This achievement can be earned on the Outlaw to the End downloadable cooperative mission in Read Dead Redemption. To get the Dodge This achievement, start a private match with a friend on the Herd mission. Once the mission starts, select the bolt action rifle and the rolling black rifle. Use the bolt action as your primary weapon, and shoot the TNT crate next to the tent on the righthand side. Quickly switch over to your rolling black rifle. Have your teammate use one of the repeaters to weak...

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...

In this video tutorial, viewers learn how to use Flickr photos in their screen-saver. This task can only be done on the Windows computer. Users will need to download the program from the website provided in the video. Once downloaded and installed, there is an option in the Screen Saver Settings. Users are able to take photos from specific users or groups, or can search through tags and contacts. Further options include selecting the size of the photo and delay between switching the photos. U...

In this video, presented by the experts at the St. Louis Community Credit Union, learn how to prevent thieves from stealing your identity or account information. These days, between paper bills, Internet banking, social networking and all the other ways we interact, there are many ways for crooks to get into our private lives.

When conducting mobile convert surveillance, you will be following someone and it is important to dress appropriately for the environment and carry your surveillance equipment in a bag that will fit into the scene.

When you need to gather information without anyone knowing you will need to utilize covert audio surveillance. There are a variety of ways and technique to most effectively get the information you need.

Have you ever had to close an application with private info in order to let someone else use your PC? LockThis! is a windows application that lets you secure individual programs without the hassle of having to save your progress and closing the program. To use LockThis! just hold the control key and click on the application that needs to be locked and simply enter your password on the dialog that pops up and your done. Now anyone can use your pc without you having to look over their shoulder....

Hak5 is at it again, with a plethora of somewhat accessible solutions to your technological problems. If you've ever needed to get through your school's firewall, or secure traffic tunneling, or try out applications in a fast, efficient manner? This video has it all and more.

This educational safety video is geared toward public and private utility workers and linemen who need to remove pole tops while dealing with high-voltage electrical cables and electrical insulators. It discusses the proper pole topping removal procedure and demonstrates effective procedures for removal.

Strings of DNA aren't the only things that contain helixes. With a bit of skill and practice, you can make your own rope helix for fun or bondage and BDSM play by watching this video by Two Knotty Boys.

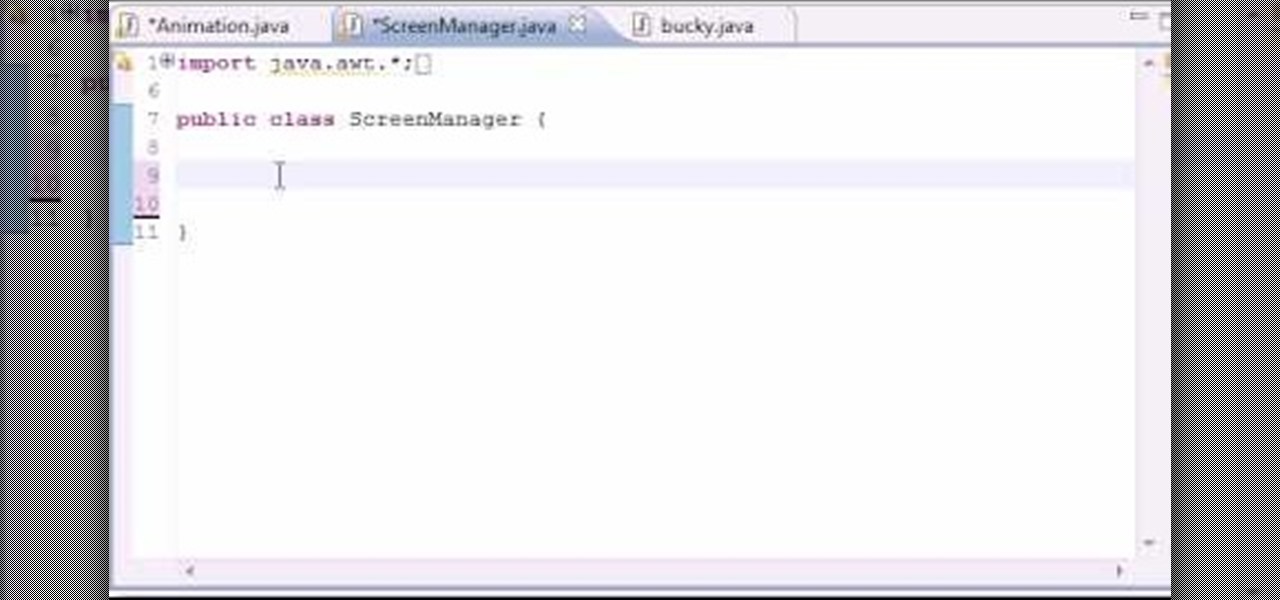
In this 14th video in a series about JAVA game development, "thenewboston" (Bucky Roberts) explains how to redefine your screen to avoid annoying flickering. Flickering in JAVA games often occurs because of time lags as the viewer watches the computer draw a new screen, pixel by pixel. Pre-installed code in JAVA can be used to eliminate this problem by taking advantage of "Buffering" and "Page Flipping". These functions permit you to delay the composition of a new screen until it is finished,...

