How To: Web Development 02 - Simple Webpage
Hello fellow Null-Byters! In this "tutorial" we will be going basics of HTML. In the next tutorial, we will be going over CSS and then apply JavaScript.


Hello fellow Null-Byters! In this "tutorial" we will be going basics of HTML. In the next tutorial, we will be going over CSS and then apply JavaScript.
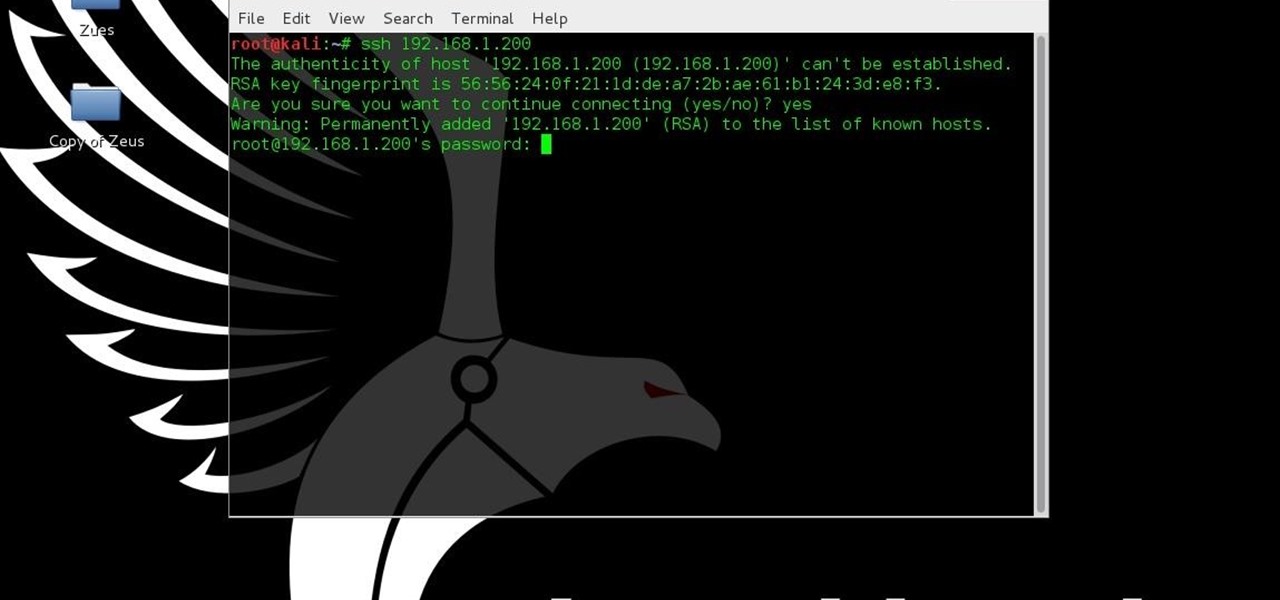
This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.

At last, what you all finally waited for! Hi! Fire Crackers,

Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps that could accomplish roughly the same thing.

In general, we never really put much thought into fonts, but they comprise a huge portion of our online experience. A whimsical mood can easily be set by using something like Segoe Script, but switch it up to Sentinel and you've got a more sophisticated feel all of a sudden.

Converting files from one format to another can be a pain. Sometimes you have to download software that you'll only end up using once. Other times you have to use a shady third-party conversion site that's riddled with ads. Not to mention that after a while, unless you're extremely organized, your converted files will be scattered all across your hard drive.

Injustice: Gods Among Us is one of the most popular games to come out over the last couple of years. It was a hit on video game consoles, and it's got a solid 4.5 rating on both Google Play and the iOS App Store, with almost 2 million people rating the game combined.
To contemporize a popular quote, "A cluttered desk(top) is a sign of a cluttered mind." Of course, it's difficult to maintain a tidy desktop... as you read this, mine is cluttered with screenshots, folders, Word documents, videos, pictures, and apps.
With Nexus devices already enjoying Android 5.0 Lollipop, most other manufacturers are scrambling to get their flagships updated to Google's latest operating system. While HTC has promised Lollipop by the end of 2015, OEMs such as Motorola and Sony have already issued updates to their latest models. Then there's Samsung.

