When a photo or video is just too sensitive to leave laying around in your Photos app, you'll want to either delete it for good or hide it away in safe, secure location on your iPhone. As for the latter, Apple actually has a few tools available to make photos and videos hidden — even password-protected — on your iPhone.

Since starting as a simple messenger with self-destructing pictures, Snapchat has grown into a full-fledged social media platform. As features were added, new permissions were requested, and we're all probably guilty of just tapping "OK" to try out the latest and greatest. But at some point, it's a good idea to review your settings to see what personal data you're putting out there for all to see.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

The cosmetics industry faced a rude awakening on Friday as beauty behemoth L'Oréal gobbled up ModiFace, one of the leading providers of augmented reality technology to the cosmetics industry (price details for the acquisition were not disclosed).

Apple has tools built into iOS to help parents monitor the iPhone habits of their children. However, those same tools can be used by everyday iPhone owners to both hide apps they don't care about, as well as restrict features they don't need or that infringe on privacy. Whether you fit into one category or the other, all iPhone users can benefit from the "Restrictions" feature.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

A survey by ABI Research revealed that only 25 percent of businesses have implemented augmented reality technology in some form or fashion.

Paying for street parking in New York City just got so much easier. Instead of searching for loose change or hoping you didn't forget your wallet, you can use a device you always have with you: your phone.

Wegmans recently partnered with Instacart, an online grocery-delivery app, to bring your groceries right to you. The collaboration will begin in the suburbs around Washington, DC, and Wegmans plans to expand to other areas later on.

The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels.

Nokia, the Finnish telecommunications company, is about to shake things up a bit after its networks sales in the final quarter of last year declined 14% compared to sales in 2015.

Responding to the rapid emergence of dangerous pathogens around the world, a new initiative to prevent or contain pandemics was announced in Davos, Switzerland, yesterday. If you ever worried that a highly contagious pathogen could take down your community, or the country, this news is for you.

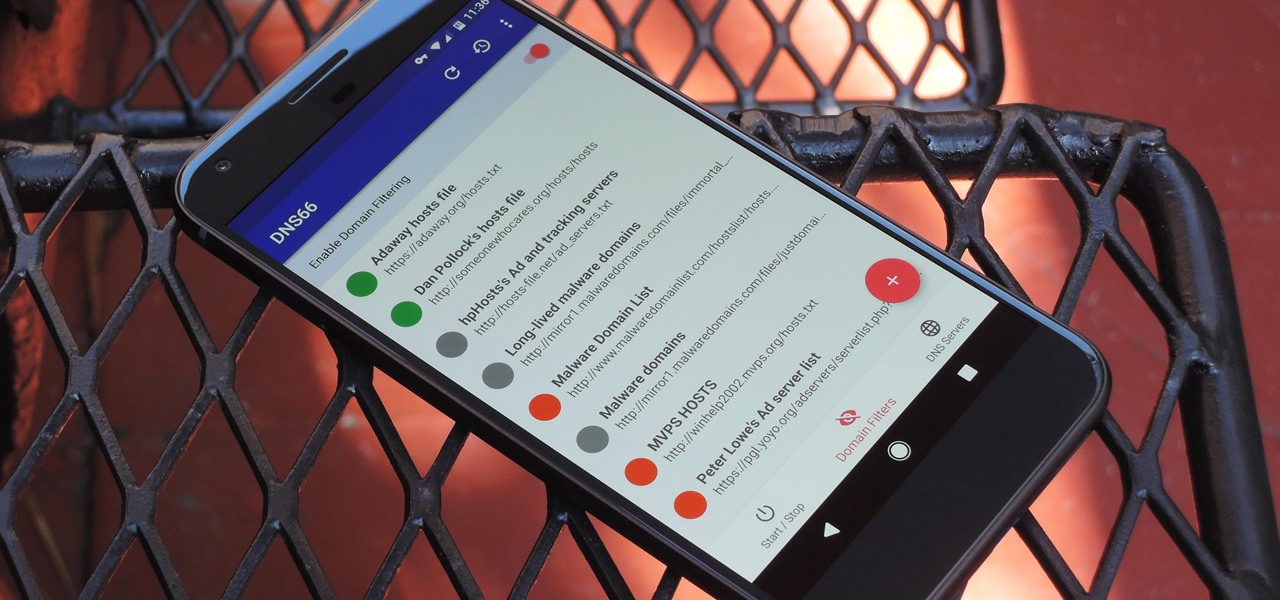
If you're in the market for a non-root ad-blocker, developer Julian Klode has an app that you'll definitely want to check out. It uses Android's VPN system in a similar manner to alternative apps like NetGuard and AdGuard, but it's got a new twist that should save lots of battery life in the process.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

The telecommunications industry has come a long way since Ma Bell opened the first telephone exchange in the late 1800s. With the advent of fiber optics and wireless broadband technology, we no longer have a need for a dedicated phone connection, as today's data networks can carry much more than a simple voice conversation.

