At its core, grilling is the simplest form of cooking. You create extreme heat, you put a piece of food on top of the heat, and then you sit back and watch the magic happen. Yet despite the inherent simplicity in grilling, there are a million ways to make it more complex, more unique, and, yes, even more flavorful.

Ask 100 chefs what the most important tool in their kitchen is, and you'll get 100 chefs saying the exact same thing: their set of knives. For home cooks and professional chefs alike, nothing is more important (or exciting) than a good knife. A good knife allows you to work more quickly, more efficiently, more consistently, and more safely. And best of all, they're just a lot of fun.

Tomatoes are the perfect barometer for kitchen knives and knife skills. If you've ever watched an infomercial for a set of knives, you've surely seen the enthusiastic host waxing about how well the knives cut tomatoes. And if you've ever had your knives sharpened, you've most likely tested them out on a tomato.

Easter may have come and gone, but my love of hard-boiled eggs sure hasn't. Yet as much as I love hard-boiled eggs, I hate making them; I have to work in small batches to have consistent results, and they're always a little overdone, crumbly, and sometimes even green.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

Android has a system-wide user dictionary file that any third-party keyboard can utilize, if it so chooses. This file contains all of the words that you've added to your keyboard manually, and of the big-name players, Minuum, TouchPal, and the Google Keyboard call on this file to determine their user dictionaries.

One of the biggest hits this past fall wasn't a movie, television show, or book—it was an unassuming podcast called Serial, which centered around an unsolved murder from 1999 of a high school student in Maryland.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Mushrooms are glorious: they're nutritional powerhouses, add meaty savor to just about any dish, and are cheap and plentiful (mostly). But just when you thought you knew best how to use edible fungi (in gravies, as portobello burgers, stewed and served over pasta, just to name a few uses), you learn something new: there's a mushroom out there that tastes like maple syrup. Yep, maple syrup.

Welcome back, my nascent hackers!

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.

Like most people who cook in a small kitchen, I'm very wary of adding anything to my drawers and cabinets unless I'm sure it's going to be essential to my cooking arsenal or that it can be used in multiple ways.

First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements

Like many others, I like a good cocktail every now and then, and I've always been impressed when my cocktail enthusiast friends would come up with a new drink or even just remember how to concoct a Clover Club (FYI, it's made with gin, raspberry syrup, lemon, and egg white). There's a secret bartenders and craft cocktail aficionados know, though: It's all about math, the simplest and most intoxicating math. Pythagoras would be so proud.

If you've ever attempted to report a bug to a developer, no doubt you've heard the response, "Get a logcat." This is infinitely important to a developer because of the fact that a logcat captures a full report of every command that was recently executed on your Android device, and it allows them to see exactly where something went wrong.

