More platforms and more tools to make content for those platforms. It seems like the Dev Report —Next Reality's breakdown on the latest information on tools and processes to make augmented reality experiences — is going to be coming out on a much shorter cycle.

When Chan Mei Zhi Alcine chose her senior project, she thought outside the box by thinking inside the bottle. Along with a research team at her university, she found a way to combine health and enjoyment, while meeting a challenge not so definitively met before in alcoholic beverages. She and a research team at her university claim they've created the world's first probiotic sour beer.
In the first part of this series, we looked at the surface detection that is provided by the ARKit. We looked at how it worked and covered some of the tools that could help us determine what is not working; when it doesn't. Now let's take this to the next step.

New research reveals how E. coli bacteria construct elaborate and effective tunnels to pump unwanted molecules like antibiotics and other toxins out of cells. The discovery could help us better understand how antibiotic resistance occurs and give us a leg-up to beat them at their own game.
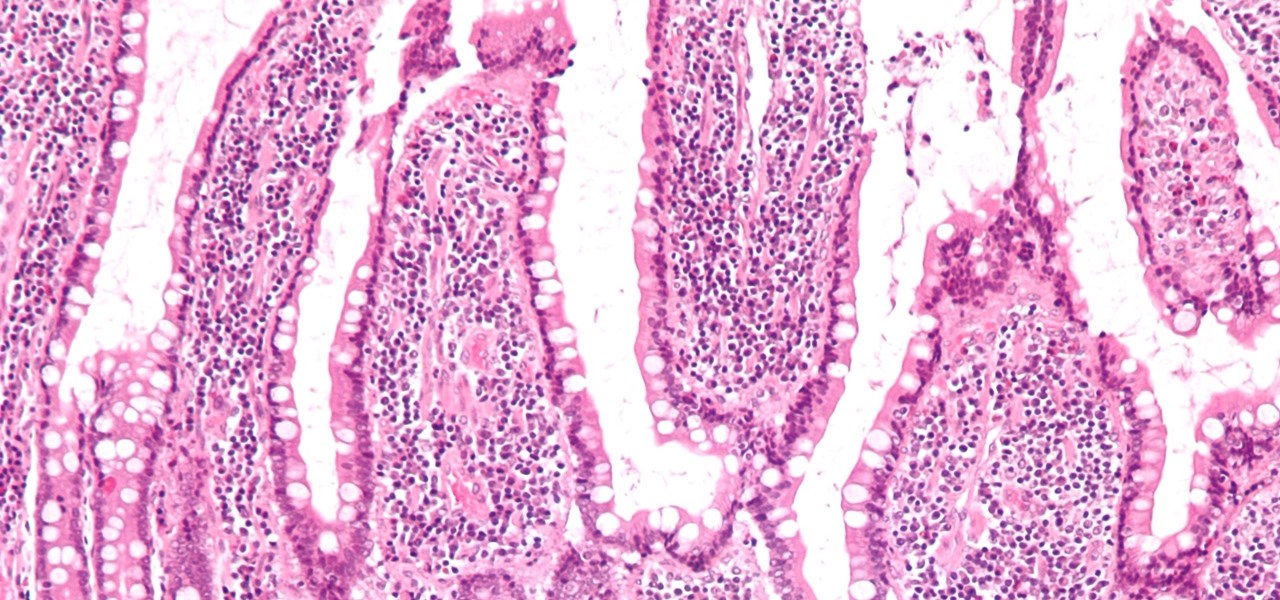
If the all the fingerlike projections in our gut were flattened out, its surface area would be 100 times bigger than our skin's. It's so large that the actions of just a small part of it can impact our health. A new research study has found that enterochromaffin cells in the intestinal lining alert the nervous system to signs of trouble in the gut — trouble that ranges from bacterial products to inflammatory food molecules.