Most diehard Mac users have used TinkerTool at some time or another, and if you haven't, it's time to start. Whether it's to change your system's font or to disable UI animations, it seems like anything you could ever think about tweaking in Mac OS X is doable through TinkerTool. And now, developer Marcel Bresink has updated his app to work with Yosemite, so let's see what it can do now.

With recent security breaches in the news, there is no better time than the present to make sure you know exactly what's happening on your device.
In the past few weeks, the internet has been abuzz with nightmarish horror stories of Comcast's questionable decision-making and downright terrible customer service. The central theme of many of these disputes with the nation's largest cable provider is that without evidence, the conglomerate will refuse to acknowledge its mistake and place the burden of proof on the customer.

We tend to assume that eating is mostly a physical act, but the mind has so much to do with the choices we make.

If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its UK counterpart, GCHQ, are mining the ad networks utilized in these apps to collect a trove of information on you.

With so many cloud storage services out there, many people are starting to keep their important documents online, especially when they know they'll need to view them when they're away from their computer.

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...

Any living creature will die if deprived of sleep for long enough. The longest documented occurrence of a person not fully sleeping and surviving is only 11 days. There is a rare disease where deep sleep is never achieved, affecting roughly 100 people worldwide. Patients usually only survive between 6 to 18 months after the onset of chronic insomnia, and only 3 to 9 months in a parasomnia state without any real REM sleep.

I recently had my iPhone stolen at public park and did everything I could to locate it, but with Find My iPhone disabled (I know, what an idiot) and no exact address to give to the police, I had about a .00000001 percent chance of getting it back.

We've all had to write an essay or research paper at some point, and undoubtedly the hardest part about it is always the citation, right? If you ask me, it's a huge pain in the arse. Even more so if you're gathering your facts from a huge variety of sources.
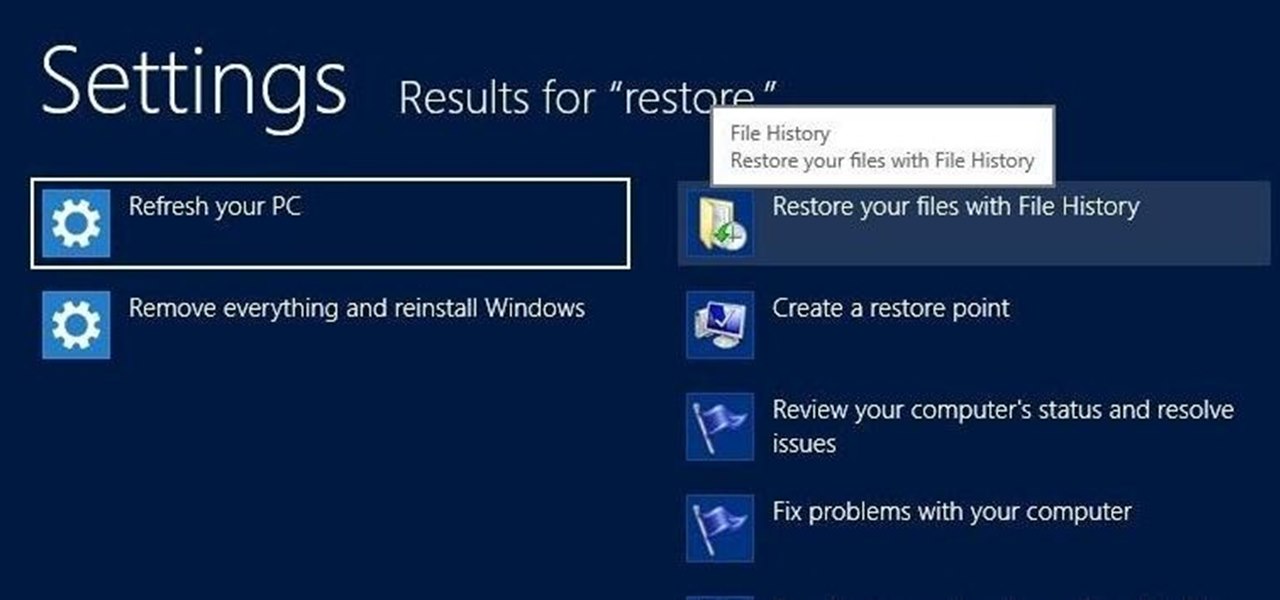
There is nothing worse than losing valuable information or programs on your computer. And if you've ever accidentally deleted a file or document, you know how agonizing that entire process can be.

On Thursday, March 14th, Samsung unveiled their new Galaxy S4. With it came a slew of new features, but what does that mean for us S3 users? Unless we're willing to shell out big bucks for the full retail version, most of us S3 owners (at least in the states) will not be eligible for upgrades until next year.

Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording capability on the remote system of your roommate.

UPDATE: The whitehouse petition has received enough signatures to require a response from the government. Your voices have been heard! Now we wait...

The convenience of storing things on the cloud can definitely make life easier, but if you're storing sensitive files, it could be a total disaster if anyone hacked your account. Some encryption services can be expensive, but if you just need it for personal use, there are some really great ones that don't cost anything. Here are three programs that let you encrypt your cloud storage for free. BoxCryptor

If you're doing research that includes a lot of copy/pasting, it can get really tedious to open a new document every time you want to save something. Luckily, you can cut out the extra step and save text and images that are currently in your clipboard directly to a folder or your desktop—without the hassle of creating file after file. Here's how to do it on both Windows and Mac OS X. Windows

Robert Templeman from the Naval Surface Warfare Center in Crane, Indiana and several of his friends from Indiana University recently developed an Android application that is capable of gathering pictures and videos from mobile devices in order to reconstruct a user's environment in 3D. The malware would come coded inside of a camera application that the user would download. The malware, called PlaceRaider, would then randomly take pictures throughout the day and carefully piece them together ...

If you've got more than one computer, it can be a huge pain to switch form one to the other. Between files, settings and apps, it can take a while to transfer everything—and if you're running different operating systems, it's even worse. Image by Onion

Taking screen captures is a standard feature on iPhones and newer Android smartphones, but for some reason it's not very intuitive. Screenshots allow you to share your phone's screen with your friends, document technical problems for customer support, and even make how-to guides easier to follow. So, it's definitely worth remembering. Here's how you do it.
An amazing amount of news this week; new proposals and new agreements have sprung up. But so has our "need" to spread our presence. The military warns of another war, while 26 congressmen decry the use of drone strikes. Read on:

When doing a research project it is very important to not only cite the sources you use to give proper credit but to also cite them correctly. To cite information sources:
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack EXP, HP, pupils and ranks in MyBrute (08/12/09).

Let TutVid teach you how to make metallic text is Adobe Illustrator CS3. This video shows you how to do it step by step. You only need basic knowledge of Adobe Illustrator CS3 to do this.