This video will show you how to record video on your Apple iPhone 3G for free! This is a complete guide to installing the iPhone Video Recorder on your iPhone 3G, which also works on the First Generation iPhone.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

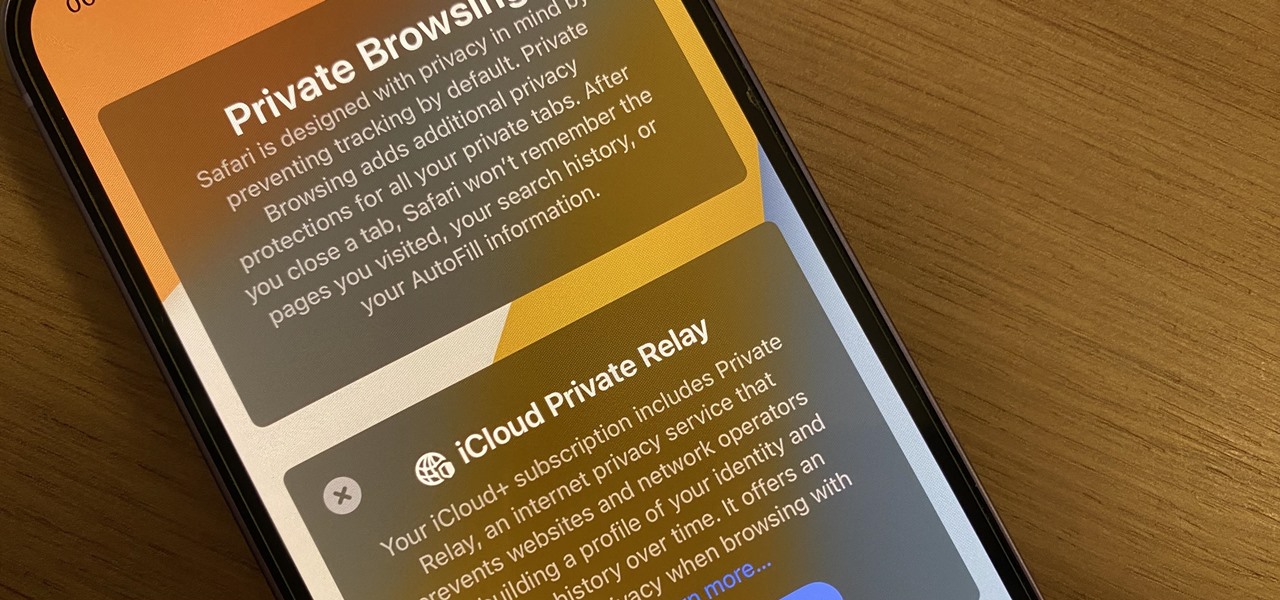
Safari's massive upgrade in Apple's latest iPhone software update includes new features you won't find in any other web browsers on iOS, from better ways to stay organized to enhanced security and further privacy protections.

For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption.

If you prefer to use Google or another search engine for everyday browsing in Safari but would also like a more secure browsing experience for all your secret searches, there's a simple way to switch between them quickly while also adding additional layers of security on top of your already clandestine browsing.

When conducting covert mobile surveillance with video it is vital to have a good bag that will contain and allow you to get footage in an inconspicuous manner. Always take into consideration the lighting and distance you’ll be at.

