Check out this basic back-to-school look that's also great for daily work and church services. It's a neutral makeup look with very little shimmer. It only takes about 5 minutes to create these beautiful eyes! Watch and learn how to apply these eyeshadows and cosmetics.
Want to receive daily, weekly or monthly updates on a subject of your choice? With Google Alerts, it's easy! So easy, in fact, that this home computing how-to from the folks at Easily can present a complete (and somewhat talky) overview of the process in just under five minutes' time. For the specifics, and to get started setting up and using Google Alerts yourself, just watch this handy how-to.
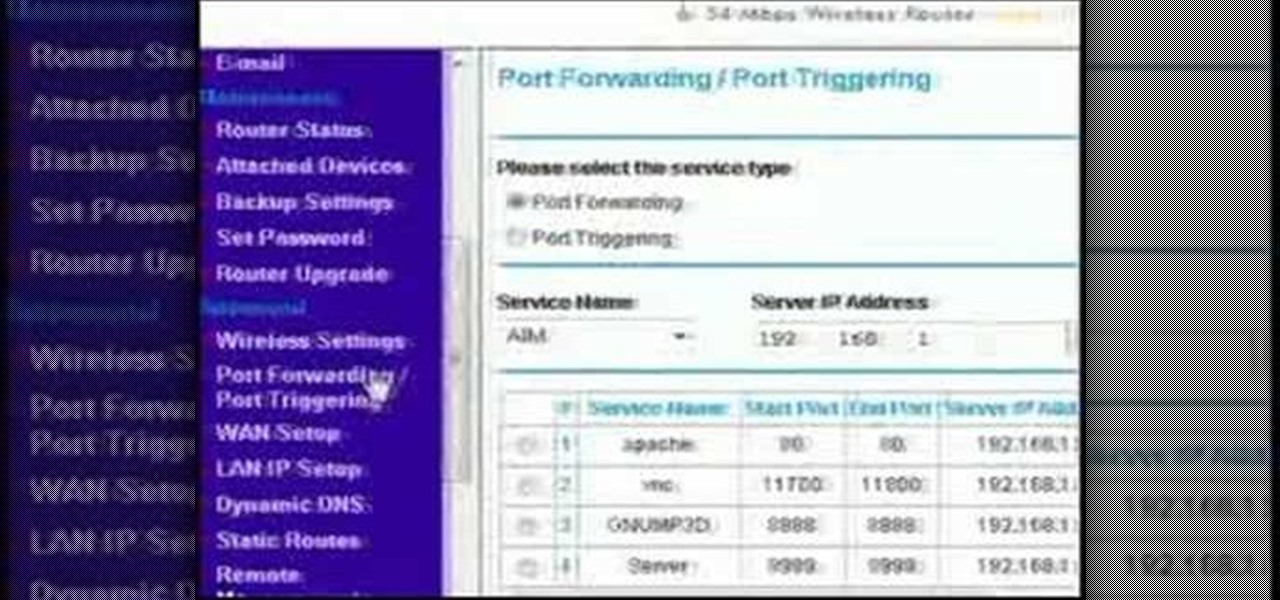
This video discusses how to bypass your router to access your server. In the search window type in CMD to open up a command prompt. Then type in ipconfig to bring up the ip configuration. You want to look for the ip address for the default gateway and the one for your computer. They should both start with 192.168. Once you find them open up internet explorer and type in the ip address for your default gateway and it should then prompt you for a user name and password. Log in and look for a po...
This tutorial will show you a super simple way to get free ringtones for your iPhone. This method will let you bypass iTunes's expensive ringtone service and create your own - anytime, from any song and for free!
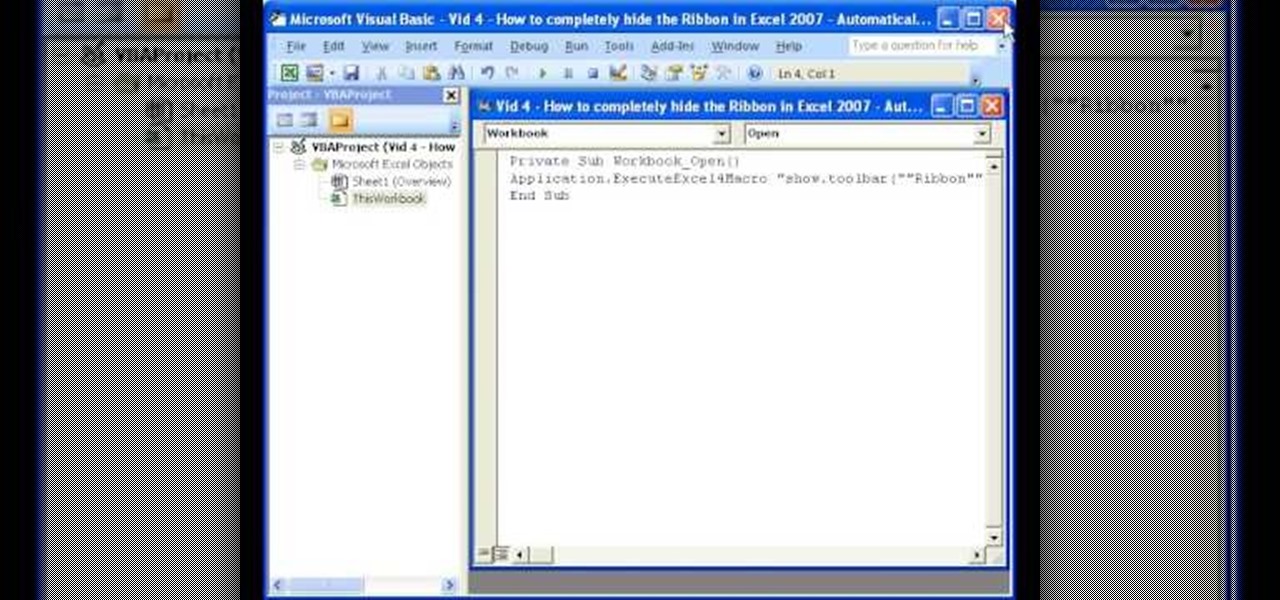
Teach Excel demonstrates how to completely hide the Ribbon menu system in Excel 2007 as soon as the workbook is opened. This will be done by writing a macro which hides the Ribbon only for the specific workbook in which the macro is implemented. Some helpful shortcuts are Ctrl+F1 which partially hides the ribbon, Alt+F11, which opens the Visual Basic screen, and Alt+F8, which opens the macros list. First, hit Alt+F11 to open the Visual Basic screen. Then double-click "This Workbook" on the le...

