Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

Welcome back, my newbie hackers! Recently, I "upgraded" to Kali as my hacking platform, despite my preference for BackTrack. I did this reluctantly, primarily because new readers here could no longer download BackTrack from their site. I want to point out here that we all must keep in mind that with any software—or for that matter, any product—that is newer is not necessarily better.

One of the most common complaints about the Nexus line of devices is that they don't have expandable memory.

The way you use your camera just got a bit more interesting. Phogy, a brand new camera app for Android, allows you to capture pictures with a 3D effect that comes alive when shifting your phone from side to side.

Welcome back, my greenhorn hackers!

The international hit Xperia Z2 may be headed to Verizon if a posted, and quickly erased, image is any indication. Take this information with a grain of salt—I certainly am—but this could be Sony's entrance into the non-GSM realm. The image above was posted to Sony's Xperia Google+ page, and very quickly removed. Compared to the Z2 that's currently on the international market (below), we can see that not only has the Sony logo shifted to the bottom, but a Verizon logo rests squarely along the...

Did you know that using your Nexus 5 can deprive you of sleep—and not just because you can't seem to quit playing that addicting game or watching Netflix videos?

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

It can be a pretty exasperating ordeal to hunt for one image on your tablet when you have hundreds and hundreds of photos in your gallery. Luckily, there are ways to make this a pain-free process on your Nexus 7, as well as make sure it's never a problem in the future.

Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.

Last week, I showed you why your refrigerator is one of the best tools in the kitchen when it comes to saving money and preserving food at its tastiest. But did you know your freezer is another underutilized ally in the cooking game?

Windows 8's interface was met with criticism when it was released, mainly directed at the tiled Start screen, a departure from Windows versions of old. Many felt that this new home screen style was better suited for mobile devices like Microsoft's Surface tablets and Windows Phones.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

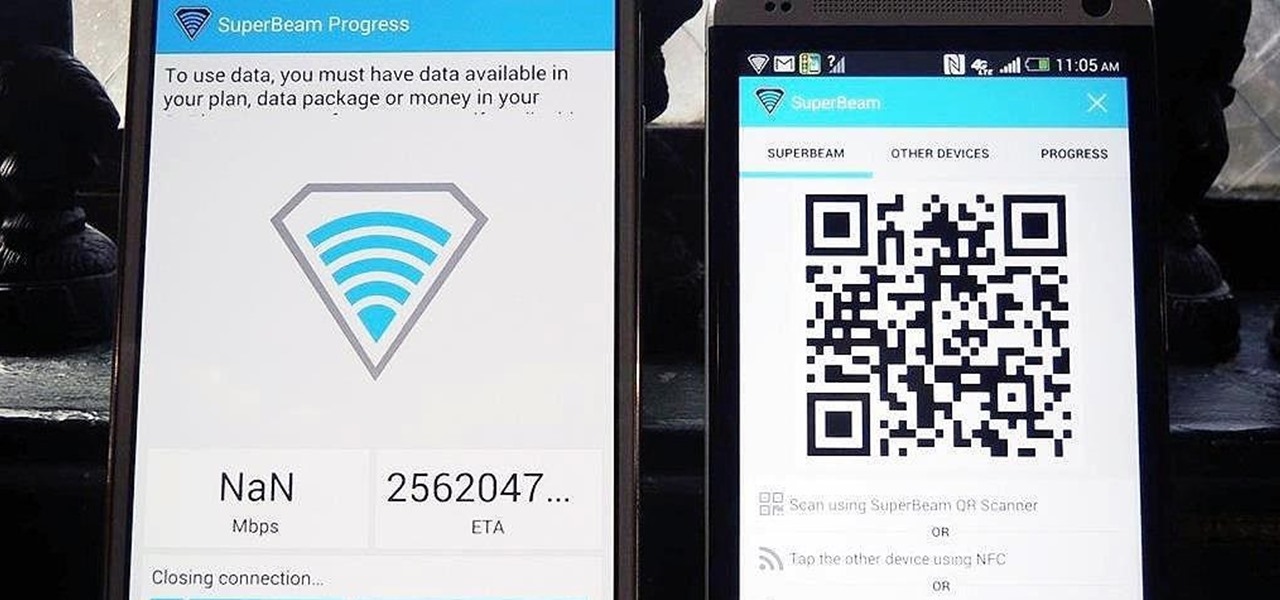
Sending and receiving files between Android devices has no shortage of options—Bluetooth, email, MMS, and Wi-Fi are just a few of the more popular ones that we use.

