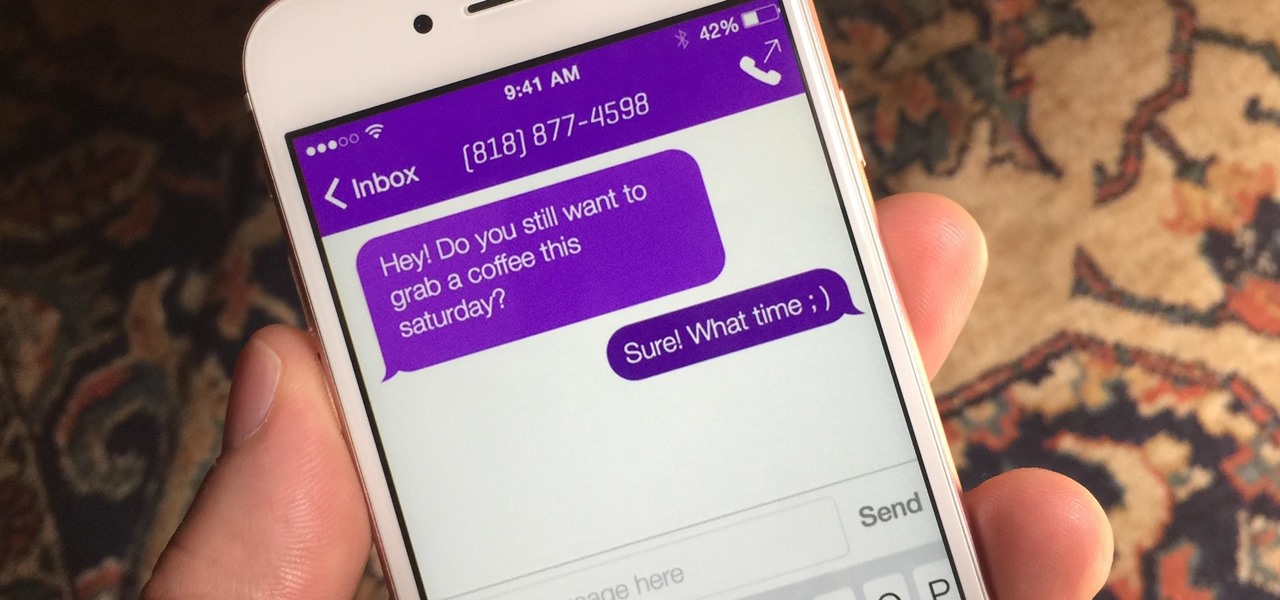
One of the most disappointing experiences ever is when you save all your money for a really expensive gadget—and then break it. Whether it happens the day you buy it, or years later, it's always frustrating.

Most of the spam messages are commercial advertisements, phishing websites and get rich quickly messages that asks users to provide personal details and other confidential information.Spam filters in Gmail prevent its users from these spam messages and restrict them to enter in user’s Gmail inbox.Generally, it acts like a firewall between spam messages and Gmail Inbox.Gmail filters detect the sender’s email address and accordingly send the received messages in Inbox or Spam folder.

Ever been halfway to work or school and suddenly remembered you forgot to log off your computer? A lot of people are constantly logged in to email and social media accounts, so if you have a mischievous roommate or sibling, this situation could be disastrous. That's where TweetMyPC comes in—it's a free Windows application that lets you send commands to your computer just by tweeting. Image by Twittermania

Got an upset stomach or a little heartburn? America's favorite pink pill will cure it right up. But did you know that there's actually metal hiding in those chewable Pepto-Bismol tablets? Yes, metal. Technically, it's a poor metal, but metal's metal, right? Well, we do tend to eat a lot of iron in our diets, because it carries oxygen throughout our bodies, so consuming metallic minerals isn't anything abnormal. But you'd never think that Pepto-Bismol is actually made up of metal.

Riding your bicycle at night is dangerous on busy streets, especially if you've got no bike lights. In most states, it's illegal to ride your bike at night without any lights because drivers on the road won't be able to see you until it's too late. Plus, how is anybody going to notice your sweet ride without a little illumination?

