Smartphones are great. They help you keep in touch with your loved ones and stay up to date on what's going on in the world. The problem is that like everything else that's useful, they cost money to use, and between calling, texting, and data plans, it can get really expensive.

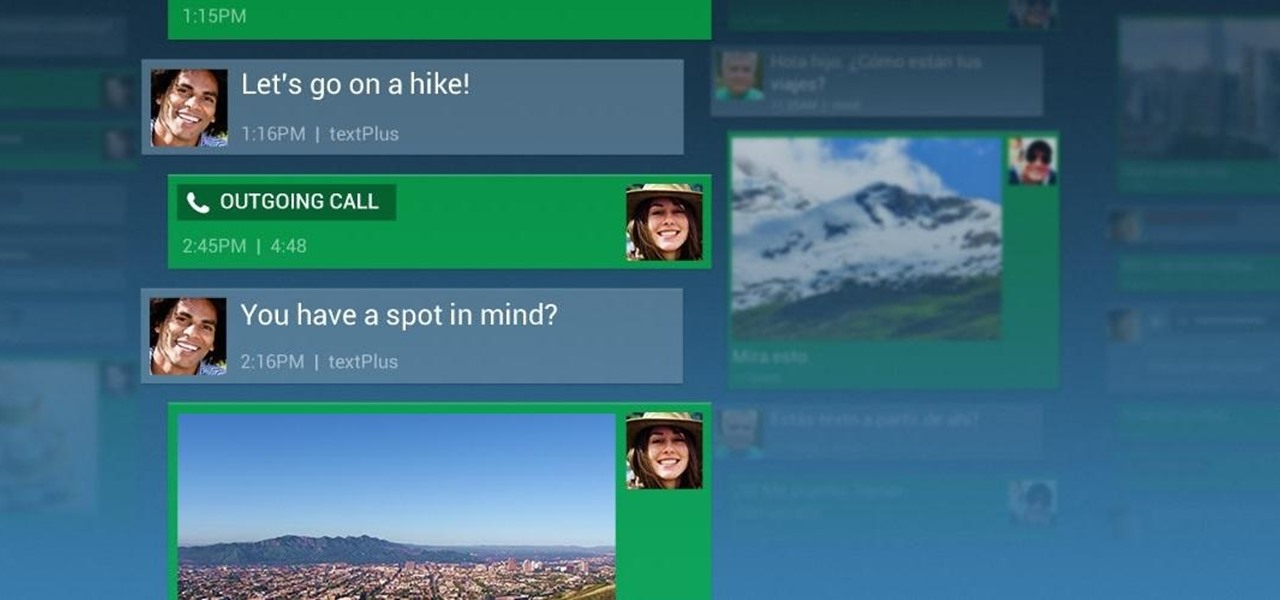
A lot of people text nonstop, but there are situations where it's either not allowed or considered rude to use your phone. Let's say you're in class or in a meeting at work, band you're expecting an important message or phone call. Rather than trying to check your phone discreetly, wouldn't it be better if you could just see your calls and messages on your computer?

There's really nothing safe about transmitting sensitive information electronically, but even if it gets there safely without being seen by prying eyes, there's no guarantee what happens to it once it reaches its destination. And let's face it, there are some things that you just don't want floating out there forever. So what can you do? Whether you want to send an email, a text, or a link, there are ways to send messages that self-destruct so that once they're read, they immediately vanish. ...

Have a super secret spy communication you'd like to send out, but don't have the funds to hire your own trusted operatives to deliver the message? Then stick to what you're used to—email it. SafeGmail is a browser extension that allows you to send encrypted emails right through your regular Gmail account. While this may seem a bit unnecessary for most messages, encrypting your email can definitely be useful.

