Learn how to add the decimals together in simple and easy steps. 1. First practice adding two normal digits using the traditional adding method and get your answer correctly. 2. Now to add the decimals together use the same example by including decimal points to them. 3. The adding will also be the same traditional method except that you have to place a decimal point in the exact location of your answer. 4. Now take another example (E.g.: 3. 33+4. 2) and add it in the same way by placing a ze...

This video details how to survive a knife threat from behind. When threatened from behind with a knife, do not attempt to move the body first, this will result in the attacker maintaining the capability to thrust the knife into the body. When threatened, place arms out and low in a submissive position, this is to be followed by moving the left arm backward in a sweeping motion to push aside the arm which is holding the knife. Once the arm is moved, turn the body and bring the elbow up into an...

This video is from HelpVids and describes how to change the axis titles on charts in Microsoft Word 2007. To access the chart tools, select the chart and the tools will appear above the ribbon. There are many different design options that you can preview on the screen to make your final selection. To change the chart title, click on the Chart Title button which is located on the Layout ribbon. You can then select where you would like the title to appear. Once you select the location you can t...
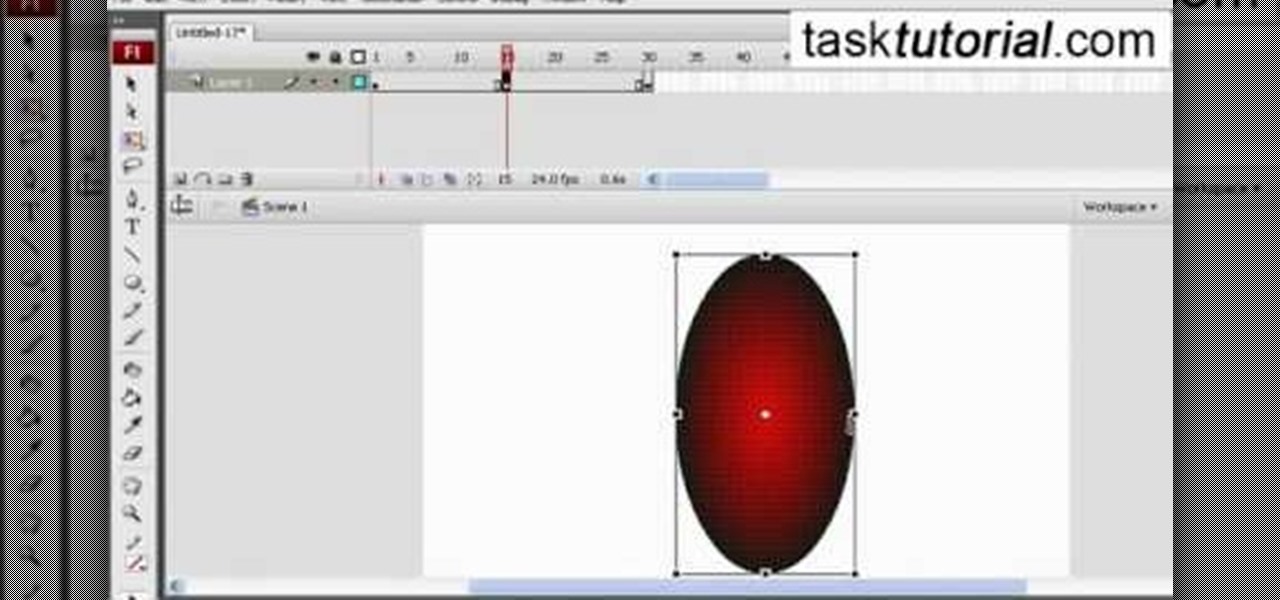
In this video tutorial the author shows how to stretch objects and text in flash. To do this open the flash tool and select the radial gradient. Pressing shift key draws a shape. Go to frame 30 and create a key frame by pressing F6. Now similarly do it at frame 15. Now at frame 15 select the free transform tool and stretch the image. Now create the shape twins in the locations shown in the video. Repeat the same process for a text starting with adding some text to the scene. Finally convert i...
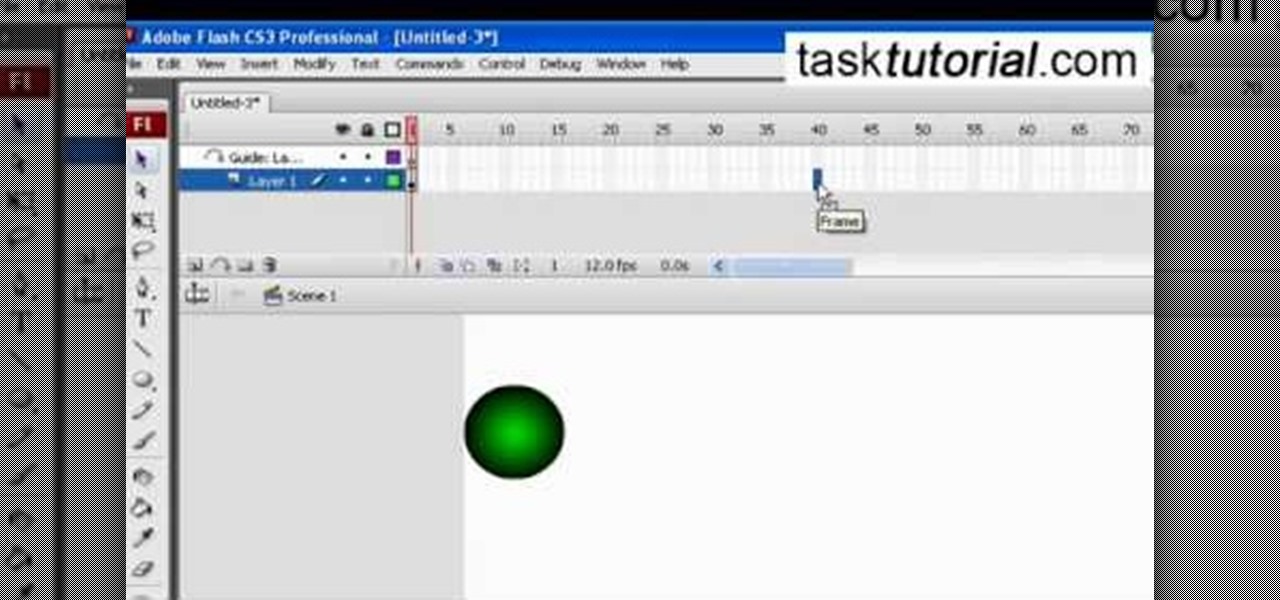
This tutorial video, from tasktutorial demonstrates how to create animation using the motion guide function in Flash. You will learn how to create an object, in this case, a ball, and create an animation that makes it appear to bounce. The guide shows you, how to add a motion guide by selecting a key frame and drawing it in. Then you will learn how to snap the object to your guide line, and add motion to it by selecting another key frame between the first and last frames, and snapping the obj...