The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

Tardigrades are some of the toughest but least well-known creatures on our planet. These tiny animals, also called moss piglets or water bears, are definitely of this earth, but some can boast that they've also traveled to space.

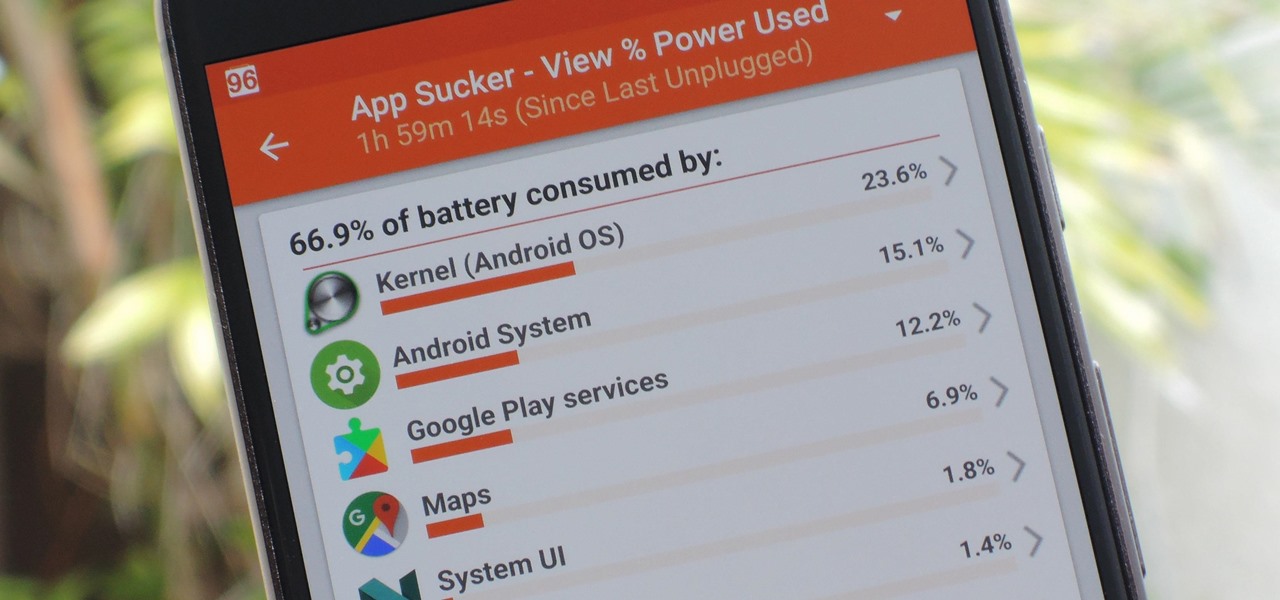
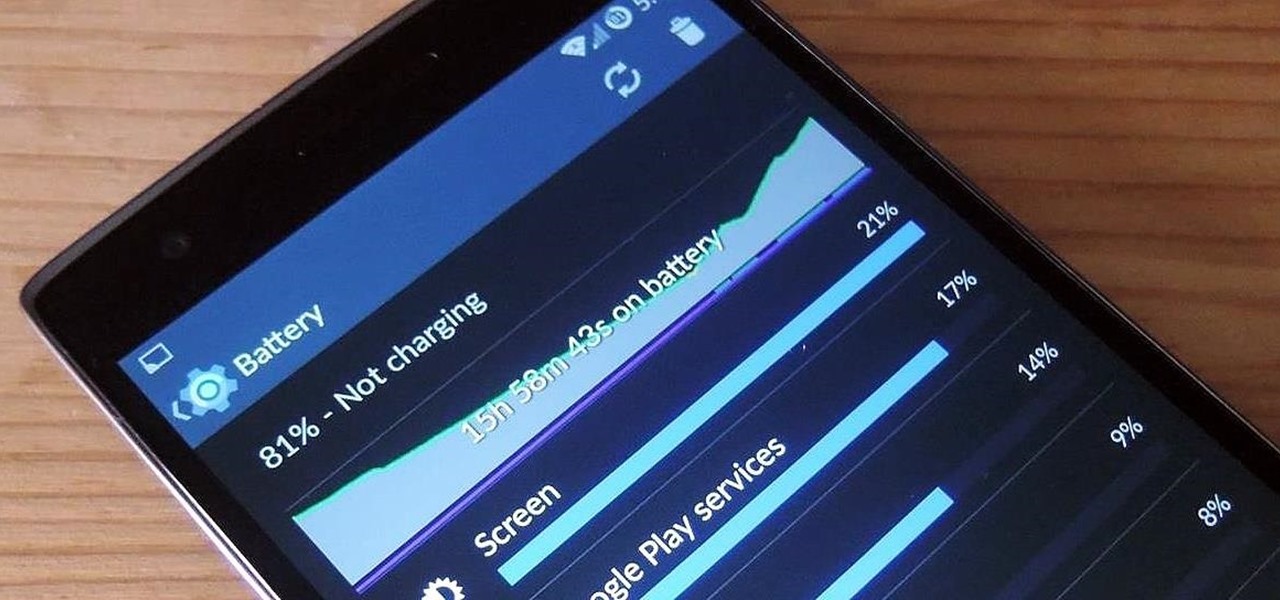
Figuring out exactly which apps on your phone are eating through resources and battery life can be a difficult task. Though some information can be found in Android's battery menu, the charts and graphs provided here pale in comparison to what's offered by the GSam app. If you configure this app properly, it provides deep insight into battery, CPU, and data usage.

