Ultimately a doctor’s note is the only necessary proof needed to show your boss that you really did go to the doctor’s but if you feel like making an airtight case you can always take a few extra steps to make sure there’s not a shadow of a doubt.

In this series of videos, learn more about playing the flute from our expert. An experienced player, she first teaches you about buying and assembling your flute. You will also learn about the accessories needed for playing and caring for your flute. Learn scales easily by watching videos on the C scale and F scale. Tuning your flute is often necessary to get the right sound. Other common problems with flutes are addressed in this series as well. Get tips on private lessons and instructional ...

Nothing on the web is ever private. If you thought you can control your privacy, you were wrong. Websites may give you security options to better hide your information from the world, but ultimately your privacy resides in the hands of the website itself. We've seen how websites let ad companies track our private usage. We've seen how Facebook mucked up their privacy controls. We even saw how websites like Gawker are prone to hackers stealing user information. And now, Etsy has made what was ...

Black Ops gamers— you have new Call of Duty maps for your multiplayer adventures. If you have no idea what I'm talking about— you might as well just sell that copy of Black Ops and pick up the newest version of Harry Potter you can find, because you're no Black Ops soldier.
Prank Calls, Masked NumbersWho is calling your phone or your child's? Pranksters use a lot of tricks to make sure they can get on your nerves. Being able to trace prank calls is important because you're not going to learn much from your Caller ID, since most prank callers use an unlisted number - such as, a cell phone number. Many also use special code *67 to mask the number so your Caller ID will show "Blocked Number" or "Private Number". There are a lot of mild cases of so-called phone bull...
You know it's crazy out there when governments start blocking social websites like Facebook, Twitter and even YouTube. But that's what happened in Egypt, when tens of thousands of anti-government protesters took to the streets on Tuesday (January 25th) in hopes of ending President Hosni Mubarak's 30 years of authoritarian power.

Don't want one of your Facebook "friends" knowing your status updates? Prefer to keep a few of those "friends" out of your photo albums? Would you like to prevent a few "friends" from accessing your address?

Kill with skill. That's the motto of the newly released Bulletstorm, available on PlayStation 3, Xbox 360 and Windows. It may sound ridiculous and somewhat obnoxious by itself, but it's actually in regards to its many "ridiculous skillshots" that a player can perform. And yes, ridiculous skillshots was an actual quote, straight from Epic Games.

Screw the airplane man. Ticket prices are too high. Competitive consumer choices are pretty much nonexistent. And need I go into the pain of being crammed into those tiny seats, elbow-to-elbow, thigh-to-thigh with a perfect stranger? Even your average Richie Rich winces at the astronomically high prices for a First Class seat.

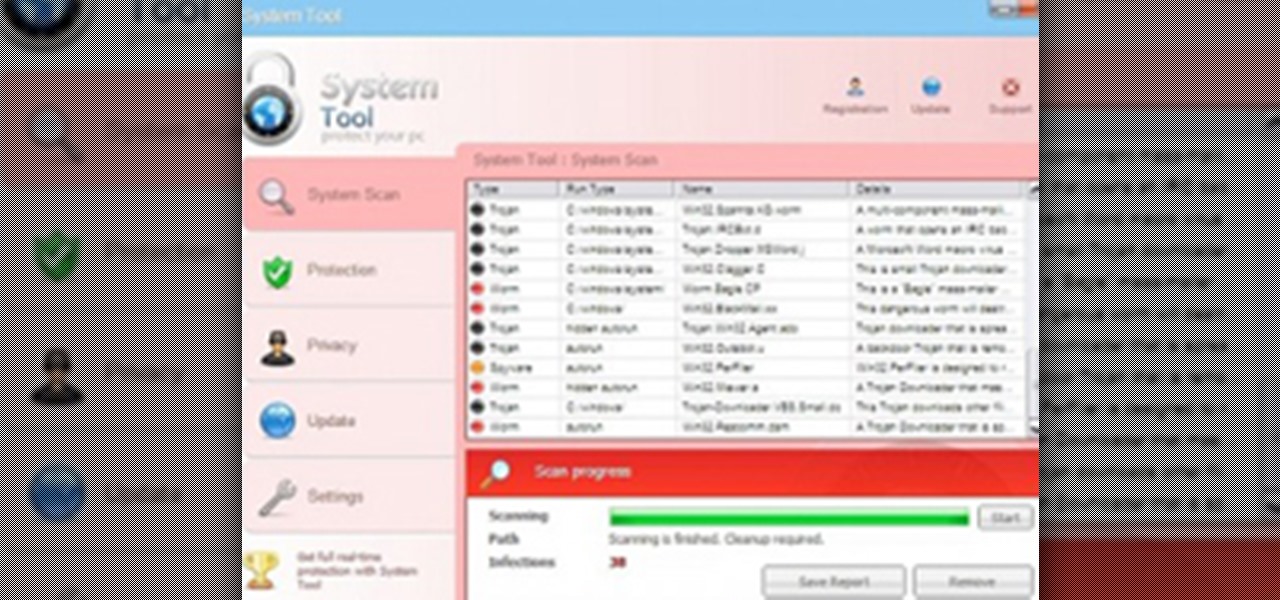
System Tool. It sounds like something your Windows computer might need, but it's the exact opposite.

