If you're looking to improve your browsing experience, then a VPN is the right way to go. If you're tired of censored or geographically blocked sites and wary of companies selling your data, then a good VPN can be your answer to a problem that limits every aspect of your experience online.

It's open season on Zoom, the video conferencing platform that has grown in popularity during the COVID-19 pandemic but has come under fire due to privacy issues.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

The latest business move by Magic Leap could result in a significant boost to its spatial computing platform's performance and headset design.

Whichever web browser you use, each comes with a way to surf the net "secretly." While nothing on the internet is truly anonymous, private browsing modes can help keep your movements hidden from those who might have access to your data. The "secret mode" for the Samsung Internet app goes a step further on Android, by locking your private browsing behind a unique password.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

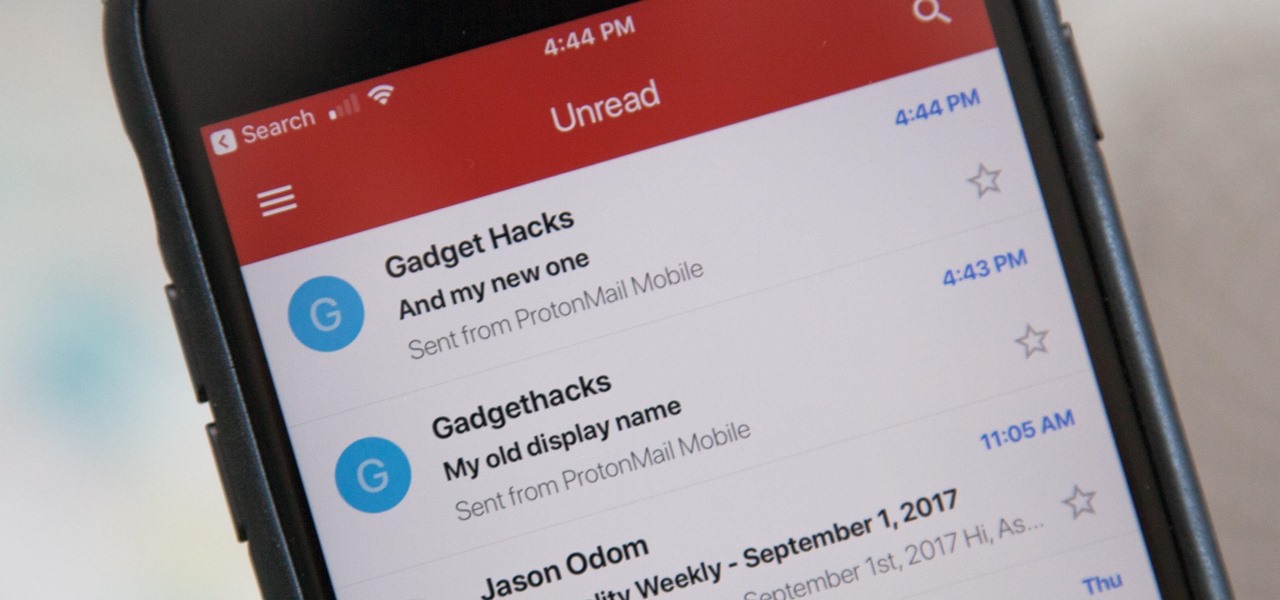
Your display name in ProtonMail is what email recipients will see when they first receive your message in ProtonMail, Gmail, or another email provider. You can choose this name when you first set up your ProtonMail account, but it can also be set up after the fact if you skipped that step.