This video tutorial by tasktutorial shows you how to create stylish text in Photoshop. Launch Photoshop and select the type tool and choose myriad-pro font light. Create a text field and type in the text as indicated. Increase the font size and location as desired. Thereafter open the layer options, choose a gradient and create a new gradient by selecting the color as required. Apply a white color outer glow change the size, range and opacity. If you want to add more text create a new layer a...

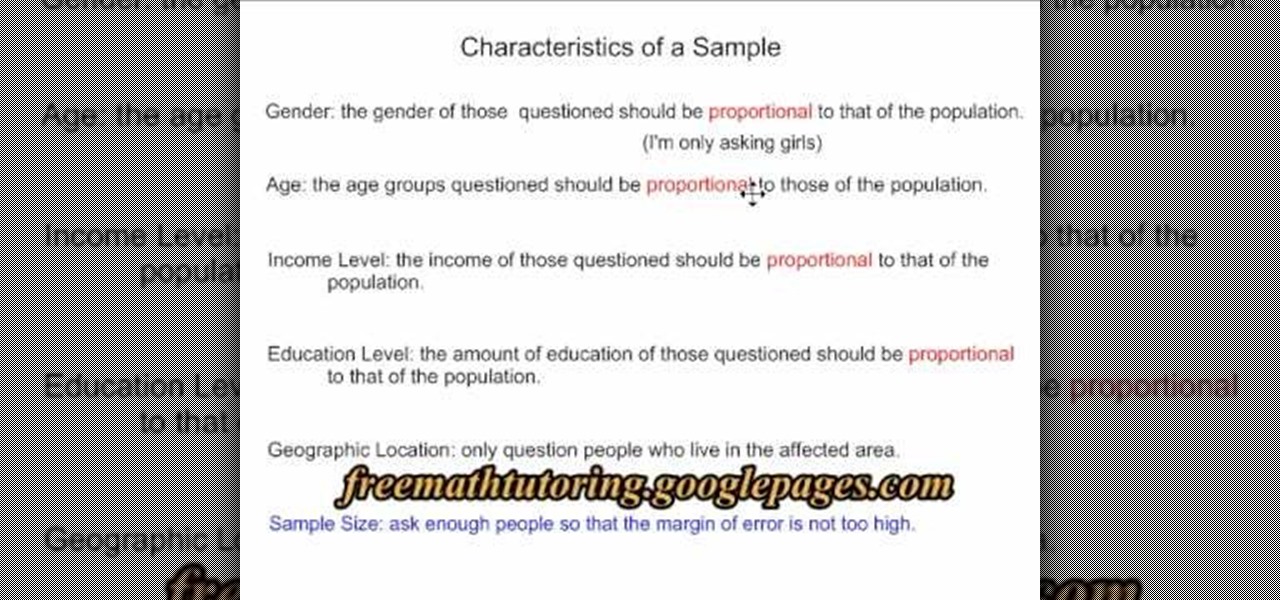
To identify characteristics of a sample in your survey, there are many factors to consider of your samples. The first four characteristics you need to focus on are gender, age, income level, and education level. All four of these characteristics must be proportional to that of the population. You also need to consider the geographic location. Only take samples from the immediate geographical area. Finally, an important characteristic of the survey is the sample size. You do not want to ask to...