Those new Nexus 7's sure are nice. Unfortunately, a number of those shiny new tablets have a manufacturing issue that makes the screen uneven with the bezel. Google's solution is to have you send it back in, but why waste your time considering the problem can be fixed by simply adjusting a single screw. All you need to perform the adjustment is a guitar pick or coin, and a very small Phillips screwdriver. Also note, opening up your tablet will most likely void your warranty, so consider that ...

The big question this week would be the controversial Obamacare mandate. And heres the answer: Yes. Obamacare passes Congress' filters and is now an official OK. Texas college hacks drone in front of DHS — RT.

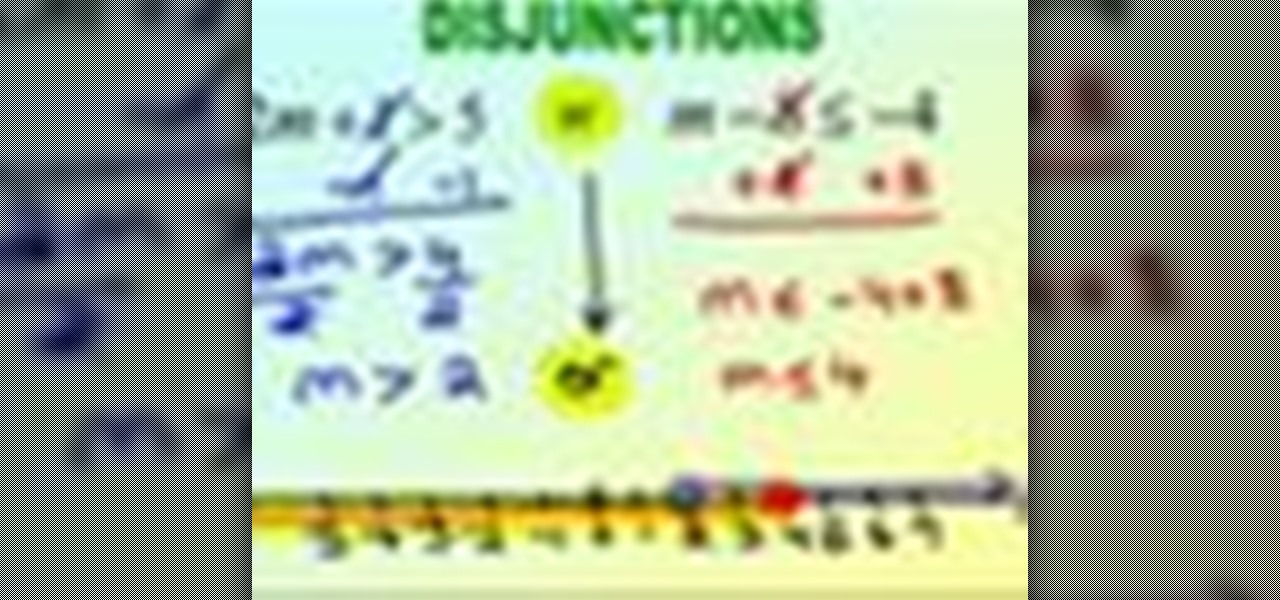
In this math lesson, you will learn how to solve compound inequality problems. A compound inequality is a combination of two inequalities joined together by the words “and” or “or”.