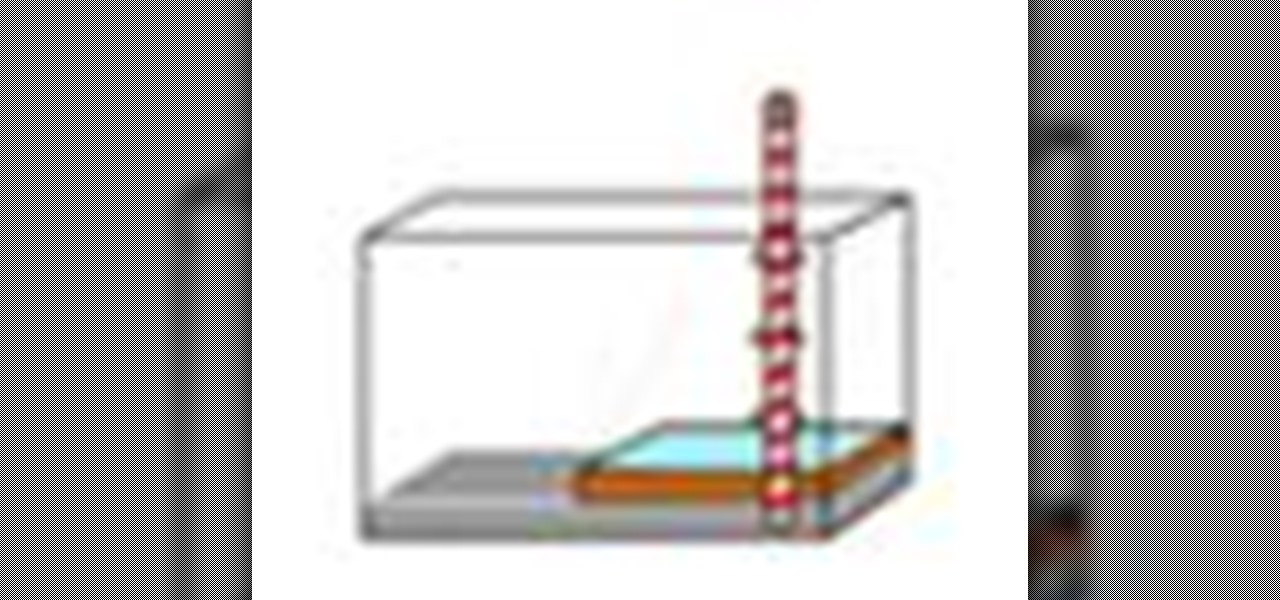
Many communities obtain their drinking water from underground sources called aquifers. If a surface water source, such as a river, is not available, water companies will drill wells into the soil and rock to a water source below. Some homes have their own private wells and must tap into the same ground water sources. In this video tutorial, you'll what aquifers are, how they work, why they are important and, of course, how to build your own model! Build your own aquifer.