Your IP address is what identifies your personal computer while you are online. You may want to change your IP address for privacy, to bypass website settings, to download, or for various other reasons. This tutorial will take you through the steps you need to start surfing more anonymously.

This is a steamy part of Heavy Rain for PS3. Steamy and sexy. But this is edited for nudity, so don't worry about seeing anything you shouldn't. See how to beat Chapter 5 - On the Loose.

in this episode of Heavy Rain, you confront the Shark. Just try not to get yourself killed when he pulls out that shotgun. Then, are you going to kill him, or are you not? See how to beat Chapter 4 - The Shark.

Now that the identity of the Origami Killer has been revealed, it should be easy to find him. In this walkthrough of Heavy Rain (PS3), you'll be in the killer's apartment. See how to beat Chapter 5 - Killer's Place.

Is the real killer captured now, or is a different man? Will you leave the case or will you continue the hunt on your own? The Origami Killer may still be out there, and it's up to you to find him. See how to beat Chapter 5 - Solving the Puzzle.

In this video you are shown how to use proxies and why they are important. Proxies are useful because they shield you and make you anonymous over the internet, it also prevents websites from logging your IP address. To see how important it is to prevent this go to whatismyip.com. It will show you your IP, click on it and go to 'look up'. It will show you all the personal information that can determined from your IP address. The easiest way to proxy are VPN's, which stands for virtual private ...

The city is full of reptiles, and in Heavy Rain, the lizard is the most treacherous of all. See if the lizard can get you one step closer to solving the murder mystery of the Origami Killer. Porcelain isn't what it used to be. See how to beat Chapter 3 - The Lizard.

Butterflies are usually sweet and innocent, but not in the downpour that is Heavy Rain. In this PS3 walkthrough, see what's up with the Butterfly and if you're ever going to catch the Origami Killer. See how to beat Chapter 3 - The Butterfly.