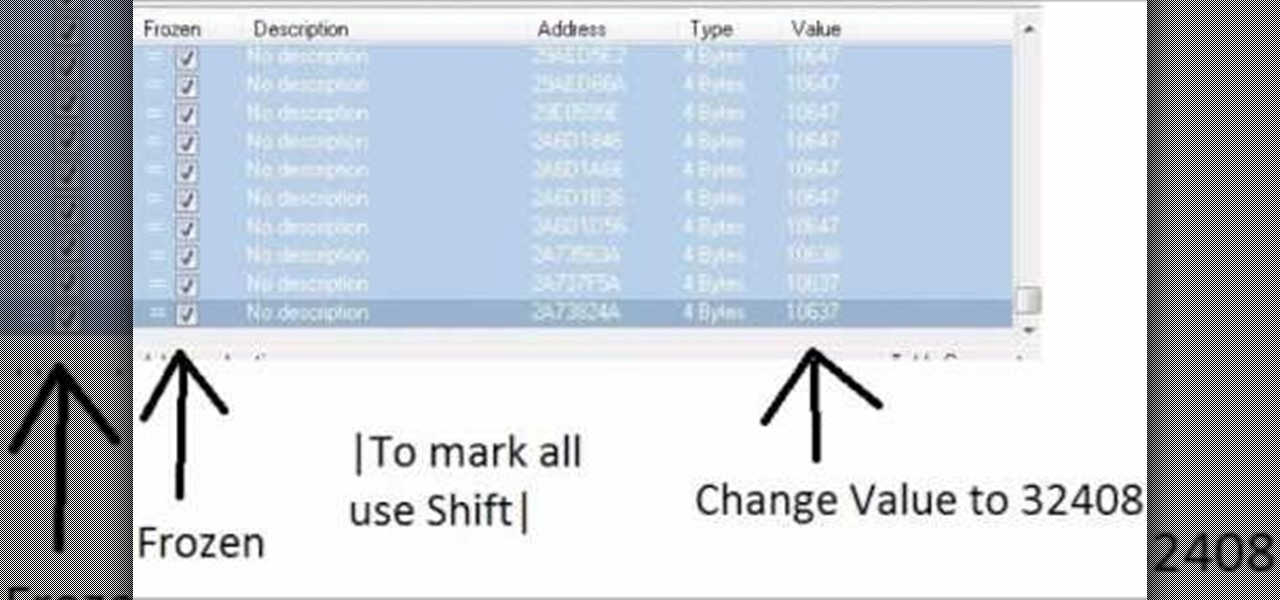
Increase your damage output in World of Warcraft! This tutorial won't work on all servers, and is better on private servers than public. All you need is Cheat Engine - buy some mundane items, and then use the program to turn them into rarer, better items.

To make instant hot ice or sodium acetate, first pour two jugs of vinegar minus one cup into a large pot. Then, slowly add baking soda to the mixture and stir it. When the vinegar and baking soda no longer react, stop adding baking soda. Next, add the rest of the vinegar to the pot. Boil half of the solution off and cool it down to room temperature. For better filtering, add charcoal to the mixture. Filter out the charcoal with a wire sifter. Heat up the solution again and filter it through c...

How to summon Illidan in World of Warcraft. This only works on a private server.

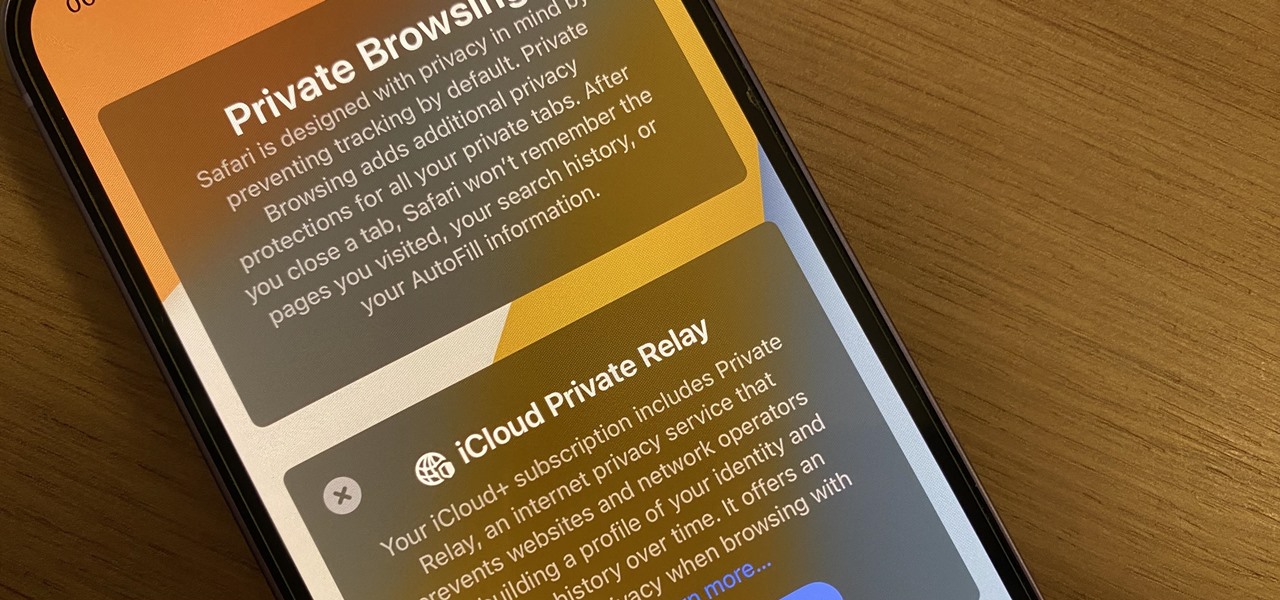
Safari's massive upgrade in Apple's latest iPhone software update includes new features you won't find in any other web browsers on iOS, from better ways to stay organized to enhanced security and further privacy protections.