This article will show you how to make an auto clicker program in Visual Basic Express Edition 2008. An auto clicker is a very useful program that makes your mouse click many times automatically, wherever it's pointed. It's a very good AFK (away from keyboard) program. Just point your mouse on your screen and turn it on! It's very useful for computer games (FPS, MMORPG, and others).

Collision Repair Related Careers When you think of a career in collision repair you probably think of a body repair or paint technician. However, there are a lot of related careers that collision repair can lead to. For Example, you can work in auto parts stores, dealerships, insurance companies, paint representatives, trainers, etc. In this article we are going to examine a career as an auto estimator.

WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling.

Today's guide is on creating a password protected folder on Windows 7 without any additional software. Yes, you heard that right. No extra software at all! This guide is intended for beginners. But please note, this method should not be used to store financial or otherwise highly confidential material. It might be a good place to hide a planning document for a family member's birthday party or similar occasion where you need to keep something secret temporarily.

Today I will show you how to create a simple keylogger in Visual C# Sharp, which will start up hidden from view, and record anything the user types on the keybord, then save it into a text file. Great if you share a PC and want to track what someone else is writing.

Learn how to play the improve game "Lines from a Hat" at your next party in this free video that will keep your party guests entertained and thinking on their feet.

Learn how to play the improve game "Interrogation" at your next party in this free video that will keep your party guests entertained and thinking on their feet.

Learn how to play the improve game "Psychiatrist" at your next party in this free video that will keep your party guests entertained and thinking on their feet.

Learn how to play the improve game charades at your next party in this free video that will keep your party guests entertained and thinking on their feet.

Learn how to play the improv game "Slideshow" at your next party in this free video that will keep your party guests entertained and thinking on their feet.

Learn how to play the improve game "Throw the Story" at your next party in this free video that will keep your party guests entertained and thinking on their feet.

Learn how to play the improve game "Dress the Mummy" at your next party in this free video that will keep your party guests entertained and thinking on their feet.

Learn how to play the improve game "The Wind Blows For" at your next party in this free video that will keep your party guests entertained and thinking on their feet.

Learn how to play the improve game "Quirks" at your next party in this free video that will keep your party guests entertained and thinking on their feet.

Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program.

Use the following Gourmandia napkin folding secrets to impress and surprise your guests at private parties, restaurants, weddings and date dining. Learn how to fold a napkin like a peacock. Fold a napkin like a peacock (Pliage paon).

You never know when you may lose your BlackBerry and expose all your personal information to whoever finds it. That's okay, protect private data on your mobile PDA by setting a password. Now you don't have to worry about strangers stealing your secrets anymore. Set a password for your BlackBerry Bold.

In this video tutorial, viewers learn how to password protect their files. This task can only be done on a Windows computer. Begin by creating a Microsoft Word document. Simply right-click on the desktop, go to New and select Microsoft Word Document. Then double-click on the document and create your text document. Now to save it, click on File and select Save As. Name the file. Now click on the Tools drop-down menu and select Security Options. Then type in a password, reconfirm the password a...

Jordy with AT&T teaches us how to block your cell phone number when making outgoing calls. By doing this, any person you call cannot read your ten digit cell phone number. It's as simple as entering a code before you dial the desired number. The code is *67 followed by the ten digit number and then placing it as a regular call. This does not allow the person you are calling to see your number. Instead it will show up on their caller ID and read as "Private Caller". Follow Jordy's advice and k...

Check out this video to see how to use the popular ES&S iVotronic touchscreen voting machine. You'll see how to begin the voting process by having a poll worker activate your ballot, then you can vote in private. So, if you are tired of using hand ballots for your county in voting elections, watch this to upgrade to an electronic system. It's easy to use, and this is your manual. Use the ES&S iVotronic touchscreen voting machine.

Last time, we looked at archaic cryptography, so you should have a basic understanding of some of the concepts and terminology you'll need. Now, we'll discuss one of the most important advances in computer security in the 20th century—public key cryptography.