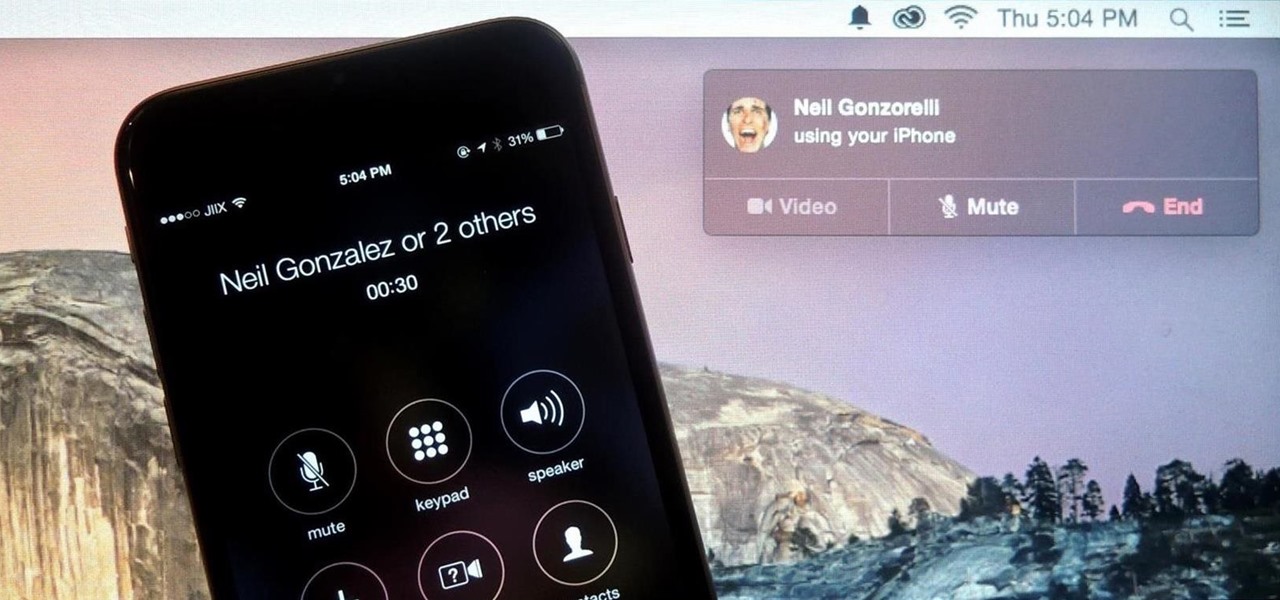
Earlier this year, Apple announced Continuity, a feature for Yosemite and iOS 8 that lets you connect your iOS devices to your Mac in order to access apps, receive phone calls, send text messages, and more while seamlessly switching between the two.

One of the golden rules to cooking a Thanksgiving turkey is to place it on a roasting rack before it goes into the oven. Missing this step and cooking it directly on the pan will burn the bottom of the bird, resulting in overcooked, dry meat.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

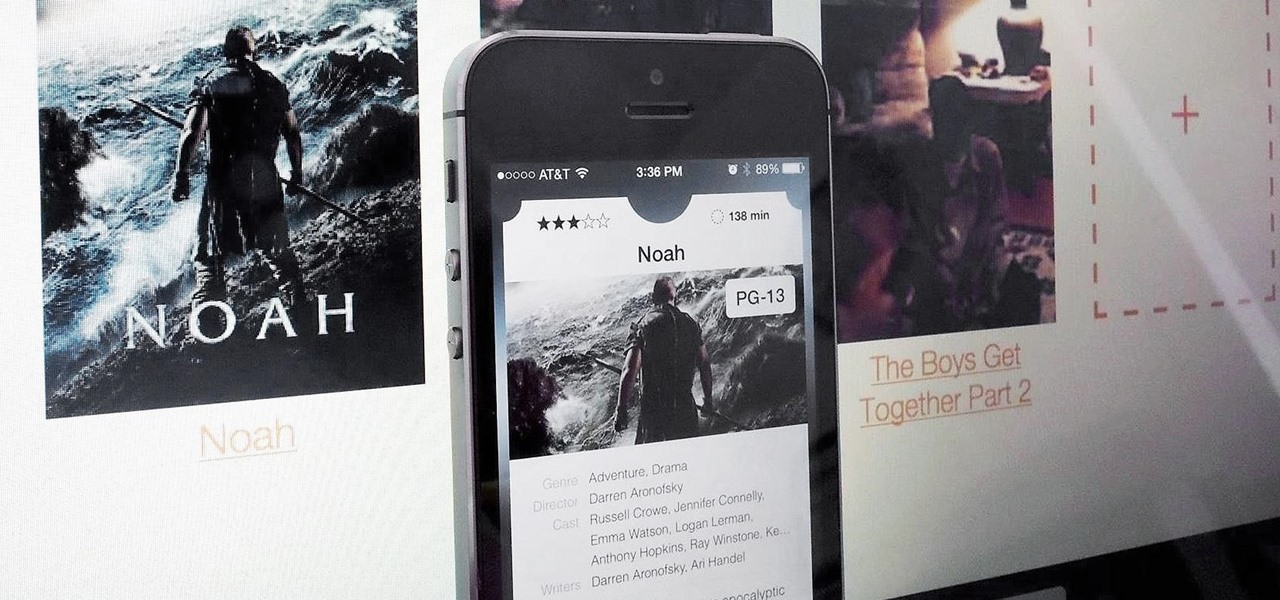
Apple prides itself on simplicity, but the company makes downloading video and music files onto your iPad or iPhone an overly complicated process, requiring iTunes and/or iCloud.

