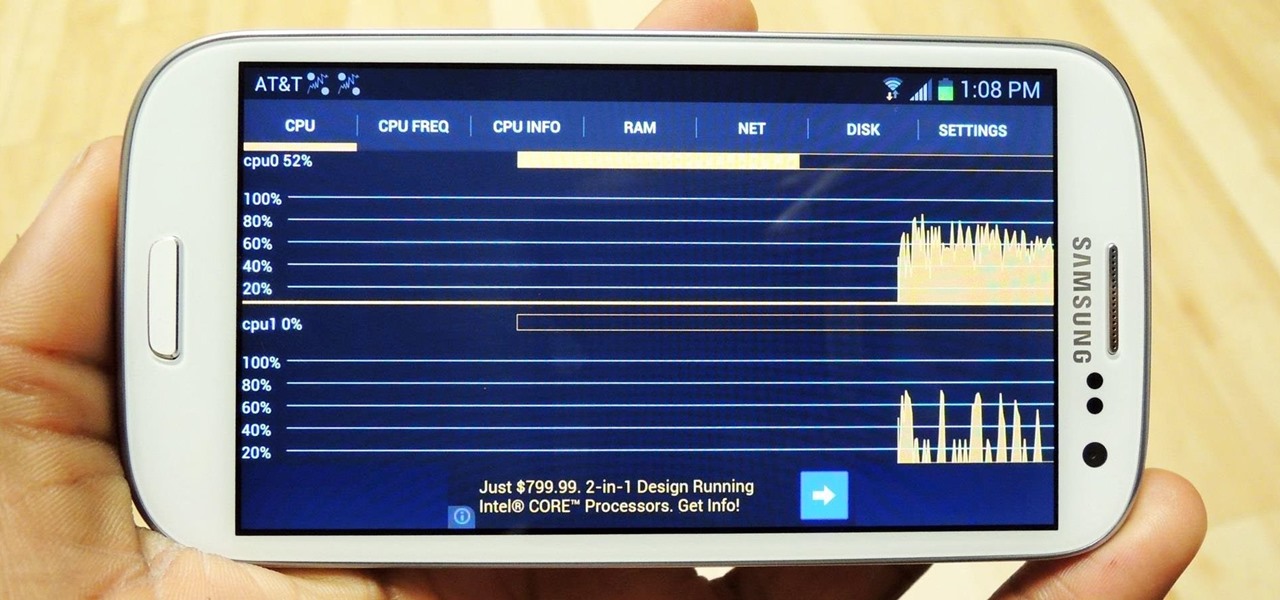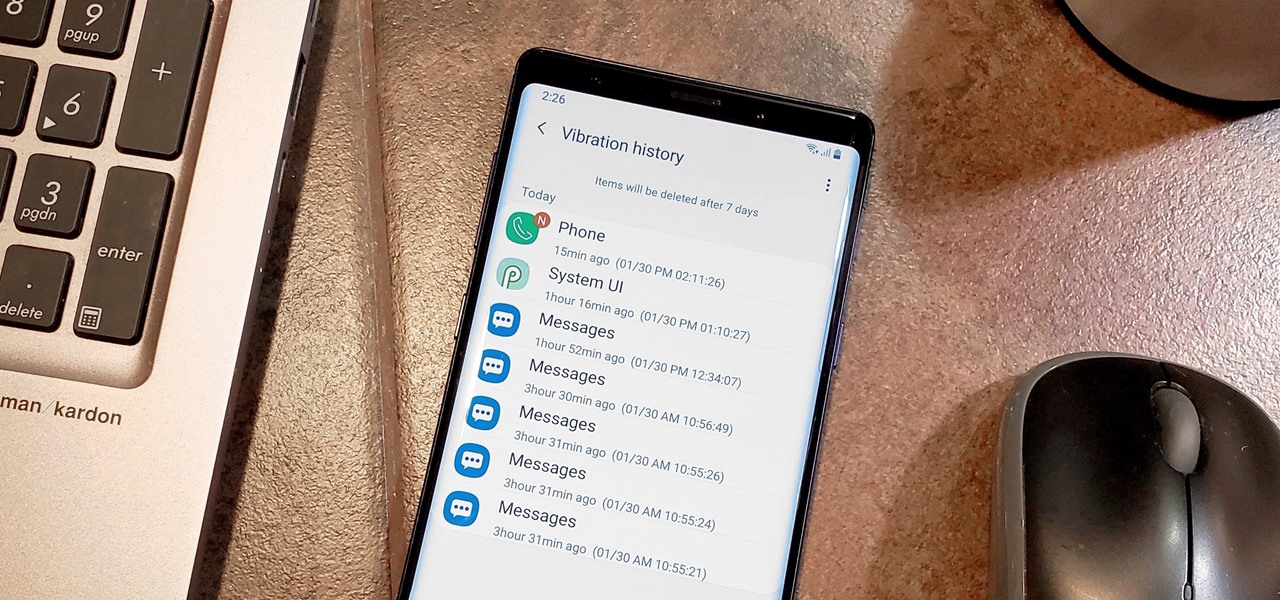
Random vibrations, ghost buzzing — whatever you call it, when your phone goes off for seemingly no reason, it's pretty frustrating. Finding the source of a phantom vibration can be almost impossible if there's no associated notification, especially given the myriad apps and system processes that run on your Galaxy device.