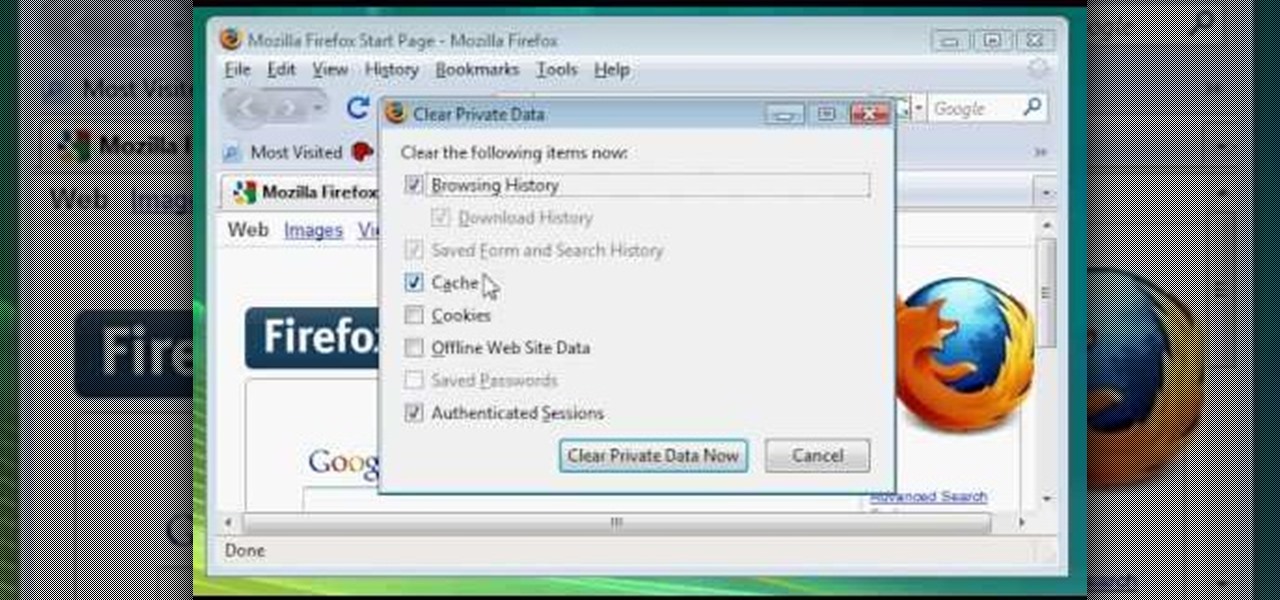
In this video, we learn how to clear browsing history and cache in Firefox and Internet Explorer. First, while in Firefox, go to the tools menu, then click on clear private data. In the new window, click on the items that you want to have cleared, then click "clear private data now". After this, the computer will clear out all the internet files. Next, while you're in Internet Explorer, go to the tools menu, then click on "internet options". Once in here, click the appropriate sections to cle...

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

If you're interested in joining or creating a fantasy football league, take a look at this guide on how to use leagues in ESPN Fantasy Football and learn the differences between the leagues. You can choose to play in a public or private league, depending on if you want to limit your fantasy league to your friends and family or if you want to play against other team owners you meet online.

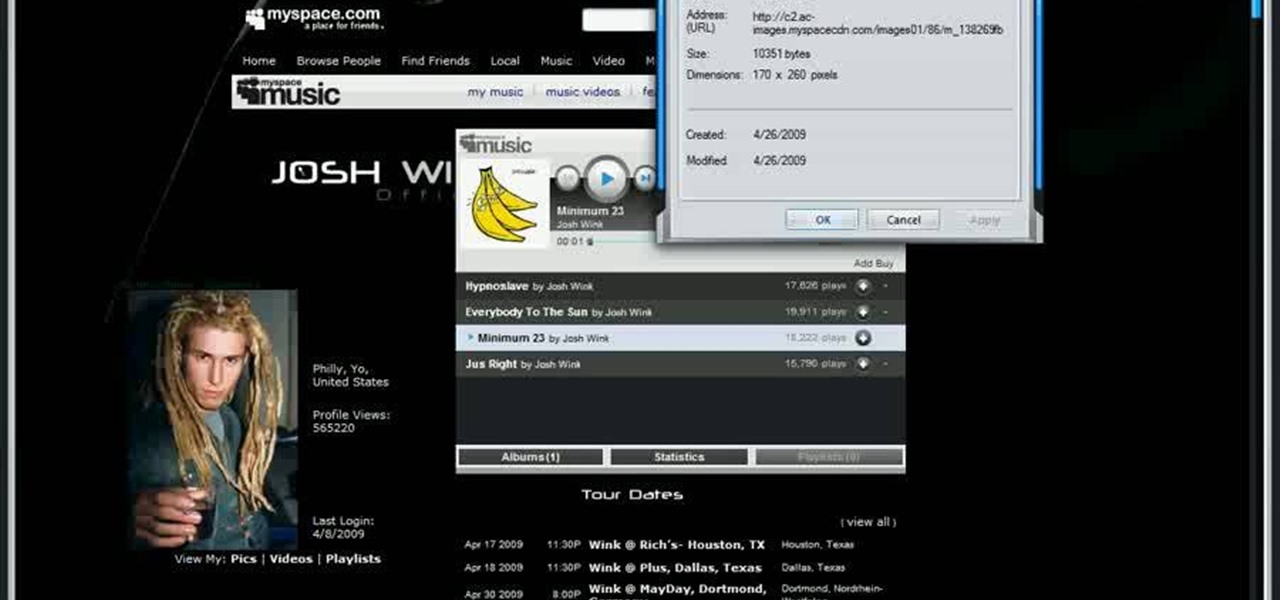
In this video, learn how to view private MySpace profile pictures. The process is easy & quick. In no time you will surfing MySpace freely with no privacy preferences to stop you.

