There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.

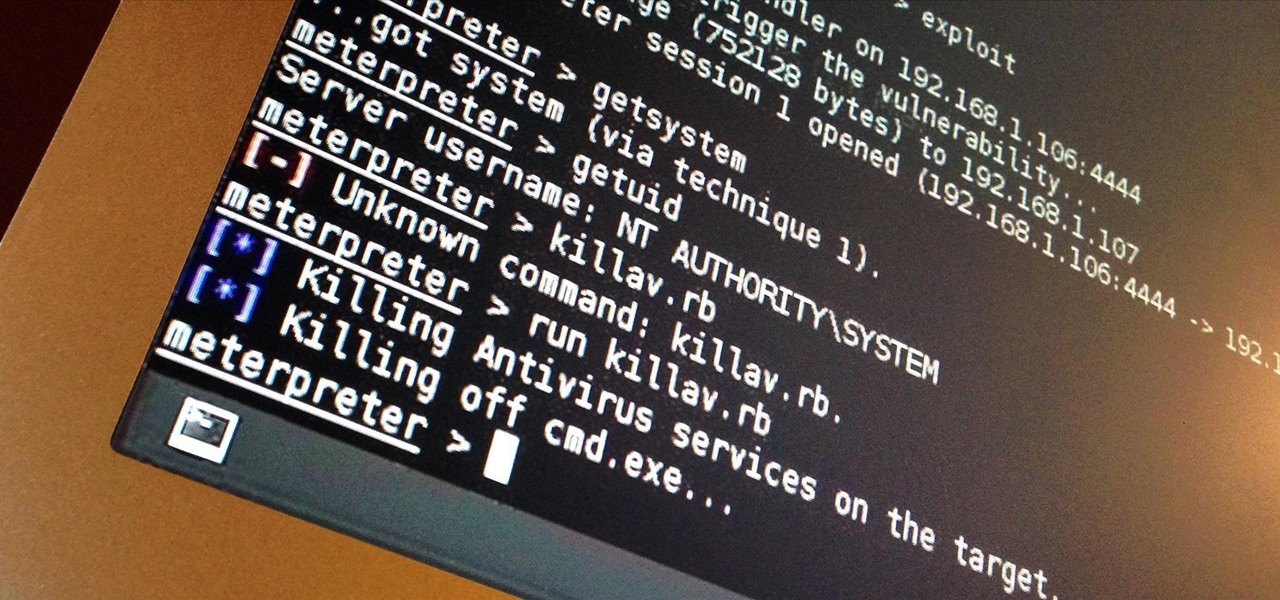
So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

All you paying Spotify users are about to get another exclusive privilege besides getting out of all those annoying "Ever wonder what it would be like to have Spotify premium?" ads. The Sweden-based company is looking to lower the royalty fees they have to pay to major record labels for their music, by compromising on their policy that all their music be free to paying and nonpaying users. Spotify would for a limited time restrict access on major album releases to their paying subscribers.

I've done numerous tutorials in Null Byte demonstrating the power of Metasploit's meterpreter. With the meterpreter on the target system, you have nearly total command of the victim.

Many people find Steampunk problematic for a whole host of reasons, not least of which is the glorification of an era of Western history that featured institutionalized slavery, racism, sexism, elitism, and many more -isms.

If maintaining privacy is an ongoing battle, the front line is your smartphone. Apple included several new security features in iOS 10, but at the same time, some of the best new functionality comes with potential privacy trade-offs that everyone needs to understand.

With the upcoming Memorial Day weekend serving as the unofficial start of summer, Pepsi is turning to Instagram to help sell its soft drinks to quench the thirst of beachgoers and BBQers.

Not content to let NFL's official pizza sponsor corner the market for feeding football fans, 7-Eleven has taken a page out of Pizza Hut's playbook with a promotional augmented reality game.

Augmented reality headset maker DAQRI today named chief product officer Roy Ashok as the company's new chief executive officer to accelerate the company's growth.

One of the byproducts of the success of Pokémon Go was the viral images that made the rounds on social media of people putting Pikachus, Charmanders, and their brethren in compromising positions. Snapchat has a similar claim to fame, most recently with the inexplicable popularity of the dancing hotdog.

Hello, Null Byters. I'm Barrow, and I'm excited to introduce myself as the new admin here on Null Byte. Just like previous admins have done before me, I will be writing new guides, updating older guides if they need it, and responding to some of your issues in the forum. Before I get started with any of that, though, I wanted to talk a little bit about myself and the future of Null Byte.

UPDATE: A patch to fix the exploit has been released. Download it here.

These days, news papers, online editorials and magazines are filled with news on Iran and Syria. Of course, that is expected, as such sources need to stay current to stay in the game. My concern is that most of these articles talk about what to do about these situations.

RedRabbit is an ethical hacking toolkit built for pen-testing and reconnaissance. It can be used to identify attack vectors, brute-force protected files, extract saved network passwords, and obfuscate code. RedRabbit, which is made specifically for red teams, is the evil twin of its brother, BlueRabbit, and is the offensive half of the "Rabbit Suite."

Although next week will mark the late David Bowie's 72nd birthday, his fans and admirers are the ones receiving a gift in the form of an augmented reality app that explores the artist's career

It finally happened. Magic Leap has given the world its first glimpse at its debut device, the Magic Leap One Creator Edition.

It's long past time to face the facts: farts are funny. The first fart joke dates back nearly 4,000 years to the ancient Sumerian people. References to flatulence were also found in ancient Greece within the works of Aristophanes. (More like Aristo-fannies, am I right?) A standard in practical jokes, the whoopie cushion debuted way back during the time of the Roman Empire.

It looks like there is a fatal flaw in the current macOS High Sierra 10.13.1, even straight from the login menu when you first start up the computer. This severe vulnerability lets hackers — or anyone with malicious intentions — do anything they want as root users as long as they have physical access to the computer.

Android device manufacturers may see the new Pixel "Phone By Google" devices as just another competitor, one that likely won't upset their entry-level margins. But that would be a mistake. Pixel is Google's call to action. With Google now offering as near to perfect an Android experience as we've had so far, OEMs that want to keep selling smartphones in a world flooded with them will need to start working for the privilege.

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

While a mobile game developer may have built something unique, they still have to go through an arduous process of fixing bugs, smoothing out gameplay, making sure it works on different screen sizes, and following Apple's rules before they can submit their game to the iOS App Store.

It's no surprise that Costco has great deals, and that's why millions pay annual fees for the privilege to shop in their wholesale outlets. Just take their hotdog and soda combo for $1.50—it's the same price now as it was 27 years ago.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

If you ever want to root your OnePlus 6, install TWRP, get Magisk and Xposed, or flash a custom ROM, the first thing you'll need to do is unlock your bootloader.

If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for us, or connects back. For this tutorial, we will use a Python reverse Meterpreter shell.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

Welcome back, my eager hackers! In recent blogs, I've demonstrated how to grab password hashes remotely using Metasploit's meterpreter and pwdump. Once we have the Windows passwords from the SAM file, we can then crack these hashes using tools such as Cain and Abel.

Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be.

After facing delays due to the COVID-19 pandemic, the Olympic Games are underway in Tokyo, but a surge in cases worldwide has taken the spectator out of these spectator sports.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.