Usually, the mucus lining of the female genital tract presents a barrier that helps prevent infections. But, somehow, the bacteria that causes gonorrhea gets around and through that barrier to invade the female genital tract.

Upskill, an enterprise software developer for industrial augmented reality applications, recently received an influx of funding and a major vote of confidence from two of their top customers.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

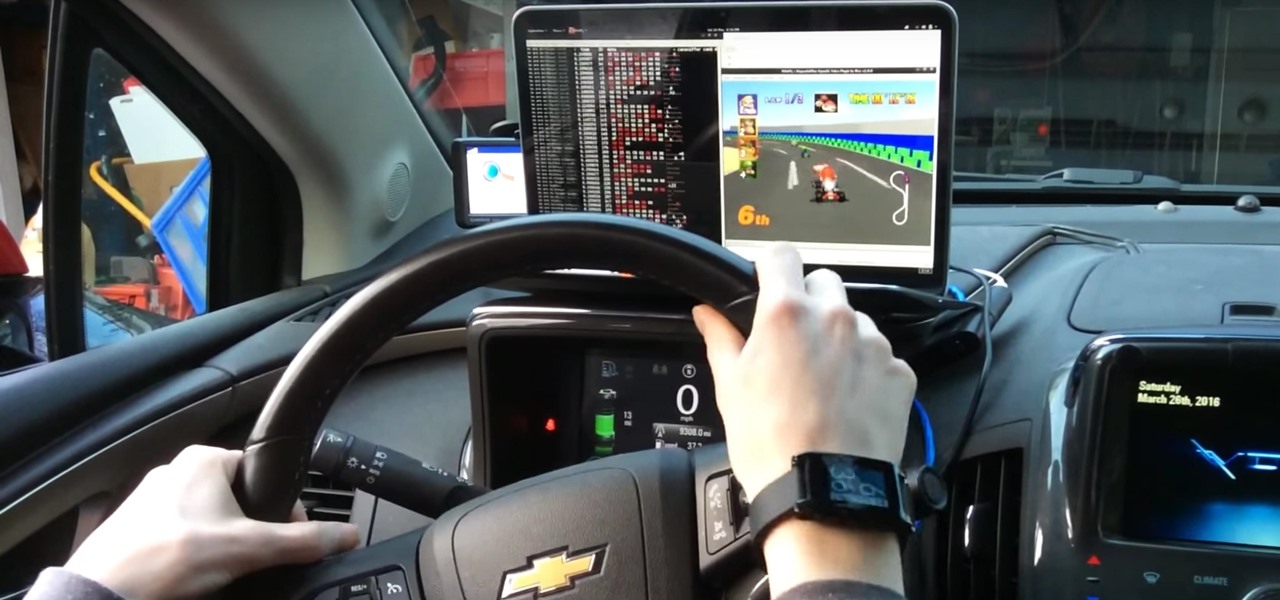
Oh, Mario. The guy that's been a part of our lives since as long as we can all remember. Well, Adam Ringwood and his friends did something pretty cool with one of Mario's most exciting games at the HackIllinois event in February 2016—they hacked a Chevrolet Volt's steering wheel into one big Nintendo 64 controller for Mario Kart.

