With a root bounty of over $18,000 up for the taking, developers were highly motivated to get the AT&T and Verizon Wireless variants of the Samsung Galaxy S5 rooted. Legendary hacker George Hotz, aka Geohot, has won the race and can now step up to claim his prize.

There are so many things in life I wish I could've canceled without any repercussions, and I'm mostly talking about text messages.

These days, you can find a digital version of almost any form of entertainment. Being able to download or stream content is convenient for a lot of reasons—you can avoid going to the store and you never have to worry about late fees on rentals.

Males fight for dominance in order to gain access to the limited supply of female eggs. This is why male birds expend energy on brightly colored plumage, but female birds do not.
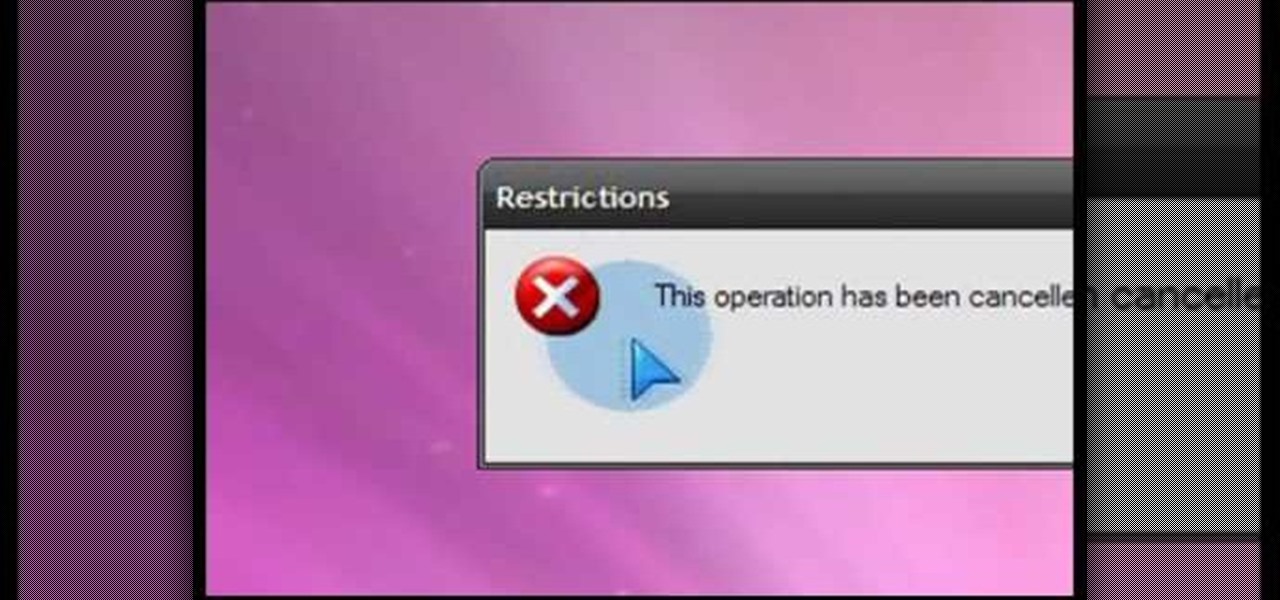
If you love computer pranks, this is one of the easiest ones to pull. This video will show you how to remove the Shut Down button from the start menu in Windows XP. Actually, it does't remove the shutdown button, it just disables it, giving the user a restriction message, stating "This operation has been cancelled due to restrictions in effect on this computer. Please contact your system administrator."

Not every nurse can get an IV every time, that's why it's important to stay in practice for the proper technique used for inserting a peripheral IV. This is a common medical procedure that all fields related to medicine should know. Even the soldiers in the military are taught how to insert an IV — every soldiers, not just the medics.

One of the hardest things a man can go through in life is a trip to the hospital, especially when he knows he's going to need a catheter. It's every man's worst fear. But for a nurse, it's necessary knowledge. Learning the male urinary catheterization procedure hands-on is difficult due to the urgency involved in patient care, so this video aims to prepare nurses so they can learn and stay fluent with the proper urinary catheterization technique of a male patient.

In many situations, learning proper medical procedures is difficult due to the urgency involved in patient care, so this video aims to prepare nurses so they can learn and stay fluent with the proper urinary catheterization of a female patient.

PowerShell is an essential component of any Windows environment and can be a powerful tool in the hands of a hacker. During post-exploitation, PowerShell scripts can make privilege escalation and pivoting a breeze, but its execution policy can put a damper on even the best-laid plans. There are a variety of methods, however, that can be used to bypass PowerShell execution policy.

Facebook recently hit a snag in its quest to take augmented reality face effects to its millions of users.

A landmark bill finally went into action this week that will allow American cellular customers to unlock their smartphones for free. The process of unlocking may vary between mobile service providers, but you can rest assured that you are now entitled, by law, to carrier-unlock your smartphone.

The last presidential debate of 2012 is over between President Barack Obama and Republican nominee Governor Mitt Romney. Now it's up to you to choose your candidate by election day on November 6th, 2012, and more importantly—VOTE!

This educational safety video is geared toward public and private utility workers and linemen who need to remove pole tops while dealing with high-voltage electrical cables and electrical insulators. It discusses the proper pole topping removal procedure and demonstrates effective procedures for removal.