As is the case with most software updates, Android 5.0 brought changes that were viewed by users as somewhat positive and somewhat negative. This generally happens because we're accustomed to the old way of doing things, and changes, no matter how useful, can slow us down.

One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

The design of iOS 7 has its lovers and haters, and if you're an Android user who just happens to love it, there are plenty of ways to make your device feel more Apple-y.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

When was the last time you bought a CD? Most of us listen to music through a number of digital channels—MP3s, Internet streaming services like Pandora and Spotify, and satellite radio, to name just a few.

Play on your own private server on World of Warcraft, be sure to follow the instructions to the letter!

Unlocking the iPhone can save you a ton of money and irritation by getting you off AT&T and onto a better service provider. One way to do that is flashing the baseband to one that works on the iPad, and this video will show you how to do using Redsn0w that, provided you're working from a iOS 4.2.1 / 4.1 equipped iPhone 3G / 3GS on baseband 5.14 or 5.15 (about to be 6.15 when you're done).

Combination locks are a major part of life for people High School, the Armed Services, and enough other places to make this video very useful to a lot of people. It will show you how to open any twisting combination lock (like a Masterlock) with using math or any other sophisticated skills or tools. All you need is a sharp knife and your fingers. Now you won't have to wonder whether Person X has your picture up in their locker or not anymore.

Apple really ate some mud in the media over the iPhone 4's blatant antenna problems, but they're finally trying to make good by offering free problem-solving bumper cases to all of their iPhone 4 customers. Keeping true to their "There's an App for that" slogan, they've made an App that allows you to order the free bumper case that they're promised you right from you iPhone. If you have service that is! This video will show you how to use it and get what you deserve from Apple.

At Daily Mugshots, you will be able to save your own mug shot. The first thing that you will have to do is sign up for an account. You will need a Flash Player in order to use this site. After you have your account set up, you can take a picture from your computer. You can also upload pictures that you have taken elsewhere. When you save your picture, you will have to wait until it is finished processing. When the blue bar is filled, then it will be stored in your mug show.

In this video from rscp1050 we learn how to SSH into a jailbroken ipod touch or iphone. First go into Cydia and search for SSH. You need to download OpenSSH. Then also install Toggle SSH. After installed, restart the iphone. Now on your computer, download WinSCP. Once installed, open it. Type in your IP address which can be found by going to your settings on your iphone. Click wifi, and click the blue arrow next to your network. There is your IP address. Then, User name is root. Password is a...

1. Describes how to setup a VPN connection on Windows XP. 2. Goto Start-> Control Panel-> Network connections.

Isn't it annoying when you want to check your Facebook or MySpace but you are at school and hit a big giant Websense blocker? Well, if you are stuck in a library or somewhere else where there are filters on your surf-ability, check out this tutorial for a useful hack.

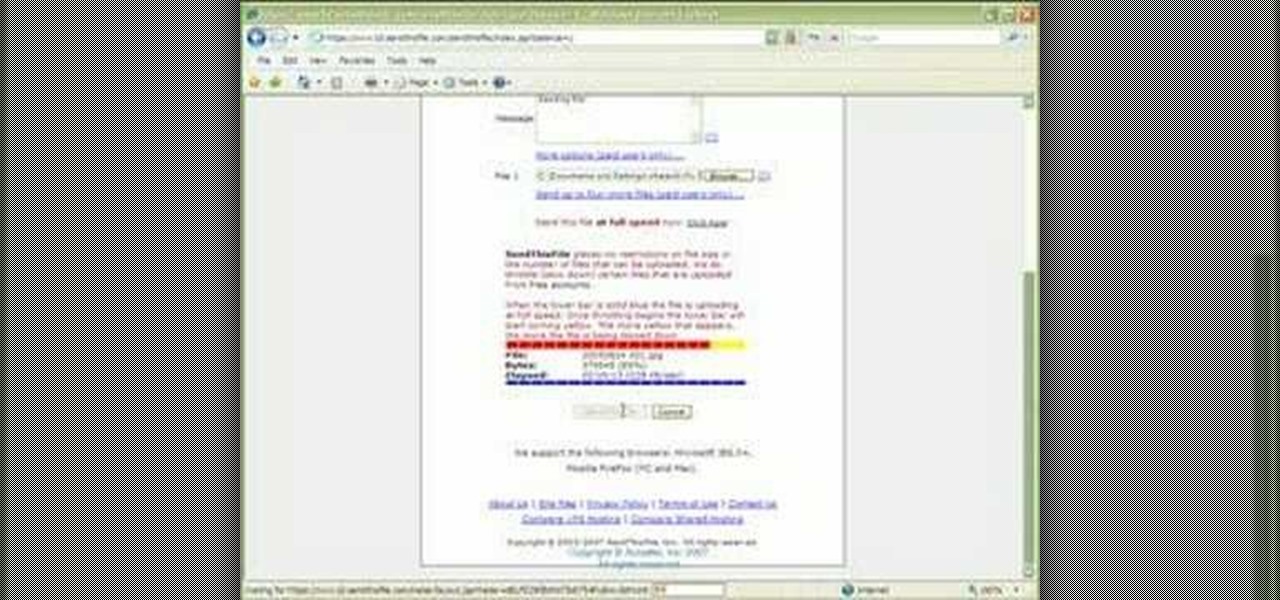
1. Type in WWW.sendthisfile.com in the web toolbar and press enter 2. Click on Register found on the top right side