Can't sleep? Of course you can't, not with a stage called "Sleepless NIght" in the video game Heavy Rain for the PS3. Watch a walkthrough of this level and see if you can get some zzz's, or see if you should be sleeping. See how to beat Chapter 2 - Sleepless Night.

This level of Heavy Rain has you in the Lexington Station, where hopefully you can make it through the crowd without embarrassing yourself. Watch the full video walkthrough to see what happens, and how to continue on. See how to beat Chapter 2 - Lexington Station.

Nothing can beat a father and son. Check out this Heavy Rain video walkthrough for the PS3 on "Father and Son". Do you think you're getting closer to catching the murderous Origami Killer in this level? See how to beat Chapter 1 - Father and Son.

Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

This is an Apple iPhone video tutorial that will show you how to unlock an Apple iPhone 2G or 3G for use with another mobile phone service provider other that AT&T. If you are using a Macintosh computer, you can unlock both the 2G and the 3G phones. If you're using a PC, then you can only unlock the 3G iPhone.

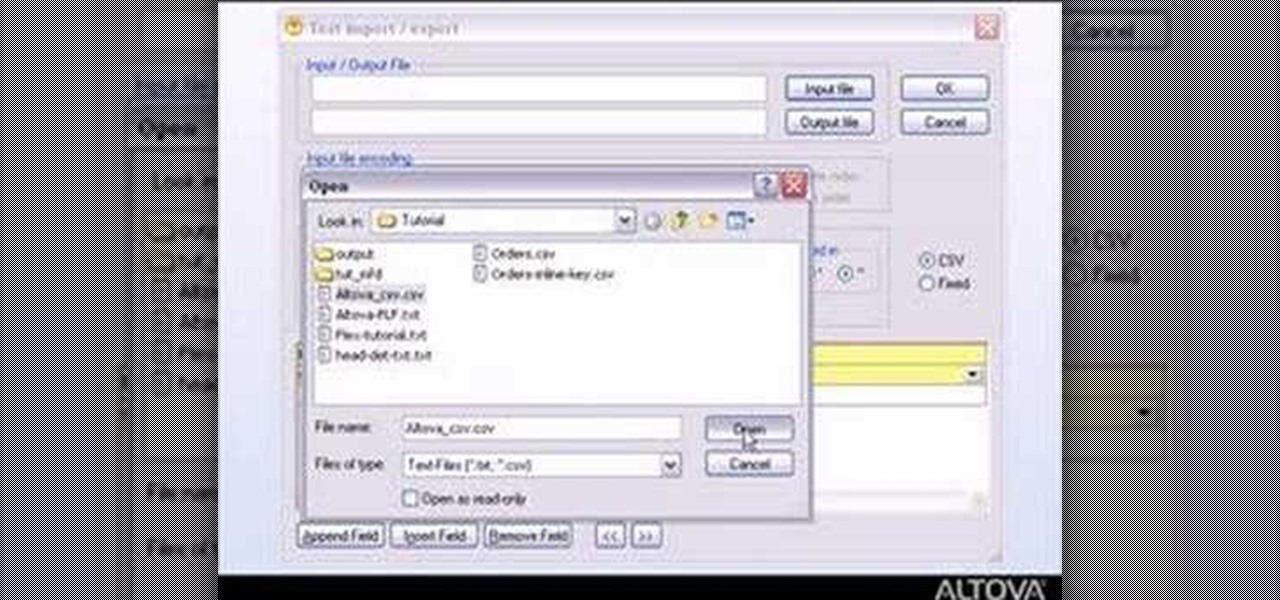
MapForce supports flat files as the source and/or target of any mapping involving XML, database, EDI, web services or other flat file data. In this how-to, you'll find instructions for mapping data from arbitrary text files (such as log files, CSV, fixed-width, and other legacy data sources) to databases and XML files.

The Prada cell phone (the LG KE850) is a unique, sophisticated and elegant mobile phone with the first complete advanced touch interface.

Watch this how-to video to learn how to get 30 days of Xbox Live Gold for free just by pretending you don't want it. Xbox Live Gold is normally a subscription service, but you can get 30 days of it for free by following the tips in this how-to video.