Jared of the TechCentric crew gives you the lowdown on the basics of keeping your VoIP conversations secure and, on the other side of things, how to use the Cain VoIP sniffing application. For detailed instructions on keeping your VoIP conversations private, watch this hacking how-to.

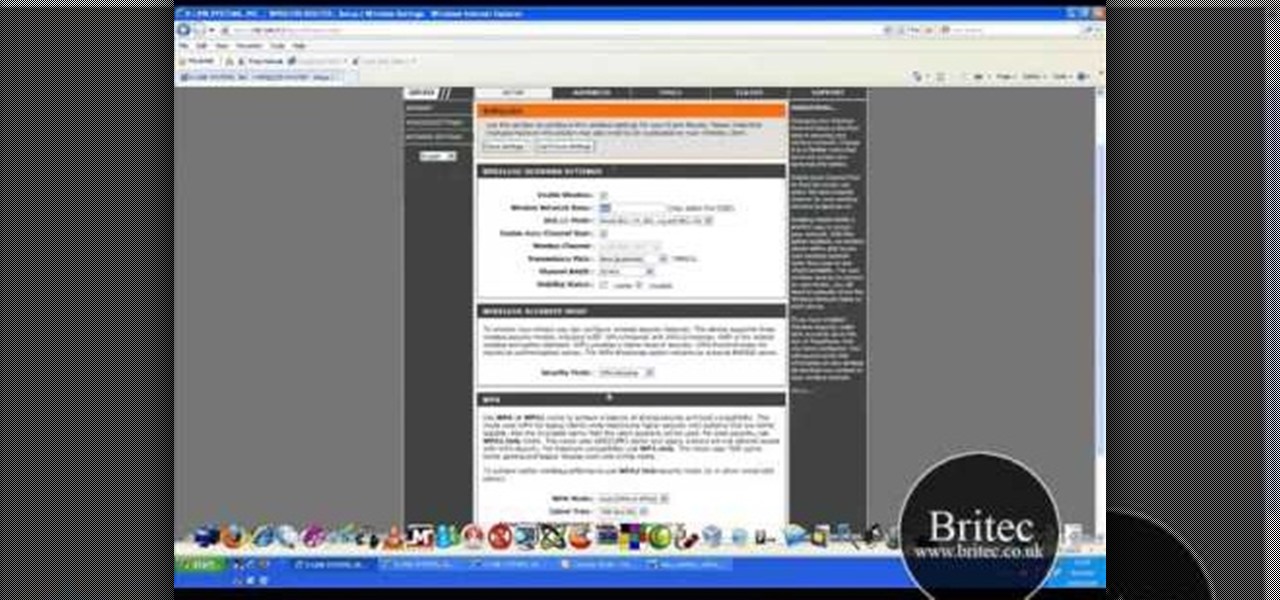
In this tutorial, Brian teaches us how to make your wireless network secure. First, go to the start menu, then go to run and type in "cmd", then type in "iconfig /all". Now a new window will pop up and you will look for the default gateway. Find the IP address to log onto the routers you have. Now, type in your IP address into your address bar on your internet browser. You will be asked to log into your account with your password and user name, which you can find at the manufacturers website....