While the iPhone XS and XS Max come equipped with 4 GB of random access memory, and the iPhone XR with 3 GB of RAM, Apple's latest flagships are still susceptible to occasional slowdowns in performance in iOS 12. This can be fixed by clearing RAM, but the process is now a little trickier compared to iPhones with Home buttons.

French manufacturer Renault Trucks is looking to the HoloLens to improve quality control processes with its engine assembly operations.

On the airplane, in the middle of cold and flu season, your seatmate is spewing, despite the clutch of tissues in their lap. Your proximity to an infectious person probably leaves you daydreaming (or is it a nightmare?) of pandemics and estimating how likely it is that this seatmate's viral or bacterial effusions will circulate throughout the plane and infect everyone on board.
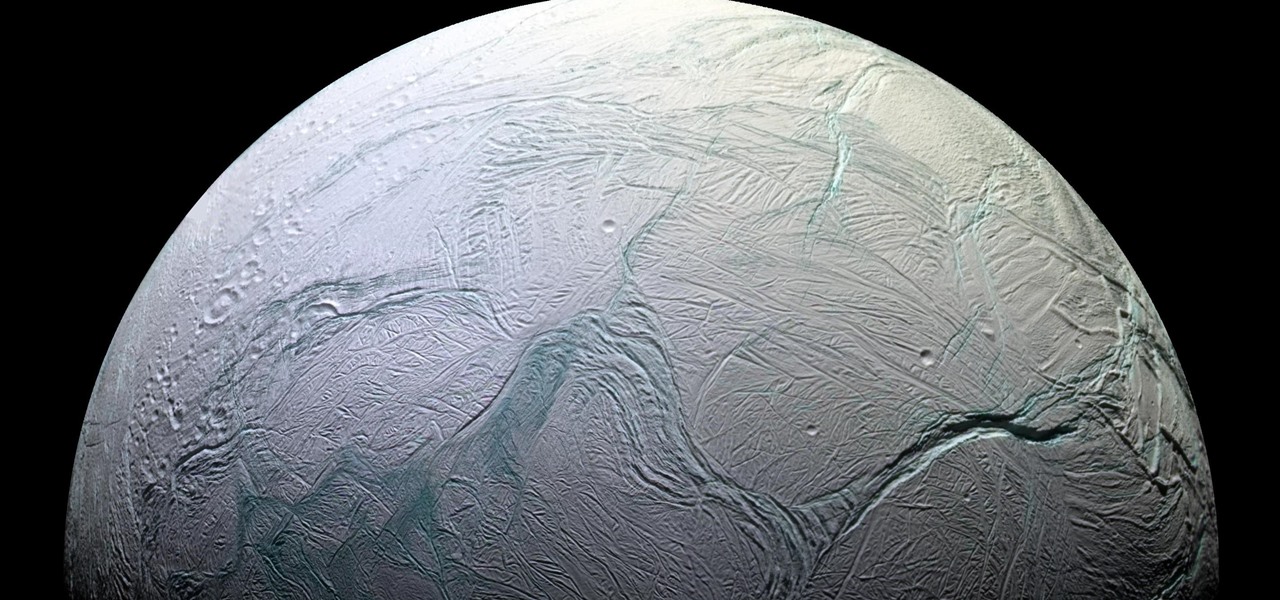
Earlier this year, NASA reported on findings that might point to water, and microbial life, on moons orbiting Jupiter and Saturn. Named Europa and Enceladus, those moons contain large oceans under their icy surfaces, which many speculate could hold microbial life.

While the technology continues to mature, businesses from various industries continue to adopt augmented reality to improve the efficiency of business processes. In this edition of Brief Reality, as conference season continues, we see examples of augmented reality applied to logistics processes and marketing of industrial supplies, as well as the topic of discussion at another trade show.

In a press event this past week at the Game Developers Conference in San Francisco, California, Unity Labs, the experimental and forward thinking arm of Unity, announced an upcoming toolset for developers in the augmented, mixed, and virtual reality space called the XR Foundation Toolkit (XRFT).

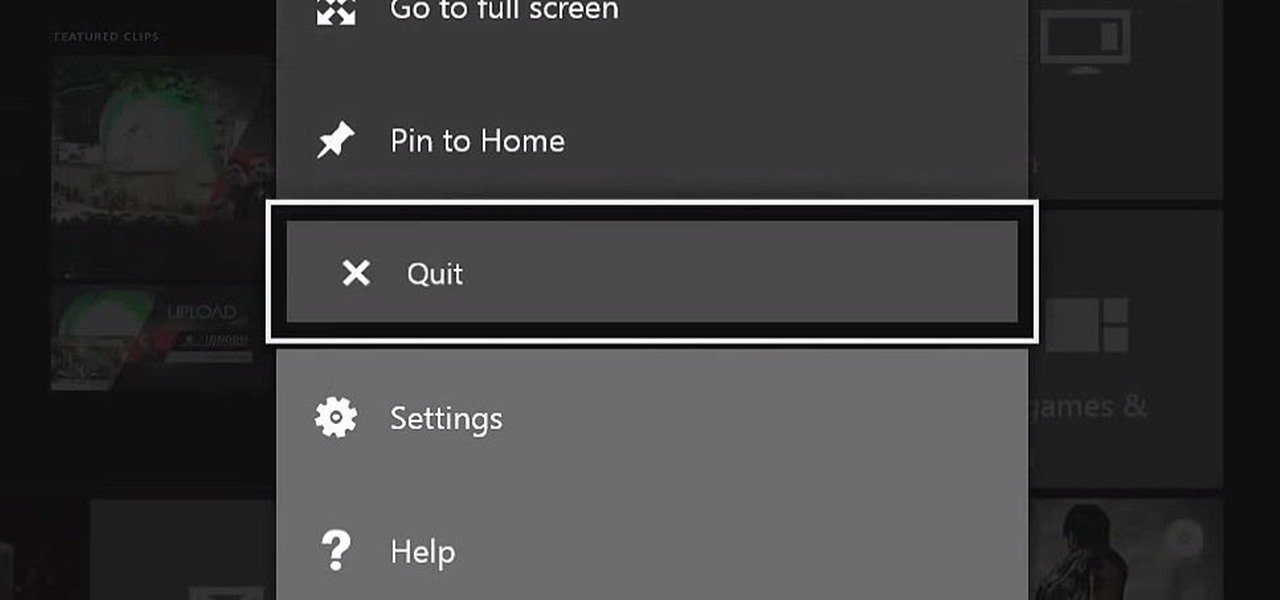
Anyone who uses a computer on a regular basis probably knows how to access the task manager to check system resources and usage stats. However, on a Samsung Galaxy S3 or other Android device, it may not be so obvious. There's no equivalent to Control-Alt-Delete, but it's still fairly easy to monitor running processes and battery usage.

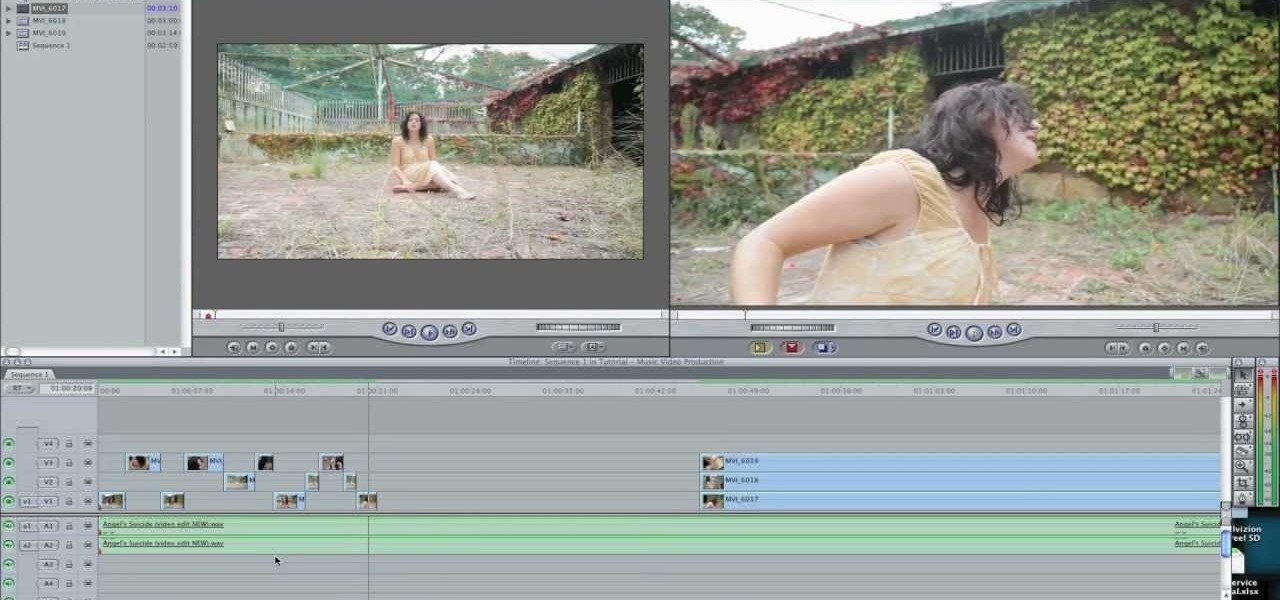
Heya Everybody, I have a brand new tutorial online - this time covering the topic of Music Video Editing and basic workflow processes like converting footage from a Canon 5D.

I may be a bit weird, but I enjoy listening to music at night as I fall asleep. Sure, you could create a playlist of songs so that it stopped after all the songs finished playing, but I have a rather extensive database of music and I enjoy listening to them randomly. Also, I like to ensure it terminates after a specific amount of time (I don't want it playing all night). Or sometimes I use it when I am cooking so that when the music stops, I know I need to check on my food, etc.

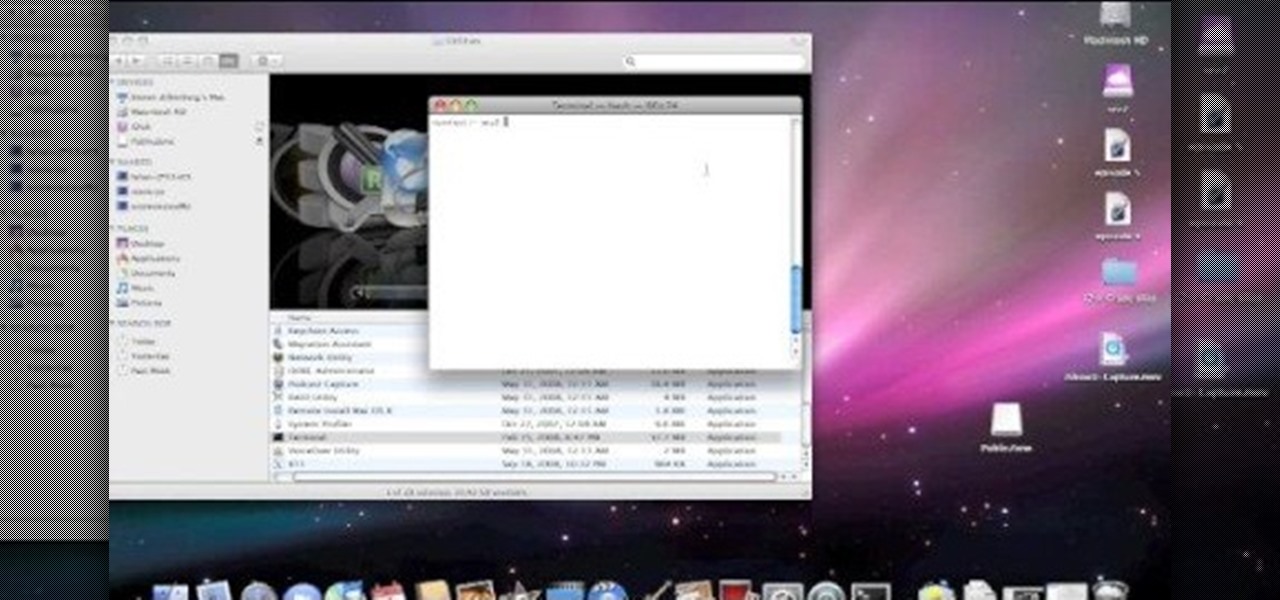
In this tutorial, we learn how to eject devices from the use of the terminal for Mac. First, go to the terminal of your computer where you will see a notepad sort of page. Next, type in "df" and then press return. You will now see a list displaying processes on your computer. On the bottom will be your public zoning device, which is your USB device. Next, type in "hdiutil eject -force (the code under "mounted on)- volumes-publiczone". This is not case sensitive, but don't forget or add in any...

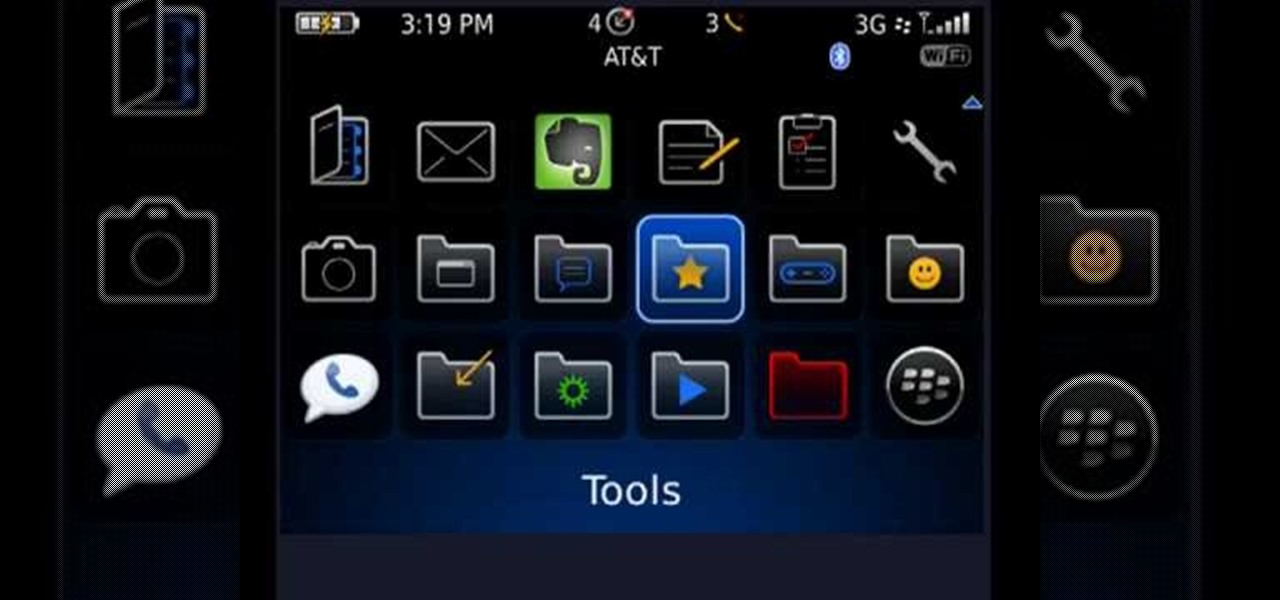
In this how-to video, you will learn how to shut down your Blackberry device quickly and easily. If you have uninstalled or installed a new program, this may be useful for you. You will have to find the power off tool in the display of your Blackberry. You can place this option in the tools section. Once you highlight it and press the track ball, it will begin the process of turning the device off. This allows you to shutdown all processes on the device and completely turn off. This video sho...

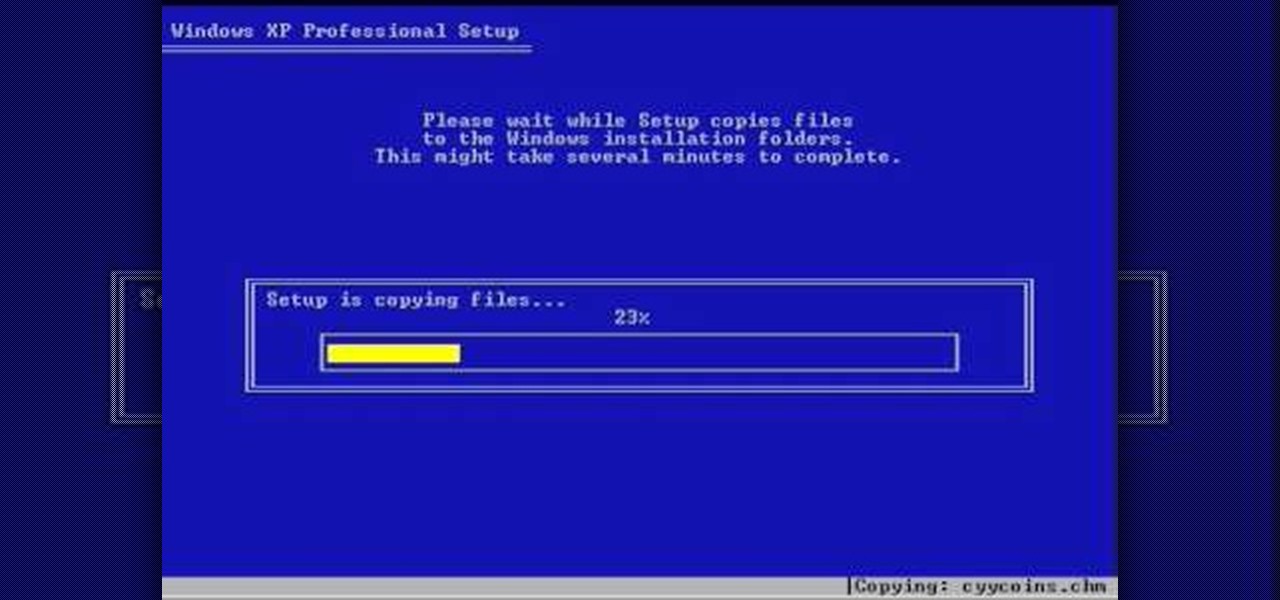
Puzzled on how to use your boot disk to repair your Windows XP system? This informative video from www.computerhilfen.com shows you step by step exactly what to expect to see on your computer screen. Fixing that slow or broken Windows XP computer system is not impossible! Make the processes easy and painless with the help of this video, which covers reformatting, reinstallation, and the first steps on preventing future problems with your Windows XP platform. Why waste money on computer repair...

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

Privilege escalation is the technique used to exploit certain flaws to obtain elevated permissions relative to the current user. There are a vast number of methods out there to go from user to root on Linux, and keeping track of them all can be difficult. This is where automation comes into play, and a privilege escalation script called Linux Smart Enumeration is one to take advantage of.

Luxury automaker Mercedes-Benz has joined the growing list of automakers adopting augmented reality to provide an assist to its manufacturing operations, in this case, via the Microsoft HoloLens.

Augmented reality headsets with larger eye boxes than any device currently available could make their way to market by the end of next year if current timelines hold true.

Mitochondria are known as the powerhouses of our cells because they generate energy to power them. But they also play a key role in the death of cells when they're damaged, infected, stressed, no longer needed, or at the end of their life.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

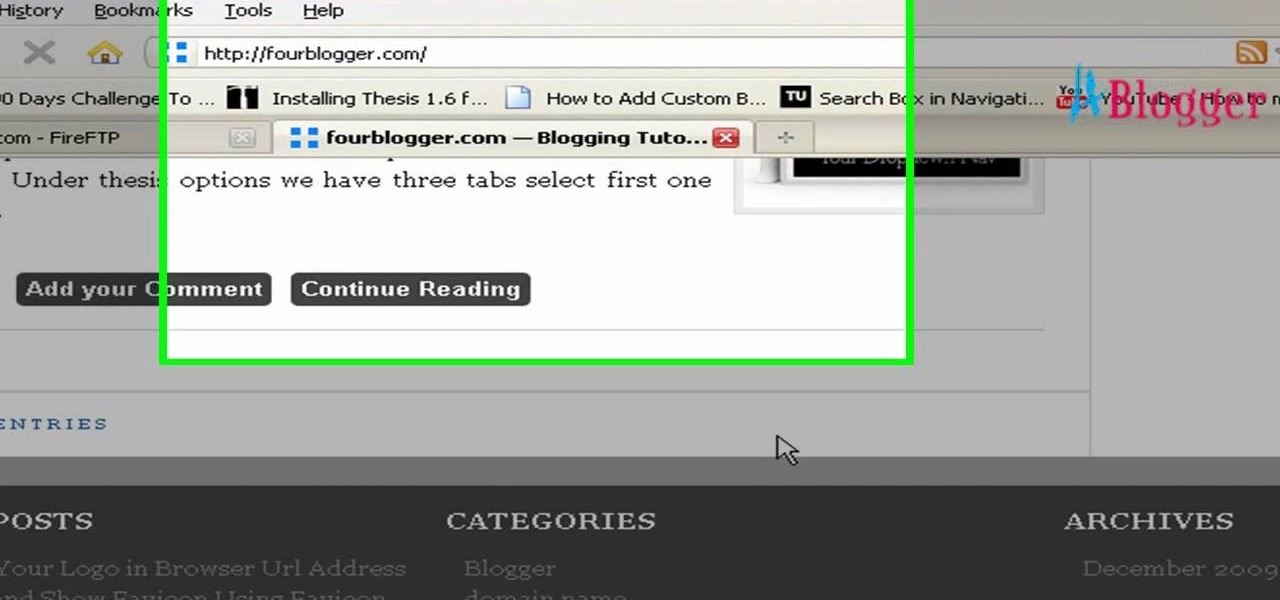
Get some great tips on Thesis themes for you WordPress blog. Watch this video tutorial from 4Blogger to learn how to remove the link in the footer of the Thesis theme.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.

Scientists know that bacteria create their own energy, get nutrients to run their cellular processes, and multiply. But, bacteria haven't been shown to respond to external mechanical stimulation or signals in a way that's similar to how our bodies respond to touch, until now.

Everything from disposed of drugs to hormones and disease-causing bacteria — anything that is rinsed or flushed down the drain — can contaminate wastewater.

Using extreme time-lapse microscopy, scientists watched a virus take over a bacteria to create a cell that looked and functioned more like a plant or animal cell. True story.

The story of Helicobacter pylori is a real testament to the tenacity of medical researchers to prove their hypothesis. It took decades before the scientific world would accept that the bacteria H. pylori caused ulcers.

Before I get ostracized by all of you whisky lovers who live and die by whisky served neat, let me say my piece.

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

KNOX is a major pain for Samsung owners who like to modify their devices. Its combination of hardware and software security measures make things rather difficult when you're trying to modify system-level files and functions without voiding your warranty.

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

The Xbox One is pinning its success on the fact that is much more than just a video game console. Microsoft is looking for the Xbox One to become the centerpiece for family entertainment, which is why they included features like multitasking, TV controls, and apps.

Back in the '80s, I was just a kid with a LEGO hobby. I remember building castles and floating boats, spaceships and monster trucks, even a working LEGO train powered by battery, lights and all.

Butterflies are beautiful creatures that can teach many lessons about the processes of nature. Learn how to make paper butterfly sun catchers from a professional art instructor in this free crafts video series.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

With Gboard, Google created a keyboard with more functionality than just inputting words. The app includes features such as GIF search and live text translation, but it gets even better when you let it learn more about you. With this data, Gboard grows from a good keyboard to one that can complete your sentences.

When your iPhone is being sluggish, one thing you can do to get performance back up to snuff is clear the device's random access memory. It's not a publicized feature from Apple, but it's there nonetheless. And while it's easy enough to utilize on iPhones with Home buttons, the iPhone X is a little trickier.