In this how to video you can learn to create a punk, goth, emo red Avril Lavigne inspired eyeshadow look. This makeup tutorial uses the following products:

An installer shows some tips to help remove your trialer hub so it can be serviced and then reinstall it so your wheel can be remounted.

Just some suggestions and roughly the way I handle calls. There is more than one way to do this and every call is different. Enjoy!

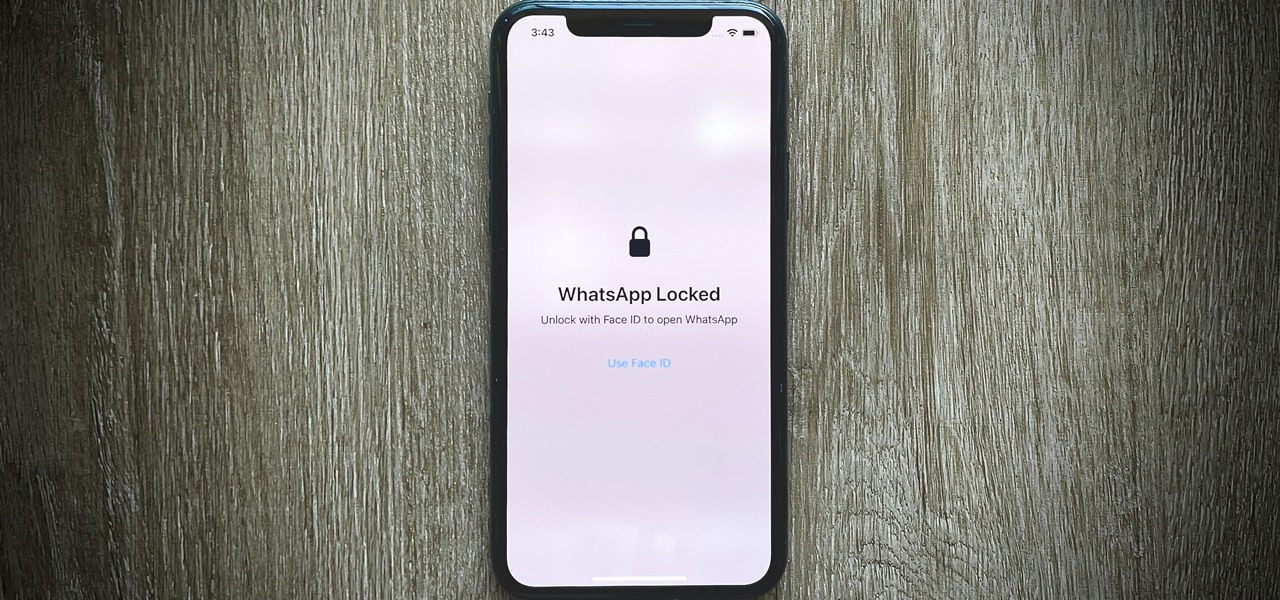
End-to-end encryption makes WhatsApp chats private and secure. However, if someone has access to your iPhone, they can easily open the app and browse through all of your personal conversations. Luckily, there's an easy way to block any would-be intruders at the gates — just lock the app behind Face ID or Touch ID.

Now that more people are working from home on unsecured networks and personal devices, hackers are having a field day accessing everything from private browsing histories to personal banking information. A virtual private network (VPN) is the first and most important line of defense when it comes to protecting all of your devices from digital intrusions, but not all VPNs are created equal.

Mobile privacy is one of the most pressing security issues in existence. Since we carry our phones with us everywhere we go, we need to ensure that we're safe from prying eyes.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

There are a number of reasons you'd want to delete your Skype account. You may have decided to move away from the app in favor of another service like WhatsApp or FaceTime, or perhaps you want to erase your account due to an online hack. Regardless of why you might want to delete your Skype account, doing so isn't quite as straightforward as it appears.