Lady Gaga is one of the most secretive women in show business, hiding behind her stage performer mask and outrageous costumes so often that we can hardly believe there's a real person underneath all that fluff.

If you're worried about having your private information taken away from you by hackers and other malicious people, this tutorial may help you. This tutorial will help show you how to easily use and understand the phishing filter in Internet Explorer 8. It only takes a couple of clicks to activate and can be the difference between making sure your private information is secure or out in the open for others to use. Good luck and enjoy!

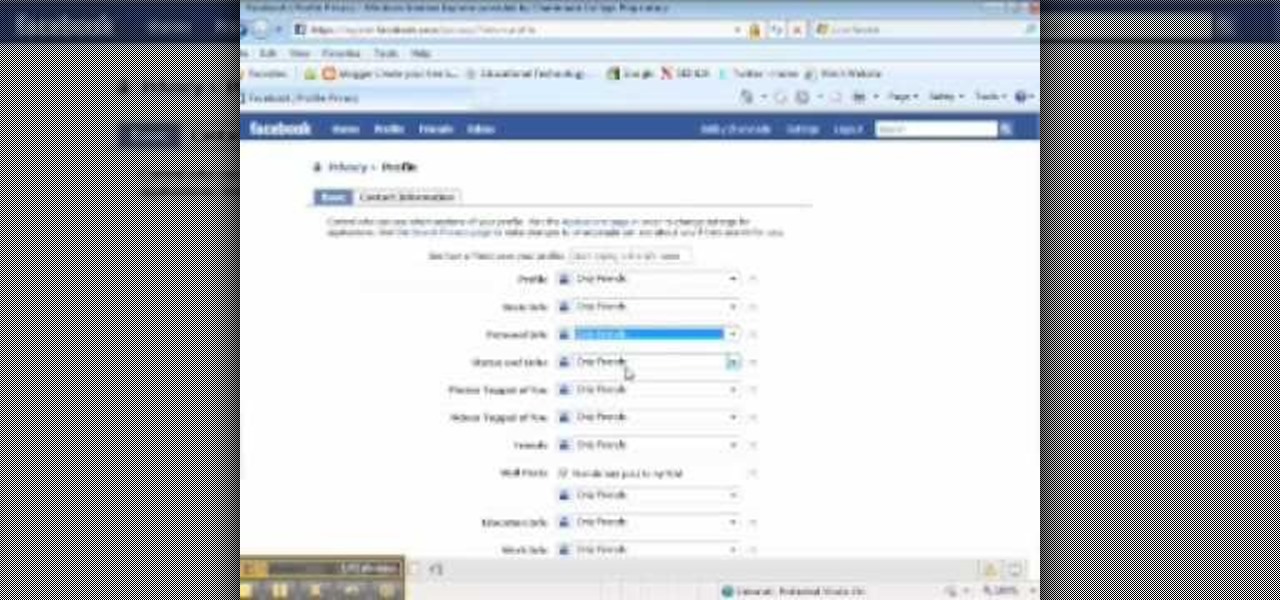
This video tutorial from ChaminadeENN shows how to set your Facebook account to private mode. First what you need to do is to sign in to your Facebook account.

You can use surveillance skills to pursue a career as an investigator or to spy on whoever you like. You will need to have a mobile means of making observation and this might include things like pen and paper, camcorder or camera.

Here Danny Beales shows you how to quickly clear your Firefox cache and cookies. To clear your Firefox cache, do the following: Go to Tools Clear Private Data Select which data you would like to have cleared, and click on Clear Private Data. Your cookies and/or cache has been cleared. Remember to do this from time to time, because it will help speed up your browser's performance as well as keep harmful cookies from tracking your browsing.