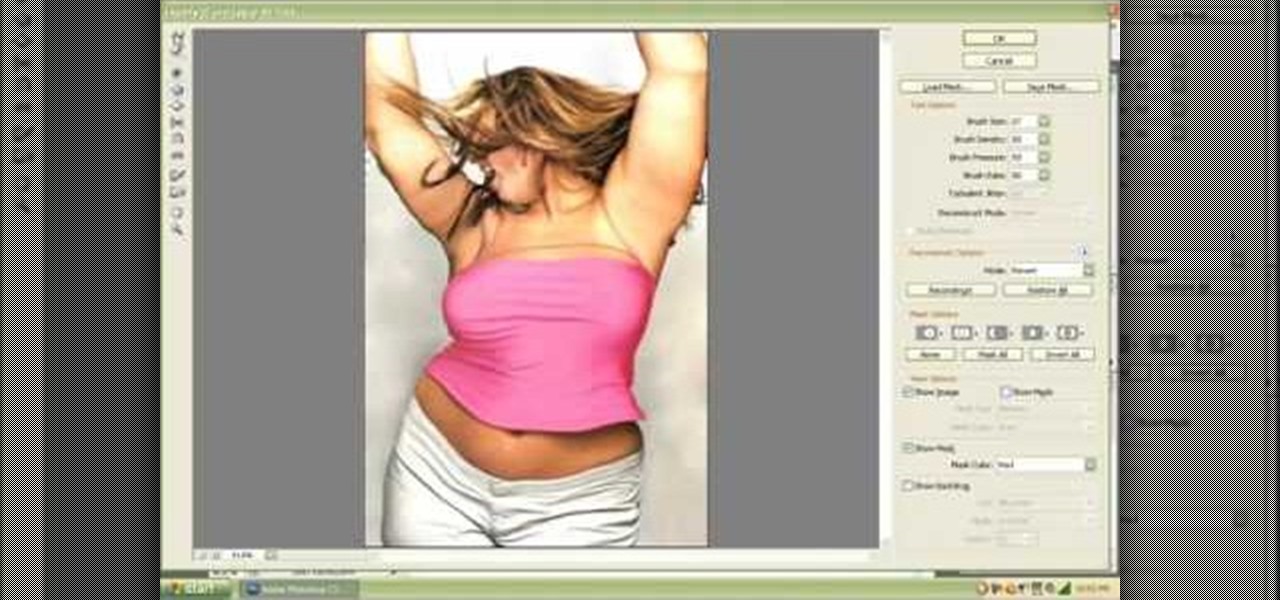
Want to know how to remove a digital tag from a garment for (in this case) a pair of shoes? This clip will teach you what you need to know. Whether you're new to Adobe's popular raster graphics editing software or a seasoned professional just looking to better acquaint yourself with the program and its various features and filters, you're sure to be well served by this video tutorial. For more information, including detailed, step-by-step instructions, watch this free video guide.

You're lost. You're cold, thirsty— you're hungry. What if you're not much of a hunter? Maybe you're a gatherer. So, then you'll eat plants. But what if you eat something poisonous? What if you're allergic to it?
A 12-year-old Minnesota girl was reduced to tears while school officials and a police officer rummaged through her private Facebook postings after forcing her to surrender her password, an ACLU lawsuit alleges.

+Nik Cubrilovic discovered last week that Facebook could track your web activities even after you logged out of your Facebook account. After some blatant denials from Facebook spokespeople, Facebook decided to fix the logout issue, but not before +Michael Arrington, on his new Uncrunched blog, made a concise post revealing Facebook's dishonesty: Facebook submitted a patent application for "tracking information about the activities of users of a social networking system while on another domain...

Introduction I will not go into some time-waster of a story about how I came to build this app. It was a prerequisite in a bigger project I am still tinkering with from time to time.

It's only been a few weeks, and already there are a lot of misconceptions and myths floating around Google+. Let's take a deep breath, and tackle some of the more prominent ones.

Although circles are Google+'s answer to the problem of social network relationship management, that's not the only thing it's good for. People on Google+ are using circles for all sorts of creative activities, some of which aren't obvious as first glance.

If you've recently noticed that you're missing Quick Settings toggles on on your Samsung Galaxy S6 or S6 Edge—specifically ones for Mobile data, Private mode, and Mobile hotspot—you aren't alone.