With a 5-inch screen, it's possible that the Samsung Galaxy S4 can be a bit large for our hands. While my grubby hands let me navigate the phone pretty easily, the same can't be said for everyone. A lot of us use two hands to type on the phone, play games, and perform tap or swipe gestures.

Not too long ago, we told you about a new feature within Android KitKat that allowed for video recording directly from the screen of your Nexus 5. Though functional, the method was a bit clunky and involved hooking your phone up to your computer and sending over an ADB command to start the recording.

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.

Sometimes, you just don't want to hit the Power button to turn your screen off. In the current age of touchscreens, you've got to wonder why we even have physical keys anymore.

As far as lock screens go, your Samsung Galaxy S4 and other Android phones offer quite a few options. You can use the classic PIN unlock, the novelty facial recognition, or the reliable pattern lock. But what if you get tired of entering the same old PIN or pattern every day?

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

70 degrees, 8 mph winds, and sunny clear skies. That's the current forecast here in Los Angeles and I can't really complain. However, if you don't live in Southern California, checking the weather may be the difference between getting stuck in a snowstorm or remembering to bring an umbrella.

What kind of music do you like? It's a classic first date question that reveals so much about the person answering, but when it all comes down to it—everyone likes or listens to music. We may each have our own unique tastes and interests, but music is usually something almost anyone can get behind.

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

The 8-bit NES may have ruled the late-eighties, but the SNES took over the early-nineties with its 16-bit graphics and 3D-like gameplay on titles like Star Fox and Dirt Racer. When 32- and 64-bit consoles came out in the mid-nineties, the Super Nintendo took a hit, but with the rise of the Internet, created a huge emulation community in the aftermath.

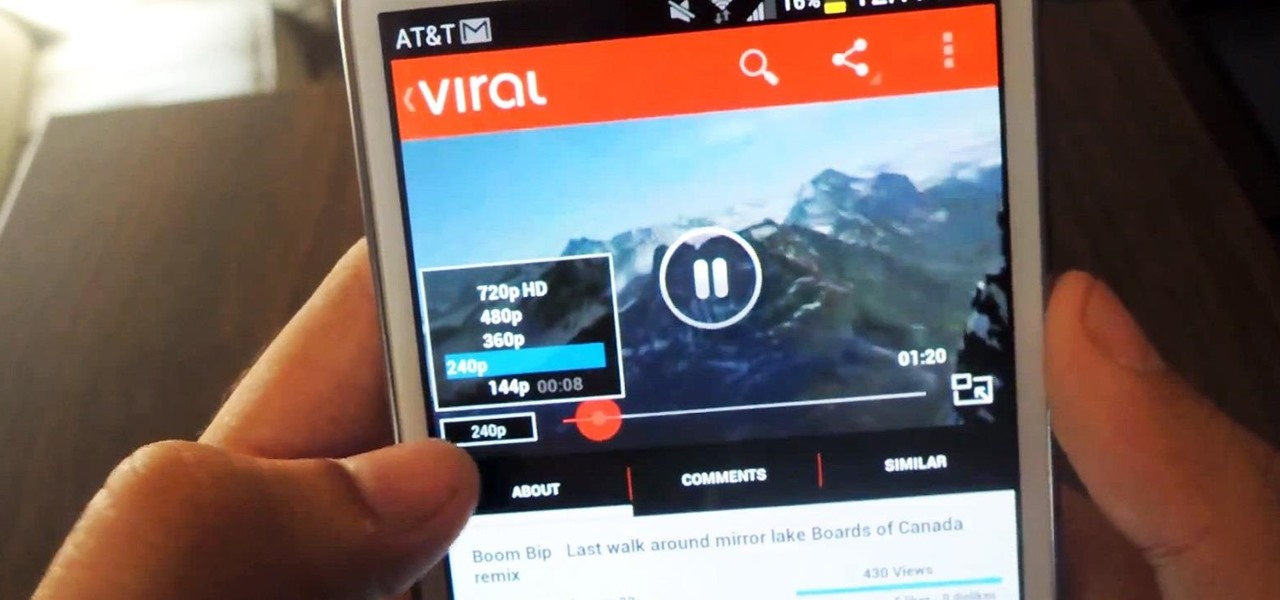
Let's face it, the stock YouTube app for Android kinda sucks. It has limited capabilities, at-time wavering connectivity, and the pop-up player it comes with is just not very good. If you want to enhance your mobile YouTube experience to how it should be, the answer lies within a third-party app called Viral HD YouTube Popup Player by Android dev Mata.