Get a crash course on HScript Expressions, Variables, and Attributes in Houdini 10. If you don't even know what this means, then you probably need to check this video tutorial series out. Understanding how to massage data in Houdini is key to giving yourself the creative edge and allowing you to unleash mind-blowing visual effects. This 18-part video series covers a variety of simple yet essential weapons in your arsenal including Global, Standard and Custom Variables to Math and String Modif...
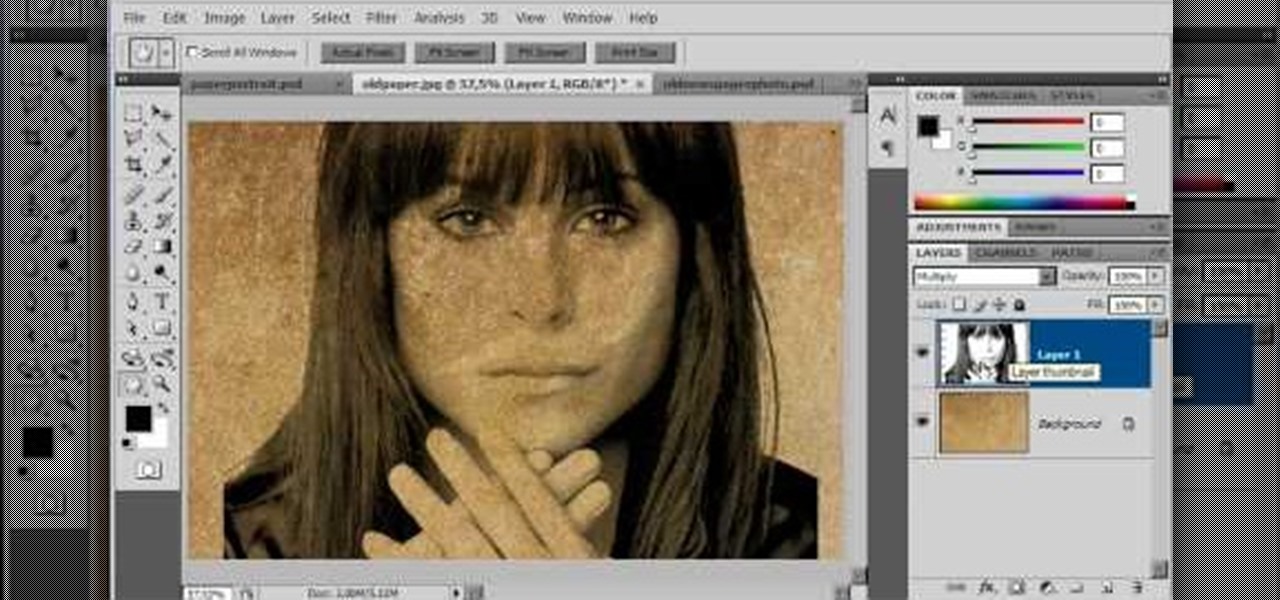
The video is about how an old stalled photographic image with faded backgrounds to a normal image. A nice clean digital image is taken and is mixed with a texture of a paper and produces a final composite image of all effects combined. The procedure is not that difficult but it needs to be followed in a proper order. First the paper texture is taken as a base and then the clean digital image is dragged onto this texture. The blending mode is adjusted from normal to multiplied blending mode, w...

We've all used electric irons before to get our clothes crisp and wrinkle-free, but what happens when you use a little too much starch? The bottom hot plate, called the soleplate, accumulates some gunky buildup. Even if you're not over-starching your dress shirts, your Rowenta iron may be getting some gunk on the soleplate, which doesn't produce a perfectly ironed shirt. That's where the Rowenta ZD100 cleaning kit comes in handy. If you get one of these, you could easily clean your iron yours...

If you're thinking about making some minor paint repairs on your vehicle, getting that paint to match the color on your car can be a difficult task. This video will help you out by showing you how to blend your automotive paint to match the existing color.

When it comes to gardening, there are various methods that can be used to help produce an area that you and others will appreciate. What might work for one person, may not work for another. Each has their own benefits, it just depends on the gardener and which works for them.

When you think of frozen foods, you're probably picturing an image of calorie bomb Hungry Man TV dinners or jumbo-sized Klondike bars. But frozen foods can be a lot healthier than you think.

The best way to make sure you have the best connections on high voltage-lines is to clean them. Cleaning high-voltage wires with cleaning solvents is the best way to get the job done for a better flow of electricity. This video, produced by Polywater, trains electricians on the proper high-voltage cable cleaning procedures during splicing and termination. Methods are shown to remove different types of shields and compounds from insulation. The "Do's and Don'ts" of abrasion, solvent spraying, ...

This video explains some important things you need to know if you are thinking about growing your own vineyard. First, think about the types of grapes you want to grow, depending on whether you want to make raisins, grape juice, jelly or wine. Talk to your extension agent to find out which grapes work best for your purpose. It's important to thin out the crop and not have too many leaves on the vines, or too many grapes, because a good balance will send the sunlight and nutrients to the plant...