Every video you like on TikTok, whether it's a stranger performing a series of choreographed movements or a celebrity showing off their new workout, is saved to your profile. If you want to watch your liked videos at any time in the future, you can easily do so from your profile — but so can everyone else.

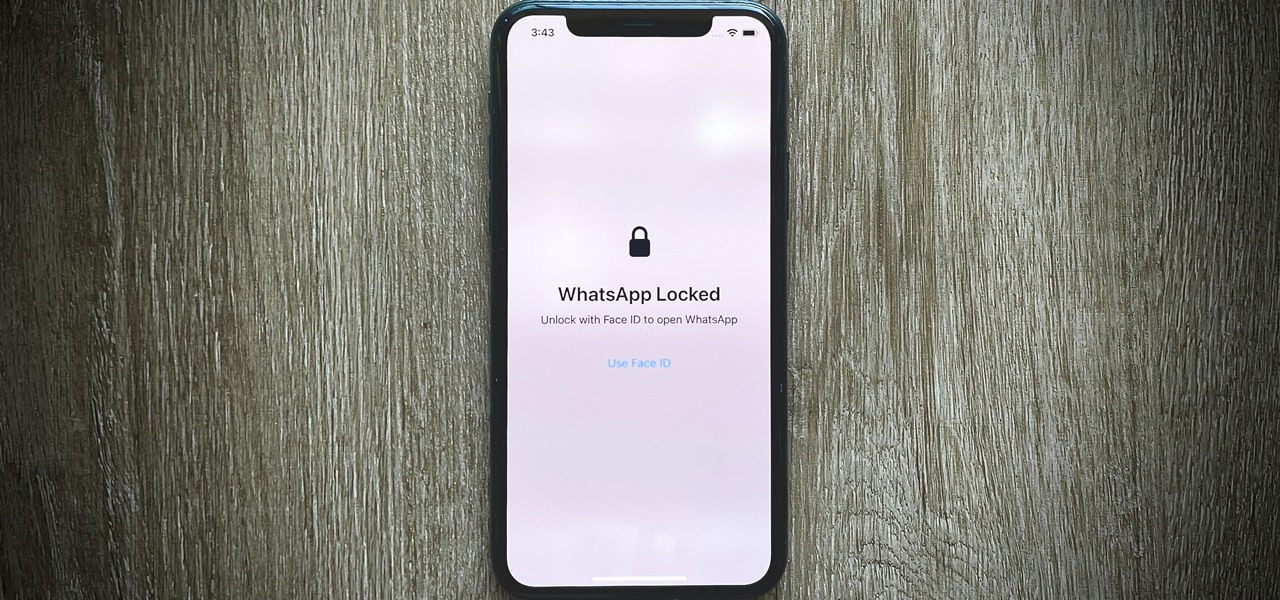
End-to-end encryption makes WhatsApp chats private and secure. However, if someone has access to your iPhone, they can easily open the app and browse through all of your personal conversations. Luckily, there's an easy way to block any would-be intruders at the gates — just lock the app behind Face ID or Touch ID.