It's a shame that one of the world's tastiest foods can be such a pain to prep. Most cooks are familiar with this conundrum: chopping or crushing garlic releases a pungent liquid that causes bits of garlic to stick your knife and hands, creating a messy affair. So what is going on here? The common assumption is that the garlic is releasing some kind of oil, but the truth is that this liquid rinses away easily in water. Yet one of the basic precepts of chemistry is that oil and water don't mix.

It's pretty logical for your MacBook to sleep when you close its lid, but under certain circumstances, you may not necessarily want this feature to kick in.

Can you tell when someone is shooting you a fake smile? Even though fake smiles are easy enough to see through, we all still do it, attempting to show others just how happy we are when we're really feeling less than fantastic. Unfortunately, every smile we fake makes us a tiny bit more miserable.

As much as app developers would like to simplify things with icons and visual cues, text is still a huge part of a smartphone's interface. Much of our media consumption is text-based, and while Google's Roboto font is a beautiful typeface, a little variety here and there certainly wouldn't hurt.

I may not be a parent just yet, but I've dealt with enough worrisome mothers to know that keeping a watchful eye over your child is of the top-most importance. Since most people cannot afford to stay right by their child's side 24/7, developers are always looking for ways to make the pain of stepping away a little less stressful for parents.

I don't deep fry food that often, mostly because it uses a ton of oil, which is expensive, and the cleanup is a son of a mother. (That oil really splatters everywhere.) Plus, no matter how careful you are, you will get hit by hot oil at some point and it will not be pleasant.

Accessing your favorite and most recent contacts on your iPhone is now faster than ever before, thanks to the iOS 8 update. Just double-click your Home button, select your contact above the app switcher menu, then choose how you want to contact them.

"Cooking" with liquid nitrogen seems like one of those activities that should be strictly limited to pros who are appearing on Top Chef, but it's the only way you'd ever be able to make Dippin' Dots at home. If that isn't enough of a reason for you to get some LN2 for your kitchen, check out this dose of pretty:

Pies and soufflés: these are two dishes that can try even the most experienced cook. Berry pies can be especially challenging, since the high water content of cherries, strawberries, blueberries, and blackberries often leads to a big, leaky mess once you cut into your beautiful pie.