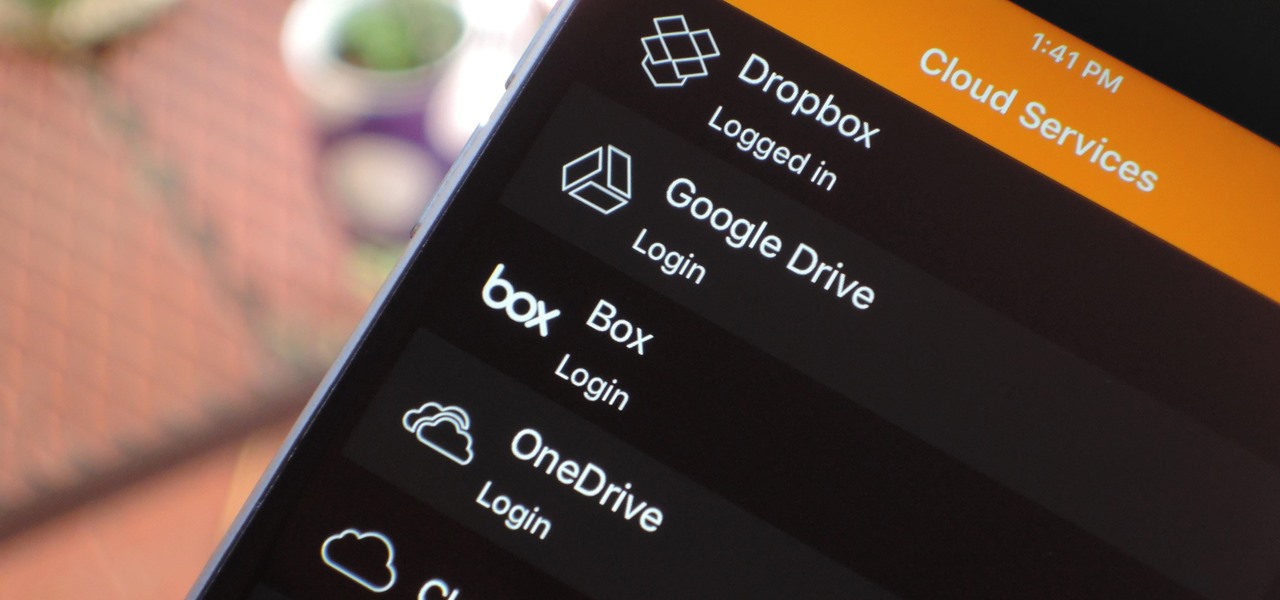
If you have movies and videos stored on Box, Google Drive, Dropbox, or OneDrive, you should definitely be using the VLC app for iPhone. After setting a few things up, VLC will let you stream videos directly from any of these services with a proper video player UI, complete with gesture controls.

Over the past week, we are seeing more companies capitalizing on services leveraging augmented reality. One company secured funding to expand their service, while two other companies grow its own services through acquisition.

Signal, the encrypted messaging app, has seen 1.4 million downloads in just the first quarter of 2017—roughly twice the downloads it received in the same period last year. Rani Molla at Recode attributes this to Donald Trump's inauguration, as the private messaging service saw a 40% increase in US downloads between Election Day and the end of the first quarter of 2017.

It seems that Facebook doesn't take rejection lightly. After being denied for a $3 billion buyout of Snapchat, Facebook-owned Instagram has updated their popular photo-sharing service with Instagram Direct—a new feature that allows users to send private photos/videos.

You'd think the ability to block calls from certain numbers would be built in to most phones by now, but that's certainly not the case with the iPhone.

Make sure your private documents are completely secure. This episode by Tinkernut deals with not only encrypting your files, but also hiding them in a hidden volume.

The convenience of storing things on the cloud can definitely make life easier, but if you're storing sensitive files, it could be a total disaster if anyone hacked your account. Some encryption services can be expensive, but if you just need it for personal use, there are some really great ones that don't cost anything. Here are three programs that let you encrypt your cloud storage for free. BoxCryptor

The big question this week would be the controversial Obamacare mandate. And heres the answer: Yes. Obamacare passes Congress' filters and is now an official OK. Texas college hacks drone in front of DHS — RT.

The people of Iceland forced their corrupt government to resign. A public assembly was created to rewrite the constitution.

If you want to increase your privacy and prevent iPhone apps from gaining access to data containing your location, take a look at this tutorial on turning off the location services in the settings menu on Apple's iPhone 3G devices and above.

To test how fast your internet speed is an intermediate level skill. Start by picking an internet speed test. You can use Google or another search engine to find one. A service that is recommended in the video is DSLreports. This site does not require you to know a lot of information about your service. To test your speed start by picking a city that is near to you. Then shut down all tabs and every application that you have running. It's important to do this on every computer on your home ne...