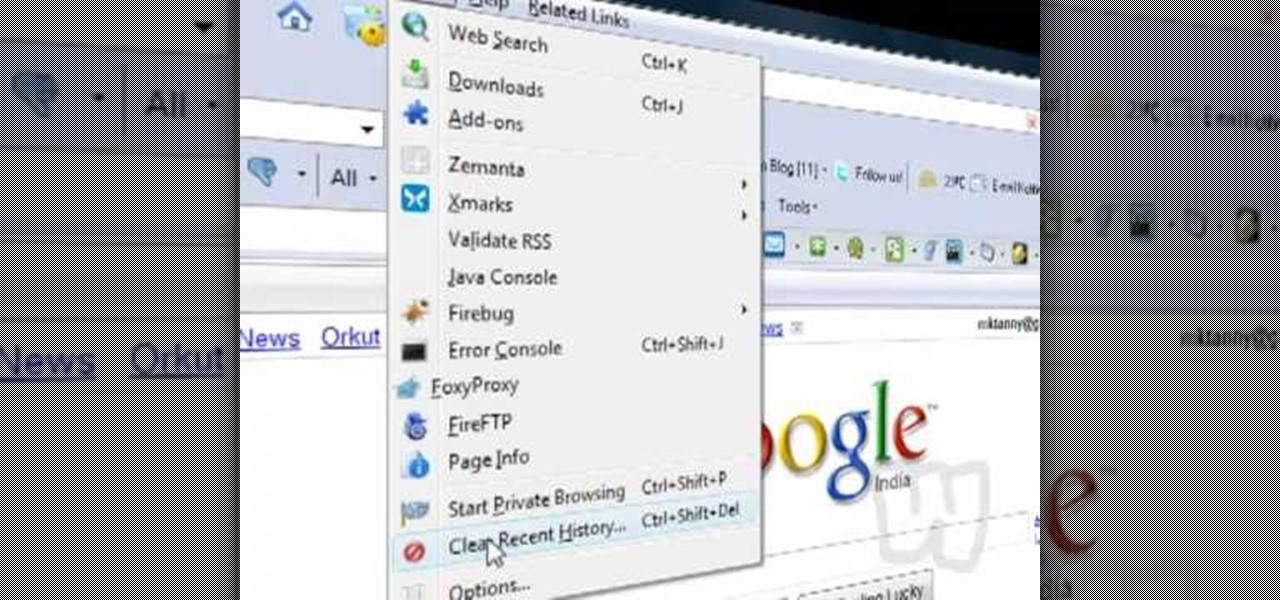
This video shows you how to easily delete cookies from your browser. First thing you have to do is open the web browser you usually use (the video shows how to delete cookies from Firefox) and go to the Options tab in the upper menu. Then choose the Clear Private Data or Clear Recent History item. In the pop-up window, check Cookies and Cache and then press the Clear Now button. The Clear Private Data/ Clear Recent History window also can be opened by pressing CTRL+SHIFT+DEL. That's it! Good ...

Some of the new features in iOS 15 take some getting used to, and the biggest one of those is Safari's relocated search bar, aka address bar. There are more than a few reasons why it's a jarring change, but the good news is that you can return Safari's search bar to its pre-iOS 15 position at the top of the screen.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

To become a bounty hunter, you will want to first check your state's laws to see if you need to be a licensed private investigator. If you live in Florida, South Carolina, Oregon, Wisconsin, or Kentucky, don't even try it--bounty hunting is not allowed! Otherwise, your first step is to find a client who needs a target to be caught. Bail bond agents employ bounty hunters to track down people who have refused to show up to court. Find out who your target is. Assemble a file, look into any recor...

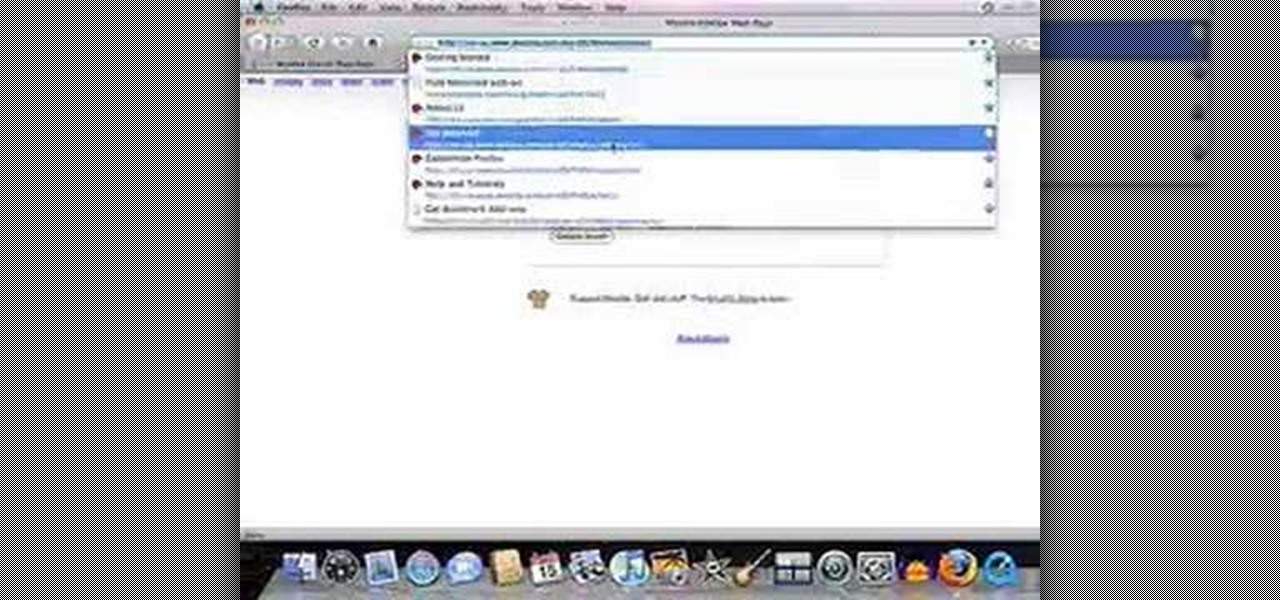
In this video, we learn how to clear Firefox location bar and browsing history. To get rid of an individual one, use your keyboard to go to the one you don't want. Then, press shift+delete and that one will be deleted. To remove them all, go to tools then click on "clear private data". Check the box of the browsing history, then click on the button to clear all the data. If you still have items in the list on your browser, then that means you have those websites bookmarked. To remove those, y...

