned by the GMs. However, if you are on a private server, or don't mind the risk, here's how you can use Cheat Engine to hack the game.

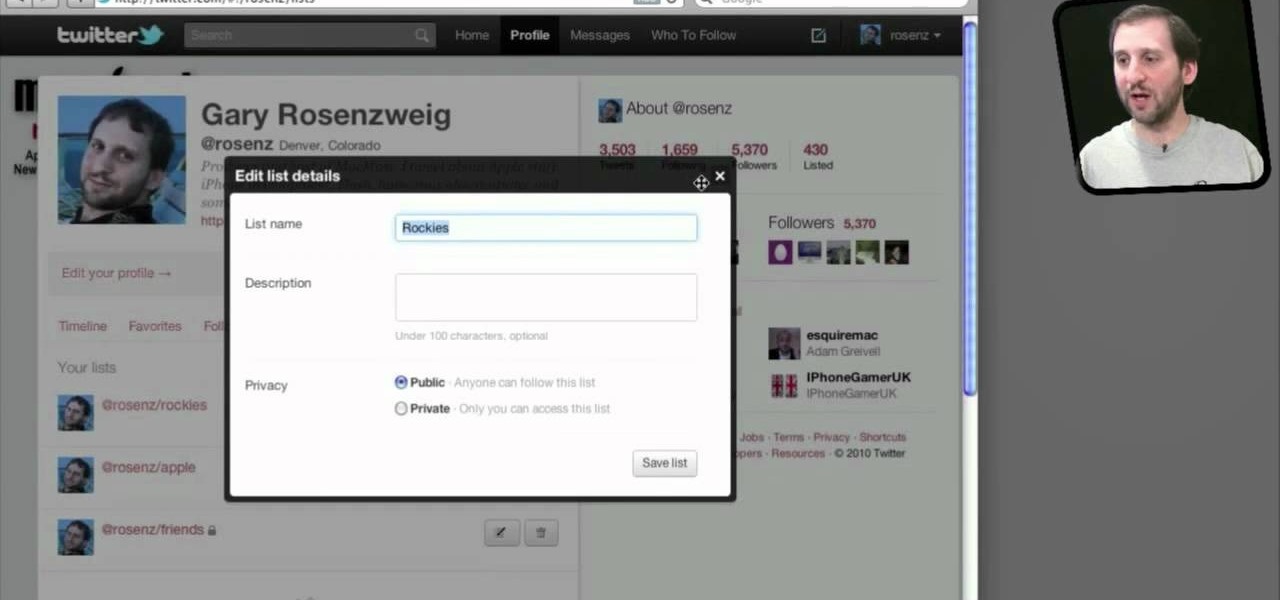
Do you spend a lot of time on Twitter? You can sort and organize the people you follow by grouping them together into Twitter lists and then viewing only that list. These lists are arbitratry categories that you create and can be viewable by others, or made private. You can also view other public lists that people have made. This video shows you how.

When you use Gmail, Google Maps, Google Documents or any of the other Google products, you send trackable information about yourself to Google. By going in and configuring your account settings in Google Dashboard, it's possible to manage the information about yourself that you send them. This informative video shows how.

