In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, but the location is "beyond the Caucasus mountains," which could imply Russia?) desperately want their hands on this system.

I have been on Null Byte for a long time, a very long time and. I havent always had an account here, ive like many of you also have, been looking and decided to make a profile to contribute.

With the brand new SMS-based ordering service called Magic, anyone with a mobile phone can order whatever they want—really, anything—by sending causal text messages. Who says magic isn't real?

Each flavor of sake, the national spirit of Japan, comes with its own fans, not unlike whiskey aficionados here in the States. While sake is often called "rice wine," it is more akin to a malted beverage like beer.

Hard as it is to imagine, there are people out there who loathe garlic and onions. Some might have allergies or medical conditions like IBS, or are supertasters (i.e. people who carry a certain gene that makes them extremely sensitive to how certain foods taste). Others might just be picky eaters.

The release of the Nexus 5 marked the debut of the Google Now Launcher. Even with an integrated Google Now page on your home screen, the most talked-about feature was actually the always-listening functionality.

What separates the work habits of the ultra-productive from us mere mortals struggling to check items off our never ending to-do lists? While the answer to that question is by no means simple, one undeniable factor in their success is a clearly defined, highly organized workflow.

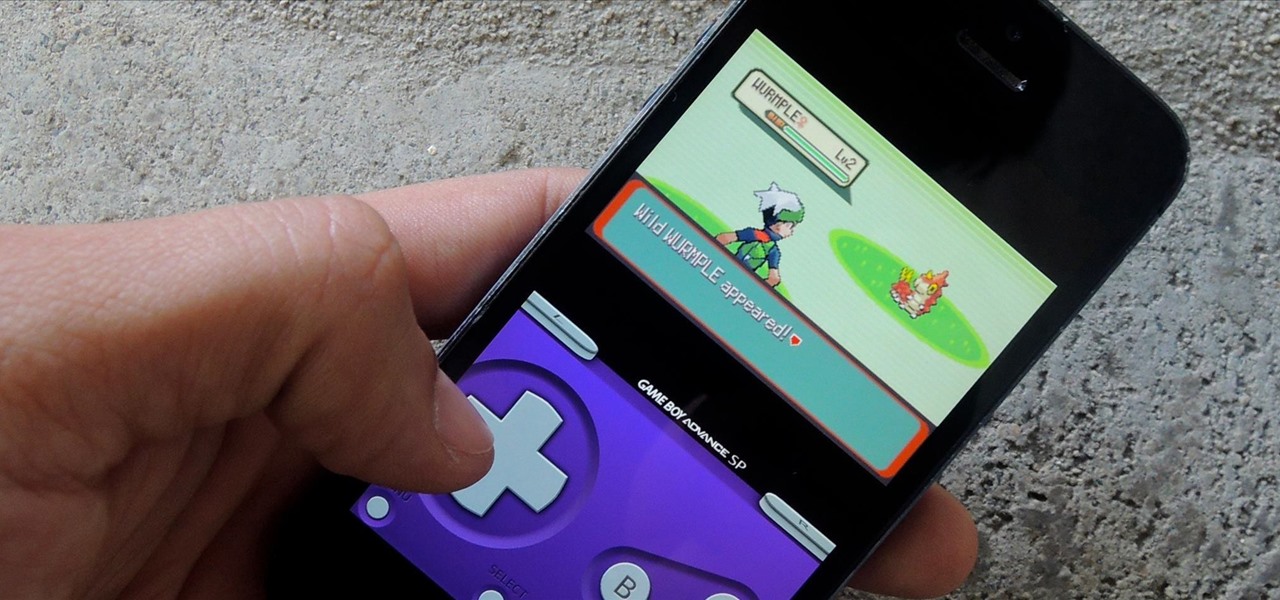
Normally, you'd have to jailbreak your iPad or iPhone to play any games that aren't available in the iOS App Store, like the now-extinct Flappy Bird game. But this isn't the case if you want to play some of your favorite old school Nintendo classics.

There are few apps on my iPhone that I visit on a daily basis, and one of them is Drippler, the discovery and news app that tells you everything you need to know about your device.

If you prefer to use Google or another search engine for everyday browsing in Safari but would also like a more secure browsing experience for all your secret searches, there's a simple way to switch between them quickly while also adding additional layers of security on top of your already clandestine browsing.