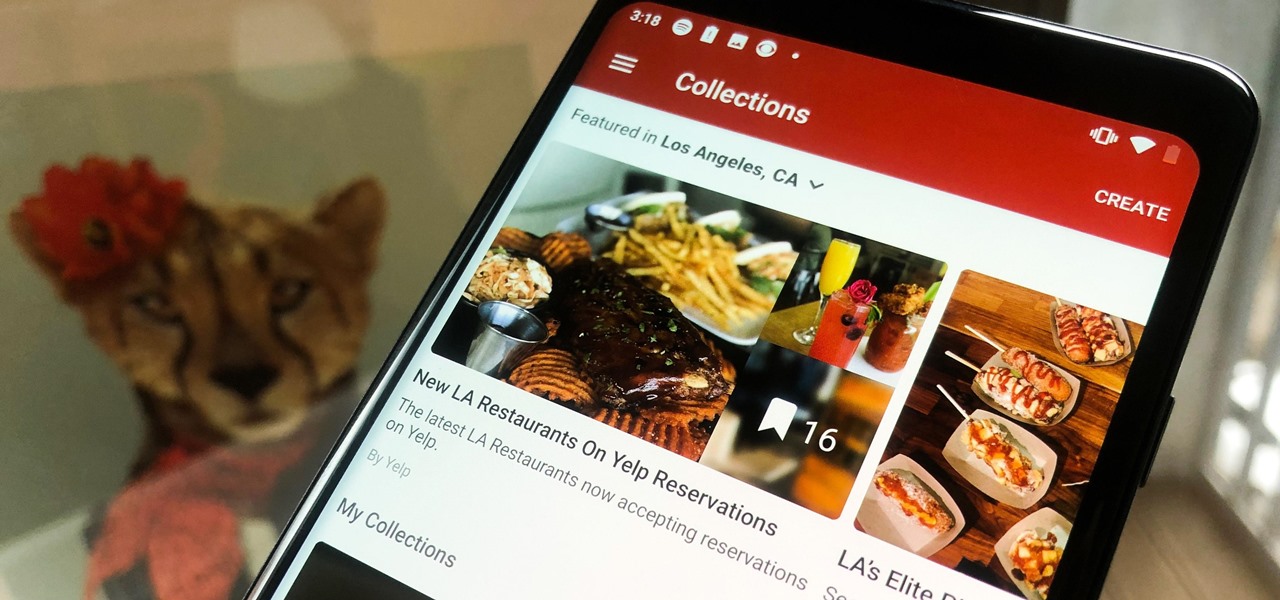
In the past, if you stumbled upon a Yelp listing you liked, you could bookmark it and check it out later on your profile. You can still take advantage of this feature in the mobile apps, but it's more refined now than it ever was thanks to Collections, a feature Yelp first added back in May 2018. You get more power over organizing, accessing, sharing, and discovering favorite businesses.

WhatsApp is the go-to messaging app for millions worldwide and its easy to see why. The app can be considered the Swiss Army Knife of texting thanks to numerous features like Group Chats and Status Stories, in addition to striking a great balance between ease of access and overall security.

Streaming movies and TV shows on phones is more popular today than ever, but what about when you're on a plane, have a limited data plan, or will be in a no-service area? You'll want to download your movies and TV shows instead. While Netflix is excellent, you can't rent or download most of the latest movies and TV series. What you need is an app that lets you do just that.

There are more than a few subscription-based movie streaming apps available for Android and iPhone, each with different benefits and varying pricing plans. Needless to say, it can get expensive fast if you sign up for multiple services because you can't decide on what's best. Hopefully, we can help you out with choosing the right video-on-demand app to spend your hard-earned dollars on.

The gig economy is thriving, and if you aren't already making money with your phone, you could be missing out on easy residual income. Some people just want extra cash, and some even manage to completely ditch the 9–5, enabling them to work at their own pace and set their own hours.

Thanks to recent reports, we now know third-party apps have a lot more access to our Gmail than we may have initially thought. In fact, these third-party apps have the ability to read our emails, not because these companies are necessarily shady, but because we agreed to it. Luckily, there's a way to view which apps have this access, as well as a way to boot those apps from your Gmail entirely.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

Chrome is the browser of choice for millions of iPhone and Android users, largely thanks to its user-friendly interface and native Google support. But with concerns over sharing private information with massive companies growing, many people are starting to want a little less Google integration in Chrome.

When you leave your iPhone on a table or anywhere within somebody else's eyeshot, a private message may pop up on your lock screen that could be read by anyone who sees it. But there's a way to keep others from reading your possibly sensitive text messages and emails without giving up the convenience of lock screen notifications entirely.