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

The design of iOS 7 has its lovers and haters, and if you're an Android user who just happens to love it, there are plenty of ways to make your device feel more Apple-y.

As things begin to clutter on your device, navigating through it can become much more difficult than when you first got it. The sheer number of added apps and mods that build up after time take its toll not only on the quickness and memory of your device, but also on your efficiency to access everything easily.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

On the new Moto X smartphone, the only thing you have to do to activate the virtual assistant is say "Okay, Google Now." That's it. You don't have to press a button or tap on the display at all. It's always ready for your voice commands via its "Active Listening" feature, making it a truly hands-free experience.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

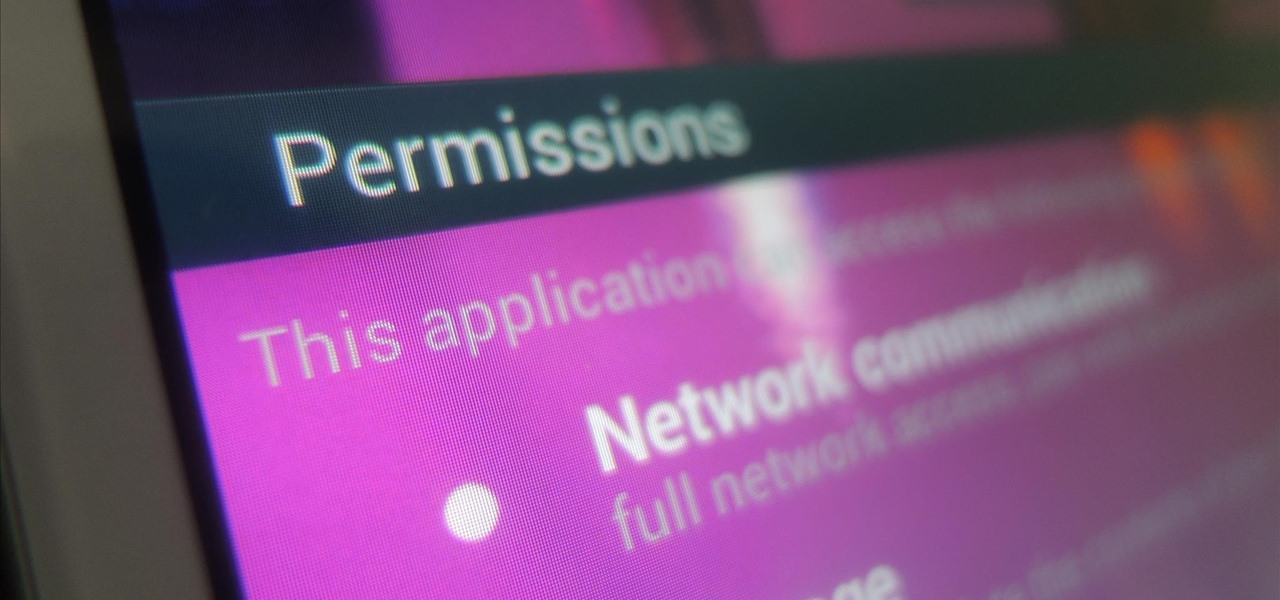
While we're usually responsible for leaking our own private information through mediums like Facebook, there are other times when we mistakenly and unwillingly allow certain applications to scour through our personal data. Some apps may have enabled permissions for internet access, thus allowing it to share said data with its external servers.