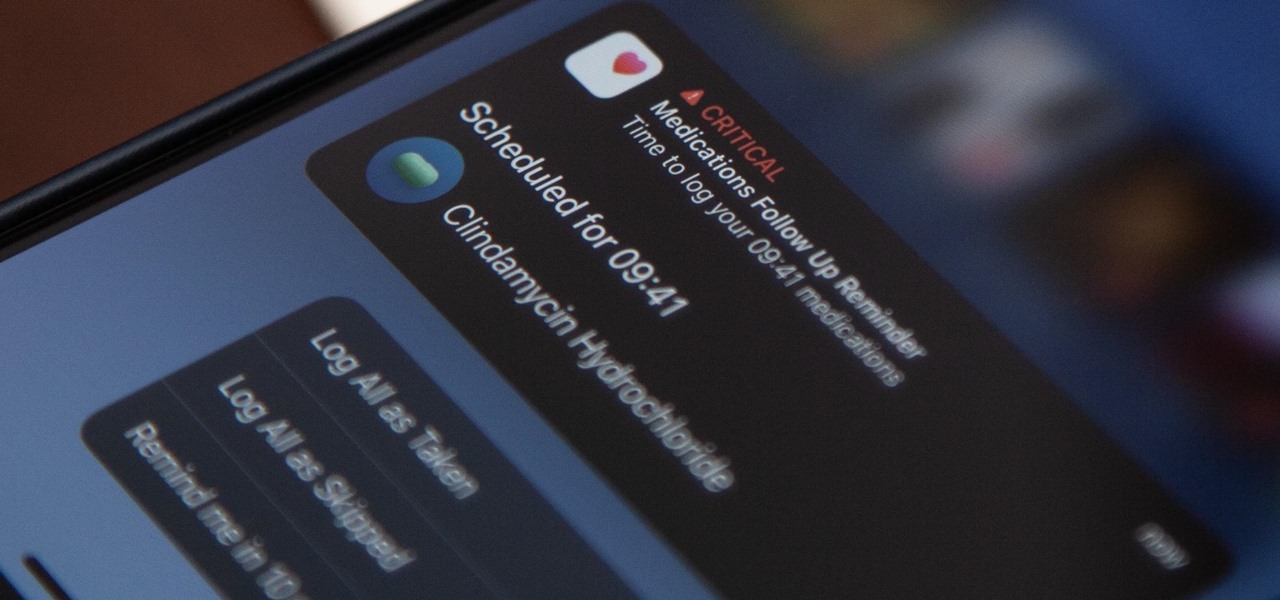
Since iOS 16, you've been able to add and track medication in the Health app, learn about potential drug interactions, and receive dose reminders. With iOS 17, Apple improves that last aspect with even more notification options to ensure you take your medicine on time and never miss a dose.

Apple just released its biggest update to iOS 17 yet, and there are 60 exciting new changes for your iPhone. With iOS 17.2, you get a brand new app, more Apple Music enhancements, upgrades in Messages, and a new security feature that was announced last year, as well as changes for Weather, notifications, Apple TV, Books, and more.

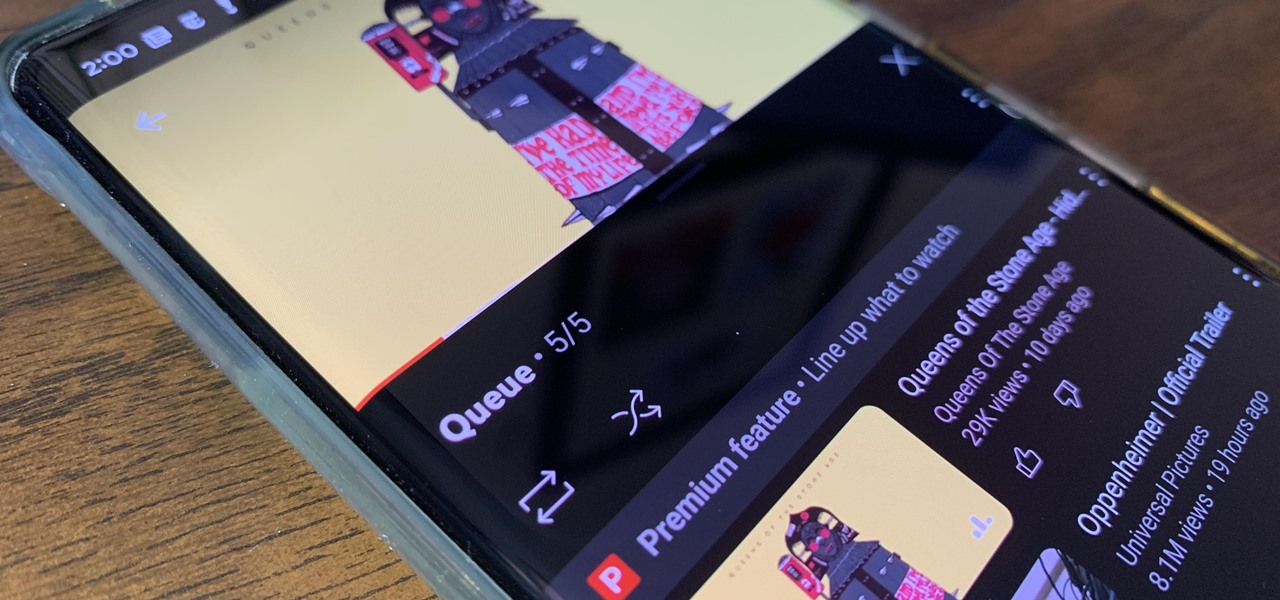
YouTube has offered viewers a video queue on desktop browsers for some time, and the world's most popular video site is preparing to finally bring the queue feature to its Android and iOS mobile apps.

If you can't find the remote for your Android TV or Google TV, don't like using its voice control feature, are sick of using the directional pad to type, or can't get it to work at all, use your smartphone instead. Using your iPhone or Android phone as a virtual remote control can be more convenient, easier to use, and more helpful than the original remote, so it's definitely worth trying out.

Apple removed the option to quickly change between miles and kilometers when using Apple Maps on iOS 16, but it's not entirely gone — it's just not as easy to find.

A little-known setting on your iPhone gives you the power to change the color of certain contact names and email addresses when drafting an email. Customizing the color works well for visually separating contacts at a glance, and it can even help you from sending an email to the wrong person.

Apple has given third-party developers access to Picture in Picture on iPad since iOS 9 and, more recently, on iPhone since iOS 14, but YouTube has been one of the few not to support the feature outside of Safari or premium memberships. Thankfully, that's no longer the case if you live in the U.S.

While the rest of Big Tech is still moving relatively slowly on augmented reality smartglasses, Snap continues to supercharge its own experimental AR wearable called Spectacles.

The initiative known as Project Aria has been the focus of curiosity around Facebook's augmented reality plans ever since Mark Zuckerberg revealed the device around this time last year.

Just when everything seemed settled over at Magic Leap, it turns out that the internal tumult is still in play.

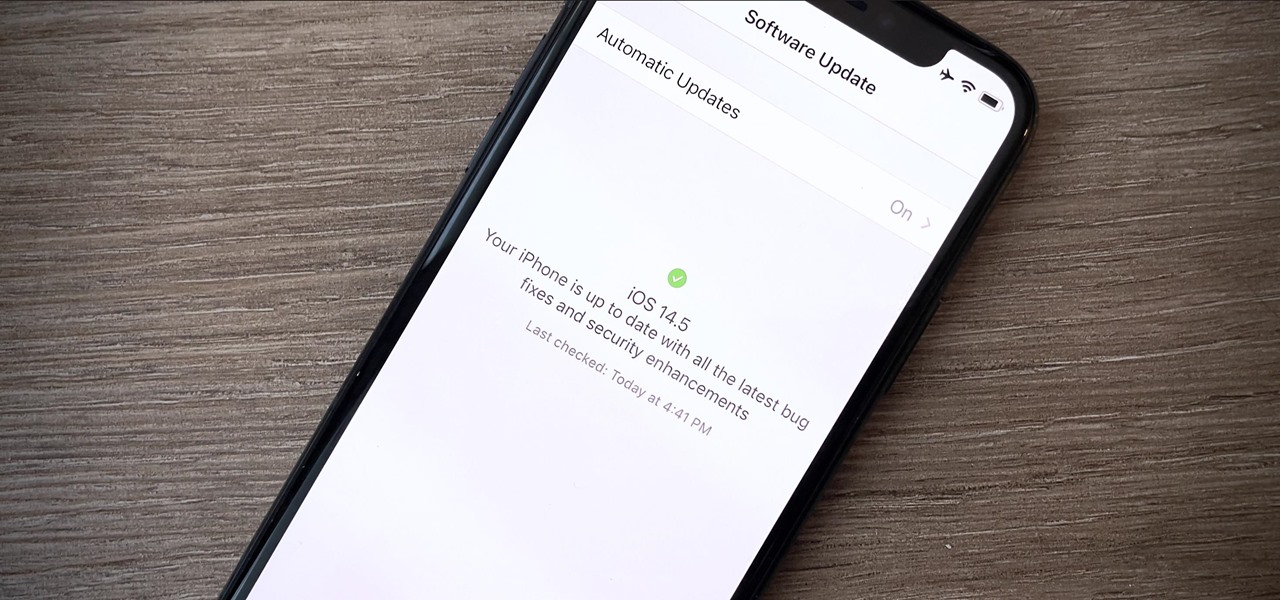
Your iPhone is full of features, many of which you might not even know about yet. Still, Apple keeps adding feature after feature with each new iOS update, and iOS 14.5 is no exception. The latest iOS version adds at least 69 features for your iPhone that you should be happy about.

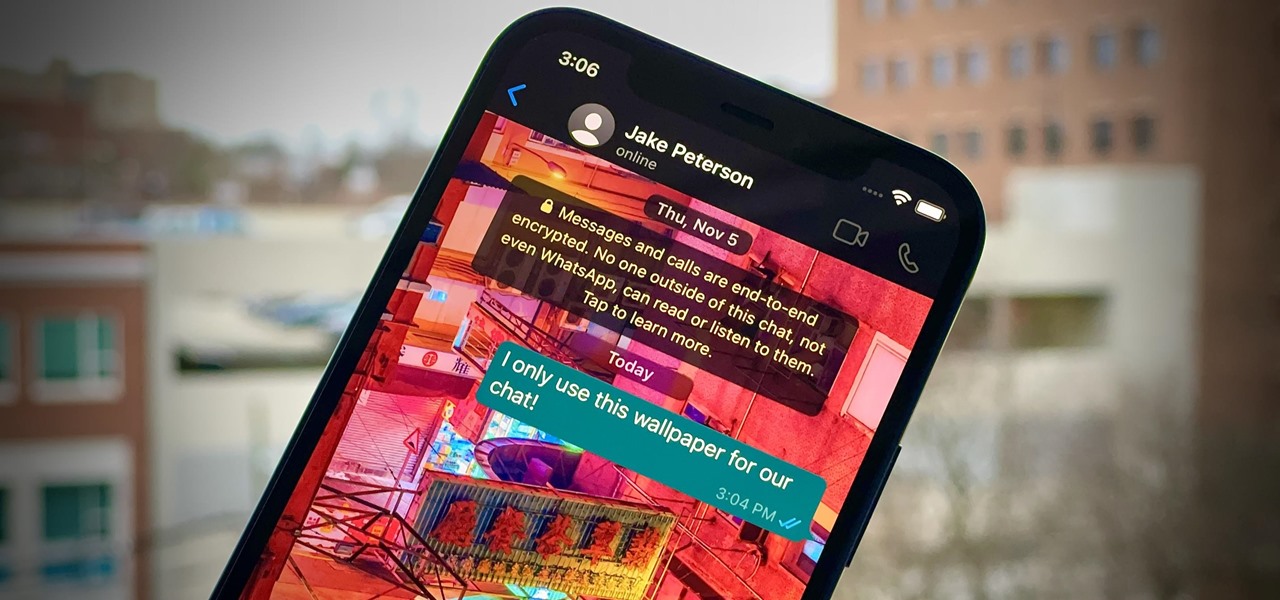
Popular chat apps like Facebook Messenger and (these days, sadly) WhatsApp might not cut it when it comes to privacy and security, but they sure do offer some fun ways to customize your chats. If you're worried that moving to Signal Private Messenger means you lose these features, don't — the privacy-focused app also lets you choose custom chat wallpapers for all your threads.

One of WhatsApp's best features is being able to change the default wallpaper for all chats. There's no reason to stick to the default WhatsApp backgrounds when you can be texting over an image of literally anything. In a newer WhatsApp update, you can go a step beyond that by setting custom wallpapers for individual chats, personalizing every text thread you have.

So, you've just plugged in your new Chromecast with Google TV. You lean back to watch a TV show or movie and you notice that people look kind of ... odd.

Apple just released the third public beta for iOS 14 today, Thursday, July 23. This update comes one day after the company released iOS 14 developer beta 3, and two weeks after the release of iOS 14 public beta 2.

Apple just released iOS 14 developer beta 3 for iPhone today, Wednesday, July 22. The update comes 15 days after Apple released the second developer beta for iOS 14, and 13 days after the release of iOS 14 public beta 2.

As government officials scramble to contain the new coronavirus outbreak with bans on large gatherings, travel restrictions, and school closures, the rest of us have to worry about how we're going to safely purchase water, toilet paper, groceries, and other household goods during the global COVID-19 pandemic.

If you're using or need to use Zoom, the popular video teleconferencing service, you've almost certainly heard about "Zoombombing" by now. While Zoom has been adding security measures to address the problem, there are other things you can do to prevent or stop Zoombombers in their tracks so that your video meetings and chats go undisturbed and uninterrupted.

Your smartphone is likely full of COVID-19 news and coronavirus panic. These are scary days, and there doesn't seem to be any end in sight. If you're having trouble coping with the stress and anxiety the virus brings with it, know that your iPhone or Android device can actually help you, rather than just bring you further down.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

Back when I worked in the music industry, I never imagined there would be a day that I'd be able to sit in a room surrounded by virtual album covers while listening to beats, but that day is really here.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

Can lightning strike twice? Niantic is betting that it can with its latest augmented reality game based on the best-selling multimedia franchise Harry Potter.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

Google's next-gen cellular carrier, Google Fi, which replaces Project Fi, is making waves across the mobile industry. With super-cheap plans starting at only $20 and the ability to connect to millions of Wi-Fi hotspots across the globe, it's tempting many users to make the switch from AT&T, Sprint, T-Mobile, and Verizon Wireless.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.