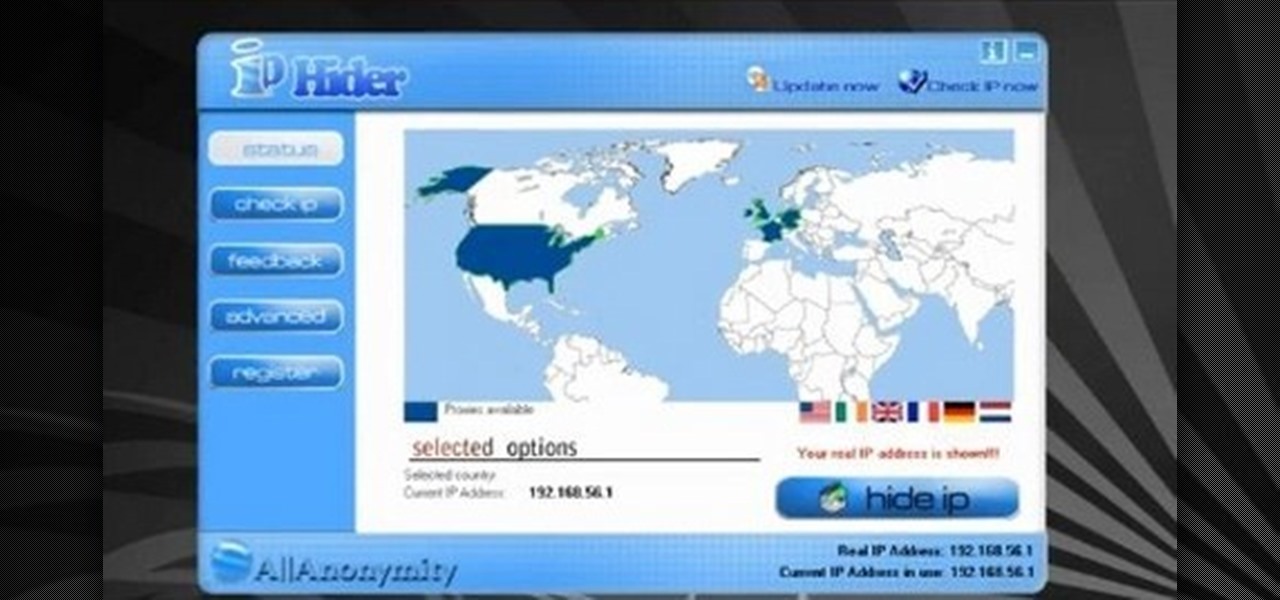
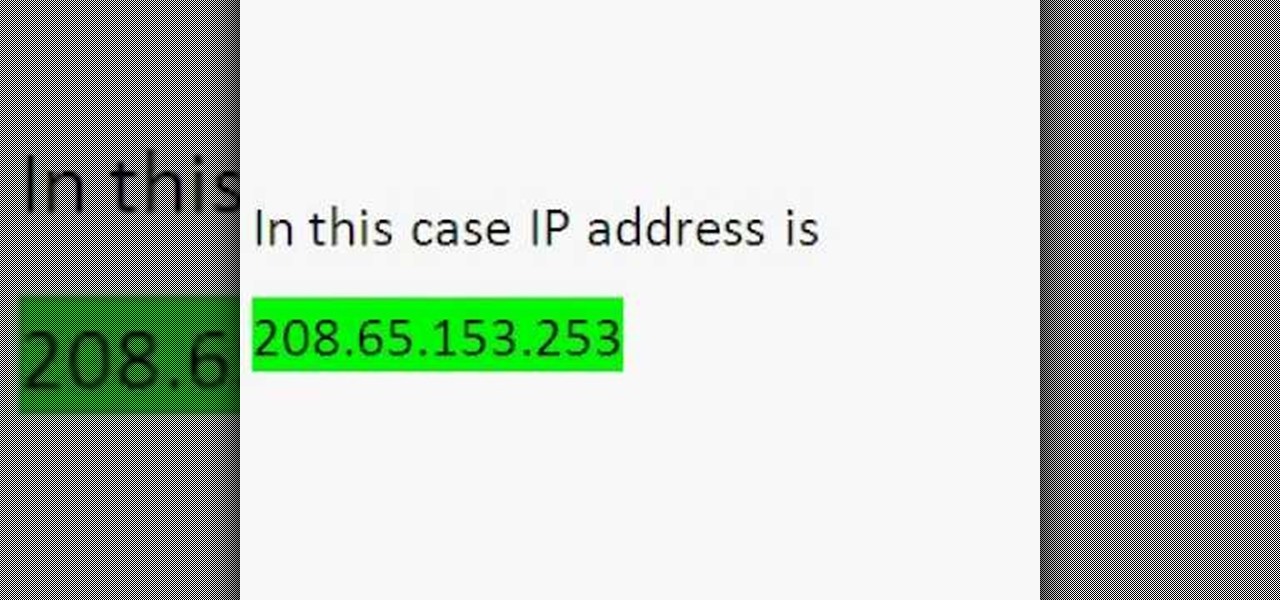
This video describes how to download videos from Hulu.com. The video details how to use a program called "IP Hider". It gives a full description of how to install and start the program, including the location of the program online. This video appeals most to people who live outside of the United States and can't watch American shows on Hulu because their IP address tells the website that they live abroad. This program essentially tricks the website into thinking that the user is within the co...

Wondering how to find the Internet Protocol address of a website?

This video shows you how to draw a cartoon smiley head in Inkscape: Open a new page.

Researching genealogy takes a little enterprise and the skills of a master sleuth.. Watch this video to learn how to research your genealogy and family tree.

This is a video walkthrough of Salamun Bridge in Killzone 2. This includes cheats, glitches and quick play strategies. This game is an FPS.

Check out this Mahalo video walkthrough of Marshlands in Resident Evil 5. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

A map is a map is a map. Unless, of course, it's a map that you're using to navigate around Left 4 Dead. Having a customized map design lets you quickly find safety points, fellow players, and identify zombie locations so you don't, well, die.