In our society, multitasking is an obsession. Whether it's driving while using your phone (DON'T DO IT) or drinking a cup of coffee while typing up some work, we multitask at every turn of the day. People that work all day in front of a computer are especially prone to multitasking, and that's why XDA-Developers member Floyd1973 has developed a way to control any Android phone while connected via USB to a Windows or Linux PC. Android Remote Phone Tools
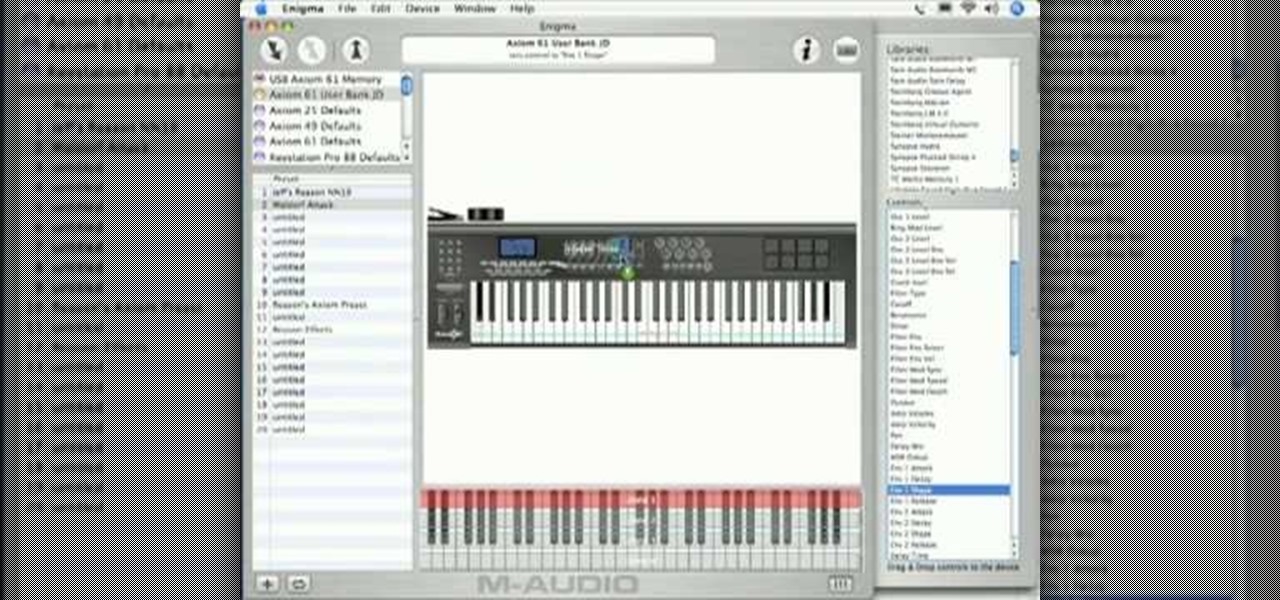
In this tutorial, Jeff Dykhouse demonstrates how to use the powerful Enigma Editing Software to assign MIDI message to all the different controllers that the Axiom 61 keyboard has at its disposal. Jeff covers: Downloading Presets, Creating User Banks and Loading and Creating Presets. You can use the Axiom 61 with Reason, Ableton Live, Pro Tools and even GarageBand.

Politics(the Government) is built to accomplish a few things: maintaining order, providing necessities, operating businesses (stimulating the economy, trade), maintaining public relations and the most important of all, protecting the rights of the individuals it governs. It has a broad role, and as such, an array of bills, laws and rules to regulate itself and the country.

As a kid I fell in love with stop-motion animation while watching the superb mastery of Ray Harryhausen (who didn’t? I mean, skeletons! Fighting!).

Via WonderHowTo World, LoadSave: Rock Band 3, coming this Fall, was revealed at none other than USA Today. Fully functional 25 key keyboard, 80+ songs including The Doors and Bohemian Rhapsody, Pro mode, updated guitars, and a kitchen sink are included in this new sequel. USA Today:

Rock Band 3, coming this Fall, was revealed at none other than USA Today. Fully functional 25 key keyboard, 80+ songs including The Doors and Bohemian Rhapsody, Pro mode, updated guitars, and a kitchen sink are included in this new sequel. From the article:In addition to the new keyboard controller, also due for the game's release are two advanced guitar controllers that take advantage of the Pro mode, one a full-sized, fully functional Fender guitar (all sold separately, no prices yet).Other...