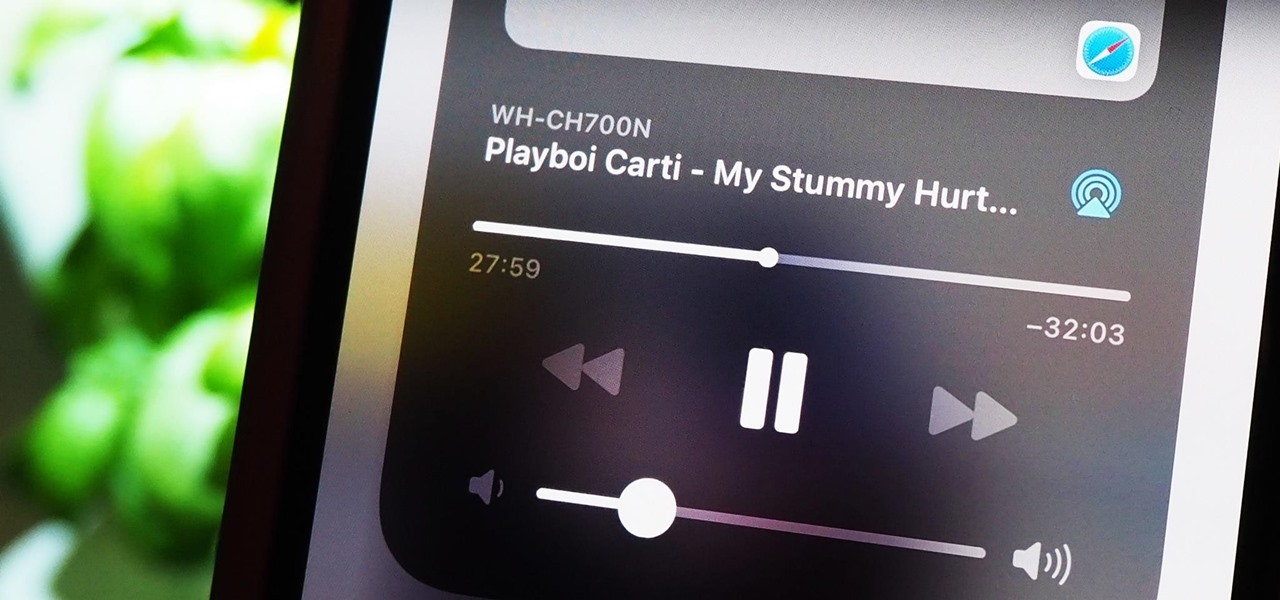
It's pretty clear with all of the annoying "Get YouTube Premium" pop-ups that litter the YouTube app that Google really wants you to pay for its Premium membership tier. That's why you'll see that "Get background play with YouTube Premium" ad after closing YouTube with a video playing — even in iOS 14 which supports Picture in Picture playback. But there are workarounds for background listening on iPhone.

Now that more people are working from home on unsecured networks and personal devices, hackers are having a field day accessing everything from private browsing histories to personal banking information. A virtual private network (VPN) is the first and most important line of defense when it comes to protecting all of your devices from digital intrusions, but not all VPNs are created equal.