Matches may not be the ubiquitous part of every person's going-out equipment that they once were, but they are still useful both for lighting fire if you don't have a lighter and for pulling these two hilarious bar pranks. The first is a simple counting game where you manipulate your victim into making piles of matches of sizes you guess correctly, because you rigged the game. The second involves challenging the victim to make six equal half of eleven using a pile of matches. Both are funny, ...

Do you have something important that you want to hide from your parents or friends? Well, then check out this tutorial. In this video, you will learn how to take an ordinary Pepsi bottle and turn it into a secret stash box. Because the bottle is see-through, no one will ever suspect there is something inside of it.

In this Computers & Programming video tutorial you will learn how to hide and lock folders in Windows. When you want a private folder that you don’t want any one else to open and see. You will need this feature. For this open a new folder. Open the folder, right click on it and go to ‘customize’. Then select ‘change icon, click on a blank icon, click OK and ‘apply. Now you will see that your folder icon on the desk top will disappear; only the name will be visible. Now rename it with a small ...

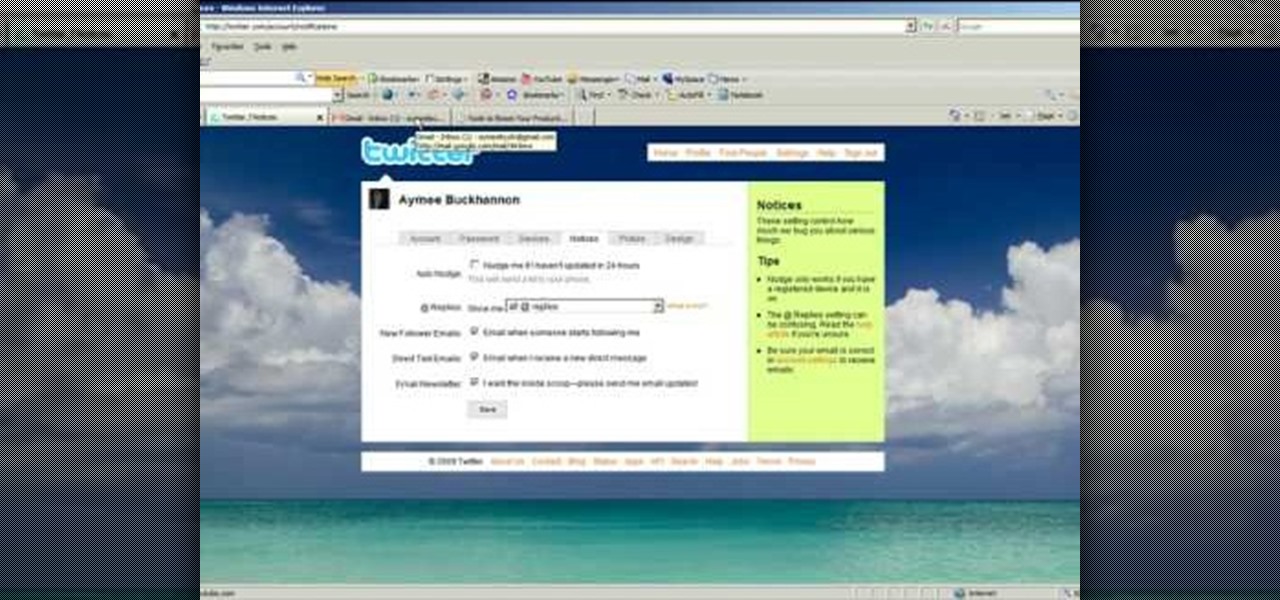
Twitter is the latest popular social networking forum. Twitter is used to keep your friends updated with what you are doing using 140 character messages called tweets. In twitter you can follow your friends and you will be notified when ever your friends posts a new message. Similarly other people can follow you on twitter to know what you are doing. In twitter you can customize to send an automatic private response to your new followers. To do this open your twitter account. Go to the notice...