This video demonstrates how to send and receive text messages on your iPhone. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to send and receive text messages on your iPhone, For Dummies.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to shoot and share video on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

This video is on how to setup the axon racing anti gravity razorback racer. it involves receiver installation, zeroing your servo with the trims and lifting the horn, programming the esc, installing the lipo, testing the unit, initial turn on.

HP TouchSmart comes with a lot of inbuilt powerful features. Voice notes is one of them. To use this feature tap on the notes icon on the HP TouchSmart home page. Now tap on the microphone icon which is present at the bottom left of the screen. The TouchSmart contains two microphones that are integrated into you computer and are present on the either side of you web cam at the top of the screen. To record a voice message tap the record button and speak into the microphone. Tap the stop button...

Sending and receiving email on the go is made easy with the Apple's "Mail" app on the iPhone. However, up until the release of iOS 5, plain text was the only option for sending emails (even though well-formatted messages could still be received). The information below, coupled with unlocking the emoji keyboard will make you an unstoppable force of communicating accurately.

I'm sure we've all heard about MSN and Yahoo! Messenger, right? They can be useful, but the setup can be quite time consuming for those who need to use it just once or twice—and the privacy statements are a real bother. For example, we must provide our real details. You could use Fake Name Generator, but if you get caught, you will have your account suspended. I don't have a law degree, but to my understanding the United States recently passed legislation that gives the authorities the power ...

You can quickly correct a mistake in an iMessage you send, but the recipient will still see whatever you originally wrote since there's a history of edits. When you don't want the other person in the conversation to know what you originally sent, there's a better thing you can do.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

What could Apple be planning here? Are we going to see some revolutionary new features for the iPhone? Will we see mostly bug fixes and security patches? It's time to find out, as Apple just released the first developer beta for iOS 13.4.

Phones these days are expensive. The iPhone 11 Pro is presumed to start at $999, following the iPhone XS and iPhone X's leads. One way to bring down that cost is to trade in your old iPhone, but there isn't one clear-cut way to do that. You could trade your iPhone into a participating website or put yourself out there and sell the iPhone on your own. It's all about what's best for you.

With new iPhone models out, you'll have updated cameras to try out, a faster processor, and new colors to choose from. The only thing that could stop you from picking one up yourself is, well, your current iPhone. Here's how to check if you're eligible to upgrade to iPhone 11, iPhone 11 Pro, iPhone 11 Pro Max, or any other iPhone still being sold.

Despite years of user complaints, OEMs are still preinstalling third-party apps on brand new devices. Even in 2019, you'll still find plenty of phones with Facebook preinstalled. What's worse, it's installed as a system app, so it can't normally be uninstalled without root access. However, there are a few workarounds.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