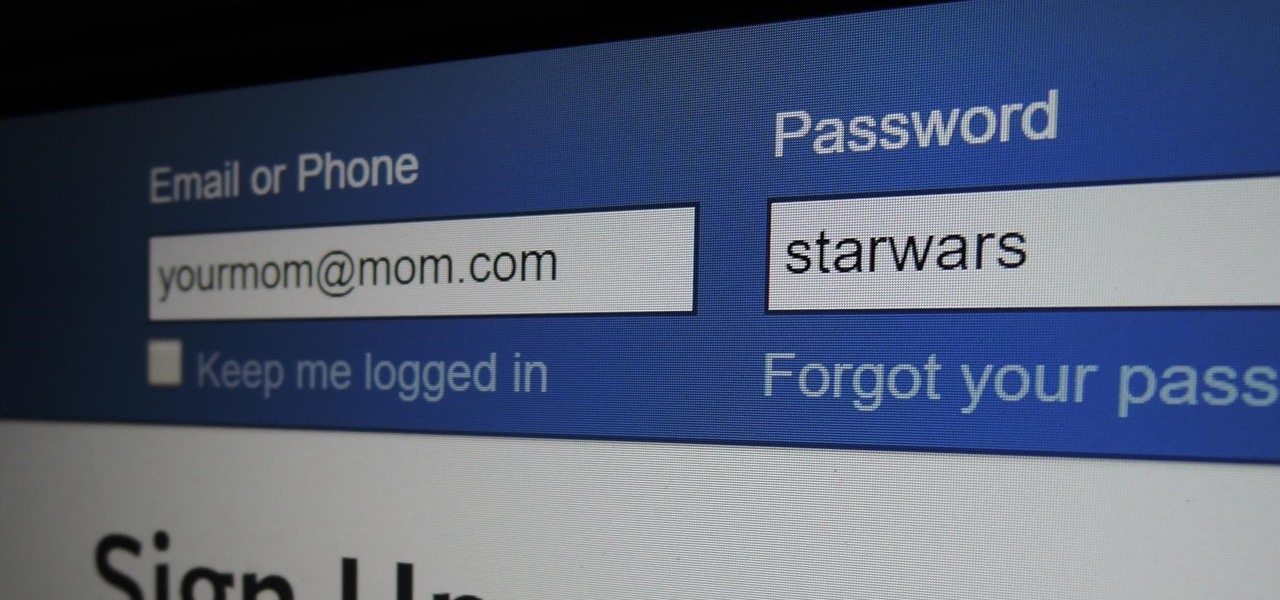
In this tutorial, we learn how to keep personal information private when using Facebook. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

Big Brother is closer to becoming a reality than ever before, especially in the UK. If you're concerned about whether you phone is being tapped, watch this video to learn about steps you can take to find out whether your phone has been bugged or not and make sure your communication remains private.

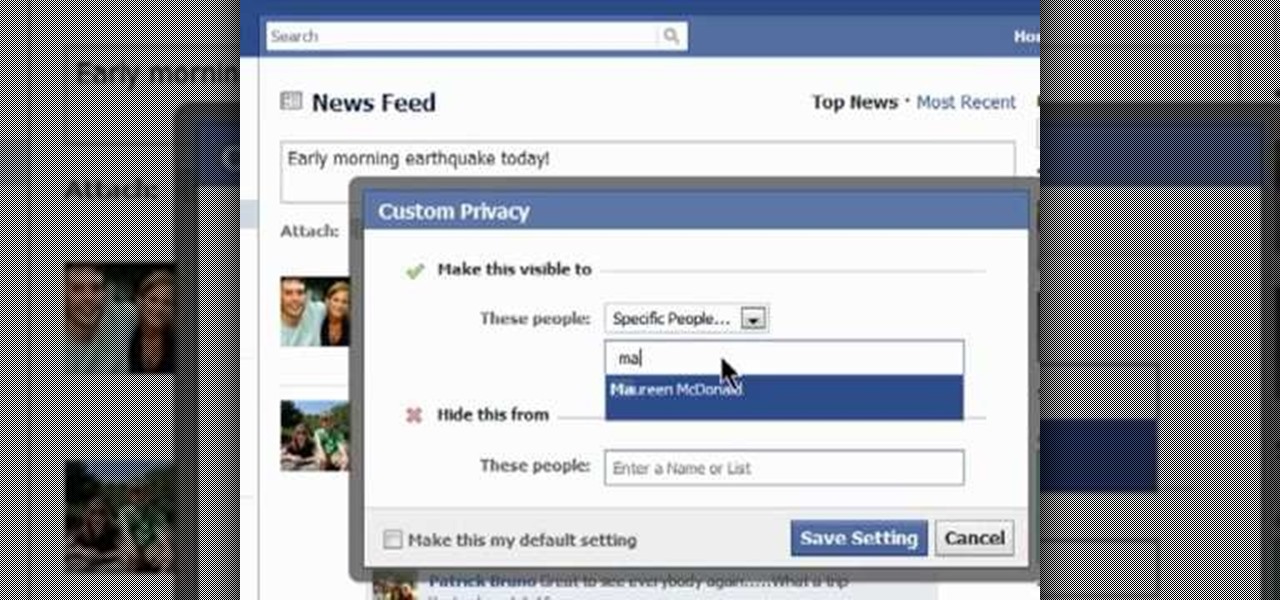
Protect your Facebook posts! This clip will show you how it's done. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to perform a particular task on Facebook, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.