If you have a load of dusty Game Boy Advance games you've been itching to play, load them onto your Samsung Galaxy Note 2 for instant gaming anywhere—anytime!

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

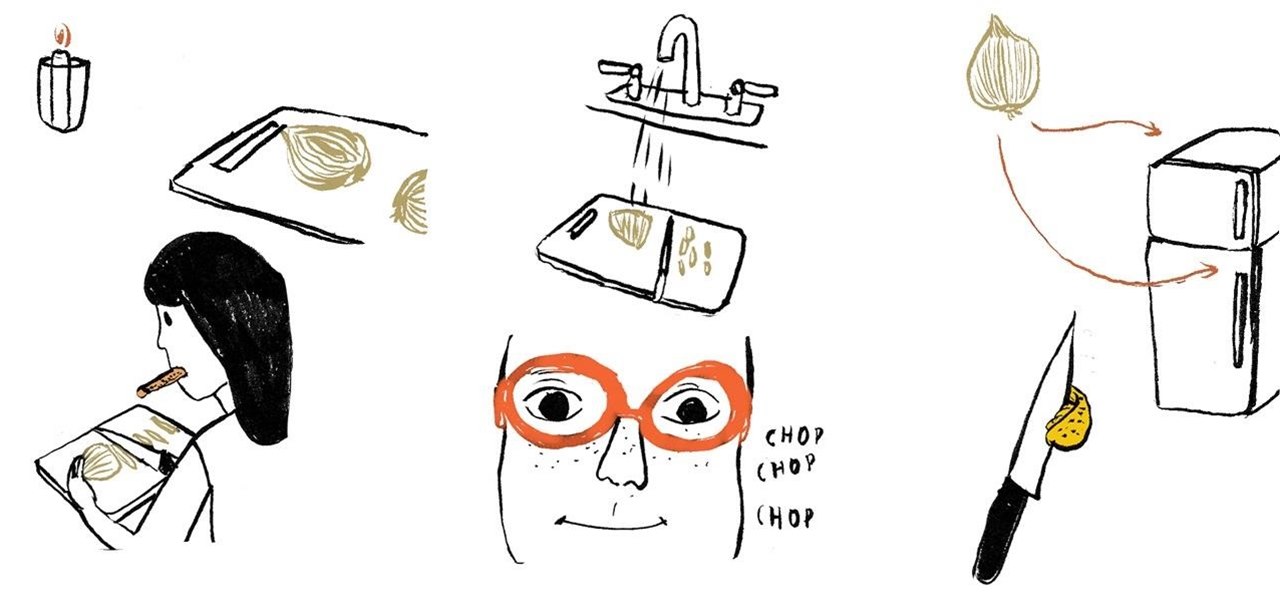
Is it possible to cut or chop onions in the kitchen without stinging eyes and looking as if you just watched the saddest movie ever? Before we get to that answer, it's important to know why we tear up when cutting raw onions in the first place. What is this irritant? Are you reacting to the odor? The answer to the latter question is "no," and the irritant responsible is amino acid sulfoxides.

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.