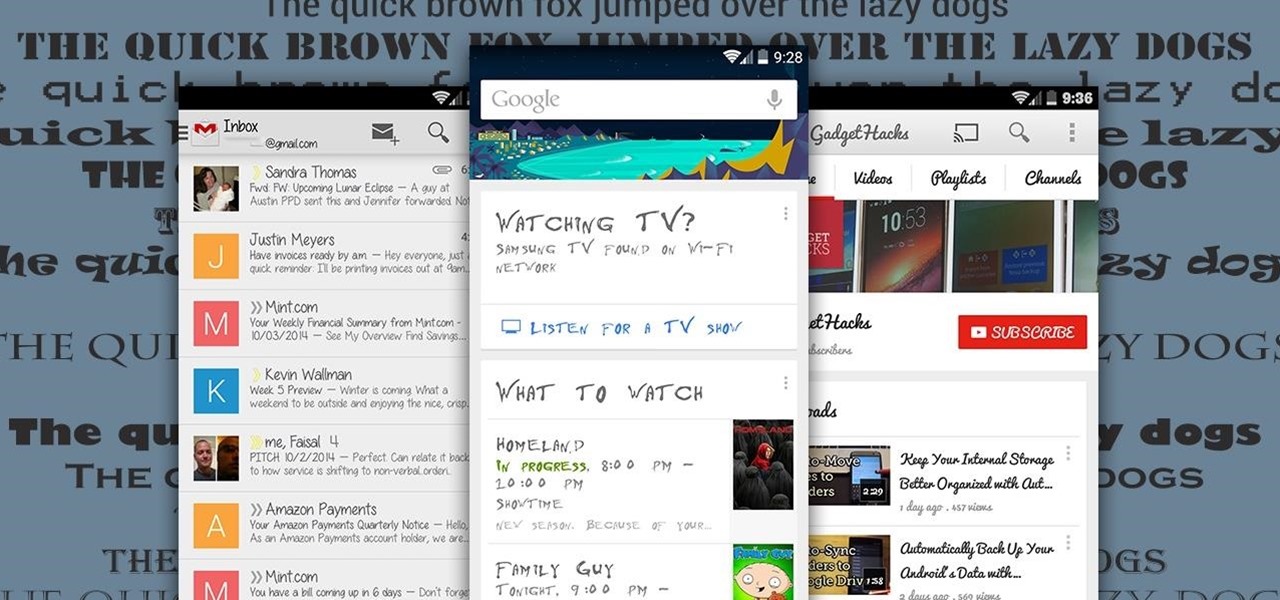
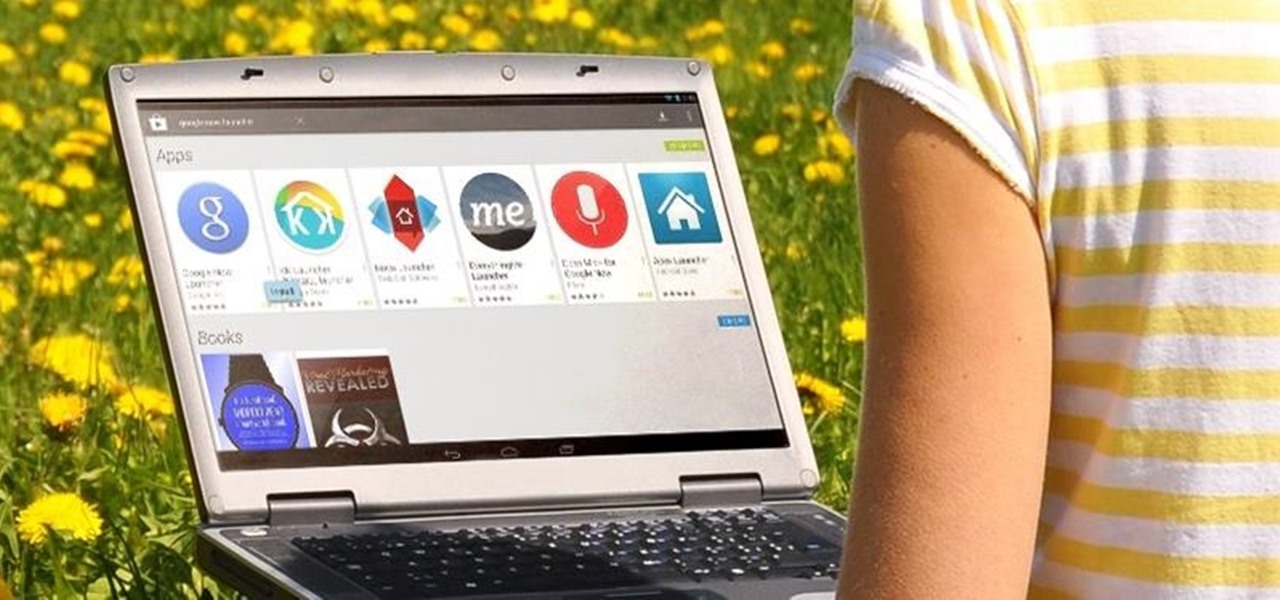
There are tons of good reasons that you might want to use Android on your desktop. Perhaps your favorite game is only available on Android, or maybe you use a messaging service that doesn't have a Windows companion app.

A huge chunk of my life revolves around my computer, and whenever I'm on my laptop and get a text message notification on my phone, I find it extremely distracting to stop whatever I'm doing to hunt it down. That's why I'm a big fan of text messaging via my computer.

When you're not using your phone, it doesn't make much sense that it would be wasting power by maintaining an internet connection for the inside of your pocket or purse. Well, perhaps you need a little bit of intermittent data here and there so that apps can update themselves in the background and still post notifications, but it doesn't need to be constant.

As this generation continues to evolve, we become more involved with social media. For example, you may have a Facebook, Twitter, and a Google+ account, and be heavily involved in using all three, but the constant switching between sites, logins, and conversations can get very tedious.

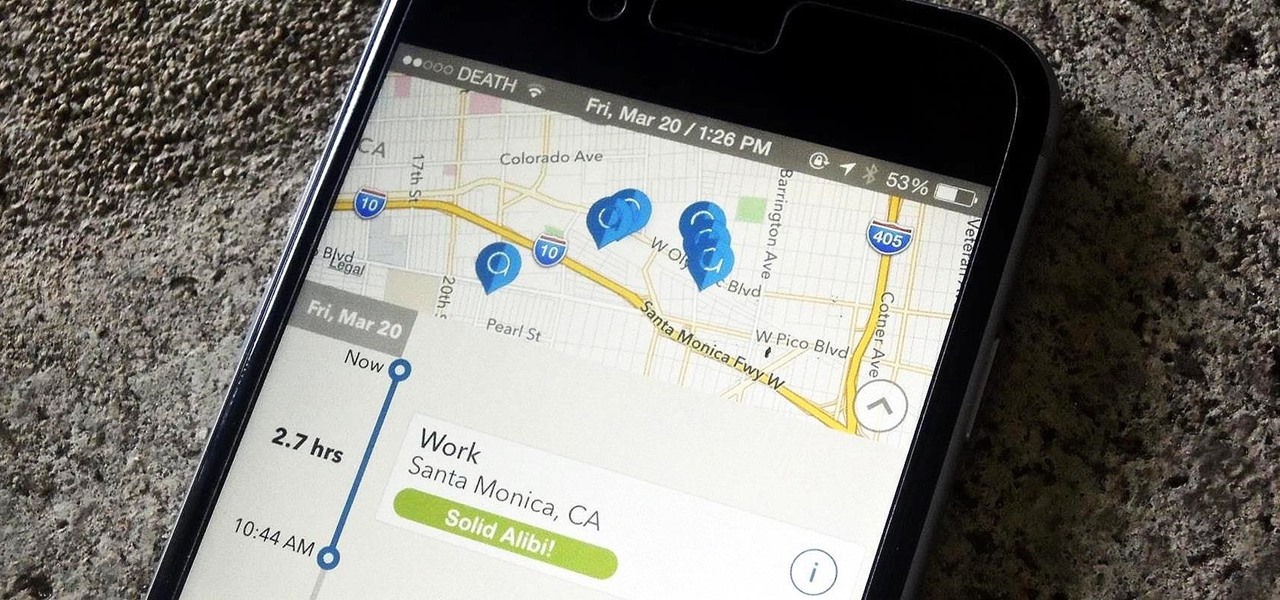
Developing an imperceptible lie is difficult, especially when you're lying right to someone's face. Thanks to smartphones, getting people to trust you is now easier than ever. You can craft a lie in seconds and hit send, all without ever seeing their untrusting faces.

Although lacking in megapixels, the HTC One M8's camera can be considered a top-tier, flagship-level shooter. With the Duo Camera and UltraPixel technology behind it, it can make even the most inexperienced photographer snap pictures like a pro. There seems to be little missing for the average user, but for the more seasoned photographers, some of the standard settings may seem a bit too dumbed down.

The newest version of iOS 8 beta is now out. Almost three weeks ago, in the iOS 8 beta 2 release, we saw podcast integration, full-screen caller ID, new assistive touch toggles, and a "disable all" button for app notifications, among other things.

Text input on a touchscreen device is constantly evolving. From early beginnings of pecking out each individual character to today's predictive text and gesture keyboards, we've already come a long way.