In this how-to from Household Hacker, we learn of a number of free proxy services that make getting around your school's Internet filter software a breeze. For all of the details, and to start accessing and using all of your favorite websites when at school, watch this video guide.

You keep all kinds of important and sensitive information and data on your computer, and if your hard drives crashes, you're done for… unless you've backed it up. CNET has some "Insider Secrets" on how you can backup your system with an external hard drive, network-attached storage, and online services.

Google Voice is the newest release from the experts at Google. Google Voice is a low-cost Internet phone service that redirects calls to your home phone and works over your WiFi connection. This service is very exciting and useful for those that are looking to save some money on long distance. Google Voice was in limited use for a while and is now available to everyone, so check out this clip and learn how to use it!

This video demonstrates how to fix the batter length problem on a jailbroken iPod. First, make sure that you have a Wi-Fi connection so you could download the necessary files. Turn your iPod Touch on and locate the Installer icon. Wait until the installer program loads. Then, on the bottom portion of the screen, select the icon Install. In the Packages section, scroll all the way down to letter S and look for Services. Select it and install it. After the installation completes, go back to hom...

Is the proper term nudists or naturalists? Doesn't seem to be too much of a difference, because when it all boils down, they're both still butt-naked on the beach. Nude beaches are fascinating places for the adventurous spirit, but unless you’re an old-time nudist, you probably have questions about the proper way to behave on a nude beach. Well, we’ve got the answers.

Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

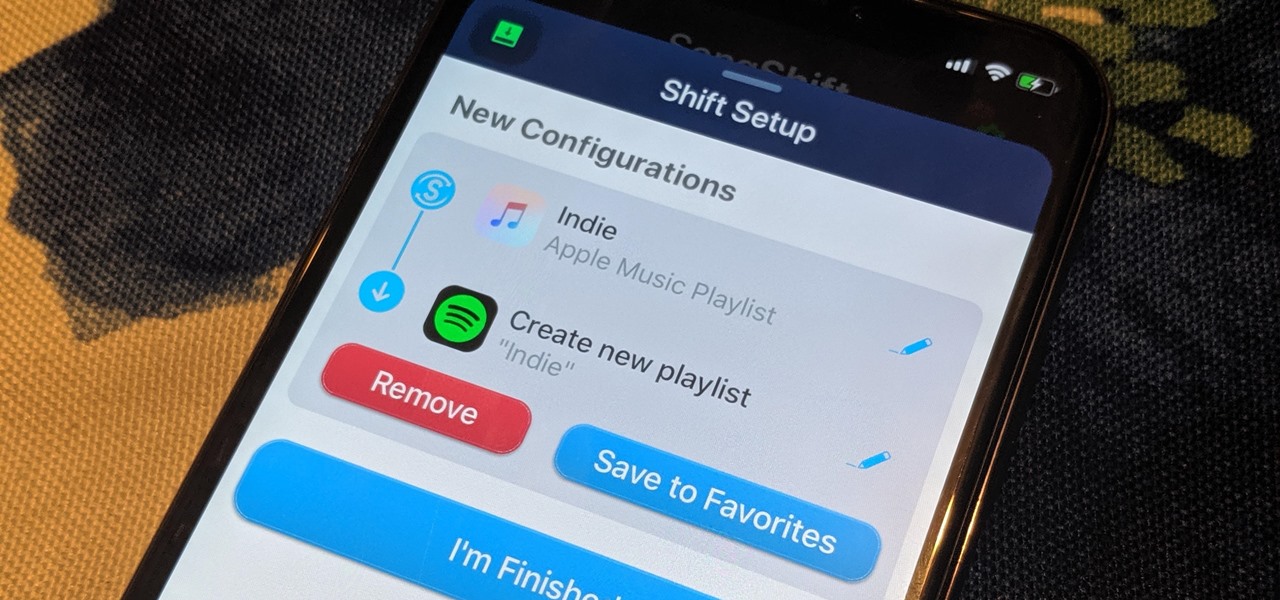
Switching from one popular music streaming service to another shouldn't have to be a hassle, but it is if you want to transfer all your favorite music over. No popular service offers a built-in feature to export or import playlists, so if you want to move your favorite Apple Music playlists over to Spotify, you'll have to use a third-party service.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

After a district judge approved the $85 billion merger between AT&T and Time Warner, we knew AT&T would be quick to reap the rewards of capturing Time Warner's media properties. Today, we get our first look at this with two cellular plans from AT&T. What makes these plans unique is they include a new cord-cutting service called WatchTV.