Norovirus outbreaks occur all year long, but peak in the winter months, which means we are in the middle of norovirus season. But there's still time to protect yourself from the highly infectious bug.

Some bacteria can already do it—generate electric current, that is—and those microbes are called "electrogenic." Now, thanks to the work of a research group from the University of California, Santa Barbara, we know how to easily turn non-electrogenic bacteria into electricity producers.

Sleep lets our body processes rest and restores us for the next day, so a bad night's sleep can ruin the following twenty-four hours and even make us feel sick. Now, new research published in the journal Sleep cements the idea that loss of sleep actually leaves us vulnerable to sickness.

In this first part of our tutorial series on making physical objects come to life on HoloLens, we are going to set up Vuforia in Unity.

Robots are always really cool, if you ask me. Sometimes they're made out of Legos, and that's even cooler.

If you're standing in a foreign city, surrounded by signage in a language you don't understand, you won't suddenly be able to read it. But with a clever feature in Google's Translate app, your smartphone can.

If you find yourself switching between Android devices frequently—for instance, your Nexus 6P and a Samsung tablet—you've probably noticed how the button placement can be different. Normally, it's back, then home, then the recent apps button, from left to right. But Samsung devices have this backwards, which can lead to frustration when muscle memory kicks in and the back button isn't where you expect it to be.

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

Do you have a file (or many files) that, in the wrong hands, may cause you trouble? Don't worry about it, because I'll show you how to wipe it (or them) from your computer in order to leave no trace behind.

Hello Hackers/Viewers, It is a new day, and you might be thinking, It is so boring, why not try to be cool with computers in front of my friends? That is why, I have made this tutorial to make fake viruses using notepad to look cool!

The Galaxy S6 already has one of the best cameras on the market, but a few minor annoyances still linger. Full-sized photos are stored with heavy compression that can cause artifacting, burst mode shots aren't taken at 100% quality, and the camera flash cannot be used when your battery is below a certain threshold.

Does your Samsung Galaxy Note 3 feel slower than it used to? Background processes, cached files, malicious applications, and buggy updates can all lead to a sluggish smartphone. It's just what happens over time.

The new OnePlus One packs a 3,100 mAh battery that promises to last all day and night. While that will work for most, some of us don't quite know how to put our phone down and save some juice.

Changing your wallpaper and downloading icon packs is nothing new to the HTC One, but some people will go overboard with remapped keys, icon layouts on custom grids, and extensive wallpaper cropping—processes that could take hours to get just right.

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

Rooting a mobile device may not be a big deal these days, but not being able to root definitely is. Even the Library of Congress, National Telecommunications and Information Administration, and White House can agree on that.

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.

Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some significant changes to how it's used.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.

Do you want to know some quick tricks for improving tech processes at your company? How about equipping yourself with skills that will land you a new job or promotion this year? Becoming a cloud computing expert will make it happen, and right now, The 2021 Cloud Computing Architect Certification Bundle is on sale for just $29.99. That's an amazing 98% off the regular price of $1,800.

Linux has been one of the most popular desktop operating systems for nearly three decades, ranking fourth in the world behind Windows, macOS, and Google's Chrome OS. The open-source operating system is loved for its quick, powerful, text-based interface and efficient communication tools.

The native timer feature on your iPhone works well enough that you probably haven't even thought about installing a third-party timer. With just a few taps, you can get a countdown for any amount of time up to 24 hours (or one second shy of 24 hours, to be precise). But as fast as it can be to set a timer from the Clock app, there are even faster ways to start the countdown.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

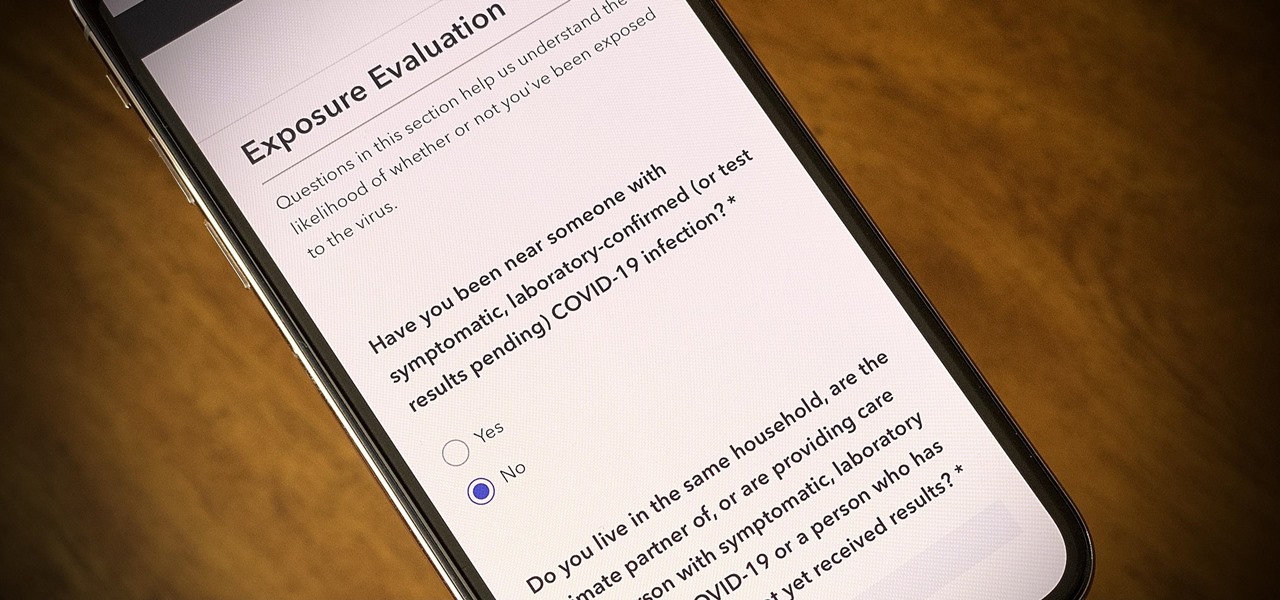
One of the scariest things about the COVID-19 virus is that you can show no symptoms but still be infected (and contagious). Naturally, we all want to know whether we're carrying the new coronavirus, but if you're showing signs of COVID-19, how can you be tested to know for sure? Websites are popping up to help with that, screening for symptoms, and directing you to a testing site if needed.

One vital part of Android 10's new navigation system is the "QuickStep" gesture. Swipe up from the bottom of your screen, then pause. You'll see your recent apps along with a dock containing a handful of icons for quick access. This dock is provided by the phone's launcher, which means your home screen is now integrated into the multitasking UI. So what happens if you change your home screen app?

Augmented reality plays a key role in the evolution of adjacent technologies, such as 5G connectivity and brain-control interfaces (BCI), and the business news of the week serves up proof points for both examples.