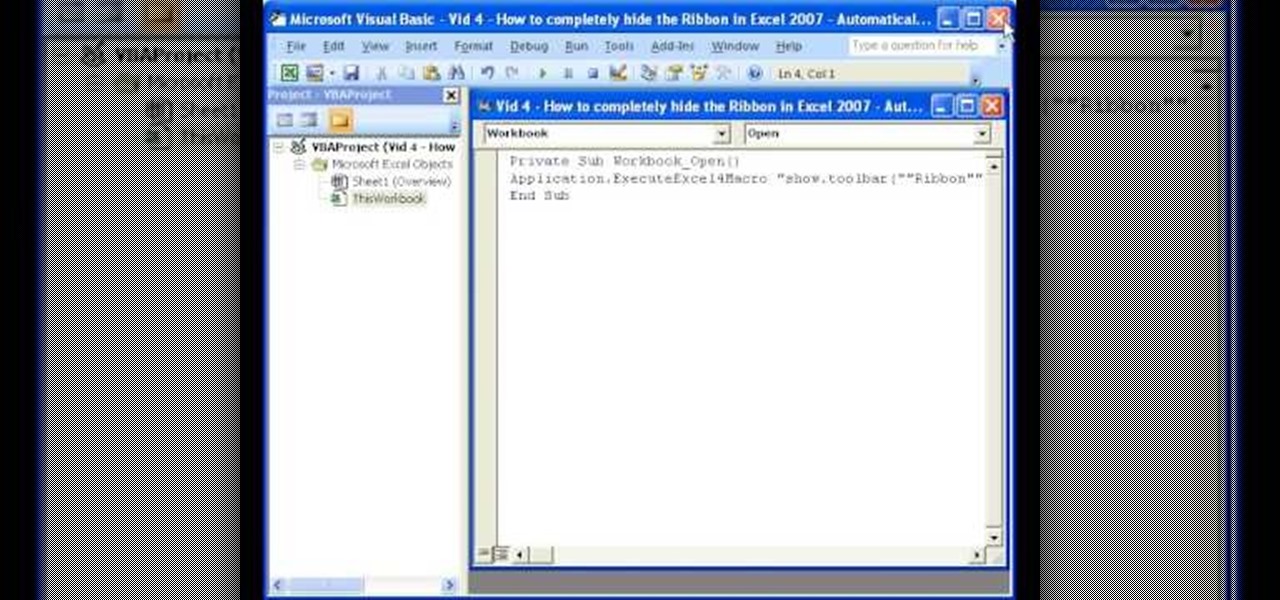
Teach Excel demonstrates how to completely hide the Ribbon menu system in Excel 2007 as soon as the workbook is opened. This will be done by writing a macro which hides the Ribbon only for the specific workbook in which the macro is implemented. Some helpful shortcuts are Ctrl+F1 which partially hides the ribbon, Alt+F11, which opens the Visual Basic screen, and Alt+F8, which opens the macros list. First, hit Alt+F11 to open the Visual Basic screen. Then double-click "This Workbook" on the le...

This is a steamy part of Heavy Rain for PS3. Steamy and sexy. But this is edited for nudity, so don't worry about seeing anything you shouldn't. See how to beat Chapter 5 - On the Loose.

in this episode of Heavy Rain, you confront the Shark. Just try not to get yourself killed when he pulls out that shotgun. Then, are you going to kill him, or are you not? See how to beat Chapter 4 - The Shark.