First of all you have to search for a reputed dealer. Then ask him all necessary questions like what sort of lenses shall fit in your camera, what shall be the size of the lens to fit in your camera. If you are going to purchase it online then you have to ask whether the surface of the lens is scratched and marked in any way. Make sure that three is no mould or scratches on the lenses. You can also hold the lens towards the sun or a light source. Do not hold it directly against the sun. Now y...

In this economy any job is better than none at all, right? Of course, but if you know you are worth more than you're making, follow this tutorial for tips on how to ask your boss for a raise. You'll never know if you don't ask! Good luck!

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.

I've never understood gift cards. Aside from being severely restricted as to where you can use them, they're also a strange gift, especially if you don't shop at that particular store. Some even have expiration dates and service fees.

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

Paying retail just isn't as good of a deal as buying straight from the manufacturer. To become a buyer, figure out the right manufacturers for you. Initially, you can start this process by doing web research. Surf the internet to find out what manufacturers sell directly to the consumer. Internet access is important for finding product information. Scan the manufacturer's website for online catalogs that describe an item's price, color, model, ID number, and make.

The first thing that comes to mind when your car is stolen is: ####!! However, once calm, cover these bases when your car is stolen to notify relevant parties and help ensure vehicle recovery or replacement.

If you want to stop telemarketers from calling, use this guide and try a multi-pronged approach. You Will Need

Need to leave town earlier or later than planned? Flying stand-by is not as simple as it used to be. Learn how to fly stand by - you never know when it may be necessary.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

There's nothing more disappointing than finding yourself all packed and ready to travel when you find your flight has been canceled. You can make the best of the situation by finding out just what you are entitled to or how to best ameliorate the situation.

Snapchat isn't the only tech company transforming landmarks with augmented reality for Pride Month. About four miles southwest of New York's iconic Flatiron Building, which is getting its own Pride makeover via Snapchat's Landmarker AR, Stonewall National Monument is also receiving some augmented reality treatment by way of the Stonewall Forever mobile app published by the Lesbian, Gay, Bisexual, and Transgender Community Center (better known as The Center) in partnership with Google.

Get ready for more software testing. Just two days after the official release of iOS 12.1, Apple seeded public software testers iOS 12.1.1 — one day after developers received the update. While the rest of the iOS world is just getting to know all of the cool, new 12.1 features, testers are now sinking their teeth into what the next iteration of iOS has to offer.

As awesome as the 2017 Galaxy lineup may be, few can forget the monstrous disaster that was the Note 7's exploding battery. Needless to say, the last thing Samsung wanted was another news story about a problem with the Note 8's battery. Unfortunately, that's exactly where we find ourselves today.

Apple has billed ARKit as a means to turn millions of iPhones and iPads into augmented reality devices. The refrain is similar for Kaon Interactive, a developer of product catalog apps for businesses.

Thanks to augmented reality, fashion companies can let customers try on cosmetics, clothes, more cosmetics, and sunglasses from the comfort of their homes and through the non-judgmental eyes of their smartphone camera.

In the changes to the App Store Review Guidelines for iOS 11, Apple has announced that developers must use the App Store rating API. The API was introduced in the iOS 10.3 beta period as something that would eventually become mandatory. Now, Apple has followed through on that promise.

The US Department of Transportation says it is actively completing a previously promised revision of voluntary guidelines for driverless vehicles originally drafted by President Obama's administration.

The east coast is becoming a hotbed for driverless. Sure, the west coast has all of its fancy tech companies testing self-driving cars, but we've got the goods too. Uber has brought the technology to Pennsylvania and will soon do the same in Toronto. (Stratford, Ontario, has plans to test out driverless too!) And today we got some great news: Governor Andrew Cuomo just approved of driverless testing in New York.

Lately, the biggest news in driverless has been the raging lawsuit between two autonomous spearheads, Uber and Google's Waymo. A new bill back by General Motors, however, could take them both out of the race towards driverless.

All you paying Spotify users are about to get another exclusive privilege besides getting out of all those annoying "Ever wonder what it would be like to have Spotify premium?" ads. The Sweden-based company is looking to lower the royalty fees they have to pay to major record labels for their music, by compromising on their policy that all their music be free to paying and nonpaying users. Spotify would for a limited time restrict access on major album releases to their paying subscribers.

Both the US and UK seem to be leaning toward requiring level 3 autonomous cars to train their "eyes" not just on the outside world, but even on the driver itself.

There will always be a time when you're not entirely sure what you're doing with a certain subject. But the days of weighing the pros and cons yourself are coming to an end. Whether it's a common quandary like "Where should we eat?", or a more specific question along the lines of "Should I buy this shirt or not?", you can now simply AskInternets.

Whether you have AT&T, Verizon, Sprint, T-Mobile, or any other mobile carrier, chances are your smartphone is sold locked to only work on that specific carrier's network. Sure, you could unlock your carrier-subsidized device, but that would mean breaching the Library of Congress' latest Interpretation of the Digital Millennium Copyright Act—making the whole process illegal. As softModders, boundaries and regulations are things that we don't take lightly, although many times we have to begrudg...

If you bought the new iPhone 5, you've probably been less than thrilled with the lack of cases and accessories that you can use it with. Docks are no exception—users were disappointed to learn that Apple has no plans to even make one for the newest addition to the Apple family.

If you use apps on your smartphone, chances are you have no idea what those apps are doing with your information. Just this year, there have been several scandals involving apps transmitting user data, like Path uploading users' entire address books onto its servers, HTC's Security Flaw, and Brewster exposing users' personal information (even Ashton Kutcher's). A new service called Mobilescope wants to make sure you always know where—and to whom—your data is going. Lots of apps copy your cont...