This tutorial demonstrates how to create what is called a complete client-server web application which consist of a Web Application, PHP, and MySQL. The tutorial shows how to automatically generate the PHP necessary to talk to a MySQL database using Adobe Flex Builder 3.

Plug this baby into your FiOS-powered computer and simulate the real-time climate of any location in the country -- rain, lightning, fog, sunshine.

In this three part episode, Jennifer goes over the use of prepositions in location and direction in the English language. The list of prepositions is long, so this is meant to be a review and not an introduction. This is great for high beginner and intermediate students learning English as a second language (ESL).

This video walkthrough guides you through the "Forest Temple" chapter of Legend of Zelda: Twilight Princess for the Nintendo Wii including the boss fights and locations of any heart pieces, golden bugs, and poe souls.

While Apple introduced new AR features for iOS 15 and Object Capture for Reality Kit 2 during the WWDC 2021 keynote, updates for ARKit were curiously absent in the official presentation.

The built-in Files app on your iPhone has only gotten better since it was introduced in iOS 11, with small improvements after each new iOS version. You can manage files on your internal storage as well as in iCloud Drive, but one of the best features is being able to manage media and documents from all of your cloud storage accounts in one place.

In the event of an emergency where you can't answer for yourself, trained professionals can view your Medical ID on your iPhone to learn about your medical situation, granted that you have created one. But that's not all your Medical ID can do. With a new feature, iOS can share your Medical ID data automatically with first responders when you place an emergency call.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

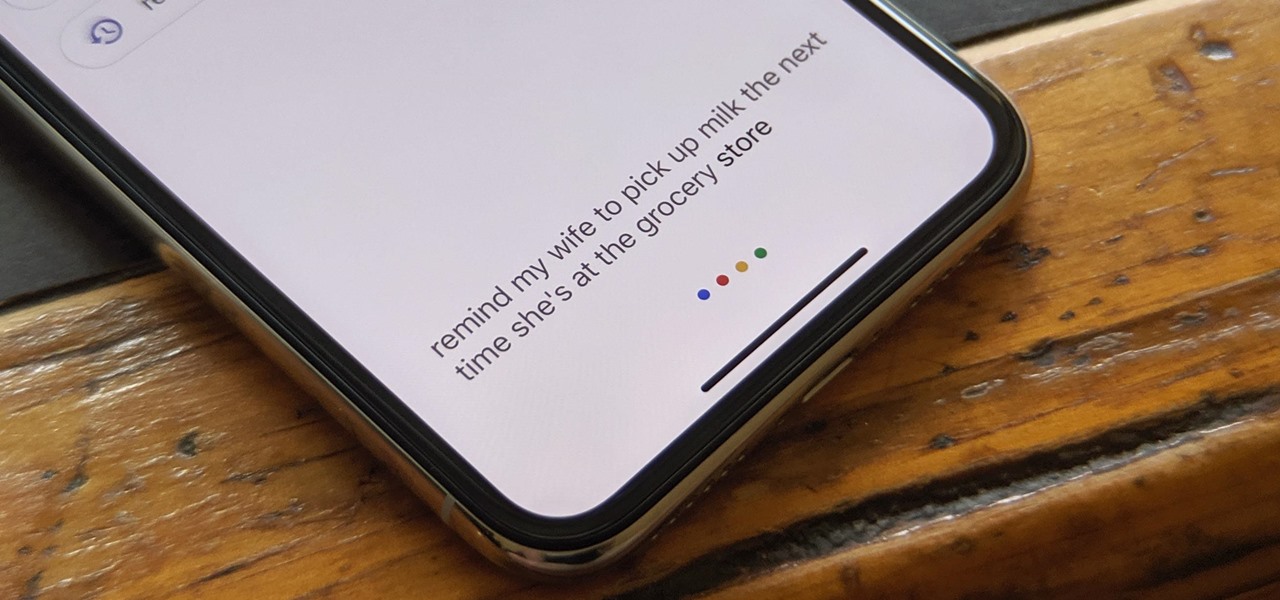
The Google Assistant is available almost everywhere. It powers smart speakers like the Google Home, it's built into Android phones, and it can even be installed on iPhones and iPads. So when Google adds a feature like the ability to send reminders to other people's Assistants, it's far reaching.

London-based developer Andrew Hart has been working on AR navigation since Apple's original ARKit tool was still in beta preview. Now, he's ready to unleash his technology on the world.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

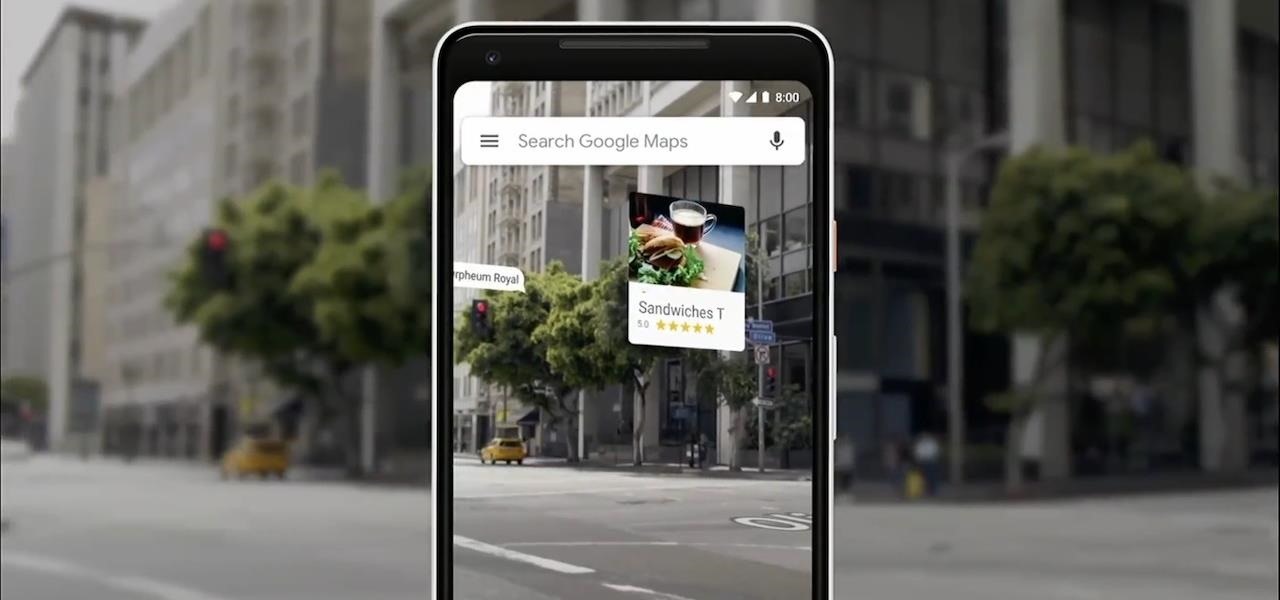
The augmented reality walking navigation mode for Google Maps appears to be closer to an upcoming release for the general public.

It's no secret that MoviePass is a shell of the service it once was. The primary $9.95/month plan for three movies each month is inconsistent and can change drastically depending on your location. Thankfully, MoviePass isn't the only movie ticket subscription service available. We've compared all the best plans on the market to help you find the one that's right for you.

Apparently, it's Google Week for the augmented reality business. Now that ARCore has a firm foothold in the app ecosystem, Google is making a case with educators and marketers that the apps should have a place in schools and campaigns, and the company is also encouraging developers to learn how to build apps using ARCore.

When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, that is.

Among its many new features, Android P returns the spirit of lock screen widgets to users by presenting the current temperature and weather conditions underneath the clock. It isn't flashy, but it's a fun and useful addition that, unfortunately, does not always work. If your lock screen weather isn't showing up, you might want to try these steps to fix it.