Now more than ever, people everywhere are suffering from bad credit. Credit is important. You need it to take out loans, buy a house, rent an apartment, get a car, almost anything! Check out this two part video, presented by Daniel Medina from United Credit Education Services, and listen along as he offers you tips on how to improve your credit - even in a recession. This helpful and informative video can start you on the right track to financial stability, no matter what the circumstances.

This video illustrates the method of Downgrading the iPhone 3Gs firmware from version 3.1.3 to version 3.1.2. The process is composed of the following steps -Step 1Download the iPhone 3Gs firmware version 3.1.2 from the internet. You can find this on apple's official site or you can get this from a customer service center.Step 2Upload the firmware files in the root of your iPhone's internal phone memory. Create a folder named "firmware v312" and add the firmware files in it.Step 3Access this ...

Link shortening is the process of cleaning up the URL link which is long and converting it into a short URL. You can use bit.ly to do link shortening. Using bit.ly you can not only shorten the link but also track the users who are using those links. To use this service go to the http://www.bit.ly website. There in the home page you are provided with a text box. Enter your long link in the text box and submit it. Now the website converts the long URL and provides you with a short link which ca...

Saving money during this tough economic period is more important than ever, especially when it comes to servicing your vehicle. So in this 2 part video tutorial, you'll find out one way you can keep your wallet fat, by learning how to change the oil to your Vespa scooter.

You need four persons to play doubles. One person shall be on the forehand side while the other person shall be on the backhand side. Same thing for applies for the opposite team. You need to be in your side of the court. Either you should be on the right or the left side of your court. However you have the option to move or switch sides at any time. When you are doing the service then your partner must stand in the service box with his back towards the back wall. The opposite team must stand...

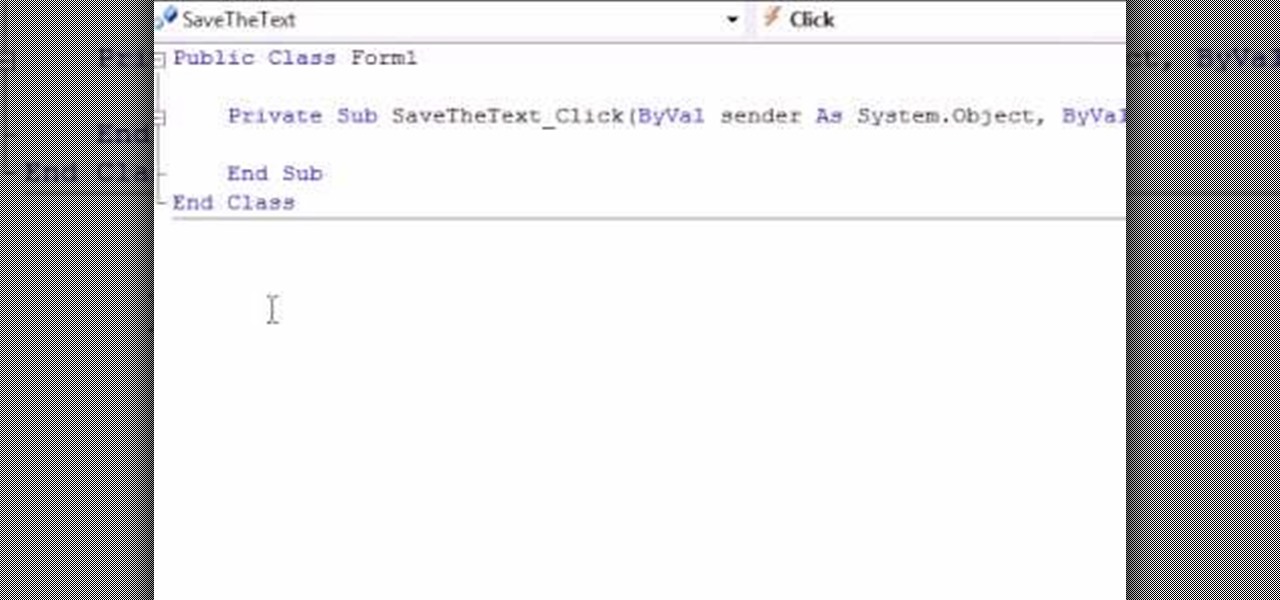
This video takes us through the process of using the Stream Writer and the Save File Dialog Step 1

Need to make an newsletter for your company or business? It's really not that hard to do, if you know a little bit about HTML coding. Ryan Quintal and the Email Dance House sits you down and shows you how easy it is to make a custom HTML email from design to Constant Contact.