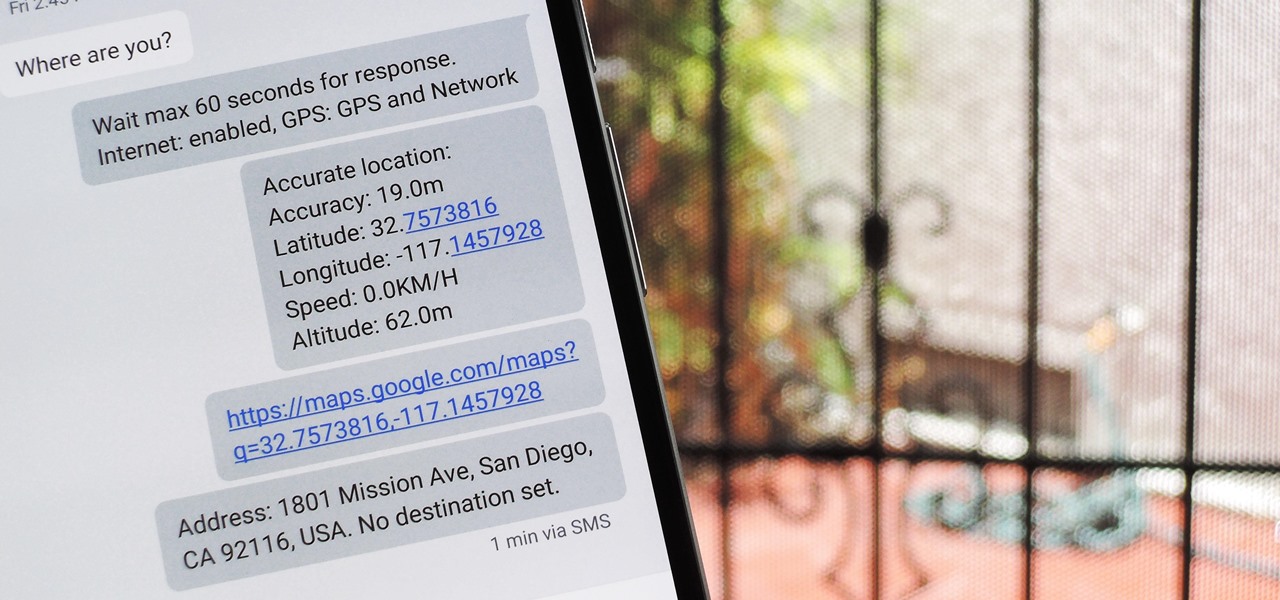
You're at the bar, but your friend can't find you. You could call them, but that wouldn't feel very 2018. Instead, let your iPhone do the talking. Right in the Messages app, you can easily send your friend your current location — all without interrupting the friends you're hanging out with.

If you have an iPhone, you probably know that iOS 11 hasn't been the smoothest iOS version released, to put it lightly. We've seen bug after bug cripple the software's usability, many times within the Messages app. Now, yet another glitch has emerged to drive us crazy, one where just a simple Indian character can crash Messages as well as other third-party apps.

If you use the Google Assistant on your Android device, you can easily send a text message to any one of your contacts. But even though that same Assistant is powering the Google Home, you can't use the smart speaker to accomplish the same task — at least, not without some tinkering.

Out of all the new changes in iOS 10, the most noticeable difference is a handful of fun new features that were added to iMessage. Not only can you now send GIFs directly from the Apple-exclusive messaging platform, but there's now an entire App Store dedicated to bringing fun new stickers and other cool add-ons to iMessage.

When you're driving, the last thing you need to be doing is messing around with your phone. But these days, people expect you to be available at all times, so the text messages continue to flow in while you're on the road. It's a terrible distraction, and one that is responsible for 25% of all car wrecks in the United States.

Hello guys, I recently made a how to about whatsapp but the problem with that script is that it is way to long and you need to copy and paste it so many times so I made a new one that works just fine and is more easy to use lets get into it (Here Is How The Code Supposed To Look)

Students have been passing notes in class for decades, so what's the big deal about sending a quick text message? Everybody does it, even your teacher was surely guilty of covertly communicating with his or her peers back when they were in high school.

In 1987, two brothers, Thomas and John Kroll, began work on an image editing software, which was eventually acquired in 1988 and released to the world in 1990 by Adobe. That software was Photoshop 1.0, initially exclusive for the Macintosh platform. Over the years, Photoshop became a great wizard of image editing and gained application rockstar status.

Let's say you're flush with Google Opinion Rewards credits, or you just got a Google Play gift card for your birthday. This is a perfect opportunity to remove ads and unlock new features by upgrading some of your free apps to their paid counterparts, or to finally purchase that app you've been lusting after that doesn't offer a free version.

Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series to demonstrate how to do the hacks he uses in the show.

Disclaimer: All information in this tutorial is for entertainment and educational purposes ONLY. You pesky teenagers.

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

In today's world of ordering food from your PC or hailing a cab with an app, it almost seems archaic when we have to actually use our vocal cords to contact a local business. It sure would be nice if we didn't have to use our smartphones as, well, you know...phones.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.