Before you go ahead and delete your Facebook — don't lie, you've been thinking about it — consider this. Facebook offers users a wide variety of privacy options to mess with, which can help you find a little control over your information. We're not saying this solves Facebook's privacy crisis, but it might be a more reasonable option than throwing in the towel entirely.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

IFTTT is an application that allows you to automate certain tasks on your iPhone or Android. It can communicate with a myriad of apps and services on your phone by creating applets that perform actions automatically — actions you'd normally have to do manually. Finding those applets, however, can be a little difficult.

Unscheduled pit stops go hand in hand with road trips, no matter how well-planned they are. In the past, making a stop due to low fuel or an emergency bathroom break may have snowballed into massive delays when you went off course on your own, but thanks to a feature in Apple Maps, you can do this in the most efficient manner possible.

Now, when the weather outside is frightful, Pokémon GO players can expect it to be just as unpleasant in augmented reality.

Essential just dropped the Oreo Beta Program for their flagship PH-1 phone. Users have been eagerly awaiting this update as the early Nougat builds of the PH-1 software have suffered from numerous performance issues and lag. The good news is that you can grab the Oreo update today with a few simple steps.

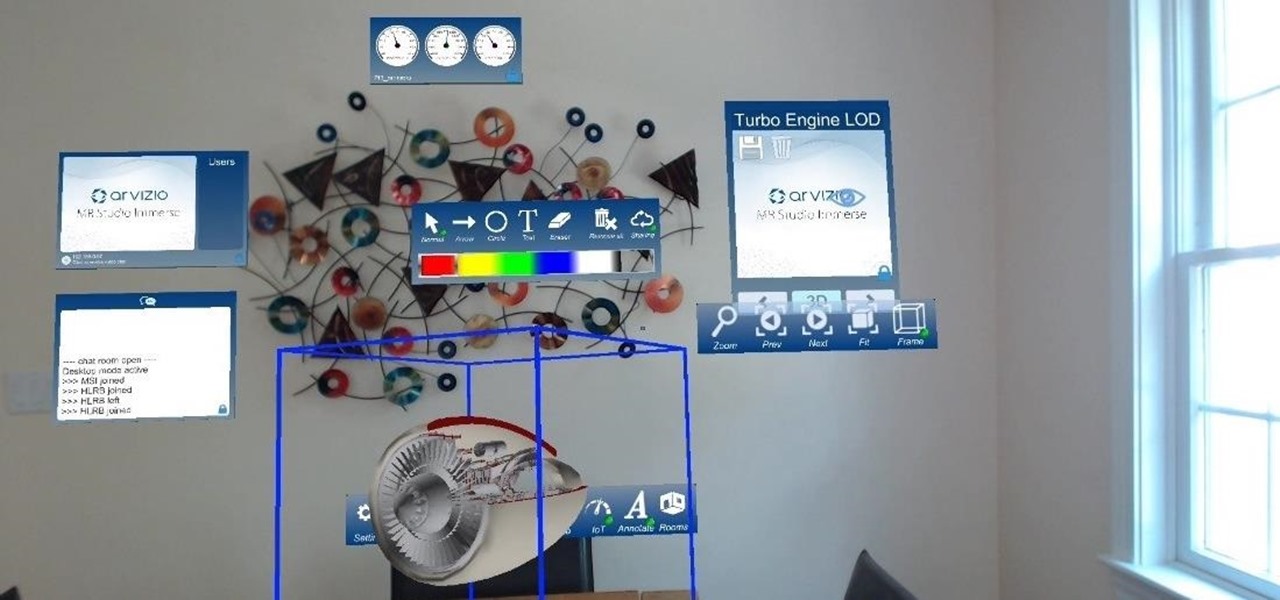
HoloLens developer Arvizio has expanded its collaboration suite of tools for enterprises with a device that can stream and record mixed reality experiences in high-definition for local and remote audiences.

Map apps, while incredibly helpful in our technology-centric world, can often be a source of frustration. No maps app is perfect, and things can get confusing fairly quickly when trying to navigate GPS mapping. iOS developer Andrew Hart has experimented with a new way of mobile mapping using Apple's ARKit that could make finding your way so much easier.