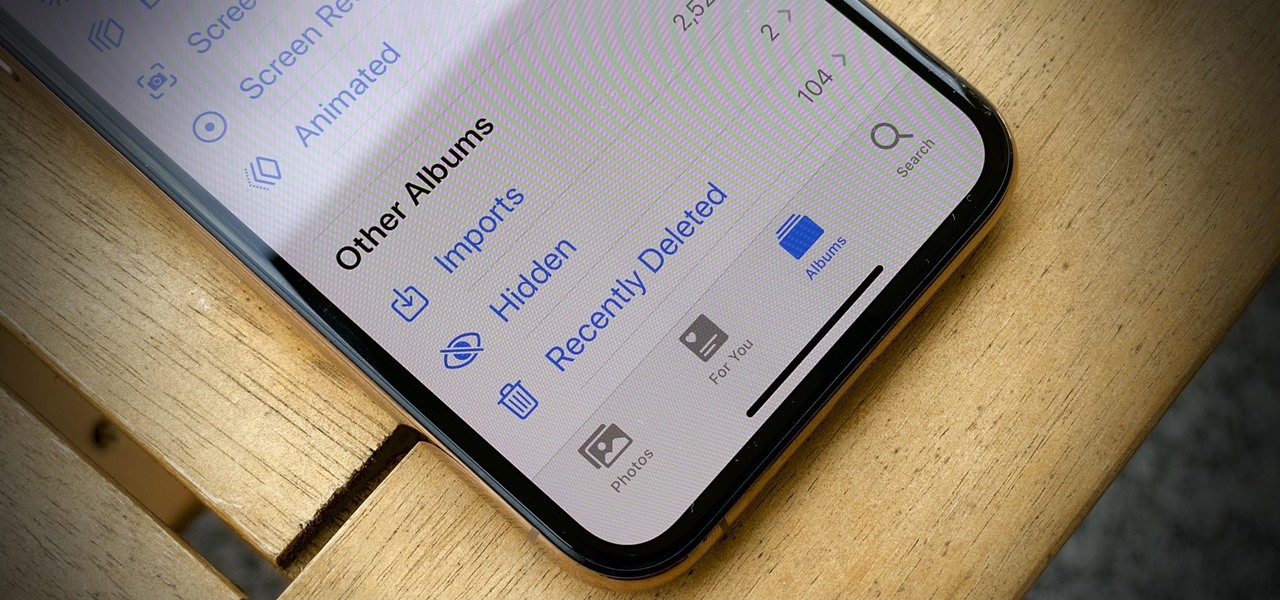
The "Hidden" album on your iPhone has always had one problem — it was never truly hidden. Since iOS 10, when the feature was introduced in the Photos app, any image or video that you conceal in the private folder could be seen by anyone with access to your unlocked device. Finally, that has changed.

Mobile privacy is one of the most pressing security issues in existence. Since we carry our phones with us everywhere we go, we need to ensure that we're safe from prying eyes.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Throwaway phones aren't just for seedy criminals and spies—they can be useful for many everyday situations.

Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.

When it comes to security, there are usually only a handful of things that you want protected from prying eyes on your iPhone—private photos, scandalous videos, and important text, such as credit card and social security numbers.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Many people wrestle with their ugly scars and birthmarks every day. These are usually quite difficult and expensive to remove, but there is another solution: cover them with a tattoo! Watch this video for tips on getting some ink done to cover a scar or birthmark.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to bizarrely merge photos in Photoshop.

Have you ever wanted to go into another user's account on your computer but had trouble finding the energy to log out, then log out, only to log back into your own account? Well, here's your solution: XNest will let you log in to another user's account from your account in a virtual way. It's very simple to set up and may just help you with your virtual account crisis!

Check out this video tutorial on how to Solve a ten digit number math problem. This video will show you the key to solving the puzzle to find a 10 digit number, such that 10 digits are divisible by 10, and the first 9 are divisible by 9, and so on.

Check out this video to learn how to solve the 20-ball pyramid puzzle. There is no sound in this video.

This is the solution to the notorious 3x3 Soma Cube puzzle. Well, there's one mistake -- can you spot it?

Ever had a picture cube that you just couldn't fix the middles for? If you already understand the Rubik's Cube, then watch these two videos, if not, then watch something else, or read the "7 Step Solution Guide."

Smudges ruining otherwise perfect pictures? Patrick, from Tekzilla, has a solution for cleaning your camera lenses.

This video series is full of 16 videos of 16 levels of puzzle-mania for the Kaboom Desert puzzle piece in Eets, the addicting 2D puzzle game. If you've played Eets (Hunger. It's emotional.) before, but not this piece of the jigsaw puzzle, then sit back and see the solutions in this walkthrough.

Graffiti— do you have the guts to get out there and tag some property? There's a whole lot more than just spray paint involved. To be great, you'll need things like a sketchbook, pencils, pens, markers, spray can tips, latex gloves, legal (or illegal) wall, and most importantly… creativity. If you think you’ve got what it takes to be an urban graffiti artist, follow these steps to become da ’hood’s next da Vinci.