When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

While it's easy enough to make yourself invisible on Snap Map, nothing is quite as private as not having a Snapchat account at all. Whether you're concerned about your privacy or you simply never signed up for the social media platform, Snapchat's web-based map is an easy way to check in on what's happening in your area and beyond.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

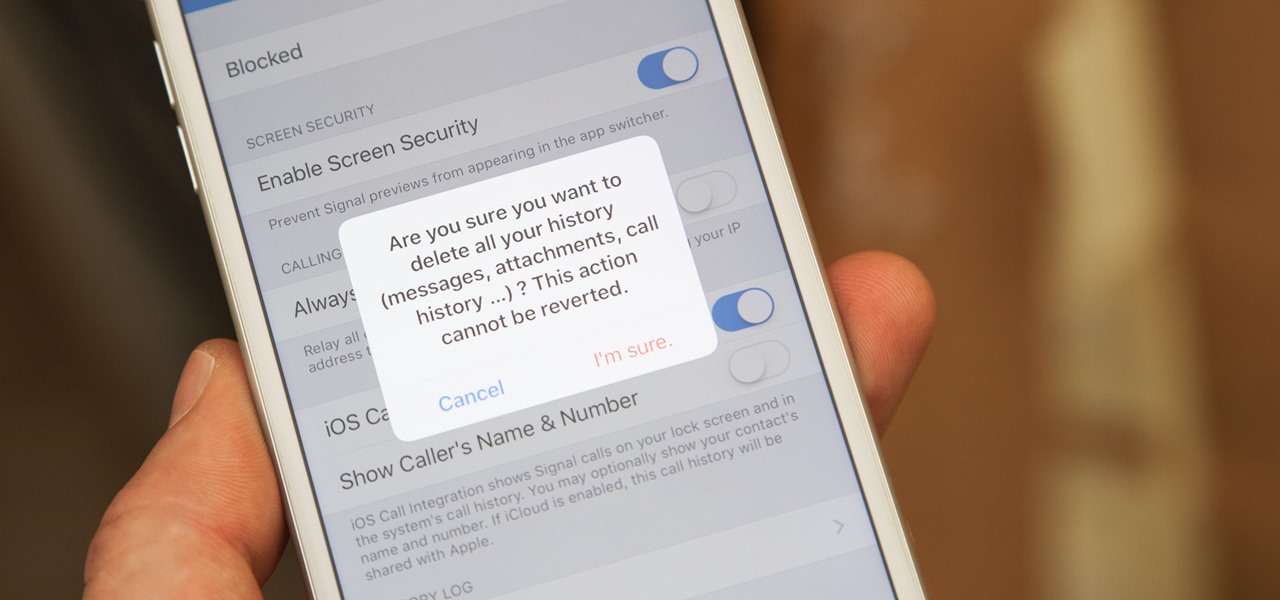
If thieves, hackers, law enforcement, or other would-be enemies should ever gain entry to your smartphone, they could also access conversations you've had in Signal Private Messenger. To better secure your encrypted communications, you can password-protect the whole app and its contents — but only on Android. Even then, it's necessary to perform data deletion on a periodic basis, if not immediately.

The common thread between this week's Brief Reality stories is that augmented reality is beginning to prove its worth as a technology that improves workflows and processes. From customer service to healthcare to manufacturing, augmented reality is helping companies improve productivity.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

I wrote a python script that allows you to easily ask what service runs on a specific port and vice-versa. Now, I am sure that such a program already exists on our lovely linux OS's, but... I didn't think of that before I started, and haven't found it yet. So if you haven't found it yet either, maybe you'll find this of some use. It's just called getport. If I have a port number, and want to know what services run on that port, I do: