In this video tutorial from CreativeCOW leader Tony Ross, learn to use Flash as a drawing tool, while making several pseudo-3D shapes, including a flower pot. Tools include the Rectangle Tool, Oval Tool, Paint Bucket Tool, and Free Transform Tool. Draw a flower pot in Flash.

This how-to video shows to remove beer from a bottle in just one second, win free beers every time with this bar trick. Granted, you probably should just drink the beer instead of spraying it all over the place. Watch this video tutorial and learn how to pour out a beer bottle at super speed. Empty a beer bottle in one second.
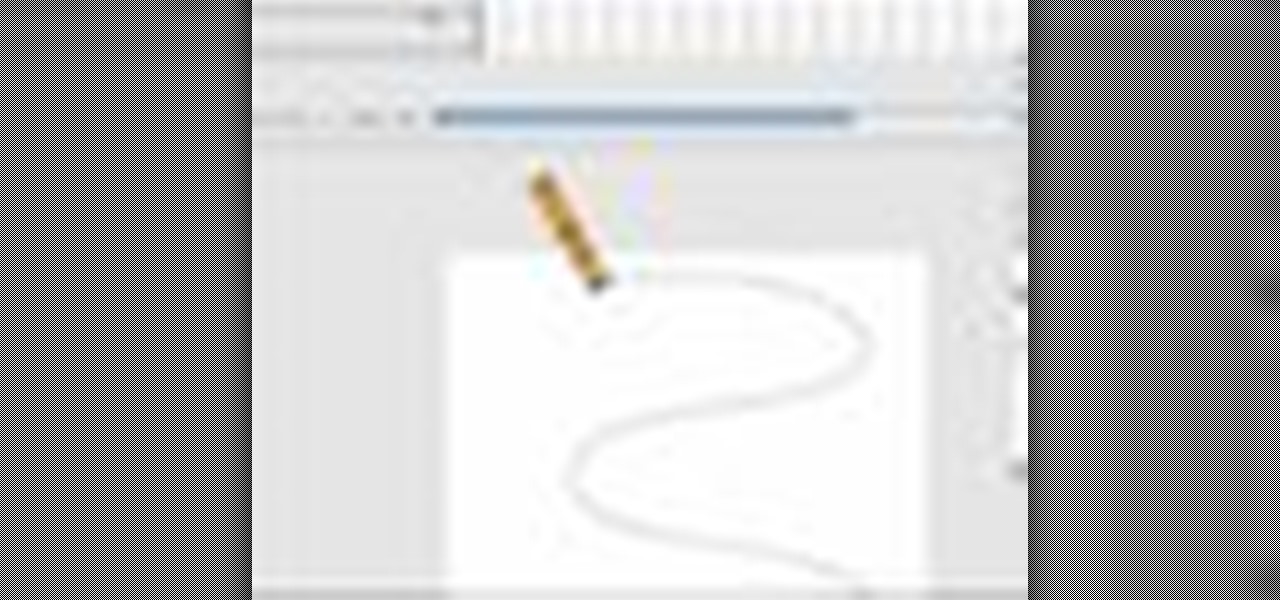
Learn how to use Masking, Motion Tweens, and Motion Guide Layers to create an animated pencil drawing a curved line. Tools used are the Rectangle tool, Pencil tool, and Free Transform tool. This is an intermediate level Flash tutorial. Animate a pencil drawing a curved line in Flash.

Learn the basic layout and functions of GIMP(GNU Image Manipulation Program) a free open source image-editor, and how to work with files. Get started using GIMP - Part 1 of 2.

How to use the Bezier tool, which allows you to create complex objects quickly and simply, in GIMP(GNU Image Manipulation Program) the free open source image editor. Use the Bezier tool in GIMP.

How to use the fill and gradient tools to work wth color in GIMP (GNU Image Manipulation Program) the free, open source image editor. Use the fill and gradient tools in GIMP.

How to add text to images and start working with layers in GIMP (GNU Image Manipulation Program) the free, open source image editor. Work with text and layers in GIMP.

WinMorph is free morphing and warping software. It runs as a standalone application or as a "plug-in" for various video editors/compositors like Adobe Premiere, VegasVideo and Wax. In this video tutorial you will learn how to do a basic morph in Winmorp. Use Winmorph.

In this Photoshop CS2 video tutorial you will learn to paint custom shapes. Learn to use the brushes, Color Picker, and layer style. This example uses a flower shape downloaded from ActionFx.com, but feel free to experiment with other shapes too! Paint within a shape in Photoshop CS2.

Need some storage space that you can access anywhere in the world? Why not use your hotmail or gmail and get free 2gb online hard drive. Turn your hotmail or gmail into an online hard drive.

Chef Gale Gand demonstrates how to make brown sugar meringue. This is a brilliant variation on classic meringue, made with brown sugar, a half a cup of egg yolks and sugar. The egg yolks are beat over a hot water bath to ensure the eggs are free of bacteria. Make brown sugar meringue.

As many of you know Windows is not the most secure Operating System in the world, but then again no OS is really secure if the user doesn't know how to protect themselves. Later I will show you how to lower the risk even more on your (the user's) end.
A nice (free) resource if you are new to Java and would like to learn more!
The beta version of Photoshop CS6! It's free indefinitely from Adobe until the beta period ends!
The cryptology course went live today and is accepting anyone who is interested for registration. Check out the link for more information and to view the other awesome free online courses!

Easy steps to create viaduct walls and portals for tunnels from cement. Drawings in actual scale are available for free download from www.railmodellingindia.com. Simple process, great result!
Away3D is a 3D engine built for flash that leverages Flash's new 3D capabilities. It is open source and free to use.

I'll keep this short and sweet, as the game is online, loads quickly, it's free, and easy to play: it's quicker to play it than describe it: EnterTheStory.com

Any please feel free to add videos, articles, pictures- anything related to gmail from google.
You don't need a Kindle or a library card to read! Reading stimulates the brain, exercises the emotions, and you may actually learn something too! :)
Why not waste your afternoon? You don't need those spreadsheets anyway...

This is the first official announcement for a new weekly activity on Null Byte for the community to participate in. Starting next week, depending on how much traffic we get doing it, we are going to start doing live social engineering calls via Skype. I've made a list below so that you can get a feel for some of things we'll try to accomplish in these calls.

Now Bounce Energy has made mananging your MyAccount even easier by designing an app available to Android Phone owners! Download it from the market today- for free!

Today's article serves as a general guide to keeping Windows 7 and Vista clean. The goal is to clean up your messy computer and have it running at maximum performance in no time. The question at hand is—what is your computer's performance like?

Hi Fellow hardcore Gamers within the UK Gaming Community. Please be kind enough to add us to your google plus circles and we will return the favour and add google +1 button likes for you and you can do likewise for our site.

Captured with Nokia E5 . and I used Baable free from nokia apps

Hello everyone and welcome to Part II - The Ultimate Guide: Diagnosing & Fixing Connection Issues. In this tutorial we will discuss more advanced methods that I took in order to fix our home network. I have also attached a link to download the FREE eBook - so feel free to download it to you can refer to this manual when you are experiencing connection issues. I would also like to note that the manual has been loaded onto a free server - it will remain on the server until people stop downloadi...

A few days ago, CloudOn released their free mobile app that brought Microsoft Office directly to your Apple iPad. The cloud-based service effectively runs Office on their end, allowing you to use apps like Word and PowerPoint to edit your documents, which you would house in Dropbox. But after overwhelming demand, they removed the free app yesterday from the iTunes App Store.

Most people have had the unfortunate experience of not having a washer and dryer at some point. Apartments in my area tend to charge at least one hundred dollars extra for the units with washer and dryer hookups, and even more if you want a unit with an actual washer and dryer installed already. If you are young and just starting out, this may be hard for you to manage with your current salary. If you have no washer and dryer, the only alternative is the laundromat.

Null Byte is looking for moderators. More threats to computers exist every day. Not only do we have computer viruses and malware, but we have rootkits and other nasty pieces of code that can log your keyboard strokes or even add your computer to a botnet to attack other websites. Your computer can be infected even if you have anti-virus software installed. I can't stress enough how easy it is for a hacker to write a piece of code that gets around every piece of anti-virus software.

All Mod Cons. Shot and Edited on iPhone 3G.

Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

Check out iPhone app, LEGO Photo. It converts any photo to look like it's built from Legos. Best of all, it's free. I used a photo of a dinosaur I submitted to a previous challenge in Giveaway Tuesdays. See the original here.

http://itunes.apple.com/us/app/bathroom-prank/id481762522?ls=1&mt=8

All About The Mobbing Tool-bar check it out! ***CLICK HERE***

When Windows stores a password, it is done so by hashing the password in an LM hash and putting it in the Windows SAM file. In the scary moment that you lose your password, but don't want to pay some geek to have full root access to your computer, you need to recover it using Ophcrack. Ophcrack doesn't remove the password, or bypass it, it cracks the password hash using rainbow tables.
This video tutorials shows you step by step how to get rid of most spyware from your system.

Video accompanying free plans for a photo light box offered on www.WilmerWoodWorks.com Check out our site which is full of great plans and information about woodworking by Steve Wilmer.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.